Dana Behling
@DanaBehling
Followers
75
Following
127
Media
0
Statuses
27
Experienced Malware Reverse Engineer | Senior Threat Researcher | Cyber Security Specialist | Expert in Analyzing and Mitigating Complex Threats
Texas
Joined May 2022
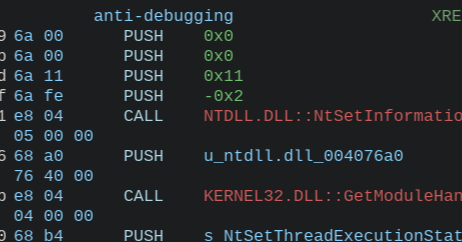
I’ve been building out the Windows API Abuse Atlas, a project I started to document how lesser-known Windows APIs are abused by attackers. The latest entry breaks down NtSetInformationThread and its use in anti-debugging. Also looking for my next role.
linkedin.com
🚀 Executive Summary NtSetInformationThread is one of those quietly powerful tricks malware uses to mess with how threads behave—usually to stay hidden from debuggers or security tools. Even though...
0
1
1
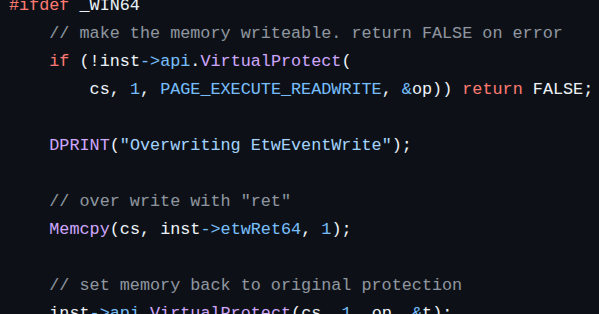
Check out my latest article: 🚩 EtwEventWrite Patching: One Way Attackers Blind Windows Defenders 🚩 via @LinkedIn.
linkedin.com
🧪 EtwEventWrite Patching 🚀 Executive Summary EtwEventWrite patching is a long-running and reliable tactic used by attackers to quietly turn off telemetry that defenders rely on. By patching or...
0
2
4
RT @jukelennings: Someone is using Evilginx to target customers of Onfido, part of Entrust, with a malicious Google advert that comes above….
0
17
0
RT @vinopaljiri: New CP<r> research is out! 😊.Breaking Boundaries: Investigating Vulnerable Drivers and Mitigating Risks 🔎. Very excited ab….
0
8
0
RT @threatintel: RansomHub has quickly grown to become one of the largest ransomware operations mounting attacks. Find out why. https://t.c….
0
8
0
RT @BSidesCharm: Embark on an epic journey with @DanaBehling in "The Fellowship of the Ring0" to identify vulnerable drivers and quickly &….
0
6
0
So excited!.
Embark on an epic journey with @DanaBehling in "The Fellowship of the Ring0" to identify vulnerable drivers and quickly & accurately determine the risk that a device driver creates by either having built-in vulnerabilities or malicious behavior.
0
1
2
Hunting Vulnerable Kernel Drivers . Awesome work with excellent detail on how to find vulnerabilities in Windows drivers.
blogs.vmware.com
In information security, even seemingly insignificant issues could pose a significant threat. One notable vector of attack is through device drivers used by legitimate software developers. There are...
0
0
2
RT @virusbtn: Last week VMware researchers wrote about LummaStealer, a Malware-as-a-Service (MaaS) that is sold widely across numerous Dark….
0
32
0
RT @M_haggis: 🚀 Introducing ⭐️LOLDrivers 2.0 ⭐️! .A milestone release that enhances user experience, threat detection, and much more. Check….
medium.com
Introducing LOLDrivers 2.0: A significant milestone that refines the user experience and expands upon our comprehensive threat detection…
0
101
0
RT @bbaskin: I'm extremely excited to present at Black Hat Arsenal the new rewrite and upgrades to Noriben. I last presented it there *8* y….
0
14
0
RT @BSidesSATX: Starting at 2pm on 6/10, we have Dana Behling w/"Driving Your Own Vulnerability: How to Navigate the Road of BYOD Attacks",….
0
4
0
RT @infosecb: I’m excited to kick the morning off by announcing the release of 🍎 Living Off the Orchard: macOS Binaries (LOOBins)!. https:/….
infosecb.medium.com
Announcing the release of LOOBins, a new living off the land open-source project.
0
181
0
RT @yarden_shafir: 170 of the drivers load with the most recent HVCI driver blocklist. Do with this information wha….
0
82
0