Explore tweets tagged as #WebApplicationHacking
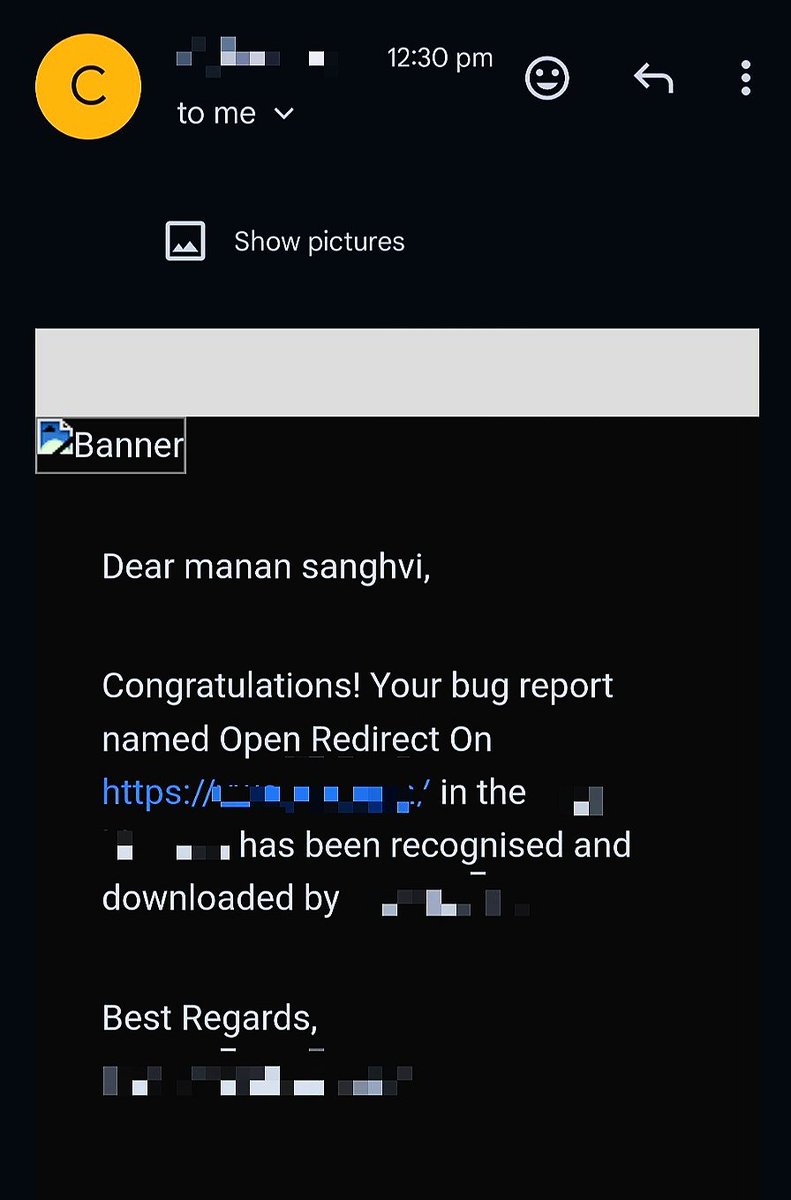
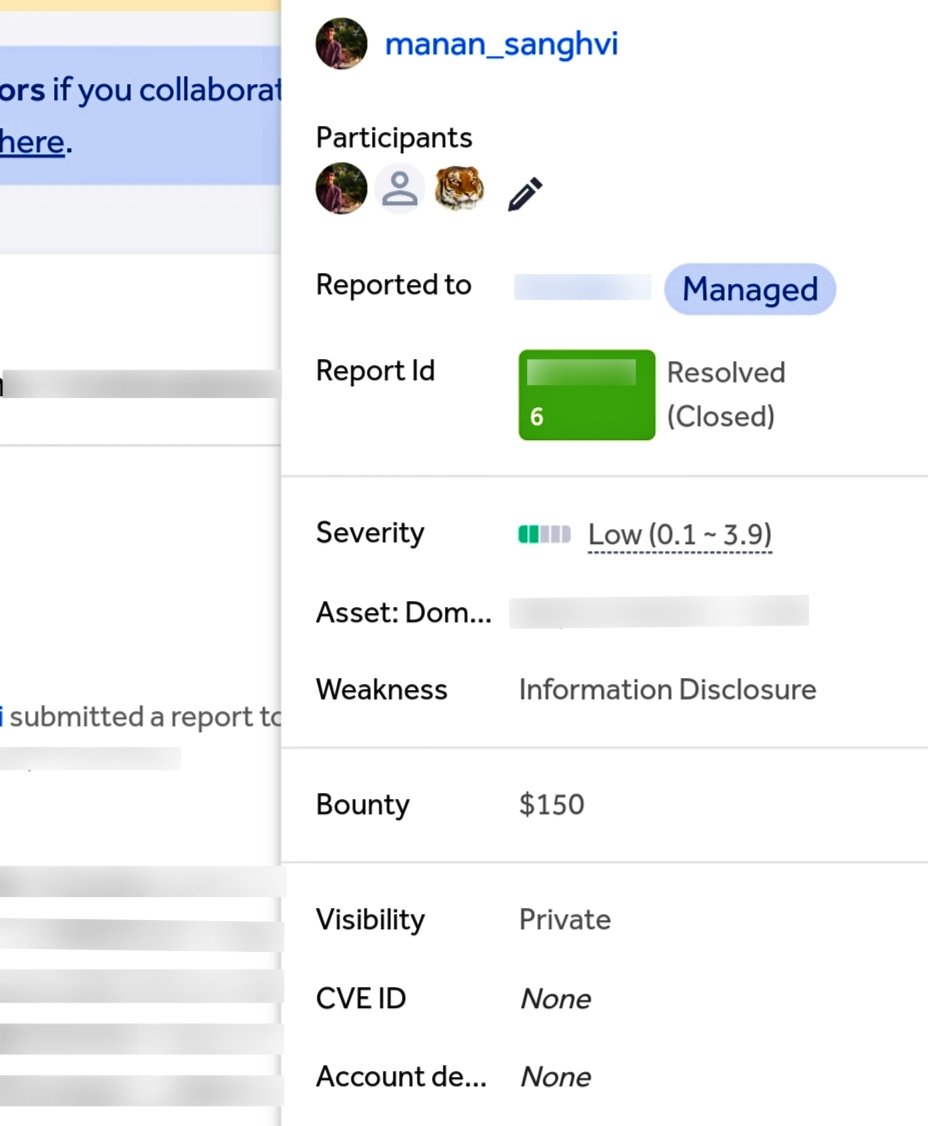
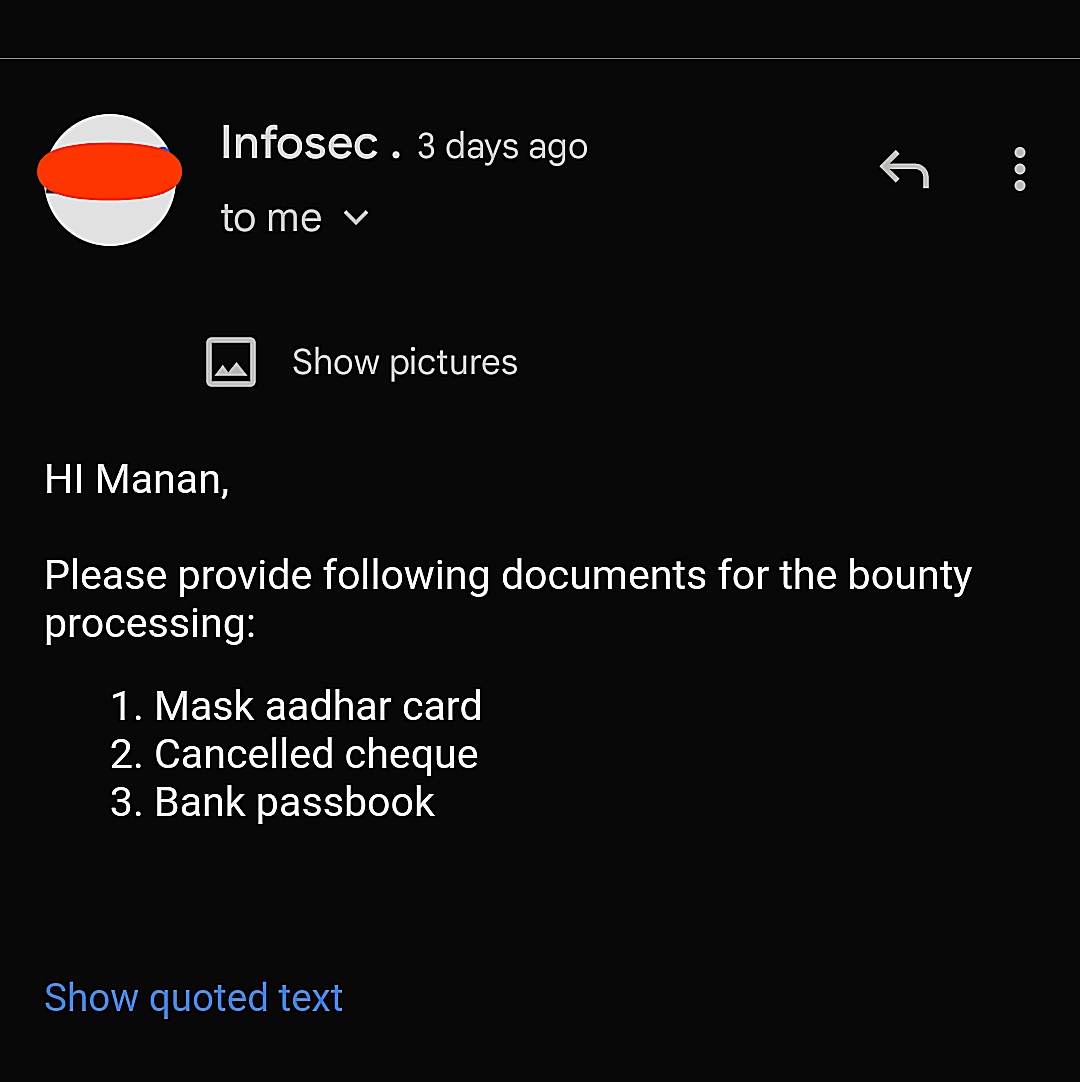
✨✨ Another Hit 🎯 Open Redirect. ✨ ✨ .#hacking #bugbounty #webhacking #penetrationtesting #openredirect #cybersecurity #security #webapplicationhacking #manualhacking #testing #manualtesting #pentesting #penterster #hacker #server
1
0
27
Bounty From @Hacker0x01. ! 🤘🤘🤘. #hacking #hackerone #penetrationtesting #idor #informationdisclosure #bugbounty #webapplicationhacking #resolved
2
1
66
Thank you @sensepost for the great training last week! Really been itching to play with web assembly, and low and behold it was in the course! Up to date and hands on training, can recommend and trainer @TH3_GOAT_FARM3R. #infosec #pentesting #webapplicationhacking #appsec
2
2
27
Hardwork Always Pays off! 🥲🥺😈💪.30 lakh Korean W0N (~$2259) , 2nd time 4 fig. Bounty $$$$. #bugbounty #ethicalhacking #penetrationtesting #fourfigurebounty #vulnerability #hacking #webapplicationsecurity #webapplicationhacking #reputation #power
0
0
5
I just got CAPen certified. Thanks to @TheSecOpsGroup for the great exam! . #SecOps #CAPen #applicationsecurity #webapplicationhacking
7
0
6
Finally done with #CAPen #CAP. It was fun exam :).I had taken several exams before, but it was really difficult.broked 5 points for each hint. @TheSecOpsGroup.#SecOps #CAPen #applicationsecurity #webapplicationhacking
1
1
15
🤟🤟🤟Bounty💰💰💰.Vulnerability: Directory Listing.#ethicalhacking #bugbounty #webapplicationhacking #directorylisting #vulnerability #bounty #testing #dollars #infosec #selfhosted
0
0
3
Finally done with #CAPen . It was fun exam :) .@TheSecOpsGroup 🖤🩶 . #SecOps #CAPen #applicationsecurity #webapplicationhacking
1
0
8
After more than a month of waiting, the bday gift finally arrived! Bug Bounty Bootcamp here we go! Thanks @vickieli7 for taking time to write this book 😁. #bugbounty #bugbountybootcamp #webapplicationhacking #security
0
0
2
This holiday, up your game with the C|EH & Web Application Hacking and Security courses. Sign Up for the Dual Program: #CEH #CertifiedEthicalHacker #EthicalHacking #Cybersecurity #WebApplicationHacking
1
2
2
Types of ethical hacking in Cyber Security!. #EthicalHacking #cybersecurity #WhiteHatHacking #WebapplicationHacking #NetworkSecurityhacking #Socialengineering #Systemhacking #MobileApplicationHacking #hacking #hackings #security #EthicalHackingTechniques #EthicalHackingtypes
0
0
1
Duplicate 🥲🥲 .Vulnerability: Open Redirect.#hacking #bugbounty #webhacking #penetrationtesting #openredirect #cybersecurity #security #duplicate #webapplicationhacking #manualhacking #testing #manualtesting #pentesting #penterster #hacker #server
0
0
4
Beginner-Friendly Ethical Hacking Course: Start your ethical hacking journey with 'The Ultimate #BugBountyHunting Course' ! . This comprehensive course introduces you to the fundamentals of #webapplicationhacking, equipping you with the practical skills to identify
0
0
2
A certificate that can certify a better future!.Congratulation H Ouedraogo for cracking "Certified #EthicalHacker examination" (CEH) under the training & guidance of our CertHippo Solution. #certhippo #ethicalhacking #courses #elearning #Cryptography #WebApplicationHacking
1
0
0
Up your game with the C|EH & Web Application Hacking and Security courses!. Sign Up for the Dual Program At No Additional Cost: #CEH #CertifiedEthicalHacker #EthicalHacking #Cybersecurity #WebApplicationHacking #UpSkill
1
1
9
Register for Certified Ethical Hacker and Receive a 100% off Coupon for the Web Application Hacking and Security Course*. Sign Up for the Dual Program: #CEH #CertifiedEthicalHacker #EthicalHacking #Cybersecurity #WebApplicationHacking #UpSkill
0
3
12
Web Application Hacking and Security.Web Application Hacking and Security is the only experiential program that provides comprehensive .knowledge and 100% hands-on learning. #Webapplicationhacking, #webapplicationsecurity, #webapplicationattacks,
0
0
0
Cross-site request forgery (CSRF), known as session riding, is a type of cyberattack in which authenticated users of a web app are forced to submit malicious, state-changing requests created by an attacker.#Cybersecurity #CSRF #WebApplicationHacking
0
0
0
Hidden OAuth attack vectors #BugBounty #bugbountytips #SSRF #OAuth #WebApplicationHacking #Hacking #Penetrationtesting.
0
2
1