Gerardo Fdez.
@gerardofn
Followers
790
Following
10K
Media
42
Statuses
12K
#malware #DFIR #Reversing Security Engineer @ VirusTotal
Benalmádena, Andalucía
Joined June 2009
The new VirusTotal plugin for IDA Pro now integrates Code Insight into your reversing workflow, allowing you to save and use relevant analyses to contextualize other functions. https://t.co/W79Be2Ulxj
0
4
8
Al final, la única forma de volver a casa era montar en un Renault Outsider. Uno de los mejores anuncios de los últimos años sirvió para rendir tributo a uno de nuestros más queridos recuerdos de infancia y para dar final épico a la legendaria serie animada DUNGEONS & DRAGONS.
35
144
702
New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution sample: https://t.co/m2AhDyZ2RK sample: https://t.co/s4LpEMBEQo c2: moodleuni[.]com
0
29
100
Awesome interview and showcase with Tim Blazytko about obfuscation and deobfuscation. https://t.co/HWvIvtbA9a
0
9
45
📣 Everything defenders need to know about UNC1549: a deep dive analysis of suspected Iran-nexus espionage targeting the aerospace, aviation, and defense industries in the Middle East. Dive into the details: https://t.co/N2KBeHdJ7z
1
50
112
Reverse Engineering WASM binaries, trace indirect calls, decode memory layouts https://t.co/f70XDu9cbZ
#WASM #ReverseEngineering #SecurityResearch
2
63
281
🎬 ¡Ya está disponible el aftermovie de Navaja Negra 2025! 🔥 Revive los mejores momentos, la energía del evento y todo lo que hizo especial esta edición. Pásate a verlo y comenta qué te pareció. 😎✨ #NN2025 🖤💛 https://t.co/NsUrEUk4Md
0
4
4
🔥 Stop switching tabs. Investigate in place. VT4Browsers is now powered by #GoogleThreatIntelligence! Get real-time threat context and a powerful investigation experience right in your browser. #GoogleTI #GoogleTIMondays #ThreatIntelligence #CyberSecurity
0
12
52
I am suggesting a new malware type: the browser remote access tool (BRAT) It's a form of browser hijacker that remotely controls your browser based on server commands. Typical form: press key combos for copy-pasting URLs, opening tabs, context menu, downloading files etc
11
25
174
💻Bypass NX on ARM64 and execute your shellcode using mprotect(). Check out the full blog here: https://t.co/3sUJJbmsqB
#ARM64 #Reversing #Exploitation
1
39
184
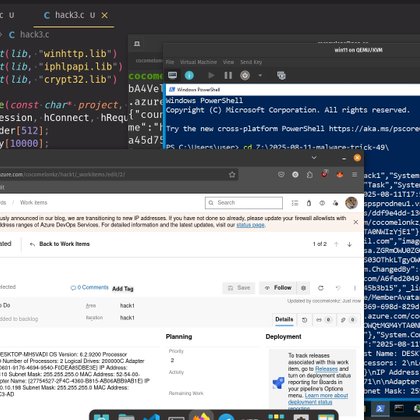
Malware development tricks, by @cocomelonckz 46 Windows keylogger https://t.co/9wUR8mBMBj 47 Windows clipboard hijacking https://t.co/LKebjdmDpr 48 leveraging Office macros https://t.co/F1x9odrdbT 49 abusing Azure DevOps REST API for covert data channels
cocomelonc.github.io
﷽
1
58
256
China: “IA para todos los niños, desde primaria.” Europa y España: “IA, sí… pero antes tres reglamentos, cinco informes, un sandbox y una multa preventiva.” Distintas prioridades, supongo.
4
5
35
🧠 Video Game Packet Encryption 🎩 Learn low-level function hooking to target the specific routines responsible for cryptography, dump the data before it gets encrypted. It's so simple it's stupid. 👉 https://t.co/jGOIZ1HfNL
0
20
122
My humble contribution to the Malware Analysis Community. Hope it helps ! Thanks @malcat4ever From WinWord to PureLogsStealer with @malcat4ever
#malcat #malware #purelogsstealer
https://t.co/7A0t8Vuk2G
prfalken.org
I recently had a suspiciously large attachment to analyze. After a few minutes, I discovered that the reason it was that big was because it was embedding a complete Python 3.10 environment. The...
2
13
67
The Agentic SOC is here. 🛡️Introducing the Alert Triage and Investigation Agent in Google SecOps (Public Preview). It autonomously investigates alerts, runs YARA-L queries, and applies @Mandiant expertise to deliver clear verdicts. See how it works: https://t.co/AOyqnFpYla
12
150
896
👑 How to Fuzz Windows Drivers 💥 Learn the dynamic analysis methodology necessary for actively testing kernel drivers, focusing on fuzzing IOCTL interfaces to uncover security vulnerabilities. 👉 https://t.co/aAztZTPRyl
0
28
171
Attention malware analysts 💻 Our latest blog post delves into Time Travel Debugging (TTD). We introduce the basics of WinDbg and TTD to help you start incorporating TTD into your analysis. 📄: https://t.co/07y5dniRy9
0
70
241
#ElasticSecurityLabs uncovers #RONINGLOADER, a multi-stage loader utilizing signed drivers, PPL abuse, CI Policies, and other evasion techniques to deliver #DragonBreath's gh0st RAT variant. Check it out at https://t.co/Df8JLO6w4d
0
57
201
For anyone who wants to understand certificates better and how to spot abuse, this is a great read (by @SquiblydooBlog ) https://t.co/55pMCg266s
2
28
96