Jason Lang
@curi0usJack
Followers
15,128
Following
195
Media
855
Statuses
5,447
@TrustedSec Red Team | Hi-Fidelity trolling | Privacy Enthusiast | Putting the "no" in nano | Avatar:
Joined September 2013
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#IanxSB19xTerry
• 272964 Tweets
#MOONLIGHT_MVTeaser
• 136185 Tweets
Rio Grande do Sul
• 116309 Tweets
Boeing
• 101794 Tweets
Suho
• 86184 Tweets
RPWP CONCEPT PHOTO 2
• 57854 Tweets
プロフェッショナル
• 56611 Tweets
joongdunk love workpoint
• 39527 Tweets
青山先生
• 29967 Tweets
عدنان البرش
• 26208 Tweets
#無責任でええじゃないかLOVE
• 25413 Tweets
Indonesia vs Irak
• 19379 Tweets
YOUNG K
• 16054 Tweets
VACHSS
• 14783 Tweets
Last Seen Profiles
Pinned Tweet
Dear new followers,
- For solid red team technical tweets, follow my Red Signal list.
- For a curated list of latest hacker news, bookmark and read this:
- To be thought-lead, follow
@HackingLZ
- Keep following me only for the sublime trolls. 😁
3
17
121
The
#1
question I get is "How did you learn to do this?"
Curiosity + Failure + Google + Friends + Failure + Stack Overflow + Cons + Failure
19
289
749
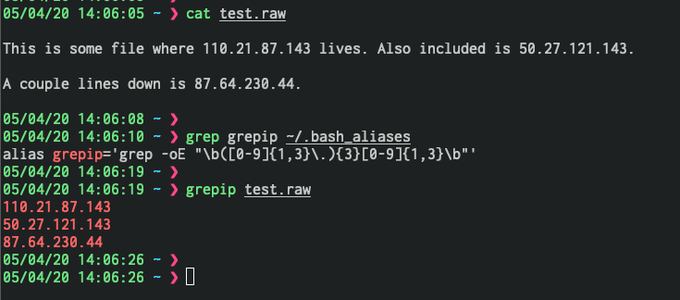
Red Team: Do you know what data your offensive operations are leaking via TLS negotiations? Neither did I until a friend showed me. Blue Team: Good blocking & detection potential. Worth your interest!
Start here:
Thanks
@haroldogden
!
14
311
737
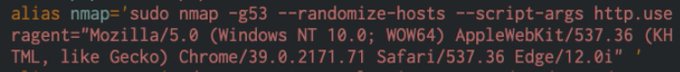
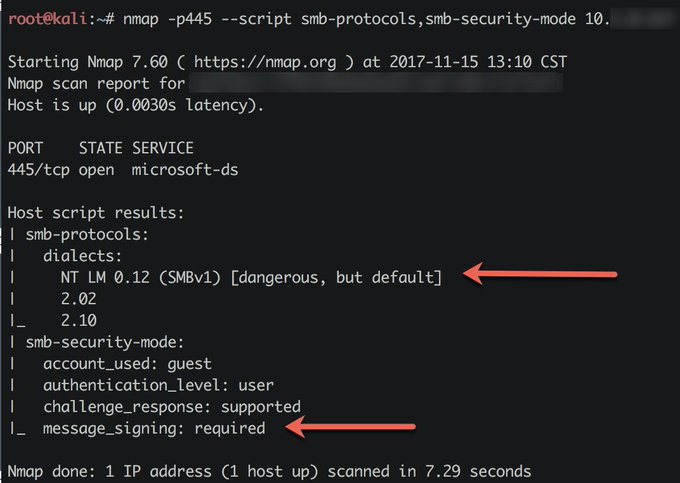
New version of nmap (7.60) includes the smb-protocols nse script which gives you definitive answers on smb version support. Combine with smb-security-mode to get a nice picture of your targets smb posture.
#pentest
4
339
627
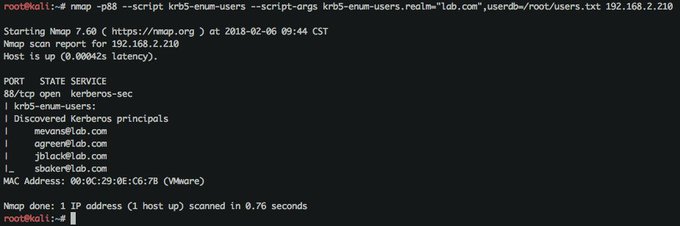
My new favorite nmap script: krb5-enum-users.nse.
Brute force Active Directory usernames using Kerberos & a userid list!
Read about it here:
#Pentesting
4
296
615
Some of people I admire most in
#infosec
:
- Rarely talk about themselves
- Love to share their knowledge
- Are competitive
- Freely admit when wrong
- Happily welcome newcomers
- Are perpetual students
- Give all the credit away
9
142
530
A few
@DakotaCon
students asked me about building an AD lab. Good resources here:
Also, for creating realistic AD users, my own meager mods to ADImporter here:
Good luck!
4
206
390
Hot new
#RedTeam
tools:
Powermad: by
@kevin_robertson
DomainCheck: by
@cmaddalena
DCOMrade (legit ascii art): by
@sud0woodo
Killer work. 👏
2
171
322
Properly configured Group Policy is more effective than properly configured $EDR.
8
41
291
Handy! Just learned AWS EC2 instances have metadata that can be queried via HTTP GET requests. Example, get the public IP if your EC2 instance by running the following command on that instance:
curl
http://169.254.169.254/latest/meta-data/public-ipv4
10
138
269
#infosec
is the industry of perpetual apprentiship. If you think you are a master, you probably are not.
8
80
250
I love innovative ways to brute Force AD creds. New technique stretches your login attempts. Well done
@foxit
(and thanks for the shout-out)!
2
117
223
Defenders: are you monitoring who is doing SELECT *'s on tables containing PII? If you're not you should be. Would you know what to do if you saw a query out of the ordinary? Would you even recognize a query that is out of the ordinary?
#FoodForThought
😈
15
77
229
Written for setting up pentest dropboxes, this fantastic blog series helped me step-by-step set up a VPN tunnel across a cloud VPS back to my
#homelab
. Great work by
@CaseyCammilleri
&
@SprocketSec
!
1
91
210
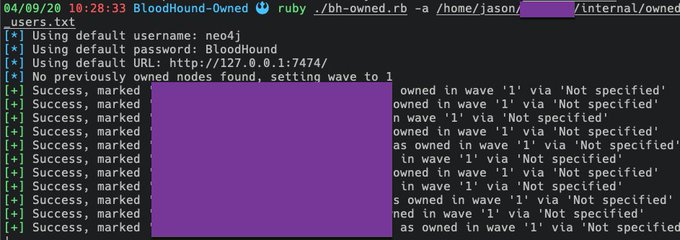
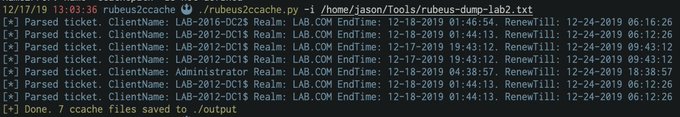
New tool: rubeus2ccache
Generates ccache files directly from Rubeus dump output.
Major thanks to
@_dirkjan
for basically writing anything hard.
Merry Christmas Red Team! 🎄
4
92
213
I've lost track of the number of times I've included this article as a finding reference in a pentest report (thanks
@Lee_Holmes
!). If your org is still on PowerShell v2, *please please* read this and convince the powers-that-be to upgrade!
4
76
202
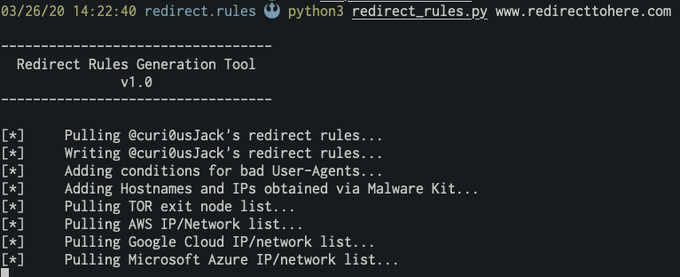
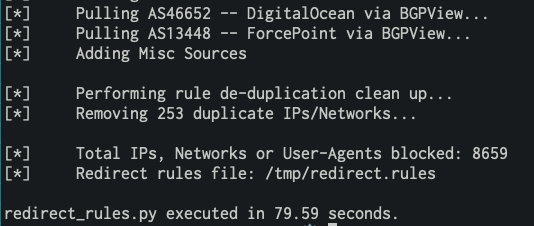
Super happy to introduce redirect_rules.py - the next iteration of the AV htaccess block gist that expands on it as well as mkhtaccess_red to dynamically generate a dedup'd rules list. Fantastic work from
@0xZDH
and
@mdfarhan06
! 🔥
0
89
198
Fun
#BlackHat
story: Student working through a COM hijack challenge on our VM that's running the trial version of Win7. He found a hijack during the boot process on slui.exe and disabled all prompts to activate Windows. 🏴☠️🤘😈
6
36
181
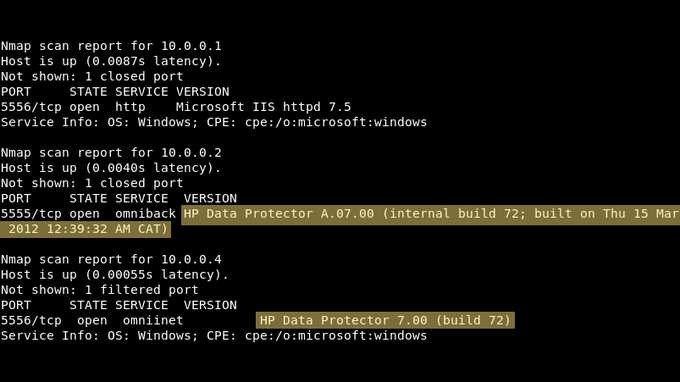
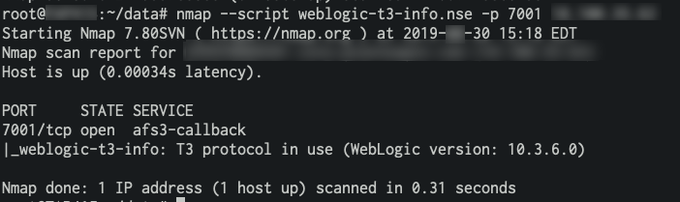
Hunting Java RMI?
1) Check for additional ports ()
2) Use nmap's rmi-dumpregistry nse script.
3) Have a look at rmiscout from
@bishopfox
.
💥Easy RCE Ports
Java RMI: 1090,1098,1099,4444,11099,47001,47002,10999
WebLogic: 7000-7004,8000-8003,9000-9003,9503,7070,7071
JDWP: 45000,45001
JMX: 8686,9012,50500
GlassFish: 4848
jBoss: 11111,4444,4445
Cisco Smart Install: 4786
HP Data Protector: 5555,5556
#ptswarmTechniques
9
429
1K
1
64
178
Red teamers: If you're facing Okta (you are lol), you'll want to keep an eye on the
@TrustedSec
blog today. Incoming hotness from
@_xpn_
...👀
7
18
170
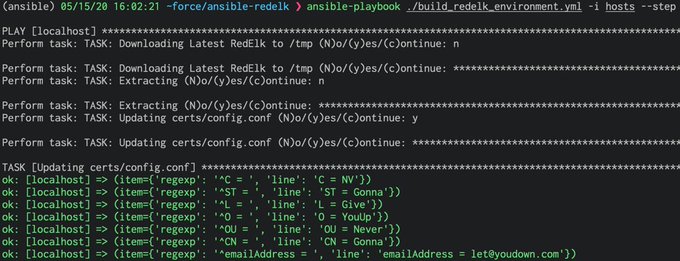
Happy to be releasing RedELK Ansible playbooks. Hopefully they help others get into the great tool that is RedELK!
Do you wish you had a step by step guide and
#GitHub
resources to deploy infrastructure automation across a
#RedTeam
infrastructure?
@curi0usJack
thought you might. His latest
#blog
"Automating a RedELK Deployment Using Ansible", is a must-use resource❗
0
114
255
6
51
167
Do your best, Blue Team, but don't forget to have fun along the way! H/T to [REDACTED].
#Respect
😂😂
7
29
162
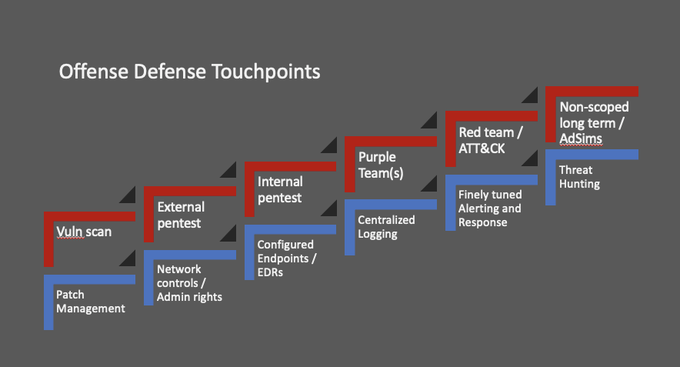
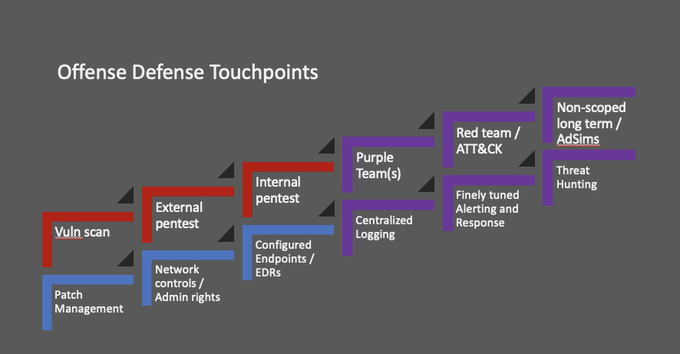
Have had a few ask me about using my Derbycon 9 infosec maturity slides. Yes, you can get them here: .
They were from a talk I gave with
@contra_blueteam
at DerbyCon 8 (here: ).
Please simply credit our twitter handles. Thanks!
3
49
162
New stealthy lateral movement technique looks incredible (existing socket hijacking). Definitely something to keep eyes on when released. The PDF paper is extremely impressive and worth the read.
"
#ShadowMove
: a Stealthy Lateral Movement Strategy" is now available to read
Read if interested to see a new practical lateral movement
Demo (TDS (MS SQL) & FTP):
Prototype will be released soon
@MITREattack
@USENIXSecurity
2
184
375
1
67
156
Hats off to the
@FireEye
FLARE team for putting together a great RE package in flare-vm. I know next to nothing about RE, but am enjoying the journey. Flare VM has made things way easier for us n00bs. Even details like the context menus are seen to. Bravo!
3
34
149
Wireshark in the terminal? What a time to be alive...
Thanks for showing me this
@mandreko
!
3
50
145
On the TrustedSec discord channel, someone asked how I do I move from pentesting to red teaming?
@jarsnah12
gave the best and most succinct answer to that question I think I've ever read. I know everyone charts their own path, but this is all around good advice. ❤️💙💜
0
36
136
Defenders: Guard your FIM sync accounts just like you would a DA. If I get a FIM account hash, I can dcsync anything I want. Many thanks to
@PyroTek3
for documenting this:
3
61
135
To be counted with the
@TrustedSec
Targeted Operations team is truly an honor. You guys are among the finest in the industry and it's my pleasure to also call you my friends. Long may your shells be fruitful and multiply.
Here's to you. 🍻
2
10
134
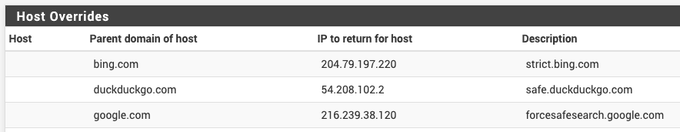
"COMPANY NAME" site: intitle:"Service Desk" OR intitle:"Desktop Support" OR intitle:"Security Engineer" OR intitle:"Help Desk"
#OSINT
3
39
124
Proud to have my Advanced Attack Infrastructure course accepted at
#DerbyCon
9! If red team infrastructure & automation is your interest, I hope to see you there! 😊❤️💜💙
5
16
122
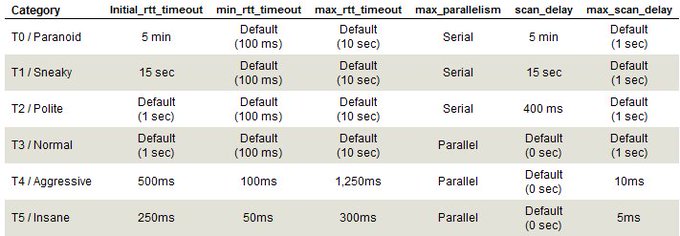
Helpful chart regarding the difference between
#nmap
's timing profiles. Note the incredible difference between T0 & T3 in terms of speed (scan_delay) & parallelization!
Taken from here: . Still accurate based on current nmap docs.
3
52
118