ARPSyndicate - Cyber & Open Source Intelligence
@arpsyndicate
Followers
527
Following
2K
Media
51
Statuses
1K
A Global Cyber Intelligence Company with hyperspecialization in Information Discovery, Shadow IT & Vulnerability Intelligence
India
Joined November 2023
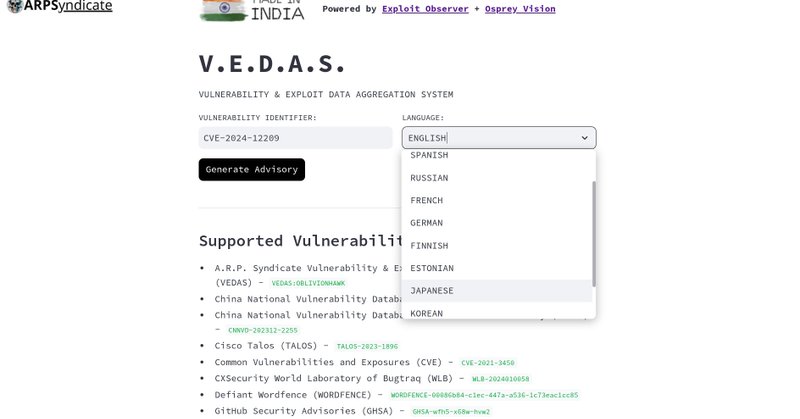
Vulnerability & Exploit Data Aggregation System (VEDAS) is the World's First Automated Advisory Generation Platform that can aggregate and comprehend Vulnerability / Exploit Intelligence, powered by Osprey Vision & Exploit Observer.
vedas.arpsyndicate.io
Vulnerability & Exploit Data Aggregation System (VEDAS) is the World's First Automated Advisory Generation Platform that can aggregate and comprehend Vulnerability / Exploit Intelligence, powered by...
6
57
390
RT @_l0gg: Blog for ToolShell.Disclaimer: The content of this blog is provided for educational and informational purposes only. https://t.c….
0
82
0
RT @HunterMapping: 🚨Alert🚨 :CVE-2025-2775&CVE-2025-2776&CVE-2025-2777 : Three Unauthenticated XML External Entity (XXE) Vulnerabilities in….
0
26
0
RT @assetnote: Sometimes, SQL injection is still possible, even when prepared statements are being used. Our researcher @hash_kitten has wr….
slcyber.io
Searchlight Cyber's Security Research team details a Novel Technique for SQL Injection in PDO's Prepared Statements.
0
77
0
RT @StartupArchive_: Elon Musk explains his 5-step algorithm for running companies. “First, make your requirements less dumb. Your requirem….
0
618
0
RT @theluemmel: If you want to quickly evaluate if you are exploitable:.
github.com
Contribute to LuemmelSec/Pentest-Tools-Collection development by creating an account on GitHub.
0
57
0
RT @deedydas: 🚨 BREAKING: Detailed list of all 44 people in Meta's Superintelligence team. — 50% from China.— 75% have PhDs, 70% Researche….
0
4K
0
RT @isox_xx: Sales team will kill me later. I've published Vulners GPT linked to the unlimited OEM API key. Free for all. Including priv….
chatgpt.com
Vulners Assistant — your live vulnerability radar. Ask for today’s hottest CVEs, search exploits or audit any software version, all powered in real-time by Vulners’ threat intelligence. Absolutely...
0
2
0
RT @akaclandestine: Bruteforcing the phone number of any Google user
brutecat.com
From rate limits to no limits: How IPv6's massive address space and a crafty botguard bypass left every Google user's phone number vulnerable
0
9
0
RT @intigriti: 3 Easy-to-exploit vulnerabilities that often receive HUGE bounties! 🤑 . A thread! 🧵👇
0
56
0
RT @deedydas: Really awkward timing on this post. 12hrs after posting, OpenAI pulled off something amazing by getting the gold on IMO 20….
0
33
0
RT @CyversAlerts: Our system has detected a hack into @CoinDCX centralized exchange 20 hours ago. Here's what we know:.- The hacker stole….
0
36
0
RT @midwestneil: Turns out you can just hack any train in the USA and take control over the brakes. This is CVE-2025-1727 and it took me 12….
0
561
0
RT @kmkz_security: It seems that someone at @opzero_en (not @0xPetitoto) wrote a write-up 👌🏻. Thank u guys !.
opzero.ru
This will be an introductory course to exploiting browsers. Not just covering a few JIT bugs and common renderer process exploits, we'll take an in-depth look at the entire browser structure,...
0
12
0
RT @Bugcrowd: If you're analyzing or breaking mobile apps, you need Frida in your toolkit. Frida is a dynamic instrumentation toolkit used….
0
5
0