Curtis
@cybershtuff
Followers
471
Following
2K
Media
18
Statuses
184
Cloud, Incident Response, Threat Intelligence | ثريت انتل | OSINT | @InvictusIR | Previously U42 and PwC GTI
Joined June 2019
RT @InvictusIR: 💙Microsoft Extractor Suite v4 is here. 𝘜𝘱𝘥𝘢𝘵𝘦-𝘔𝘰𝘥𝘶𝘭𝘦 -𝘕𝘢𝘮𝘦 𝘔𝘪𝘤𝘳𝘰𝘴𝘰𝘧𝘵-𝘌𝘹𝘵𝘳𝘢𝘤𝘵𝘰𝘳-𝘚𝘶𝘪𝘵𝘦. Learn more about the new features in….
0
4
0
Pivoting on #UNC6148 infra (low confidence finds):. 149.248.76./220.195.85.115./143 -- takesurvey./online, carlads./online.168.100.9./181 -- wg-aff./website. The reverse shell IP (64.52.80./80) has some historical indicators of likely being used for EvilProxy phishing.
A financially motivated threat actor, #UNC6148, is targeting fully patched, end-of-life SonicWall SMA 100 appliances. In this latest activity, they deploy a new persistent backdoor we track as OVERSTEP. 🔗 Full details and defensive recommendations:
0
0
2
RT @InvictusIR: 🚨 Volume 3 | Profiling TradeTraitor (DPRK) 🚨 . Our latest and greatest blog in our series on Cloud Threat Actors. This one….
0
4
0
RT @ArmsControlWonk: Why am I so unimpressed by these strikes? Israel and the US have failed to target significant elements of Iran's nucle….
0
2K
0
🔍 Detect.Query Entra ID logs for Teams/1.3.00.30866 agent.Spot device-app mismatch & targeted app ID access. 🕵️ Investigate.Correlate w/ AWS IPs & spray patterns.Check post-comp activity (e.g. mailbox rules). 🛡️ Respond.Block IPs, revoke tokens, reset creds. #DFIR #ThreatHunting.
Researchers at @Proofpoint expose threat actors’ attempt to hijack thousands of EntraID user accounts across almost 100 cloud tenants by leveraging TeamFiltration, a red teaming framework used by network defenders.
0
1
3
Great writeup from Sekoia! @InvictusIR agrees: AiTM drives initial & credential access, fueling BEC 👉 🔎For IR, check Entra ID Sign-In, Identity Protection, & Unified Audit Logs. 🛡️Harden with passkeys & MFA for identity security. #DFIR #cloudsecurity.
📝 Our latest #TDR report delivers an in-depth analysis of Adversary-in-the-Middle (#AitM) #phishing threats - targeting Microsoft 365 and Google accounts - and their ecosystem. This report shares actionable intelligence to help analysts detect and investigate AitM phishing.
0
2
9
#CharmingKitten #APT42 #TA453 analysis & pivots. C2:.Telegram Bot used for error messages and auto-start messaging to the operator.computerlearning.ddns./net. Pivots:.bookstoragestore./com.lastfilterfile/.info.78.159.117./177.78.159.117./175.185.132.176./241.154.44.186./106.
Iranian threat group #AgentSerpens (#CharmingKitten) was observed likely using generative AI in a malicious PDF masquerading as a document from U.S. non-profit research organization, RAND. The PDF is deployed alongside Agent Serpens’ “PowerLess” malware.
1
1
14
RT @InvictusIR: Allright let's do this, a thread on Laundry Bear aka Void Blizzard. This group compromised the Dutch National Police. Let's….
0
26
0
Low confidence that this is likely a China-nexus threat actor. However, it's highly likely that the threat actor blended consumer (Linksys), industrial (Niagara 4), enterprise (Check Point Spark) assets to form covert infrastructure for staging and anonymizing their operations.
Commvault is monitoring cyber threat activity targeting its apps hosted in Microsoft Azure. Threat actors may have accessed application secrets, potentially impacting customers' M365 environments. Review our recommended mitigations here 👉 📷
1
0
0
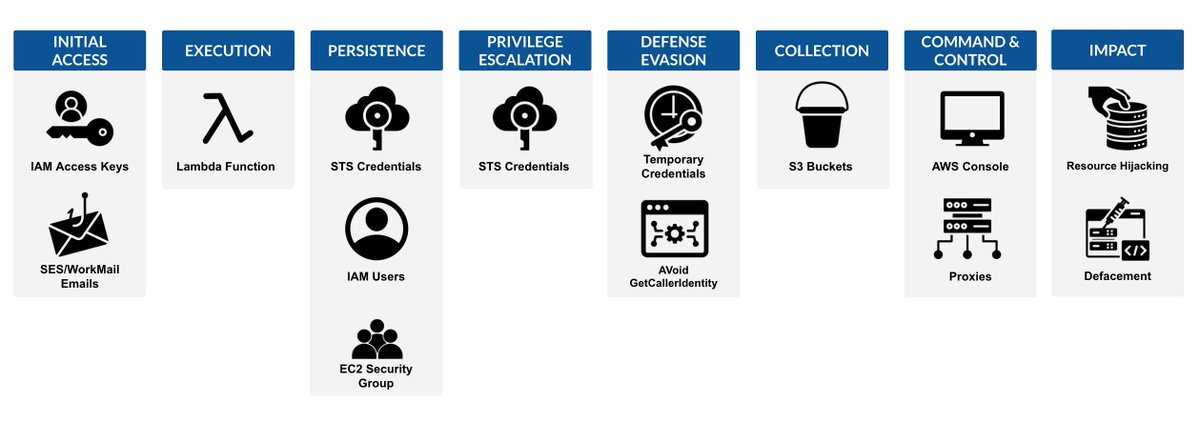
This isn’t recycled noise. It surfaces the often-overlooked details responders and CTI analysts actually need. Practical takeaways include:.✔️ Mapped TTPs.✔️ IR checklist.✔️ Actor context & relevancy. #CTI #CloudSecurity #AWS #DFIR #JavaGhost
We've started a new series on Cloud focused threat actors, today Part I on #JavaGhost. Check it out, if you want to learn how they operate, who they target and how you can defend against them. #stayInvictus #CloudIncidentResponse #JavaGhost.
0
0
3
🚨 New blog from @datadoghq on fresh AWS TTPs! Me and Team @InvictusIR pivoted & enriched their infra data to uncover the actor #JavaGhost is likely abusing callback proxy networks and leveraging Mass SMTP Tester. 🔗 #CloudSecurity #ThreatIntel #CTI.
securitylabs.datadoghq.com
A cloud attack targeting Amazon SES and persistence via AWS Lambda, AWS IAM Identity Center and AWS IAM
1
4
17
🔍 New Blog: Essential Cloud Logs for Incident Response. 🪵 Are you collecting the right logs for cloud security incidents? We break down the must-have logs to detect, investigate, and respond effectively in the cloud. 🔗 #dfir #aws #microsoft #google.
0
2
7
🚨 New Blog: Forensic Analysis of eM Client 🚨. If you investigate BEC incidents, you've likely seen eM Client pop up. We did a forensic deep dive to uncover the traces it leaves behind. #CyberSecurity #DFIR #BEC #ThreatIntel.
0
0
3
We’ve mapped the TTPs and shared actionable IOCs on our GitHub. 🛡️. 👉
github.com
Invictus Threat Intelligence: IOCs and TTPs from blogs, research and more - invictus-ir/IOCs
🔍 New BEC tactic observed. Step 1: Perform Adversary in the Middle testing to get access to someone's email. Step 2: Create a Dropbox Business account using email (no verification required). Step 3: Send files via Dropbox and WeTransfer to all email contacts. Step 4: When
0
0
3
RT @InvictusIR: If you're wondering how you can prepare for an incident in the cloud, our new blog is for you 🫵.
0
15
0