Alberto
@__ar0d__
Followers
454
Following
3K
Media
23
Statuses
721
Infosec | Tech | Entrepreneur 👋. https://t.co/NipeaWw1t2 | https://t.co/7MkpQbduIo
In the Ether
Joined August 2019
🔥🔥🔥
Stop testing in prod (even someone else's)! Are you tired of installing Active Directory on your test VMs for the 100th time? Ever YOLO a binary off GitHub into prod because your testing setup is tedious? I've built a solution: https://t.co/HvzjwZLiwr (1/5)
0
0
3
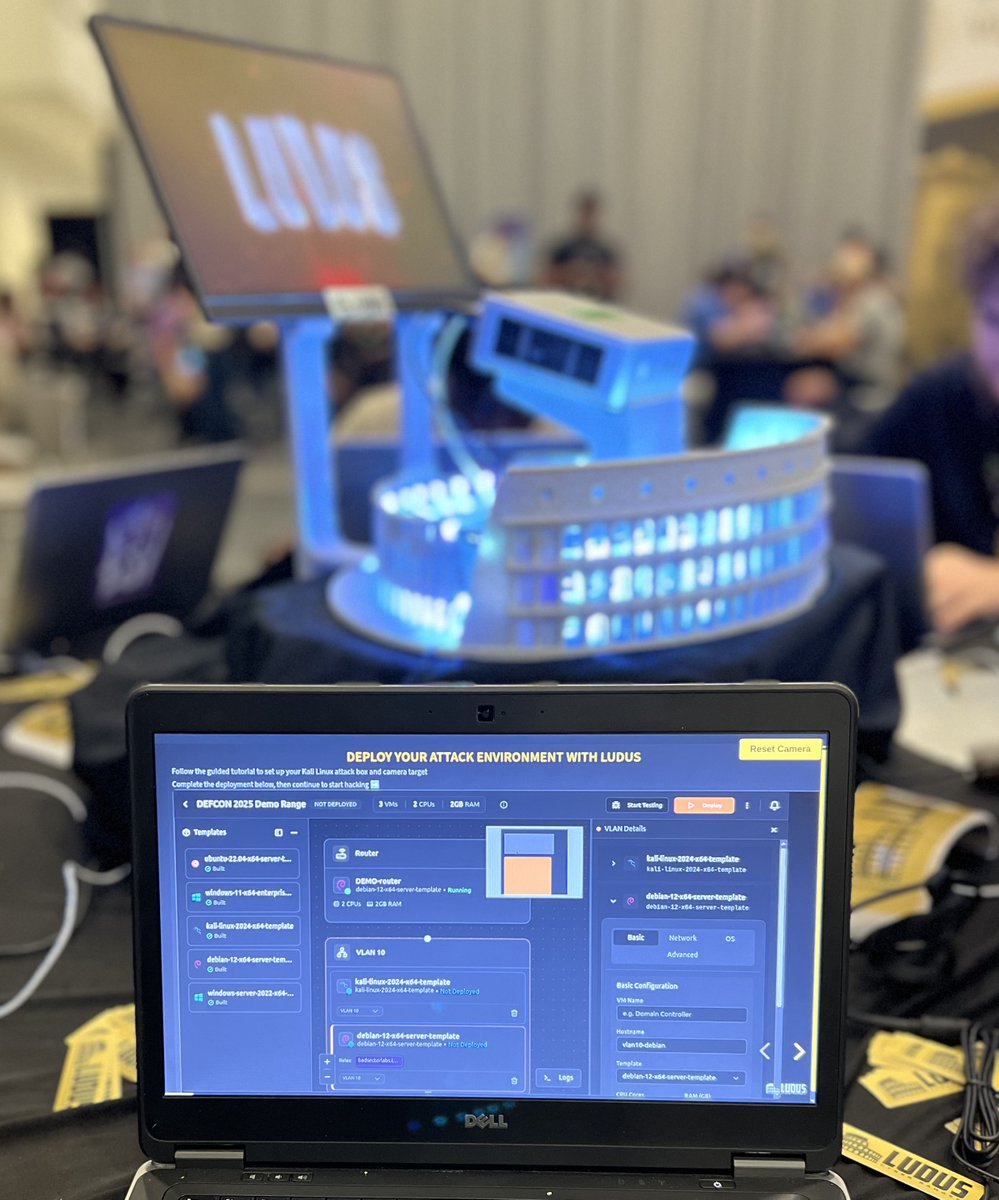
Come see a preview of the new Web UI for 🏟️Ludus at the Embedded Systems Village. Our mini-workshop walks you through deploying a range and then hacking an emulated IP camera.
6
3
42
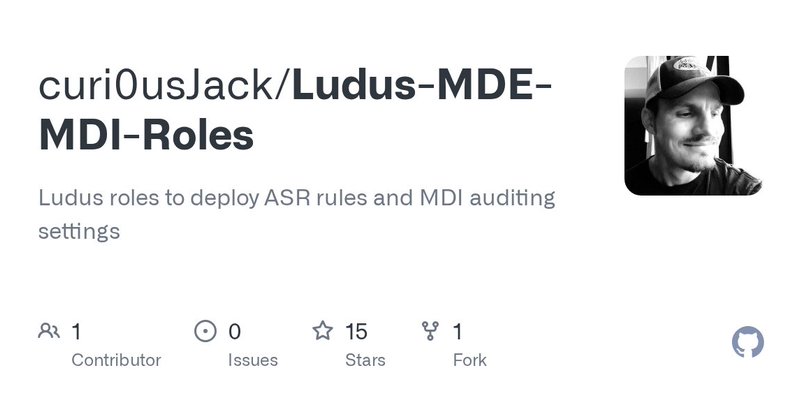
Created two new ansible roles for @badsectorlabs's Ludus that enable ASR rules and create/link the recommended audit GPOs for an MDI rollout. It's all simple powershell, so would work for AutomatedLabs as well (see tasks/main.yml) https://t.co/iofcF5jiSn
github.com
Ludus roles to deploy ASR rules and MDI auditing settings - curi0usJack/Ludus-MDE-MDI-Roles
3
31
112
I been working on GOAD. I installed @badsectorlabs Ludus and loving it. This will be fun and making videos soon on my new journey with GOAD. #Hacking #Pentesting #GOAD #Monday #Kali #Exegol #infosecurity #CyberSecurity
3
6
81
Can’t wait to try it out! Good work dude 🔥
I've recently released an MCP server for controlling your #Ludus lab or making range config files using natural language with an LLM. If you use Ludus for you cyber ranges give it a spin. https://t.co/l2blJOh2JX If you aren't using Ludus, check it out from: @badsectorlabs
0
0
1
Ludushound shows the power of community driven innovation in cybersecurity. @bagelByt3s created an awesome tool to convert bloodhound data into a working lab in 🏟️ Ludus. Replicate complex live environments with automation - and get back to the fun stuff! https://t.co/19qfjRwaOA
specterops.io
LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing.
1
90
263
This is 🔥 🔥 🔥 LESS AND LESS excuses on why you can’t test before YOLOing in your client network. Amazing work Beyviel 👏 @SpecterOps
https://t.co/3fhcaam8es
specterops.io
LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing.
0
20
86
😂 this is the way
0
0
1
Lots of good write ups (like Citrix Bleed 2) but my favorite was seeing how 🏟️ https://t.co/SFqewEhKSU helped Cameron Stish of Guidepoint Security find "LoopyTicket" (CVE-2025-33073). https://t.co/OVpVpVIXCG
blog.badsectorlabs.com
Lenovo Applocker bypass (@Oddvarmoe), Citrix Bleed 2 (@SinSinology, @inkmoro, Aliz Hammond), A+ adversary simulation (@quarkslab), DreamWalkers loader (@max2cbx), SigStrike (@rushter), and more!
1
5
25
This week's edition is packed full of great techniques and tools! One of the longest posts we've done; there's so much cool stuff being released. https://t.co/Z9LbRXMbQd
blog.badsectorlabs.com
Windows self-delete on 24H2 (@TKYNSEC), DNS rebinding (@yarlob), VSCode backdoor (@d1rkmtr), leak Google users' 📞# (@brutecat), Entra sync dumping (@hotnops), Delegations (@podalirius_), Chrome...
0
9
18
Cobalt Strike for free!? Adaptix C2 (@hacker_ralf) is the best open source C2 I've used since Havoc (@C5pider). SOCKS5, remote and local port forwards, and BOF support! Now it's easy to install the server + client, especially on 🏟️Ludus with our new role: https://t.co/3dvR7brHwR
1
83
379
WinRMS relay (@Defte_), plaintext Zip attacks (@pfiatde), SQL Server Crypto deep dive (@_xpn_), and more!
blog.badsectorlabs.com
WinRMS relay (@Defte_), plaintext Zip attacks (@pfiatde), SQL Server Crypto deep dive (@_xpn_), FindUnusualSessions (@podalirius_), and more!
0
12
33
2 weeks worth of news, techniques, tools and exploits!
blog.badsectorlabs.com
2 weeks worth of news, techniques, tools and exploits!
0
7
14
Happy to see that @frack113 added an Ansible role for our Aurora agent in Ludus Ludus https://t.co/EaMyjUQHPj Ludus Roles https://t.co/6b0cDEAG4h
https://t.co/yaEVhGarlk Aurora Agent (free) https://t.co/36uW88lEyP
0
12
36
Last week, we asked Devin to make a change. It added an event on the banner component mount, which caused 6.6M @posthog events in one week, which will cost us $733 Devin cost $500 + $733 = $1273 😢👍 Lesson - Review AI-generated code multiple times
127
177
3K
I’m building incredibly in-depth course work for Command and Control operations as well as detection engineering. This is NOT entry level. Live instruction + lifetime access to materials. Until it launches, once a week I will give away access to someone who retweets and follows
6
61
162
Sick! 🔥
Here we have it, part 2 of my NUC stack series, with input from @ghostie_ on some of his recent builds. I opted to use ludus cloud for deployment and easy lab stand-up, but there are a million and one guides on building labs. https://t.co/PG6IYhnE41
0
0
0
🤣🤣🤣
🚨 Black Friday Deal Alert: Get 🏟️ https://t.co/1HabXkoQQH for $0... today and every day! From Debian 12 to full Active Directory lab in just 3 commands. Free. Open Source. Powerful automation. The best deal is the one that's always free. Try now at https://t.co/1HabXkoQQH. (1/2)
0
0
1
MSSQL domain privesc (@_nullbind), .mobi whois takeover (@watchtowrcyber), LLM CTF (@bishopfox), mac filesystem 🪄 (@gergely_kalman), and more!
blog.badsectorlabs.com
MSSQL domain privesc (@_nullbind), .mobi whois takeover (@watchtowrcyber), LLM CTF (@bishopfox), mac filesystem 🪄 (@gergely_kalman), AlcaWASM writeup (@suidpit), and more!
0
10
25
I just released a tailscale deploy/remove role for @badsectorlabs Ludus. Thank you to @jessefmoore for all the testing. Please let me know if you encounter any bugs or if you have any ideas for improvement. Feel free to submit a PR. https://t.co/SM7IyUaXZr
#Ludus #Tailscale
0
5
16