Gospel
@4osp3l
Followers
17K
Following
36K
Media
1K
Statuses
9K
Offensive Security | Christain | Full-Time Bug Bounty Hunter On @yeswehack | 0x19 | God Is Everything
Nigeria
Joined September 2023
I asked 10+ top bug hunters who made over $500k+ about their secrets. Here’s what they said: 1. They work insanely hard (280+ hrs/month) even after earning millions. 2. They master 1–3 programs deeply. 3. Speed matters. Never break your momentum. 1/n
1
39
253
Starting November 1, I'll be committing to a 365-day bug bounty challenge, focusing primarily on improper access control ( BAC, IDOR ) and information disclosure vulnerabilities. - Will try as much as possible to report 20+ valid vulnerabilities ( 1 per month average ). -
16
6
110
I'll definitely follow this process, next year; but it's gonna be, 80/20 hacking/learning.
All my current bug bounty knowledge is gone. Here's how I get it back and make $100k in the first year: First, I've got to learn the basics. For this, I will make sure I understand at a high level how the components I'm working with function. I'll need to understand...
1
2
52
Taking a short break to go full study mode for a week; read 50-100 writeups on improper access control + a session with @theXSSrat; when I'm back, I'll be going all in on hunting access control vulns. Hey @d3q0w, keep moving; I'll join you soon.
8
2
94
If something's listed OOS but you can chain it with another flaw, do it, the combo can flip the impact and get you accepted.
1
1
5
Entering " https://t.co/dyXWRDGU72", redirects to "
https://t.co/SUJ2qP7qGF{{token}}" Bypassed : Entered "
https://t.co/FFA2WBv67s" redirects to " https://t.co/9mpnWVLqYq{{token}}
Open redirect is OOS, but the company accepted it due to, i was able to leak the access token.
3
10
146
Let's Go !! ❤
As for @4osp3l he’s gonna get some direct coaching from me Time to form shotguns into cannons ❤️
4
3
36
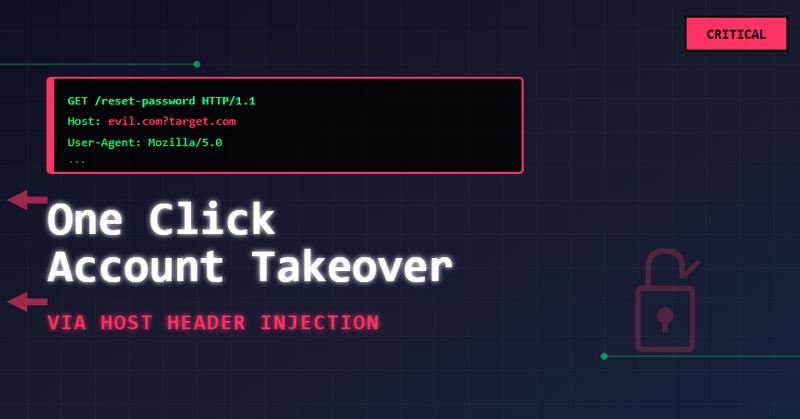
1-Click Account Takeover via Host Header Injection https://t.co/i2de1Fn4R3
3bdulr7man.medium.com
TL;DR: I discovered a Host header injection in the “Forgot password” flow that lets an attacker force the application to generate…
2
30
179
Thanks to @GodfatherOrwa, you taught me to think beyond the obvious when dealing with leaked credentials and follow-up questions from companies.
1
0
12
Behind a $XX,XXX bounty, are dozens of N/A, duplicates / informative; let's keep that in mind.
@4osp3l Not everyone want to share their real stats, many just show how good they are at finding bugs, making us feel we’ll never reach their pro level. What you show is that consistency is the real key. Thank you for that 💪
1
1
34
20 reports to a single program, only 4 got accepted; 3 duplicates; 13 lessons learned... that's how you grow in bug bounty.
8
8
149
Tip: Try to send `csrftoken=null` or `csrftoken=%00` just found this one.
13
65
451