johannes
@wiknerj
Followers
328
Following
1K
Media
14
Statuses
165
retweets are my not own 😺 occasionally dyhszlkehktikc
Joined September 2014
RT @spendergrsec: Huh, I didn't realize that the vibe-coded vulns inserted into 5 LTS kernels that still aren't fixed 22 days later haven't….
0
84
0
RT @kavehrazavi: Happy to announce that the paper about IBPB problems that included the first real cross-process Spectre exploit just got a….
0
2
0
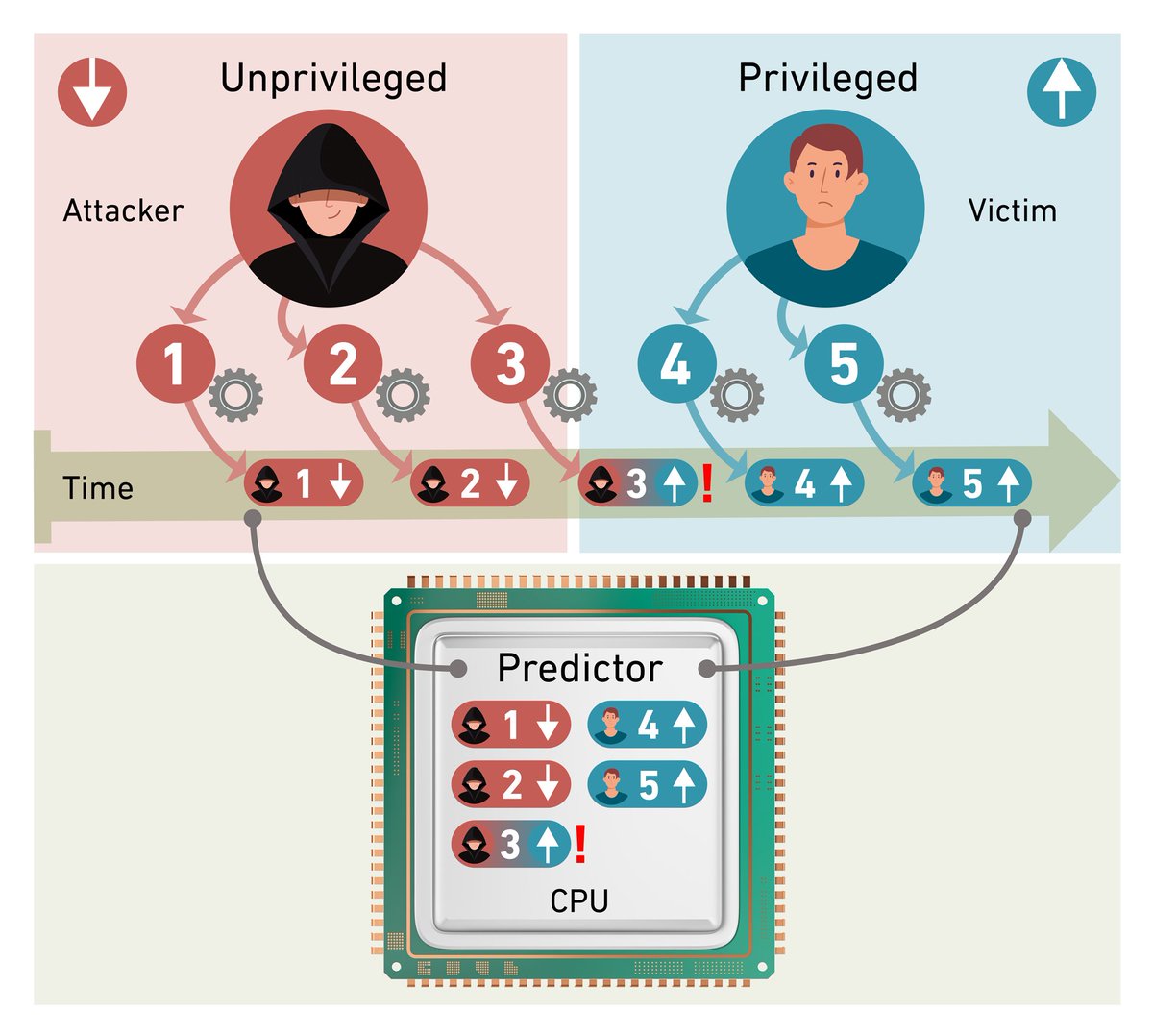
Branch Race Conditions Predictor causes recent predictions to be added after more recent privilege switches (→ wrong privilege, eIBRS💥) prediction flushes (→ retained valid, IBPB💥) finish. @sparchatus eventually figured it out 🙌.
Disclosing Branch Predictor Race Conditions (BPRC), a new class of vulnerabilities where asynchronous branch predictor operations violate hardware-enforced privilege and context separation in virtually all recent Intel CPUs. @wiknerj @kavehrazavi :
0
4
22
Thanks for the 21st @h2hconference! Always a joy to meet the mix of researchers, enthusiasts, academics, hackers. Special thanks to the organizers and yes the 🚌 trip to Rio went smoothly @bsdaemon @gabrielnb 😄 has a moment to enjoy this very special zine on the journey.
3
0
15
The first ever end-to-end cross-process Spectre exploit? I worked on this during an internship with @grsecurity! An in-depth write-up here:.
0
55
124
Curious about this. .
I've just presented at IEEE SecDev our work on reversing the eIBRS HW mitigation. TLDR: use retpoline or stibp+ibpb ;) The mitigation relies on an automatic flush of the predictor to prevent brute-force. But it is not frequent enough (thus, it relies on obscurity really).
0
0
3
RT @marazzi_michele: With RISC-H, we demonstrate the first Rowhammer bit flips on a high-end RISC-V CPU!. We had to devise a novel method t….
0
24
0
RT @marazzi_michele: For the first time, we imaged and reverse engineered 6 modern DDR4/5 DRAM chips (. Due to the….
0
54
0
RT @pjattke: Our latest work, #ZenHammer 🔨, shows that #AMD Zen 2/3/4 systems are equally vulnerable to frequency-based #Rowhammer as #Inte….
0
20
0
RT @kavehrazavi: Phantom just won a best paper award at @MicroArchConf! Phantom shows the security implications of pre-decode speculation t….
0
6
0
This might be the most outrageous transient execution attack ever :).
Dreams don't affect reality, but they may influence your actions. Turns out this applies to AMD CPUs too! After a long embargo, we can now present Inception, a new transient exec. attack that leaks data on all AMD Zen CPUs. With @wiknerj and @kavehrazavi.
1
3
11