Sekoia.io
@sekoia_io
Followers
4K
Following
333
Media
231
Statuses
828
A #SOCplatform boosted by #AI and #threatintelligence, combining #SIEM, #SOAR, #Automation in a single solution. Used by End-users, MSSP and APIs
Paris, France
Joined September 2017
💡 Curious how the full infection chain works? We have broken it all down for you here 😈👇.
blog.sekoia.io
Discover how Lazarus leverages fake job sites in the ClickFake Interview campaign targeting crypto firms using the ClickFix tactic.
0
3
8
No OS left behind. It happily infects Windows, macOS, and Linux systems. Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
1
2
2
And everything is hosted on a single platform. At the end of the process, you're politely asked to download a 'driver' to magically make your webcam work ✨.Spoiler alert: it's not a driver, it's #GolangGhost, a custom malware with remote access capabilities.
1
2
2
🔥 Hot summer, sizzling crypto. and scammers turning up the heat 🔥. Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
1
9
23
You can find the phishing kit sheets on our blog: And on our Community GitHub:
blog.sekoia.io
Explore the 2025 landscape of Adversary-in-the-Middle phishing threats with data, trends, and top detection insights.
0
4
5
RT @crep1x: We are excited to share our latest blogpost on AitM phishing threats - covering common TTPs, the PhaaS ecosystem, the most wide….
0
10
0
We hope SOC, CERT and CTI teams find our global analysis of AitM phishing threats both insightful and actionable. Dive in here ⬇️.
blog.sekoia.io
Explore the 2025 landscape of Adversary-in-the-Middle phishing threats with data, trends, and top detection insights.
1
4
10
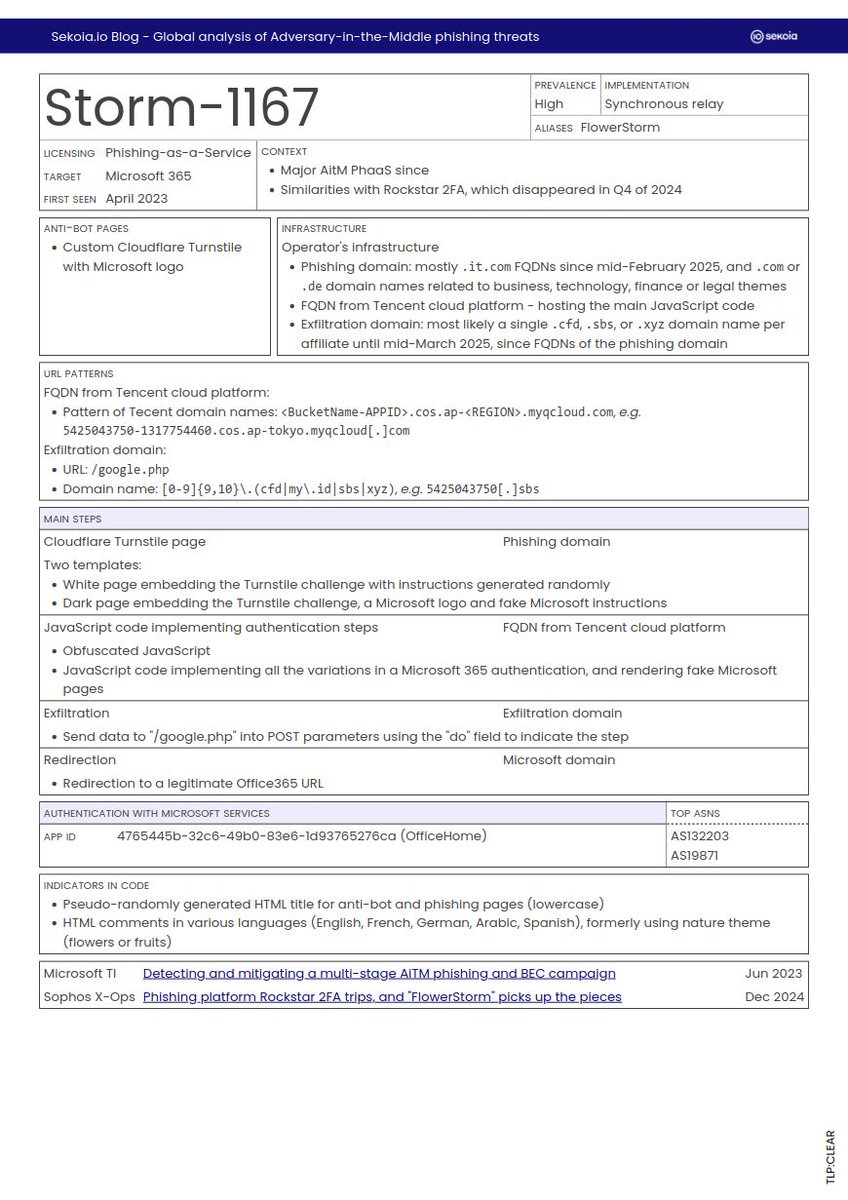
🎣 Leveraging our telemetry and proactive hunting, we ranked the most widespread AitM phishing kits - #Tycoon2FA, #Storm1167, #NakedPages, #Sneaky2FA, and more. Additionally, the article includes summary sheets covering 11 AitM phishing kits.
1
1
3
🔍 Phishing-as-a-Service (#PhaaS) is driving a wave of large-scale, sophisticated attacks against organisations. In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.
1
2
4
🪤 Sekoia #TDR's new exclusive research uncovers the #ViciousTrap, a honeypot network deployed on compromised edge devices.
blog.sekoia.io
Discover ViciousTrap, a newly identified threat who turning edge devices into honeypots en masse targeting
0
5
20
Our new report describes one of the latest observed infection chains (delivering #AsyncRAT) relying on the #Cloudflare tunnel infrastructure and the attacker’s #TTPs with a principal focus on detection opportunities.
1
14
40
Since the apparition of the #Interlock ransomware, the Sekoia #TDR team observed its operators evolving, improving their toolset (#LummaStealer #BerserkStealer), and leveraging new techniques such as #ClickFix to deploy the ransomware payload.
0
16
37