crep1x
@crep1x
Followers
3K
Following
1K
Media
170
Statuses
737
Lead cybercrime analyst, tracking adversaries activities & infrastructure, at @sekoia_io
Joined July 2012
RT @sekoia_io: These sheets aim to assist SOC analysts in detecting and investigating #AitM #phishing compromises by offering context, tech….
0
6
0
RT @sekoia_io: A few weeks ago, we published our global analysis of Adversary-in-the-Middle #phishing threats, providing actionable intelli….
0
22
0
As usual, your feedback is greatly appreciated. Enjoy the read and happy hunting!.
blog.sekoia.io
Explore the 2025 landscape of Adversary-in-the-Middle phishing threats with data, trends, and top detection insights.
1
1
6
We are excited to share our latest blogpost on AitM phishing threats - covering common TTPs, the PhaaS ecosystem, the most widespread kits, and multiple detection opportunities!. w/ @gregclermont.
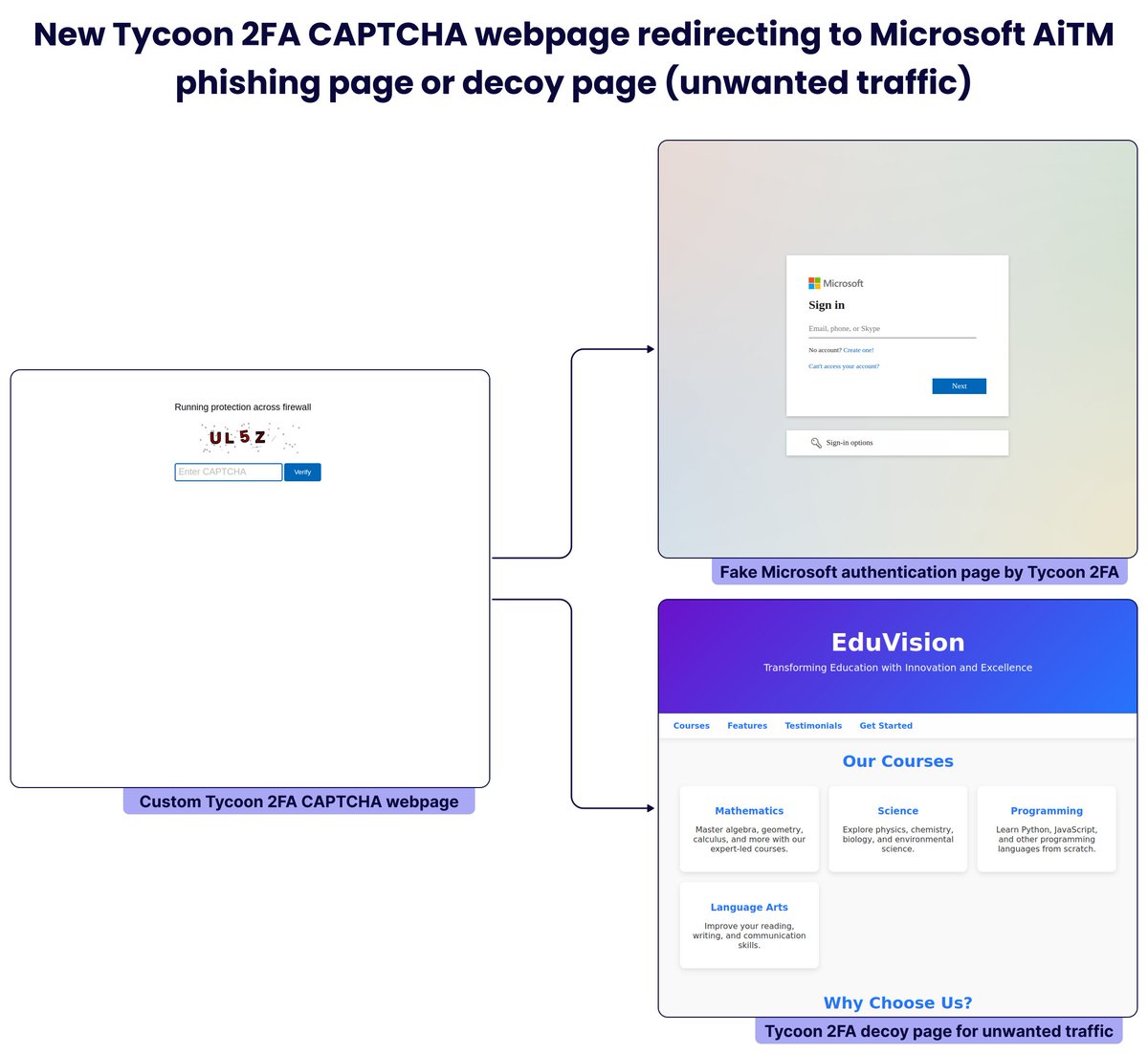
📝 Our latest #TDR report delivers an in-depth analysis of Adversary-in-the-Middle (#AitM) #phishing threats - targeting Microsoft 365 and Google accounts - and their ecosystem. This report shares actionable intelligence to help analysts detect and investigate AitM phishing.
1
10
47
RT @sekoia_io: We hope SOC, CERT and CTI teams find our global analysis of AitM phishing threats both insightful and actionable. Dive in h….
blog.sekoia.io
Explore the 2025 landscape of Adversary-in-the-Middle phishing threats with data, trends, and top detection insights.
0
4
0
RT @sekoia_io: 📝 Our latest #TDR report delivers an in-depth analysis of Adversary-in-the-Middle (#AitM) #phishing threats - targeting Micr….
0
28
0
RT @sekoia_io: 🪤 Sekoia #TDR's new exclusive research uncovers the #ViciousTrap, a honeypot network deployed on compromised edge devices.….
blog.sekoia.io
Discover ViciousTrap, a newly identified threat who turning edge devices into honeypots en masse targeting
0
5
0
RT @felixaime: Excited to see this paper finally published! Meet #ViciousTrap, a threat actor compromising and turning edge devices into ho….
blog.sekoia.io
Discover ViciousTrap, a newly identified threat who turning edge devices into honeypots en masse targeting
0
10
0
RT @sekoia_io: Our new report describes one of the latest observed infection chains (delivering #AsyncRAT) relying on the #Cloudflare tunne….
0
14
0
By the way, @MsftSecIntel published an analysis yesterday on the same infection chain leveraging new PowerShell loader/backdoor (without associating it with Interlock?) ⬇️.
microsoft.com
Since October 2024, Microsoft Defender Experts has observed and helped multiple customers address campaigns leveraging Node.js to deliver malware and other payloads that ultimately lead to informat...
1
1
5
Check out our new blog post by the TDR team, presenting the latest TTPs used by the #Interlock ransomware group!. It includes their use of the ClickFix tactic, PyInstaller, Node.js, Cloudflare Tunnels, and new PowerShell loader/backdoor ⬇️. ✍️ @KSeznec.
Since the apparition of the #Interlock ransomware, the Sekoia #TDR team observed its operators evolving, improving their toolset (#LummaStealer #BerserkStealer), and leveraging new techniques such as #ClickFix to deploy the ransomware payload.
3
8
25
RT @sekoia_io: Since the apparition of the #Interlock ransomware, the Sekoia #TDR team observed its operators evolving, improving their too….
0
16
0
Here is our in-depth analysis of the latest #ClearFake variant using the Binance Smart Chain and two new ClickFix lures. ClearFake is injected into thousands of compromised sites to distribute the #Emmental Loader, #Lumma, #Rhadamanthys, and #Vidar. ⬇️.
TDR analysts published an analysis of the new #ClearFake variant that relies on compromised websites injected with the malicious JavaScript framework, the #EtherHiding technique, and the #ClickFix social engineering tactic.
1
4
24
RT @sekoia_io: TDR analysts published an analysis of the new #ClearFake variant that relies on compromised websites injected with the malic….
0
32
0