Douglas Mun
@douglasmun
Followers
5K
Following
22K
Media
574
Statuses
49K
National Cyber Incident Response Expert | Former CISO & DPO | Vibe Coder
Singapore
Joined June 2012
“It is possible to unintentionally offend others, not necessarily due to an incorrect stance, but rather due to a difference in perspective.”
0
1
25
When I write techniques, I like to make diagrams. Here is the visualisation of the Folder Redirection (Bind Link) Technique that I posted earlier. 🖊️ Article: https://t.co/gBA3xCKMQi
📢 Bind Link - EDR Tampering 📖 1x Playbook 🚨 1x SIGMA Rule https://t.co/gBA3xCKMQi
1
25
141
SEQRITE Labs APT-Team tracks "Operation Hanoi Thief", a spear-phishing campaign targeting Vietnamese IT departments and HR recruiters with fake resume documents that deliver a C++ DLL stealer named LOTUSHARVEST. https://t.co/r1TjWFQwFJ
1
22
67
Interesting: these malware operators use Revolt (now Stoat) as a communication channel, I don't think I've seen that before 👁️ Indicator to keep in mind (this is the official API): api[.]revolt[.]chat
"security.exe": 8309a091cb7b8cdf496b696c7c0dd407e8c90bc1e9735c6845c9dc675506c5b3 Looks some usual, boring type malware sample... but one thing is different: instead of using Discord/Telegram/etc, as common these days, this sample is using Revolt/Stoat Chat for getting commands,
2
36
130
Police takes down Cryptomixer cryptocurrency mixing service - @serghei
https://t.co/Szj6NnPa3R
https://t.co/Szj6NnPa3R
bleepingcomputer.com
Law enforcement officers from Switzerland and Germany have taken down the Cryptomixer cryptocurrency-mixing service, believed to have helped cybercriminals launder stolen funds.
0
19
41
#APT36 Python Based ELF Malware Via spear-phishing emails with a ZIP archive containing a malicious .desktop file disguised as a document shortcut. Revised Malware Persistence Mechanisms in Linux (BOSS OS): Deploys a systemd user service in ~/.config/systemd/user/; enables via
1
35
132
A new RAT mobile malware called Albiriox has been exposed, targeting global finance and crypto wallets through the Google Play Store, operating as Malware-as-a-Service. #CyberSecurity #Malware
cleafy.com
Albiriox is a newly identified Android malware family offered as a Malware-as-a-Service, and enabling TAs to perform On-Device Fraud through remote control, screen manipulation, and real-time...
0
11
14
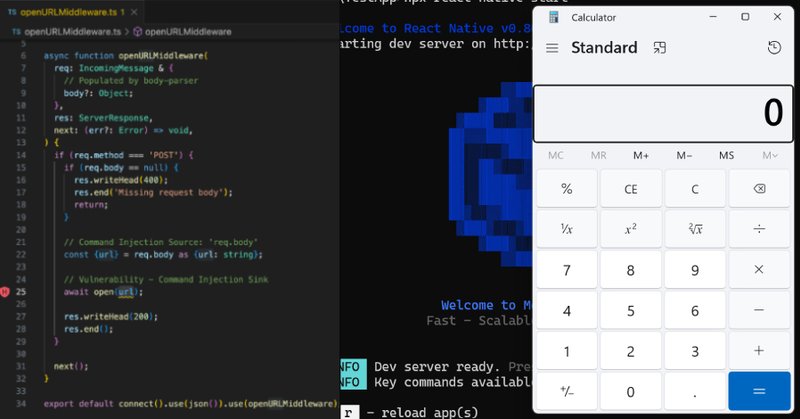
''Critical React Native CLI Flaw Exposed Millions of Developers to Remote Attacks'' #infosec #pentest #redteam #blueteam
https://t.co/js3v6B2Svh
thehackernews.com
A 9.8-severity flaw in React Native CLI let attackers run OS commands remotely before Meta’s patch.
1
7
15
AI slop security engineering: Okta's nextjs-0auth troubles @MegaManSec
https://t.co/6JfMyLQotv
joshua.hu
In October, I reported two security issues to Okta’s auth0/nextjs-auth0 project, here and here. The latter bug, an oauth parameter injection, allows for a range of types of abuse, like scoping tokens...
0
9
64
You don't necessarily need networking to connect to your Linux VM. No IP addresses. No SSH keys. No firewall rules. No routing tables. If you are on the same physical machine, TCP/IP can be just overhead. Meet AF_VSOCK. It’s a special address family in the Linux kernel
42
166
2K
Getting RCE on Brother printer (MFC-J1010DW) by chaining three vulnerabilities https://t.co/3ovzAezfgr Credits Nguyên Đăng Nguyên & Manzel Seet & Amos Ng (@starlabs_sg) #infosec
1
25
176
Someone used Elon Musk's actual thinking framework as AI prompts. It's the closest thing to having a billionaire engineer rip apart your ideas and rebuild them from physics. Here are the 15 prompts that changed how I solve problems:
94
645
5K
Opus 4.5 is insane. Just shipped v2 of my compounding engineering plugin—watch the video for my full thoughts on the model. Compounding engineering plugin v2: https://t.co/6LI5u1ZHTh This wouldn't have worked a week ago. Previous models would derail after the second parallel
22
59
869
This paper introduces a new memory system that lets AI agents research their own past on demand. AI agents create long chains of thoughts and tool calls that overflow the context window, so past information becomes hard to use. Most existing memories squash this history into
12
48
224
Great to see a new SOTSA for SWE-bench verified. The idea of using adversarial networks reminds me of GAN (Generative Adversarial Network) when it was invented for image generation, where two neural networks try to fool each other.
This is a super interesting paper on multi-agents for code patching. Claims SOTA on the SWE-bench Verified leaderboard (79.4%). Why this matters: Automated bug fixing is improving fast. But there's a catch. Patches that pass existing tests often fail on edge cases. The tests
1
1
1
SentinelOne warns that the Sha1-Hulud Worm 2.0 escalates NPM supply chain attacks by harvesting cloud credentials in the preinstall phase, urging immediate action to secure AWS, Azure, and GCP environments. #CyberSecurity #ThreatAlert
sentinelone.com
Learn about the actions required to defend against Shai-Hulud Worm 2.0 and how our real-time detection posture is securing your environment.
0
10
20
Inside the GitHub Infrastructure Powering #Lazarus’ Contagious Interview npm Attacks , Adding 197 malicious packages. Two brothers who are inseparable : OtterCookie and BeaverTail https://t.co/NLrMtZEKx1
#Lazarus carry out hands-on-keyboard activities for at least six consecutive hours, using compromised WordPress sites with vulnerable plugins as part of their attack infrastructure.#DreamJob
https://t.co/1ePt9XMVFt
1
14
66
OpenAI has been hacked. If you have used their API services, hackers may now possess your name, location, user ID, and other information.
153
1K
5K
Found a possible injection point, but WAF is preventing you from executing JS code? Time to obfuscate your payload! 🤠 JS-DOMestify is a simple tool that helps convert any JS code to browser-runnable code with only ASCII characters and minimal, non-intrusive symbols. 👀 Check
1
40
250