ShadowOpCode
@ShadowOpCode
Followers
818
Following
2K
Media
161
Statuses
467
Malware analyst & reverse engineer 🧠 Threat intel on stealers, RATs, live campaigns 🕵️ Technical analysis. No buzzwords. 📍DM open for research collabs
Joined May 2025
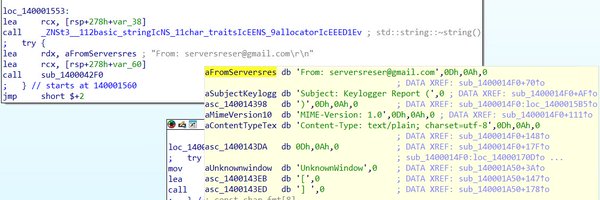
🚨 New #JavaStealer “MaksStealer” uncovered! Fully in-memory, FUD, DES–Blowfish runtime decryption, WebSockets on 4025/4028/6662. Author “Max, 17yo” left his signature in the payload 🤯 Full report & IoCs 👉 https://t.co/HHuNMn5FPL
#infosec #malware #ThreatIntel @malwrhunterteam
3
8
112
@jamieantisocial @struppigel @JAMESWT_WT @guelfoweb @marsomx_ @RussianPanda9xx @_JohnHammond maybe this is interesting for you, have a look if you want :)
0
0
2
found this russian (?) malware Downloads artifacts falcon.exe -> Stealer, packed with Themida, drops logs in russian, exfiltration via HTTPS in a ZIP file explorer.exe -> CryptoMiner, XMRig #UnPacking #Themida #ThreatIntel "Banshee" in the ZIP name, APT (?) We need to investigate
4
10
52
staging: hxxps://4bagh[.]net/doc/Encrypted_Script.ps1 C2 SMTP: mail[.]iranlabex[.]ir 🇮🇷 C2 sender: salesoffice@iranlabex.ir 🇮🇷 C2 receiver: jctrads@protonmail.com Bazaar:
bazaar.abuse.ch
Hunt for malware samples tagged with tag 'RegioneLiguria'
0
3
4
🚨ALERT🚨 Malspam campaign against Sistema Sanitario Regionale Liguria @RegLiguria 📤Sender likely spoofed (🇺🇿 based server) 📥Receiver: Institutional PEC mail > rar > jse > powershell with AES encrypted ps1 > aspnet_compiler.exe (BLACKHAWK > Agent Tesla) IoC and sample below👇
1
5
22
Phishing "Pedaggio non pagato" autostde[.]com domain created today (2025-11-19) @AgidCert
@JAMESWT_WT @illegalFawn @guelfoweb @AndreaDraghetti @marsomx_
0
1
3
🚨NEW python stealer🚨 🛸Drops .pyd in %APPDATA%\Local\Temp\_MEIxxxxx ⚠️Relaunch itself via CreateProcessW Exfil👇 browser cookies and password Discord Steam 📡send data via telegram bot C2: api[.telegram[.org/bot8484778379:AAG_EhhM1Ao139HBPfgfV0zVlMSi-2HfkCM/sendMessage bazaar👇
2
8
23
🚨ALERT🚨 #CryptersAndTools started using github and supabase as staging for #steganography images Delivering #AgentTesla
@anyrun_app : https://t.co/26LPH3iVnX hunter: @JAMESWT_WT
1
2
17
Caminho Loader Malware Analysis #CaminhoLoader #malware #ThreatIntel
@smica83
@ShadowOpCode
https://t.co/KYnUbH2SsR
0
1
4
⚠️ALERT⚠️ there is an OPEN webshell on hxxps://boldcleaningsolutionsatl[.]com/ NEW domains: boldcompanions[.]com boldinnovationspetcare[.]com @AgidCert @guelfoweb @JAMESWT_WT
@vxunderground a lot of malwere inside 😋 cc: @tobersotski
https://t.co/HwXuXe3lho
🇮🇹Analisi di #Remcos RAT diffuso in #Italia con campagna #ClickFix a tema #GLS ✉️ Indirizzo non valido, compila il modulo 8900395 📎 XHTML ℹ️ Info e #IoC 👇 🔗 https://t.co/Q9URLALWaY
0
4
7
HTA file deobfuscation from the "fake DMCA report" phishing campaign. Key features shown in the screenshots @_JohnHammond @vxunderground @ShadowOpCode
https://t.co/vMiXwrmRMk
Yesterday folks got a phishing email for a fake DMCA report-- myself included. Caught me at a good time so I could record poking at the scam and the malware it leads to: ultimately infostealer malware (the usual) from a fake domain & clearly AI slop site: https://t.co/n0jiqgVi9Z
5
7
45
Cryptocurrency investment scam #Italy Targeting @RaiNews and @SigfridoRanucci @CarContiRai @antoclerici hxxps://advertiserspots[.]com/ hxxps://advertiserspots[.]com/Italy/ spotted also by @illegalFawn
https://t.co/6XM6UzVhF6 🧵 1/2
1
0
2
🚨#Formbook #Xloader spotted in a malspam campaign in #Italy ⚠️Using another "Lorem Ipsum Dolores" variation! Related tweet: https://t.co/gNq7Bg9Bv5
@anyrun_app analysis: https://t.co/nVJAypisqu C2: www[.]grevla[.]top
🚨ALERT🚨 #Formbook #Xloader started using "incididunt ut labore" dummy text instead of "Lorem Ipsum" in its C2 Related tweet: https://t.co/7iMajHbuNE updated network config extractor: https://t.co/wAsXLNvRhF
2
2
13
@AgidCert @guelfoweb @JAMESWT_WT @illegalFawn @marsomx_ @AndreaDraghetti the domain is #FUD at the moment 🤡 https://t.co/Ou4NpQizTh
0
0
1
🚨ALERT🚨 ⚠️We have spotted a massive #phishing campaign in #Italy targeting various firms mail > pdf lure > #TypoSquatting 👀Typo squatting domain: hxxps://mircosotfonilne[.]ru
1
5
22
This variant shows identical C# runtime compilation and Donut shellcode staging → same TTP chain as Lumma Stealer documented here: https://t.co/39thjdb7gR 🔥Reverse, correlate, hunt🔥
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 https://t.co/nxGeePMpFp
#LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence
0
1
5
the payload is finally injected inside of explorer.exe It is not clear at the moment what malware is this. However...
1
1
4
the operations to create the C# executable are performed...
1
1
3