Takahiro Haruyama
@cci_forensics
Followers
3K
Following
881
Media
155
Statuses
5K
Due to some missing links on the conference web pages, I uploaded my conference talk pdfs for 10 years. Time flies.
1
30
106
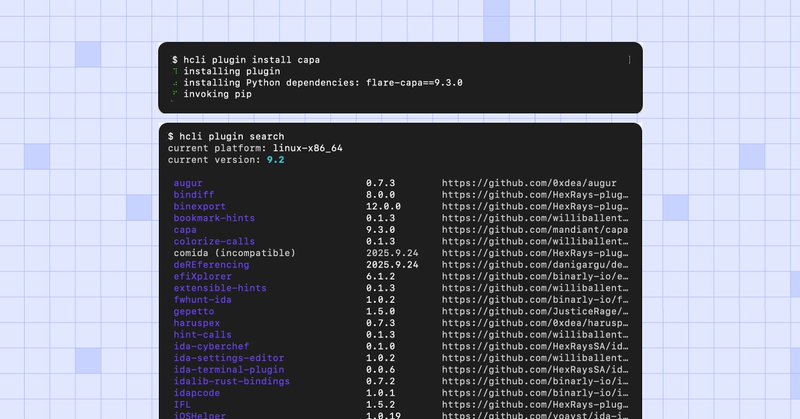
IDA has a plugin manager now! I hope this makes it so much easier for you to try new extensions, like after the Plugin Contest. https://t.co/Ldksfu9l4n
hex-rays.com
Meet the new IDA Plugin Manager - a modern, self-service ecosystem that makes extending IDA as simple as inputting a few key commands.
1
19
60
⌨️ Introducing HCLI: The Modern Command-Line Interface for IDA. Automate workflows, simplify plugin development across platforms, manage licenses and more. https://t.co/1PWeVZmePY
0
48
132
🚨BREAKING: We uncovered LANDFALL — a commercial-grade Android spyware exploiting a now-patched Samsung zero-day (CVE-2025-21042) through weaponized DNG images sent via WhatsApp, enabling zero-click compromise of Samsung Galaxy devices. 1/ https://t.co/hfTFP1MMX2
unit42.paloaltonetworks.com
Commercial-grade LANDFALL spyware exploits CVE-2025-21042 in Samsung Android’s image processing library. The spyware was embedded in malicious DNG files.
3
60
151
I built a program analysis tool which identifies cryptographic algorithms in Java bytecode and wrote about it. Core logic backed by Joern and Code Property Graphs. Hat tip for the great tech @fabsx00, and shout-out to @xorpse and @yeggorv for the support
🚀 New Release: Cryptographic Algorithm Identification in Java Bytecode. Our new analyzer scans JARs (and soon Android packages) to uncover algorithm usage, provide reachability insights, and report NIST 8457 compliance. Dive into the details:
0
6
13
🚀 New Release: Cryptographic Algorithm Identification in Java Bytecode. Our new analyzer scans JARs (and soon Android packages) to uncover algorithm usage, provide reachability insights, and report NIST 8457 compliance. Dive into the details:
binarly.io
Cryptographic algorithms protect critical properties of modern software. With the potential danger posed by the advent of quantum computers, it has become more important for companies to identify...
0
18
61
Looks like VirusTotal was added to Hugging Face’s scanning system
0
0
2
For the built-in scanner Protect AI of Hugging Face — is its scanning interval very long? This model file was uploaded more than ten days ago, but it still hasn’t been scanned.
0
0
2
⚡️UEFI system firmware still has a mitigation gap, and we measured it. We scanned 5,477 firmware images covering 2.3M+ UEFI modules with the Binarly Transparency Platform. The results are… 🔥 🧵👇 https://t.co/pZJbbgE2GV
binarly.io
Software mitigations play a critical role in the quest to secure the digital world. Shortly after the discovery and the rise of buffer overflows in the 90s, mitigations were introduced in the...
1
12
19
⚠️ Clevo’s UEFI firmware update packages accidentally exposed Intel Boot Guard private keys, breaking the root of trust and enabling potential malicious firmware signing. 💥VU#538470: https://t.co/4EKWkzUWA2 💥More Details: https://t.co/t0H9WjK0Do
1
14
23
Just got back from @osfc_io and @UEFIForum DevCon! Here’s a quick thread on our @binarly_io contributions and a few of my favorite presentations🧵
1
7
12
NtDoc has been updated with definitions and documentation from the official Windows Driver Kit DDI reference and portions of the Win32 API reference. This update reduces the need to switch between NtDoc and Microsoft Docs, addressing one of the most common suggestions for NtDoc.
It's common knowledge that the best source for Windows native API definitions is the collection of System Informer (formerly Process Hacker) phnt headers. Surprisingly, there were no online docs for them, so I created a simple website: https://t.co/WHU55QVZQl
0
2
16
Had a blast attending and presenting at @labscon_io for the second year in a row! If you are curious about BYOVD in UEFI, and how we at @binarly_io uncovered an incomplete patch for a Supermicro BMC bug, check out our talk slides below👇
1
15
26
他のBriefingsの発表紹介は下記の発表をまとめました - Machine Check 例外による ring 0 → ring -2 権限昇格 - BYOVB(ootloader)可能なセキュアブートバイパスの脆弱性 - BitUnlocker. Windows リカバリーの脆弱性を使って Bitlocker をバイパス
今回のエンジニアブログは Black Hat USA 2025 の登壇報告になります。 今年は中川と松尾の 2 名がそれぞれ Briefings へ登壇しましたが、まずは松尾の報告になります。 登壇経緯、当日の感想に加え、いくつかの発表をご紹介します。#ffri_research #uefi
0
2
0
🚨Binarly REsearchers revisit an already-patched Supermicro BMC bug and discover two new high-impact vulnerabilities that expose major gaps in software supply chains. CVE-2025-7937: bypassed “fix” for CVE-2024-10237. CVE-2025-6198: Supermicro RoT bypass. https://t.co/AkLhM9Z5SU
binarly.io
In a previous blog post, we detailed three Supermicro BMC firmware vulnerabilities that were originally found by the NVIDIA Offensive Security Research Team and disclosed earlier this year. All these...
2
21
76
#ESETresearch has discovered #HybridPetya ransomware on VirusTotal: a UEFI-compatible copycat of the infamous Petya/NotPetya malware. HybridPetya is capable of bypassing UEFI Secure Boot on outdated systems. @smolar_m
https://t.co/UQAcC4O3Pu 1/8
welivesecurity.com
ESET Research has discovered HybridPetya, a copycat of the infamous Petya/NotPetya malware that adds the capability of compromising UEFI-based systems and weaponizing CVE‑2024‑7344 to bypass UEFI...
2
67
148
🔐BYOVD, but in firmware. Signed UEFI shells, vulnerable modules offer new paths for Secure Boot bypasses. Read the latest REsearch from @pagabuc and @yeggorv on the fragile foundation of UEFI ecosystem. https://t.co/13b6KKIIwd
2
21
46
Rustで作成されたバイナリのリバースエンジニアリングに関するレポートを公開しました。 レポートはGitHubリポジトリにて公開されているため、そちらもご覧ください。^TK https://t.co/KtifXsQzqu
https://t.co/VFffIHthR6
github.com
Rustで作成されたバイナリのリバースエンジニアリング調査レポート. Contribute to JPCERTCC/rust-binary-analysis-research-ja development by creating an account on GitHub.
0
46
114
QUANTUMSTRAND beta 1 released: built for analysts to quickly understand *where* strings are, *what* they might be, and *how* important they are, without getting lost in a sea of undifferentiated text. Thanks @m_r_tz and the crew at @Mandiant FLARE https://t.co/IKMi5fNM13
2
37
108
#ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/6
56
674
3K