Theori
@theori_io
Followers
5K
Following
510
Media
100
Statuses
389
Empowering Innovation with Security.
Joined January 2016
Our intern @_qwerty_po was destined to analyze a recent Linux kernel LPE vuln (CVE-2022-32250), a bug found and reported by @FidgetingBits. Here's a brief write-up on the analysis of the bug and the exploit development. Check it out! (exploit included).
2
102
244
We've started a blog series on N-day full chain exploits. The first part is about chrome renderer exploit, CVE-2023-3079. Check it now!👇👇. #Theori #티오리 #Blog #Research #Fermium252 #Chrome #VirtualMachine #CVE #Vulnerability.
Do you use a virtual machine to browse dangerous links safely? If you use the Chrome browser inside that virtual machine, is it secure enough?.As you might have guessed, the answer is not so much. We chained six unique CVEs from 2023 listed below. • Chrome Renderer RCE :
4
87
217
"Building a 1-day Exploit for Google Chrome" by @brian_pak.Code and slides are available here:
1
95
175
Theori researcher, Junghoon Lee (@lokihardt), reported ASLR bypass for Chrome and Safari that utilize conservative GC. The runtime is greatly improved compared to similar techniques, making it more feasible. Blog post coming soon!.
4
37
173
The third series in our N-Day full chain exploit is out now!. We exploited CVE-2023-29360, a beautiful logical vulnerability in the Windows driver, to elevate the privilege from user to SYSTEM. It was also leveraged by @Synacktiv at Pwn2Own 2023.
2
56
155
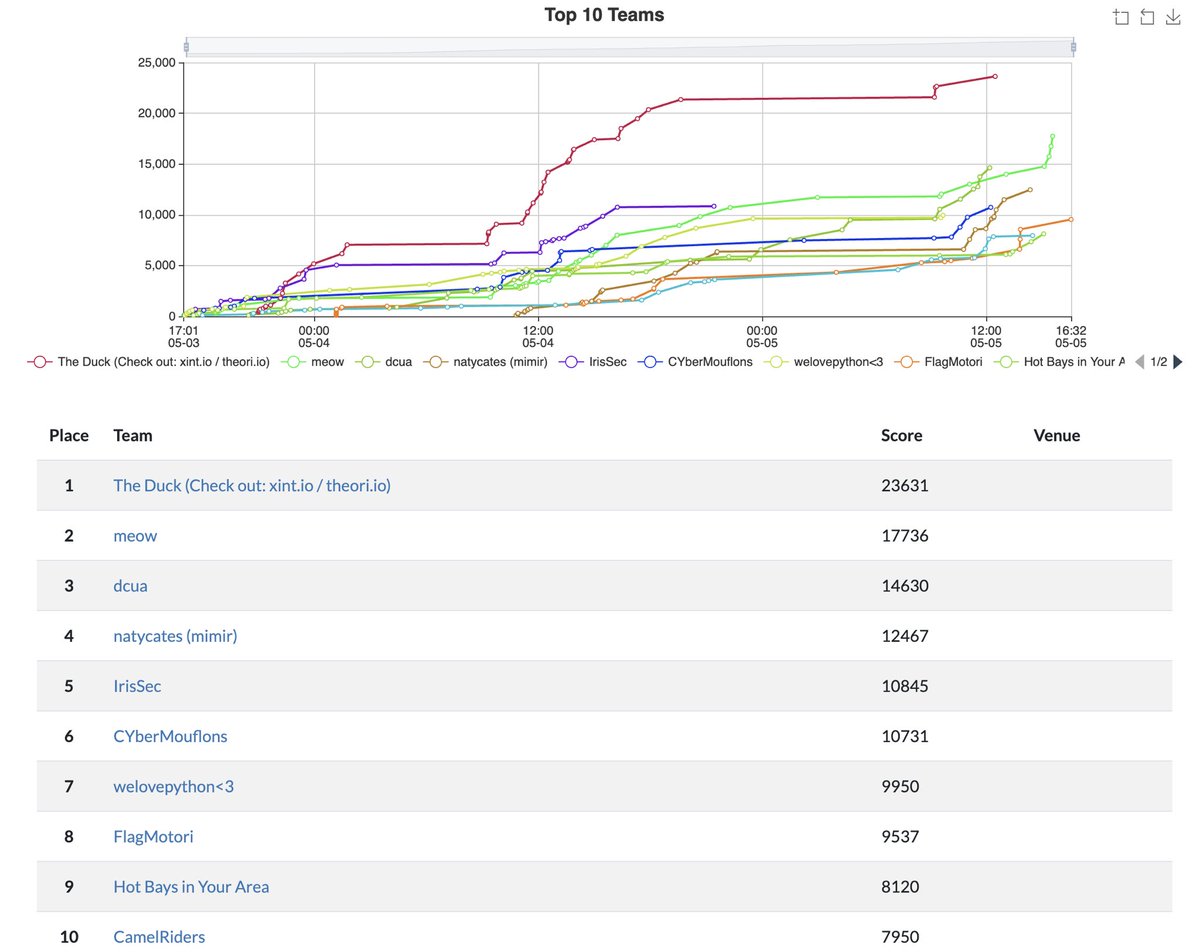
This effectively makes # of unsolved challenges to be 0 for The Duck :) It was a fun weekend activity that allowed Theori researchers to show off their deep knowledge and strong skills in Web3 security. Thanks to @paradigm_ctf for hosting the CTF!
after further discussion, we've made the decision to pull POOL from the list of active challenges due to certain issues. we apologize to any teams who are affected by this.
7
8
121
Can't escape from COVID-19 madness, but here's how we escaped Chrome Sandbox by exploiting a bug found by our researcher, Tim Becker (@tjbecker_ ) Check it out!.
0
51
118
Theori overtakes the @defcon leaderboard once again!. 🏆 @mmm_ctf_team takes 1st place at the world's largest hacking competition, DEFCON CTF. Shout out to our joint partners @maplebaconctf and @PlaidCTF !. Conquering the most difficult cybersecurity challenges, one at a time 😎
2
26
107
Part 4 of our N-Day Exploit Series is LIVE! 🔥.➡️ Unveiling CVE-2023-34044, an information leakage vulnerability in #VMware Workstation’s #VBluetooth device, found by our own @pr0ln!. It’s a variant of CVE-2023-20870 demonstrated by @starlabs_sg in.
0
43
97
Waiting for our N-Day Exploit Part 5? 😎. We exploited CVE-2023-20869, a Host-to-Guest escape vulnerability in the VMware Workstation VBluetooth device, showcased by @starlabs_sg at #Pwn2Own2023 in Vancouver. Check out our blog for more details!. #Theori.
3
33
96
Did you attend @hexacon_fr this year?. Check out our summarizing blog post 👀. Take a look at the #WindowsOS privilege escalation #vulnerability.and dive a little deeper into the #exploits at the code level. #Theori #티오리 #HEXACON #kernel #lpe.
1
22
83
작년 구글 #Chrome 취약점 공격엔 어떤 기법이 사용되었을까요?. 티오리 취약점 연구 팀은.#WebAssembly 의 raw 포인터를 사용해.V8 샌드박스 보호 기법을 우회할 수 있었던. 자세한 내용은 블로그에서 확인해 보세요!. #Theori #티오리 #Sandbox #V8Engine.
0
27
76
We came, we saw, we conquered. MMM takes 1st at @defcon CTF! We had a great time playing with our friends @maplebaconctf and @PlaidCTF as @mmm_ctf_team! 🍁🦆🗝. Great job to Katzebin and StarBugs, and all other teams! Thank you @Nautilus_CTF for organizing!. Now, back to work!
1
12
65
Here's our write-up on three challenges from Paradigm CTF 2022: Solhana-{1,2,3}, Stealing Sats, fun-reversing-challenge.
We're done! Thanks to everyone for playing Paradigm CTF 2022. Congrats to @theori_io, @hexensio, and @PwningEth for scoring in the top 3!. A big shoutout to @0xGreg_, @Mauricio_0218, @Zellic_io, @osec_io, and @dumbcontract2 for guest authoring challenges. See you next year!
0
14
48
Hiring CTF 🚩 Offensive Security Researcher. 세계 최정상 해커와 함께.내 손으로 안전한 세상을 만드는 경험. 2024년 3월 31일까지.Hiring CTF로 도전해 보세요!.👉 #티오리 #Theori #채용 #채용공고 #SA #컨설팅 #Consulting
0
10
47
In related to the Chrome exploit talk, we've also updated the pwn.js (our JS library for browser exploitation) to support Chrome targets, thanks to our researcher @zoaedk. An example exploit (from the talk) for Chrome is also added. Please check it out!
1
19
42
🏆 티오리 박세준 대표, 대통령 표창 수상! @brian_pak. 사이버 보안의 지속적인 연구 개발, 국내 보안 기술 발전과 인재 육성에 힘쓴 공로를 인정받아, . '2024 과학·정보통신의 날 기념식'에서 박세준 Theori 대표가 대통령 표창을 수상했습니다! . 티오리는 앞으로도 사이버 보안 분야 고도화된
0
3
40
청와대 영빈관에서 열린 '청년 화이트해커와의 대화’ 자리에.티오리의 “The Duck”팀이 초청받아 다녀왔습니다!. 사이버 공격에 대응하는 화이트햇 해커의 역할과 중요성에 대해 이야기 나눌 수 있는 영광스러운 기회였습니다 👏. #티오리 #theori #해커 #청와대
0
3
39
Our researchers conquered yet another CTF at #codegate 2022!.Congratulations to ‘The Duck’ and all our researchers who competed as different teams. GG everyone! 👏
1
0
38
N-Day Exploit부터 Pwn2Own까지 🏆.연달아 놀라운 소식을 전한 티오리 팀. Vulnerability Research 팀의 연구와 준비 과정을.블로그에서 확인해 보세요!. #티오리 #Theori #인터뷰 #취약점 #취약점연구 #Vulnerability #VR #P2OVancouver.
0
6
37
🎯 What's the Linux kernel's biggest target for researchers?. Mingi Cho from Theori's Vulnerability Research Team unveiled a crucial Linux nftables vulnerability at #Zer0Con2024. Our findings show advanced mitigation bypasses, spotlighting its risk in KernelCTF contests.
#Zer0Con2024. His research will bring great light this year 🎆. Mingi Cho 🇰🇷 of @theori_io."Exploiting a Missed Linux Kernel Patch in a KernelCTF Instance"
0
2
39
During the first day of #Pwn2Own Vancouver 2024,.our researchers Gwangun Jung (@pr0ln) and Junoh Lee (@bbbig12) successfully combined three different zero-day vulnerabilities for a #VMware Guest-to-Host escape and #Windows11 Privilege Escalation!. #Theori #Vulnerbility #Windows.
Confirmed! Gwangun Jung (@pr0ln) and Junoh Lee (@bbbig12) from Theori (@theori_io) combined three different bugs to escape #VMware Workstation and then execute code as SYSTEM on the host OS. This impressive feat earns them $130,000 and 13 Master of Pwn points. #Pwn2Own
0
5
34
Theori representing South Korea’s cybersecurity technology at @RSAConference 🫡.Come swing by our booth at S-634 to hear more about Xint, the newest #USPM encompassing cloud security and external threat detection! . #Theori #RSAC2024 #Xint #CloudSecurity #ExternalThreatDetection
2
4
29
Mark your calendars! 📅.Our researchers Junoh and Jeongoh will be presenting at @hexacon_fr. They'll be sharing the #WindowsOS privilege escalation #vulnerability and exploit technique. See you in Paris on October 13-14th!.#Theori #HEXACON2023.
👣Unveiling Hidden Paths: Unearthing Vulnerabilities and Exploiting Modern Windows Kernel, by Junoh Lee and JeongOh Kyea
1
3
30
Our CTF team, The Duck, is the winner of LINE CTF 2024!. Completing all of the challenges with 6 hours to spare😎,.we’ve won almost every single LINE CTF so far!. Here’s to today’s victory, as well as many more to come 🥂. #Theori #티오리 #TheDuck #LINECTF #LINECTF2024
1
1
31
✨ Missed @offbyoneconf? Catch up now!. At #offbyoneconf, Theori's Vulnerability Research Team— @kkokkokye, @pr0ln, Yeonghun Kim—broke down the N-Day Full Chain, detailing the exploit methods and chaining techniques. Check out the comprehensive details on our blog! 🔍.🔗.
감사합니다 to the phenomenal @theori_io team @kkokkokye @pr0Ln & Yeonghun Kim @offbyoneconf 𝐌𝐚𝐤𝐞 𝐍-𝐃𝐚𝐲 𝐆𝐫𝐞𝐚𝐭 𝐀𝐠𝐚𝐢𝐧-𝐓𝐡𝐞 𝐒𝐭𝐨𝐫𝐲 𝐨𝐟 𝐍-𝐃𝐚𝐲 𝐅𝐮𝐥𝐥 𝐂𝐡𝐚𝐢𝐧 𝐟𝐫𝐨𝐦 𝐛𝐫𝐨𝐰𝐬𝐞𝐫 𝐢𝐧 𝐠𝐮𝐞𝐬𝐭 𝐭𝐨 𝐒𝐘𝐒𝐓𝐄𝐌 𝐢𝐧 𝐡𝐨𝐬𝐭 is a winner! 또 보자
0
7
28
We had two of our researchers speaking at #zer0con2018 last week. We are releasing the code and slides from the talk! Links to each of them will follow.
1
16
28
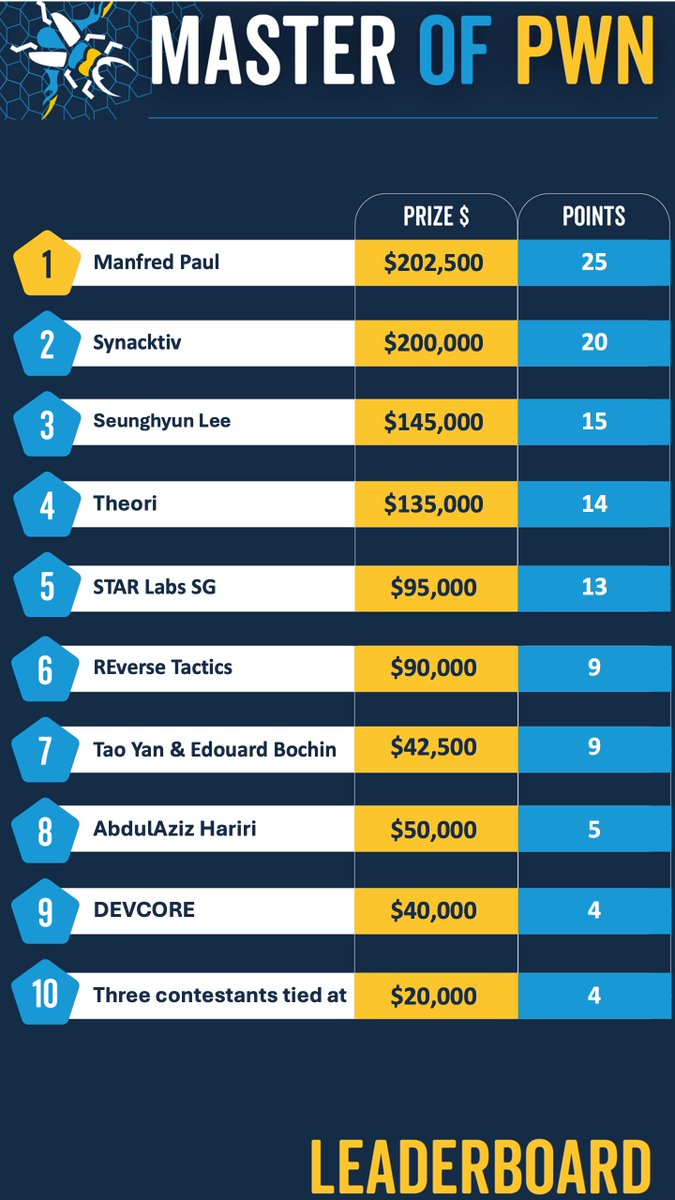
Final results are in! #Theori takes 4th place on the #Pwn2Own leaderboard! 🏆.Along with yesterday's VMware exploit with Windows kernel addon, our researcher Mingi Cho also successfully escalated privileges on #Ubuntu desktop, winning $5,000 in prizes!.#Zeroday #P2OVancouver.
That's a wrap! #Pwn2Own Vancouver is complete. Overall, we awarded $1,132,500 for 29 unique 0-days. Congrats to @_manfp for winning Master of Pwn with $202,500 and 25 points. Here's the final top 10 list:
0
1
29
In the 2023 OpenTRS #3 📡. CTF Team GYG and Theori VR team explores #MacOS, #Win32k vulnerabilities. And our CTO @andrewwesie takes you through #Web3 ZK proof-based @RelicProtocol. On July 6th, live on This seminar will be conducted in English.
2
7
23
Theori의 새로운 모습을 공개합니다!. 누구나 안전하게 꿈꿀 수 있는 세상을 위해.티오리가 더욱 견고해졌습니다. 티오리가 펼칠 새로운 모습을.기대해 주세요!. . #티오리 #Theori #브랜딩 #리브랜딩 #rebranding.
0
7
25
국내 최대 보안 교육 플랫폼 드림핵과 함께.3년 연속 개최하는 LG전자 사내 CTF ⚔ @LGE_korea. 구성원 보안 역량 향상을 위한 선택,.드림핵 엔터프라이즈로 보안 혁신을 이끌어가요!. #Theori #티오리 #LG전자 #LGE #Dreamhack #드림핵 #CTF #Hacking #Hacker #Cybersecurity
0
4
26
[Notable CVEs from Theori’s #Vulnerability #Research in 2022]. 1/.Our Vulnerability Research team has worked tirelessly last year to discover and report numerous vulnerabilities, including critical zero-days on Windows, Linux, and popular browsers.
1
2
25
Theori, 2024 사이버공격방어대회(CCE) 종합우승 🏆. CCE 일반부에 참여한 티오리 4개 팀이 1, 2, 3, 4등 모두 차지했습니다! . 🥇 종합우승 'The Duckling': @junorouse, @5unKn0wn, @_bincat, 성해빈.🥈 일반부 우승 'The Gosling': 강우원, @RBTree_, @yechan_bae, 김현태.🥉 일반부 준우승 'GYG':
0
9
25
드림핵 (@dreamhack_io) 채용 CTF 프로그램을 통해.실력 있는 오펜시브 보안 연구원이 합류하게 되었습니다!. 티오리 보안 컨설팅 핵심 부서, SA(Security Assesment) 팀의 채용 CTF 후기부터.보안 실무 인사이트를 담은 CTF 문제, 관련 이벤트까지. 자세한 내용은.
1
6
24
Heading to @hackinthebox 2022 Singapore?.Interested in browser hacking?. @singi21a, a star researcher of our Vulnerability Research team, will be presenting his research about Browser Hacking with ANGLE. Attend his talk to learn ANGLE basics and how it is used in WebGL/WebGL2.
1
1
23
티오리에선 누가, 무엇을 하고 있을까요?. 세상을 더욱 안전하게 만들기 위해 노력하는 티오리 구성원의 이야기를 전해 드려요. 보안을 누구나 쉽게 공부할 수 있도록 노력하는 @dreamhack_io 콘텐츠 팀 bincat의 이야기,.지금 확인해 보세요!. #티오리 #인터뷰 #드림핵.
0
6
22
📡 티오리는 지금 Open TRS 중 #BEACON2023. #web3 보안을 리딩하는 @ChainLight_io 과 함께 .지속 가능한 Web3 생태계 구축을 위해.의견을 나누고 있습니다.
📡 Web3의 미래가 궁금하신가요? 🧵(1/2). 지속 가능한 #Web3 생태계 구축을 위해 펼쳐지는.화려한 라인업의 발표와 토론들,.맛있고🍕 유익한 네트워킹까지. 11월 23일 오후 7시, 무료로 즐겨보세요!.👉 #Theori #티오리 #Web3Networking.#웹3 #ChainLight #Defi #crypto
1
1
23
Following up on @QubitFin's post about the recent attack, here's our brief post-mortem. While we can't prevent our customers from modifying the code after our audit, additional mitigations could've been suggested by our team that would've reduced risk.
4
8
20
[📰] Theori x 두나무 업무 협약(MOU) 체결 🎉. 티오리가 블록체인·핀테크 전문 기업 두나무와.웹3 보안 인재 양성을 위해 업무 협약을 체결했습니다!. 티오리의 웹3 전문부서 @ChainLight_io 가.커리큘럼을 개발하고 강의, 멘토링 할 예정이에요. #티오리 #theori #두나무.
0
2
23
세계 최대 해킹 대회는 어떻게 우승할까요?. Theori CTF Team, The Duck이 말하는 DEF CON 31 과.@AppSec_Village 에서 발표한 dohyeon의 후기까지💬. 조금 늦었지만, 생생한 8월 @defcon 현장을.티오리 블로그에서 확인해 보세요!. #티오리 #DEFCON #해킹 #대회 #발표 #후기.
0
8
21
🔥 Theori at #HEXACON2024 🔥.We’re excited to have four researchers sharing groundbreaking insights:. 1️⃣ Guest Revolution: Our Story of Compromising the Host Kernel from the VMware Guest – @bbbig12 & @pr0Ln detailed their Pwn2Own 2024 success, highlighting vulnerabilities and
0
2
21
Our researchers Dohyun and Woowon will be presenting at the @DEFCON #AppSecVillage this year. They'll be sharing noteworthy vulnerabilities and mitigation measures from a front-end perspective, based on their experiences in security consulting. See you in Las Vegas in August!.
ASV is excited to welcome Dohyeon Kim and @wooeong337 to the @defcon stage this August! . We're looking forward to their discussion on protecting #frontend #applications from overlooked #vulnerabilities . See you Vegas Dohyeon and WooWon! . #appsec #applicationsecurity #defcon31
0
5
21
오늘은 티오리의 6번째 생일입니다 🎉. 모두 함께 티오리의 성장을 자축하며,.우리의 도전을 응원했습니다!. 티오리의 생일, 여러분도 다 같이 축하해 주실 거죠?. #BusinessAnniversary #6YearAnniverary
0
1
21
🎉 #Web3 이용자, 거래소, 프로젝트 빌더를 보호하는 통합 보안 플랫폼.ChainLight DART(Digital Asset Risk Tracker)를 런칭했습니다!. DART를 통해 웹3상에 산재하는 다양한 취약점과 위협으로부터 보호받으세요. 아래 링크를 눌러 DART에 접속할 수 있습니다 👇.
0
7
20
청년이 일하기 좋은 기업 티오리! 🙋♂️. 취약점 연구 Vulnerability Research 팀에.티오리 최연소 청년이 있다는데요. 고등학생 인턴 heegong이 경험한 티오리는 어땠을까요?.티오리 인턴 생활을 확인해 보세요!.👉 #티오리 #Theori #인터뷰 #인턴 #Intern #Vulnerability.
0
4
19
Theori는 Web3 보안을 위해 무엇을 하고 있을까요?. #블록체인 데이터를 살피고 위험 관리를 하며 Web3 세상을 안전하게 만드는 팀입니다. #Web3 세상을 밝게 비추는 @chainlight_io 팀 juno, mika, qwaz의 이야기,.지금 확인해 보세요!. #티오리 #인터뷰 #체인라이트.
0
6
18
약 9만 명이 주목한 바로 그 취약점! 👾.최근 가상 머신의 취약한 부분을 공유한 티오리 팀은.평소 어떤 업무를 할까요?. 사이버 위협을 사전에 방지하기 위해 끊임없이 연구하는 .Vulnerability Research 팀의 이야기를 확인해 보세요!. 👉 #티오리 #Theori #인터뷰 #취약점.
0
2
18
Our researcher will speak about browser and kernel 1-days for Windows. Also releasing a JS library for browser exploitation. #POC2017.
0
6
18
" 압도적인 기술력과 윤리 의식으로.사이버 상의 모든 문제를 해결하기 위해 노력해요 ". 사이버 해결사가 되어 세상을 보호하는.SA 팀 reset의 인터뷰를 지금 확인해 보세요!. #티오리 #Theori #인터뷰 #SA #컨설팅 #Consulting #보안.
1
1
18
Another day, another win – Theori on the podium at Hack the DRONE 2024! 🤖. Theori’s researchers @bbbig12 and @s0ngsari530 with Team GYG took 3rd place 🥉. Hack the DRONE, hosted by the Korean Drone Security Association, saw 164 teams from 35 countries competing to uncover drone
0
1
20
Congratulations @chainlight_io for winning the NumenCTF. Thank you @numencyber for organizing a great Web3 competition!.
🥳 We're excited to announce that we WON a Web3 CTF competition!. ✅ Check out the NumenCTF scoreboard and take a look at our impressive performance!. ⏳ Even though we were ~15 hours late to the party compared to other teams, we managed to take the lead.
0
2
14
LoL 게임 DDoS 사태를 분석해 화제가 된 화이트햇 해커,.본업은 국내 최대 규모 사이버 보안 교육 플랫폼 개발자!?.🔗 해킹을 공부하는 사람이라면 모두 거쳐간 플랫폼, @dreamhack_io.드림핵은 어떻게 탄생하고, 개발 팀은 어떤 문화를 가지고 있을까요? . 지금 바로 티오리.
0
5
16
사이버 공간의 ‘숨겨진 수호자’를 밝히다. 네트워크에 새로운 '점'이 하나씩 추가될 때마다.사이버 보안의 중요성과 시급성은 더욱 중요하기에. 디지털 수호자들의 날카로운 통찰력과.지칠줄 모르는 인내와 끈기를 강조합니다. HACK created by THEORI. #DOTHACK2024
0
10
15