Colonel Panic🌻🇺🇦 will be on other platforms now
@timhelming
Followers
508
Following
16K
Media
192
Statuses
5K
Musky twitter's not for me Mastodon is where I'll be
0
0
1
30 days til this account gets annihilated, I guess. Oh well!
0
0
1
Insightful thread. There's feasible, useful automation. That will not/should not lead to an autonomous SOC.
🧵 the 'Autonomous SOC' is a pipedream. 1/n https://t.co/5gwY9IC19f
1
0
1
⚠️ATTN @punsandrosess @DoGoodComplex
0
0
3
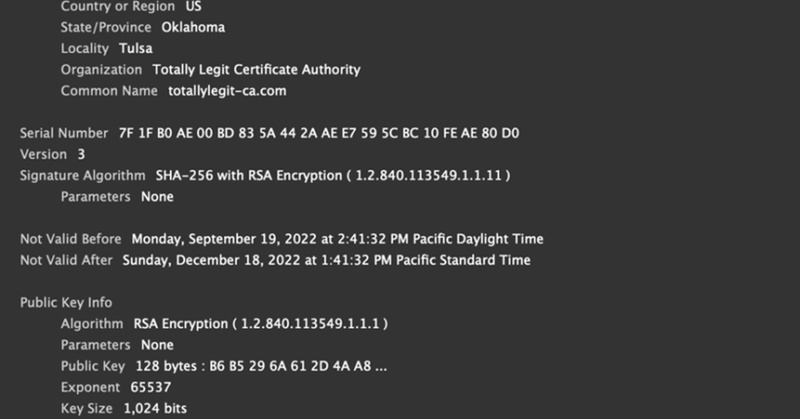
Awesome work by @turboCodr, opening up a can of OSINT on x509 certs. (Part 1 of the blog is here: https://t.co/GiZawJNGyS)
blog.gigamon.com
Editor’s note: This article is the first of two blog posts on analyzing x509 certificates using open-source intelligence. Read Part 2 here. I’ve spent a
Here is the follow up post of a 2-part series I've written on OSINT analysis of x509 certificates used by phishing, malware, and everyday companies. This one focuses on the Subject Alternative Name and all the bits you can infer from it. https://t.co/Bb1F7axNjj
0
0
1
This week on #BreakingBadness, @tw_pierce, @punsandrosess and @timhelming discover you can't talk about #OldGremlin without talking about the movie Gremlins. The crew also discusses double extortion attacks from #BlackByte. Listen here: https://t.co/GPtafsBbck
0
0
1
This week on #BreakingBadness, @tw_pierce, @punsandrosess and @timhelming discover you can't talk about #OldGremlin without talking about the movie Gremlins. The crew also discusses double extortion attacks from #BlackByte. Listen here: https://t.co/GPtafsBbck
0
0
1
⚠️ATTN Gremlins fans
This week on #BreakingBadness, @tw_pierce, @punsandrosess and @timhelming discover you can't talk about #OldGremlin without talking about the movie Gremlins. The crew also discusses double extortion attacks from #BlackByte. Listen here: https://t.co/GPtafsBbck
0
0
2
0
0
0
Thanks @mWISEConference for having us...always a great event and @gclef_ and I enjoyed sharing our research. @DomainTools #ThreatIntel
0
1
4
0
1
4
I'm SO STOKED to be presenting with @gclef_ ! Super fun collaborator and great researcher. @DomainTools #cybersecurity
0
1
4
This is my first @GrrCON but I sure hope it won't be my last. Very impressive show. Only regret: that I can't see all of the talks! Speaking of talks, I'll be presenting on #DomainBlooms, something we at @DomainTools have been studying for a couple of years now.
0
2
5
Excellent thread on how IR in operational technology (OT) is a very different beast from in IT
OT incident response requires pretty different skillset, mindset, and tools than IT incident response, and if a cybersecurity company tells you otherwise they are trying to sell you something. I call it ‘OT/IT DFIR divergence’, and it makes it challenging to hire and train folks.
0
0
0
Excellent thread
I love @MITREattack - but the ways some vendors operationalize it is misleading and often useless. 🧵
1
0
1
This is cool. @tw_pierce talked about the leak of #bruteratel on the #BreakingBadness podcast this week and one of the things we kicked around was how soon there would be good detections.
Super proud of the work the team did to get #bruteratel 🛡️ detections and playbooks out, in this blog we: 1. ⚗️ Reverse an example 2. ⚒️ Breakdown the C2 capabilities 3.🤺 Simulate for testing using Atomic-C2 Here are the bloody details: https://t.co/GwnIJLpwIc
#STRT #splunk
0
2
6
I wrote about the need to broaden the set of paths into infosec—it doesn't make sense for us to simultaneously decry the skills gap and hold unrealistic requirements for entry-level positions. I also wrote a bit about my own path.
.@CISAJen was right - the #infosec industry needs good people! @TimHelming describes his nonlinear path to a career as a security evangelist with skills from previous jobs and often overlooked soft skills. Read the full story here: https://t.co/YJflKXhpMb
0
1
2
Always worth checking out @securityskeptic 's stuff!
Dave Piscitello @securityskeptic will present findings & recommendations from recent studies of 3M phishing and 2.5M malware reports @M3AAWG #mtg56. Security experts also will discuss TLS, DNS, DDOS, malware, spam texting & more. Info
1
0
2