Arris Huijgen
@bitsadmin
Followers
2K
Following
266
Media
42
Statuses
238
Windows Offensive Security Enthusiast 🤠 Blog: https://t.co/CAwdjs2rKS GitHub: https://t.co/YG2YOxfosm
Amsterdam, The Netherlands
Joined March 2016
Many more examples are in the CHEATSHEET at https://t.co/Bngi8ZEVFC or use the Get-Help/man command followed by the cmdlet, e.g. man iwr. Regularly new cmdlets are added in NoPowerShell's DEV branch so keep an eye there to get the latest and greatest! 🔥 https://t.co/1jlgmhJ4Ks
1
0
3
🔎 Inspecting ACLs and file hashes using the Get-Acl and Get-FileHash cmdlets.
1
0
1
📡 To accomplish persistence, creating a shortcut in the Startup folder using the (unofficial) New-Shortcut cmdlet.
1
0
1
🛜 Checking IP configuration and testing routing using Get-NetIPAddress and Test-NetConnection. 🔐 Checking TLS certificate chain details using Invoke-WebRequest.
1
0
1
🗄️ Running queries on Microsoft SQL Server using the Invoke-Sqlcmd cmdlet.
1
0
1
💻 User/session reconnaissance, on both the local as well as remote machines using the Get-LocalUser and Get-WinStation (unofficial) cmdlet. 📄 Hunting for authentication details of a specific user in the DC Security event log using Get-WinEvent.
1
0
1
Because the last release of #NoPowerShell was 2 years ago and to celebrate the repo has 999 stars, I just merged DEV ➡️ MASTER and published Release 1.50 containing over 60 offensive cmdlets! 🥳 https://t.co/dBOcwRPgSw See examples of some of the cmdlets below 👇
github.com
PowerShell rebuilt in C# for Red Teaming purposes. Contribute to bitsadmin/nopowershell development by creating an account on GitHub.
1
46
141
[Research] Starting Chrome Exploitation with Type Confusion 101 ^-^☆ Part 1.(EN) https://t.co/ohHvknIIr1 Ever wondered how Chrome's V8 engine actually runs JavaScript, and how those internals can lead to security issues like Type Confusion? In this post, I break down the V8
0
41
140
🚀 We just released my research on BadSuccessor - a new unpatched Active Directory privilege escalation vulnerability It allows compromising any user in AD, it works with the default config, and.. Microsoft currently won't fix it 🤷♂️ Read Here - https://t.co/c969sNjQH0
21
373
876
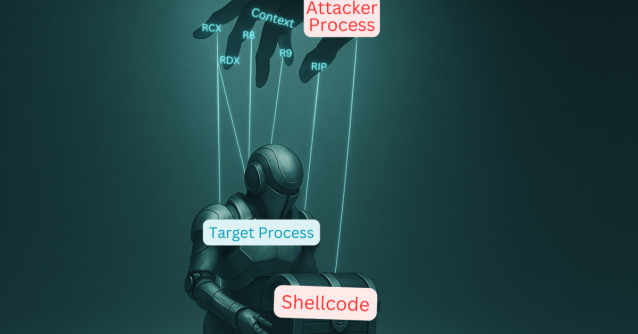
What if you skipped VirtualAlloc, skipped WriteProcessMemory and still got code execution? We explored process injection using nothing but thread context. Full write-up + PoCs: https://t.co/Sa1oUSYyqU
blog.fndsec.net
What happens when you skip memory allocation, skip writing, and weaponize thread context alone? This post explores a new class of process injection that lives entirely in the execution layer — no a…
6
78
222
Blogpost from my colleague about what’s still possible with recently published COM/DCOM toolings, Cross Session Activation and Kerberos relaying 🔥 https://t.co/ggXWsw9ZE8
r-tec.net
This blog post will dive into the world of some of the recently published potato techniques that can lead to more serious risks than
3
112
307
ProxyBlob is alive ! We’ve open-sourced our stealthy reverse SOCKS proxy over Azure Blob Storage that can help you operate in restricted environments 🔒 🌐 https://t.co/KO4AYUDTmb Blog post for more details right below ⬇️
github.com
SOCKS5 proxy tool that uses Azure Blob Storage as a means of communication. - quarkslab/proxyblob
Look at those cute little blobs in your internal network. They look harmless, but how about the one carrying SOCKS? It's ProxyBlob, a reverse proxy over Azure. Check out @_atsika's article on how it came to exist after an assumed breach mission ⤵️ 👉 https://t.co/ApZloWD3hl
3
45
112
Cool, novel, lateral movement technique by @william_knows by dropping a .dll file on a remote host obtaining code execution! 💡
0
23
155
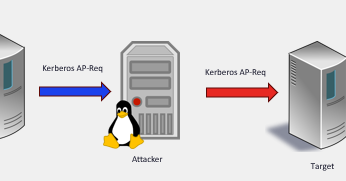
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️ https://t.co/OztMeuoU5L
decoder.cloud
While I was reading Elad Shamir recent excellent post about NTLM relay attacks, I decided to contribute a companion piece that dives into the mechanics of Kerberos relays, offering an analysis and …
2
150
351
The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP. By @Defte_ Writeup: https://t.co/NpKZCmPgdY PR to impacket: https://t.co/Fr8S5HoCbd Demo:
github.com
This PR adds a new relay capability allowing us to relay SMB/LDAP/HTTP NTLM (v1 or unsecured ones) authentications to the WinRM HTTPS endpoint. This endpoint is not configured on a default server i...
1
44
120
We’re glad to announce we released Soxy!🚀 A Rust-powered suite of services for Citrix, VMware Horizon & Windows RDP. Red teams & pentesters can use it to pivot for deeper access. Get the tool and more details: 🔗
github.com
A suite of services (SOCKS, FTP, shell, etc.) over Citrix, VMware Horizon and native Windows RDP virtual channels. - airbus-seclab/soxy
0
61
148
Your laptop was stolen. It’s running Windows 11, fully up-to-date, device encryption (BitLocker) and Secure Boot enabled. Your data is safe, right? Think again! This software-only attack grabs your encryption key. Following up on our #38C3 talk:
neodyme.io
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only
2
29
86
How to bypass BitLocker encryption on Windows 11
noinitrd.github.io
Memory-Dump-UEFI is a UEFI application for dumping the contents of RAM.
0
43
173
Just released SCCMHound! A BloodHound collector for SCCM. SCCMHound allows both attackers and defenders to construct BloodHound datasets using the vast amount of information that is stored/retrievable through SCCM. Feel free to take it for a spin! https://t.co/3J1IjEfDmO
0
102
344