Biswajeet Ray🇮🇳
@BiswajeetRay7
Followers
622
Following
10K
Media
687
Statuses
10K
Indian Security Researcher | Pentester | Analyst | #OSINT 🔍#SOCMINT #GEOINT | Research & Analysis | Secured Microsoft, IBM, NASA & more | National Security.
India
Joined October 2017
Finally after lot's of hardwork and failure. Got Hall Of Fame from Microsoft. 🤩 #bugbounty #infosec #cybersecurity #recon #microsoft #security #bugbountytips #acknowledgment #osint #msrc #websecurity #pentesting #linux #vulnerability #india #bug #flaws
@microsoft
4
4
25
How i Found Easy ₹5,000 IDOR | Bug Bounty Writeup | P3 https://t.co/xuk1dljdS8
#bugbounty #bugbountytips #bugbountytip
medium.com
Introduction
0
4
31
The classic GTA Vice City can now be played directly in your web browser. • Full original gameplay experience • Quick launch • Supports all screen resolutions • Gamepad and touch controls enabled • Local and cloud save support Play here: https://t.co/HWttuRcoIc
22
133
1K
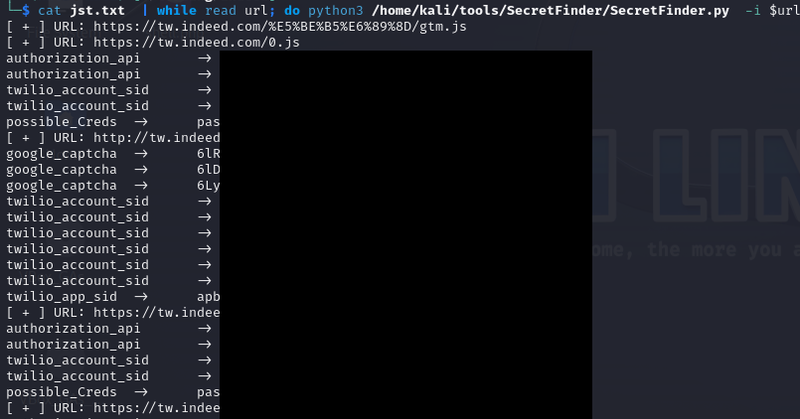
Easiest way to find hidden api from js files https://t.co/MTDwQMwyT2
#bugbounty #bugbountytips #bugbountytip
jeetpal2007.medium.com
Hello
1
16
97
No security can stop you if you are persistent enough every system has a weakness, and persistence is the skill that finds it. ~Biswajeet Ray ⚡️
0
0
0
Osman Hadi's last post before getting shot! Whoever was behind it—you just turned someone's feeble talks into a call for reckoning! We need to be mature about this. Step one is dropping our collective and individual atlamı! Step two is not making an impulsive judgment!
515
83
613
Very cool of Yearn having all past security disclosures, including bounties and other events. All projects should follow along. https://t.co/vIHHBi1hq3
1
10
124
In the last 5 years, I have tested 50+ bug bounty tools... Each has its own superpower. Here is the MEGA list of bug bounty tools you need to bookmark: 🧵
4
50
209
Lost his eyesight in an accident, but never lost his courage! After a life-changing accident in 2014, C. Dwarakesh rebuilt his life from scratch. Through sheer determination, hard work, and the aid of assistive technology, he became India’s first fully blind officer to serve in
40
780
5K
Begani Shaadi me Abdullah Diwana 😂
#WATCH | Delhi | Addressing at Delhi AI Grind 'India's first City Centric AI Innovation Engine', Indian Astronaut & IAF Group Captain Shubhanshu Shukla says, "AI is engraved in each and every aspect. It is a tool to accomplish things and is being utilized extensively... These are
0
0
0
This is a nice resource on Bug Bounty notes and checklists: https://t.co/KH3eajSMmX
github.com
A Collection of Notes, Checklists, Writeups on Bug Bounty Hunting and Web Application Security. - HolyBugx/HolyTips
1
19
83
Chota Matka, one of the most blood thirsty tiger to live in Indian forests !! He has killed 4 adult male tigers in territorial fights till now, has a disfigured distinct face due to fights
226
952
12K