R.
@0xrb
Followers
6K
Following
3K
Media
889
Statuses
5K
Reverse Threat Intel | Malware /Threat Hunter | Exploit Research \\ #IoT #Malware #Research, Reverse Engineering, #Botnet C2 #Hijacking
localhost
Joined June 2010
here is the list of more than 4k sub-domain infrastructure including #DGA domain used by #UNC2452 #SolarWinds #backdoor Link: https://t.co/UL9myJnYbn cc: @iblametom @TheHackersNews @threatpost
pastebin.com
Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
3
33
87
CVE-2025-55182 (React) and CVE-2025-66478 (Next.js) are critical unauthenticated RCE vulnerabilities in the React Server Components (RSC) "Flight" protocol. Default configurations are vulnerable – a standard Next.js app created with create-next-app and built for production can
2
4
46
another exploited in-the-wild FortiWeb vuln? It must be Thursday!
7
119
416
Awesome new threat report from Google Threat Intel Group documenting how threat actors are leveraging Gemini. A lot of information and actionable avalable in the report! Great work 👌 https://t.co/0ktEQbUhmq
4
138
527
Proofpoint threat researchers have designed an open-source tool—named PDF Object Hashing—to track and detect the unique characteristics of PDFs used by threat actors... similar to a digital fingerprint. We use this tool internally to help track multiple threat actors with
0
45
164
💥 Wiz Research has uncovered a critical Redis vulnerability that's been hiding for 13 years We found RediShell (CVE-2025-49844): an RCE bug in Redis that affects every version of Redis out there. It's rated CVSS 10 - the highest severity possible. The vulnerability lets
7
171
524
🚨 Rhadamanthys v0.9.2 is here! What’s new in this multi-layered stealer’s latest evolution? We break down the updates, tactics, and what defenders need to know. Dive into our blog for the full analysis. https://t.co/b5SL8bWR81
research.checkpoint.com
Research by: hasherezade Highlights Introduction Rhadamanthys is a complex, multi-modular malware sold on the underground market since September 2022. It was first advertised by the actor “kingcret...
0
32
113
#ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/6
56
674
3K
Just released LLMEx - open-source security testing framework for LLMs: OWASP Top 10+1 for LLMs compliance, Smart false positive reduction, Works with OpenAI + custom APIs, Extensible for custom tests, and much more. Checkit out: https://t.co/HAV56nFAhL
1
4
19
IP whitelisting is fundamentally broken. At @assetnote, we've successfully bypassed network controls by routing traffic through a specific location (cloud provider, geo-location). Today, we're releasing Newtowner, to help test for this issue:
github.com
Abuse trust-boundaries to bypass firewalls and network controls - assetnote/newtowner
14
239
880
🔥 𝐀𝐈 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦𝐢𝐧𝐠 𝐏𝐥𝐚𝐲𝐠𝐫𝐨𝐮𝐧𝐝 𝐋𝐚𝐛𝐬 from @Microsoft 12 free labs to up-level your hacking skills from the “AI Red Teaming in Practice” Black Hat training, covering: - Credential exfiltration - Extracting a secret from the metaprompt - Indirect prompt
2
86
261
After the announcement of seizure of some of the Lumma Stealer panel domains, new ones were opened shortly in the following hours. Please remember that the whole activity has not ceased👀 /yuriy-andropov.com @ViriBack
0
1
11
Autopsy of a Failed Stealer: StealC v2 When Your $3000 Malware Budget Goes to Marketing Instead of Actually Enabling the Encryption Function I did some analysis on the updated #StealC v2. The blog comes with config extractor, hunting queries and Yara rule. Let me know your
7
62
185
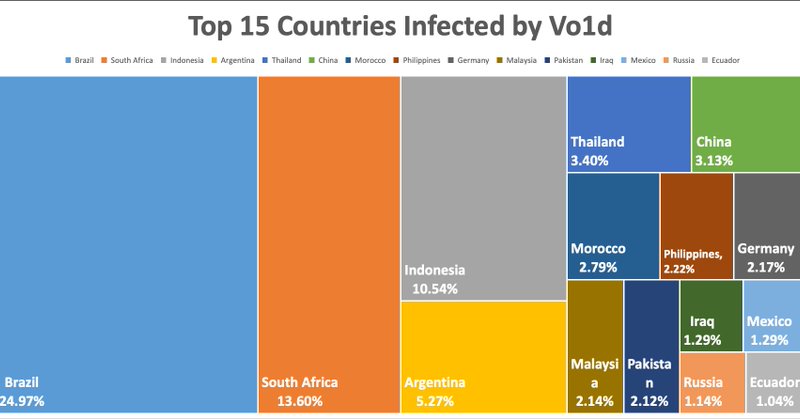
Our latest blog dives into a new variant of #Vo1d #botnet. C2 sinkhole data reveals it has infected 1.6M Android TVs across 200+ countries. Now leveraging RSA , its network can remains secure even if researchers register DGA C2s
blog.xlab.qianxin.com
Prologue On February 24, 2025, NBC News reported: "Unauthorized AI-generated footage suddenly played on televisions at the U.S. Department of Housing and Urban Development (HUD) headquarters in...
1
16
29
hi threat hunters and malware analysts! I want to introduce you to my newly developed tool called "Matkap". with this tool, you can infiltrate telegram bots(malbots) associated with malware, gain access to their messages, and extract all their logs! ➡️ https://t.co/JVGcnQsWcR
11
172
1K
Experts discovered #surveillance tool #EagleMsgSpy used by Chinese law enforcement https://t.co/NXPUUWc0UR
#securityaffairs #hacking #China #Android
securityaffairs.com
Chinese law enforcement uses the mobile surveillance tool EagleMsgSpy to gather data from Android devices, as detailed by Lookout.
0
3
6
This is one example of why correct attribution matters in CTI. https://t.co/Am0UGbkXx6… CC: @Gi7w0rm @Glacius_ @banthisguy9349 @0xrb
medium.com
A sophisticated cyberattack was detected, involving the impersonation of the Indian Administrative Department’s website. While the attack was attributed to known threat actor groups, SideCopy and…
5
32
132
🚨EDR Telemetry website is live! 🥳 I hope this makes it even easier for folks to compare the telemetry of EDR vendors and visualize their visibility gaps 🙂 ‣ Website🔗 https://t.co/mTj9lJzE3J ‣ GitHub 🔗 https://t.co/7Qf4wXam7r **Telemetry results reflect the most recent
I created the first draft of a website for the EDR telemetry project to help people quickly compare vendor telemetry visibility. What do you think about it? Are there any specific features you want to see for the website? Built with ChatGPT 4o with canvas (wanted to test it
19
283
900
JA4 is now in VirusTotal! All the malware using wininet: https://t.co/9gqTh5JJGP Executables using winhttp: https://t.co/a37lUKG4EL Remember, it is the combination of JA4+ fingerprints that build high fidelity detection. Rarely is JA4 a silver bullet on its own. For example,
2
36
154