Explore tweets tagged as #HashFunction
"SHA-256 is a powerful cryptographic hash function that is widely used in #blockchain technology. It ensures the security and integrity of transactions by providing a unique digital fingerprint for each block. #crypto #security #hashfunction"
0
1
4
Blake 3, recommended by NSA, offers advanced security and efficient performance against SHA-256, utilizing parallelizable multi-core functionality. #blake3 #cryptography #hashfunction
0
1
0
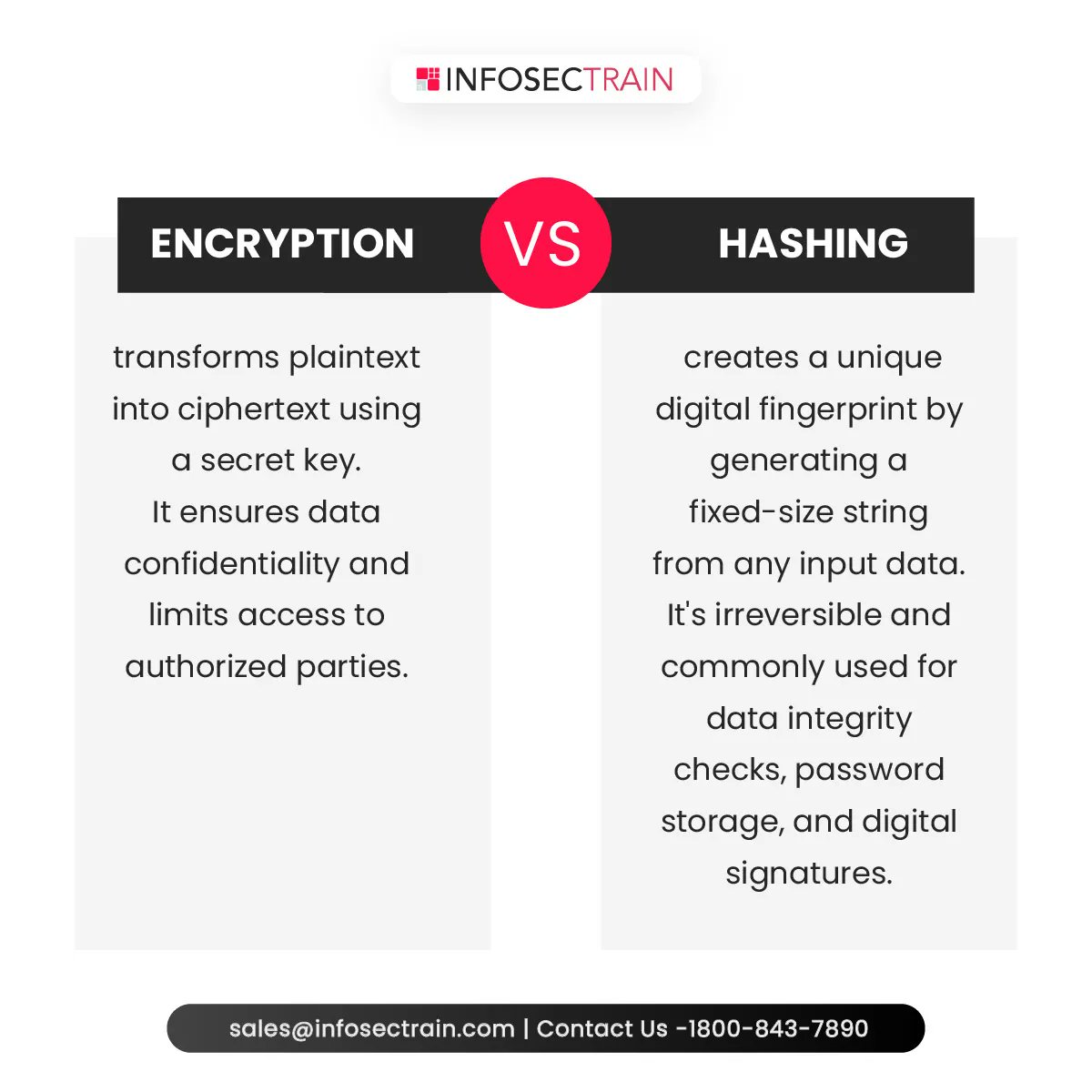
Confused about ENCRYPTION and HASHING? Let's break it down for you! Learn more: https://t.co/hHw9X24F4v
#EncryptionVsHashing #DataSecurity #SecureCommunication #Cryptography #DataProtection #EncryptionTechnology #HashFunction #DataIntegrity #DataPrivacy
0
0
4
Modified My NSH (Not so Secure Hash) Algorithm Here’s how mining looks in action! Note: Real mining is far more complex. #Blockchain #CProgramming #HashFunction #Cryptography #BlockchainDevelopment #SystemProgramming #SHA256 #Crypto #Mining #Bitcoin #Ethereum
0
0
4
Cryptographic hash functions take any size input—whether it’s a short message, a photo, or an entire video—and transform it into a fixed-size output, like a digital fingerprint. #Cryptography #Blockchain #HashFunction #CryptoEducation #BlockchainTechnology #CryptoExplained
0
0
0
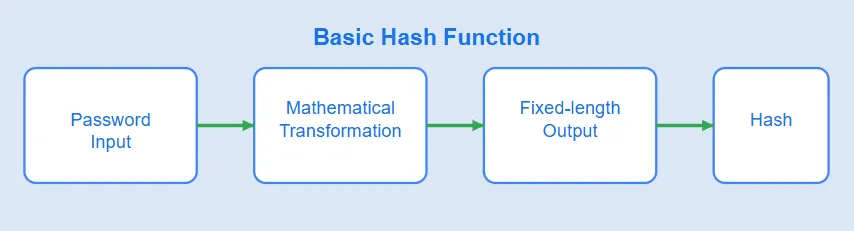
"A hash function is a mathematical function that produces a fixed-size output, known as a hash value, from an input message. Used for data validation, message authentication, and digital signatures, hash functions are one-way and collision-resistant. #HashFunction #Cryptography"
0
0
0
Network Security Model and Cryptography #networksecurity #networkinterview #InterviewPreparation #encryption #Cryptography #Hashfunction #SecurityEngineer #networkengineer Read - https://t.co/AwBUUpS0JV Follow - @NETWORKINTERVI1
0
0
0
What happens when you type your password? It goes through a hash function - turning it into a fixed-length, irreversible value. No matter how long or short your input is, the output is always the same size. Perfect for storing passwords securely! #CyberSecurity #HashFunction
0
0
4
🐶 LeetCode Problem #572: Subtree of Another Tree Language: Java ☕️ Difficulty: 🟡 Easy 🔥 Takeaway: Recursive functions are commonly used in traversing trees! 🌳🔄 #LeetCode #Java #Coding #Tree #DepthFirstSearch #String #Matching #BinaryTree #HashFunction
0
0
2
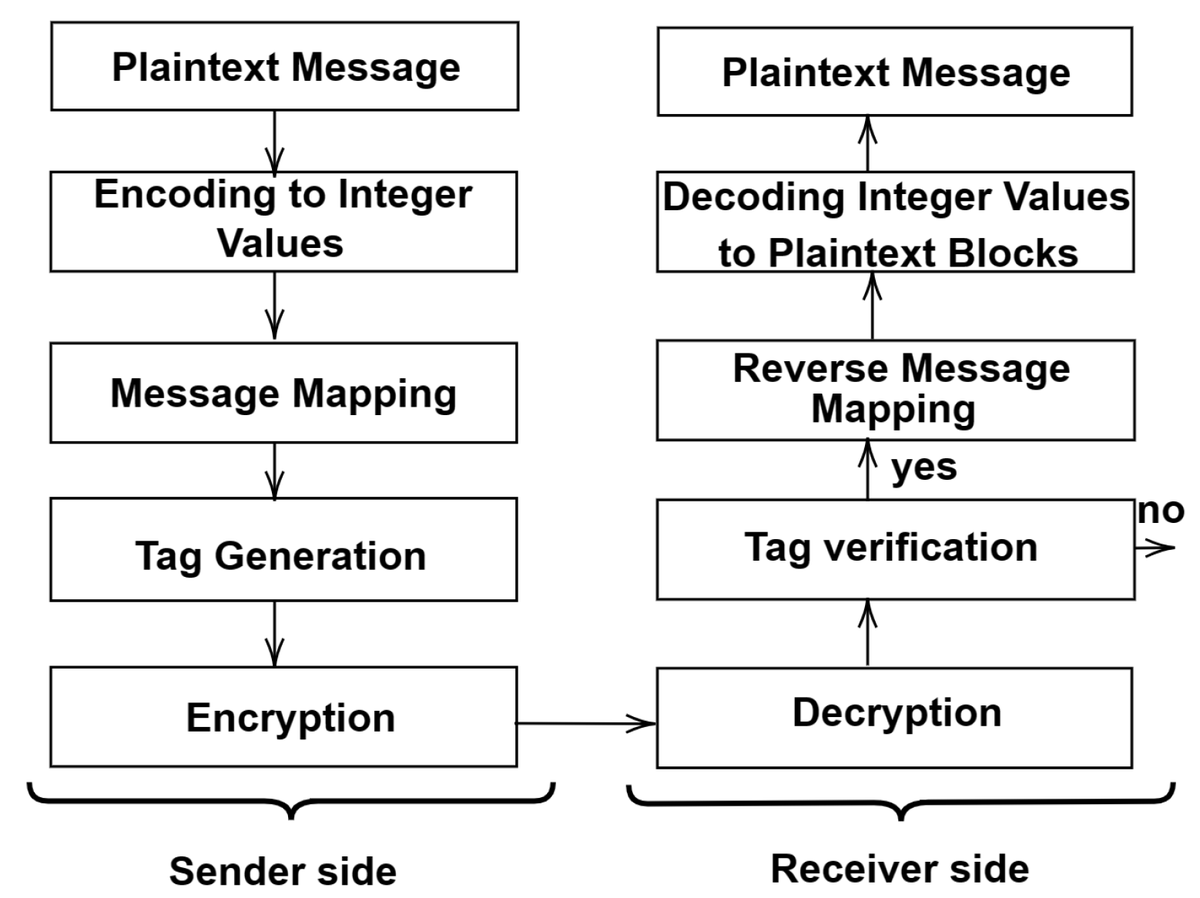
#Cryptography Securing Data Exchange with Elliptic Curve Cryptography: A Novel Hash-Based Method for Message Mapping and Integrity Assurance by Younes Lahraoui Saiida Lazaar Youssef Amal Abderrahmane Nitaj https://t.co/9HXvqz5cL1
#elliptic #curve #cryptography
#HashFunction
0
0
2
Our expert, Riley Dickens, shares all the crucial details you need to know about Hash Functions. https://t.co/czhhK8eNe6
#EncryptionConsulting #devops #hashing #hashfunction #codesigning #azuredevops #DigitalSignatures #codesigningcertificates #codesecurity #DevOpsSecurity
0
0
0
@0x9212ce55 Cones down to: - Is passphrase really strong? - Is hashing of the hashfunction to derive the private key strong? Here, some really SLOW hash function is needed. - And even both are yes - better safe than sorry
0
0
3
3042. Count Prefix and Suffix Pairs I - prefix and sufix can be found using slicing (l=len(w1), w2[:l]==w1 and w2[-l:]==w1) or inbuilt methods - feels like tricky part to how to limt the usage of nested loops to increase the time efficiency #DSA #Hashfunction #LeetCode
0
0
1
0
0
0
Can You Guess the Original Song! What are the Original Lyrics to the song below? 🎶Source Code, Everything about me’s so Source Code. You don’t even know what I’ve got, It’s really hitting the spot, Oh Macro. 😝👽👌🏾💕🎶 #hashfunction
1
0
0
#ePrint Xiaoyang Dong, Jian Guo, Shun Li, Phuong Pham, Tianyu Zhang, Improved Meet-in-the-Middle Nostradamus Attacks on AES-like Hashing (TOSC 2024) https://t.co/EEvb072QwB
#HashFunction #NostradamusAttack
0
0
0