Oluwaseyi
@seyi_Anisere
Followers
781
Following
940
Media
63
Statuses
980
Scholar| Book lover| Computer engineering student and a budding Cyber security specialist|CyberGirl 4.0| Interested in finance and money management.
Nigeria.
Joined July 2019
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Happy Pride Month
• 790370 Tweets
Champions
• 305937 Tweets
Real Madrid
• 304844 Tweets
#ExitPoll
• 304757 Tweets
Dortmund
• 217616 Tweets
#UCLfinal
• 172019 Tweets
LGBTQ
• 150338 Tweets
seokjin
• 142880 Tweets
INFINITY LOVE FOR BLANK
• 99073 Tweets
#AapKaPilla
• 91679 Tweets
BTS FESTA POSTER
• 85112 Tweets
#東京タワー
• 81843 Tweets
#SixTONESANN
• 78211 Tweets
مدريد
• 47719 Tweets
Tommy Robinson
• 42944 Tweets
Reus
• 41280 Tweets
RETURN OF CAPTAIN KOREA JIN
• 36710 Tweets
Tosin
• 34218 Tweets
دورتموند
• 24124 Tweets
Mofokeng
• 23076 Tweets
#ヨルクラ
• 22902 Tweets
LIGHT HUGS
• 18560 Tweets
Vini Jr
• 16965 Tweets
#CuentaPública2024
• 15385 Tweets
Orlando Pirates
• 14321 Tweets
Sundowns
• 12989 Tweets
ジンくん
• 12917 Tweets
KALKI MONTH BEGINS
• 11265 Tweets
大倉くん
• 10445 Tweets
Last Seen Profiles
Risk management
Which two types of control are effective after a violation of a security policy occurs ( choose two)
a corrective
b recovery
c preventive
d deterrent
e compensative
@_DeejustDee
@ireteeh
@Queenicea17
@akintunero
@Ahmed___khaan
@SecurityTrybe
@CyberSecFalcon
8
4
22
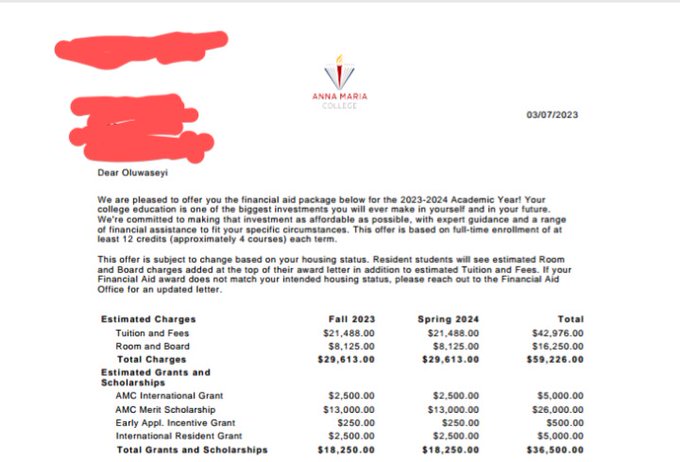
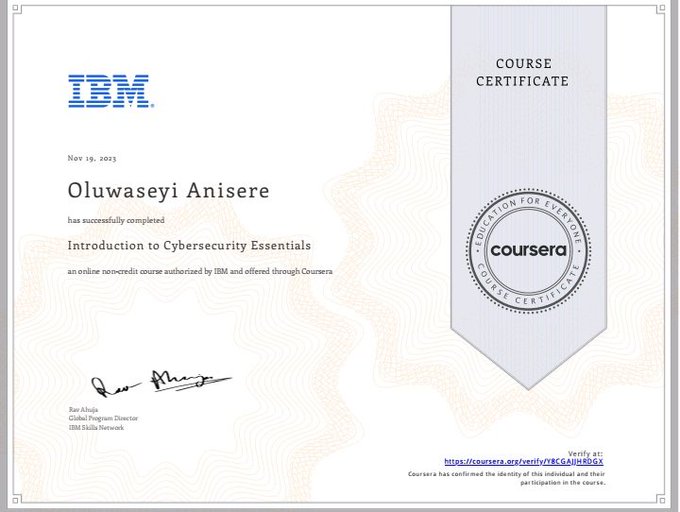
Below is my admission letter and scholarship letter
Thank you very much
@Ahmypeace
@SamdGreat01
@matajson
@Ijesha_canadian
@olumuyiwaayo
@Jamaticulus
@SummerOkibe
@drhammed
@Dr_Adeleke
@particular6
@james_omoboye
@oulawal
@adejimiadeniji
@AaronAkpuPhilip
@OgbeniDipo
@ushiebuaras
1
5
18
Week 2 of CyberGirls done ✔️
I am gradually adjusting to this rigorous learning and I think it fun.
@cybersafehq
#proudcybergirl
@sisinerdtweets
1
2
17
@gabariskufilan
Completely agree oo..my friend and her room mate was attacked by robbers and my friends room mate was completely naked when they came...niggas took laptop,phone and money and left without touching them oo..so it not really about what you are wearing
0
0
9
Week 4 of CyberGirls done✔️✔️
*I learnt how to configure a stimulated network according to organizational requirements.
* I learnt how to analyze malware files that have been extracted from packet captures
* I learnt how to evaluate endpoint security.
@cybersafehq
#proudcybergirl
1
1
9
Worth $36,500 for my tuition and fees. However I am faced with the challenge of catering for my VISA fees (
#72
,000), SEVIS fee($350) and enrollment deposit ($500). I have been informed by the school that I will lose my scholarship if I don't resume for the fall semester which
1
1
7
@omoalhajaabiola
I wish it was free
After you are selected, you will have to bring two people to enroll and pay for their course before u will be selected for the scholarship
So it is not entirely free.
4
0
8
What is a disadvantages of deploying a peer to peer network model
a lack of centralized administration
b high cost
c difficulty of set
d high degree of complexity
@_DeejustDee
@CyberPatronMC
@Queenicea17
@ireteeh
@SecurityTrybe
@segun
@CyberSecFalcon
@TheSecMaster1
1
1
7
B. To help organization detect threats before they disrupt business
0
1
8
@Queenicea17
I thought of this too...some guys have sent me messages asking me how to start their Cybersecurity career and I think a mentorship program will be of so much help.
2
1
6
@sisinerdtweets
@cybersafehq
I am going to be a cyber girl.🤗🤗
I have been selected to join 500+ outstanding fellows across 27 African countries for the CyberGirls fellowship 2024 cohort. Carefully selected from 20,000+ applicants.
Thank you Cybersafe foundation
#Cybergirls2024
0
1
6
Spot your baby girl! Happy International Girls in ICT Day!
Thank you
@sisinerdtweets
for this great opportunity to be a CyberGirl 🤗🤗
1
0
6
@Ifeoma90483092
@osemagnum
Oats
Omega 3- cod liver oil or Evening primrose oil
Zinc
Vitamin C (1000mg)
2
1
6
A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the internet. It typically protects web application from attacks such as cross- site forgery, cross site scripting(XSS), file inclusion. e.t.c
1
0
3
Day 12
A vulnerability is a flaw or weakness in an assets design, implementation or operation and management that could be exploited by a threat. A threat is a potential for a threat agent to exploit a vulnerability. A risk is the potential for loss when the treat happens.
0
2
4
Check this out if you are interested in the ISC Certified in Cybersecurity (cc) Exam
1
0
4
@Queenicea17
I like the way it is explanatory and easy to understand. It also starts with the basics concept which is needed for understanding Linux.
1
1
4
@Queenicea17
@_Rega_n
@rtate72
@segoslavia
@GeniusFranklyn
@Ahmed___khaan
@_Abiola_Y
Wishing them all the best
0
0
4
Please donate and support 👇👇
If it was up to you, to help one young woman chase her dreams of a career in
#cybersecurity
, would you make that happen with your donation?
We need your support to turn the potential of 500 young women across Africa into today's cyber talent and tomorrow's cybersecurity leaders.
11
256
420
0
1
4
The thing about period pain is no one can feel it and because everyone generally says it painful you might think that yours is the norms. I had similar experience and for some years I endured the pain and tried to live with it until I started having severe symptoms.
1
0
4
Happy International women's day to this amazing women... thank you for all you do in the Cyber space.
@ireteeh
@sisinerdtweets
0
0
4
@ireteeh
As a newbie I am currently learning the basics or cyber security, learning concepts and their meaning and also learning about the various career path in cyber security and what it takes to be in any of these path
0
0
3
Happy International women's Day to all the amazing women out there.
Happy International women's Day to every amazing woman in Cybersecurity doing amazing things & achieving amazing feats💐🥳
You are Seen & loved 🤩
Tag them😎
@sisinerdtweets
@ireteeh
@_DeejustDee
@AbbyJefia
@Lizettle_
@_Rega_n
@NazaGrace
@Gracesharonsol
14
24
125
0
1
3
This is so inspiring
"Two years ago, I was a newcomer in this field, aspiring to become a cloud security engineer. Without looking back, I relentlessly pursued my goal. It's remarkable how much can change with time, focus, and effort"- she reflected.
You see,
@bugsandbags___
used to be a software
13
18
143
1
0
3
@EkennaMg
@_DeejustDee
@SecurityTrybe
@Queenicea17
@TheSecMaster1
@Ahmed___khaan
@africacyberfest
@CyberPatronMC
@allenharper
@CyberSecFalcon
Well I can't think of any online forum for now but try and follow the right people here on Twitter
@ireteeh
@akintunero
@OnijeC
and
@_DeejustDee
1
0
3
@BaconOfLife
@cyb3rshi3ld
@_DeejustDee
@SecurityTrybe
@Queenicea17
@TheSecMaster1
@Ahmed___khaan
@africacyberfest
@CyberPatronMC
@allenharper
@CyberSecFalcon
You can do the Google Cybersecurity course and then take the Networking Basics courses
0
0
3
Thanks colab....
@seyi_Anisere
@samiira_tou
@Creed_Emmanuel7
Congratulations 🎉🎉🎉!!!
You have been selected as the winners.💃💃
Kindly send a DM to continue the conversation.
2
0
2
0
0
3
@CoLab_kd
I am a computer engineering student who is interested in cloud computing. I have started learning the basics of coding and I intend to learn JavaScript programming language. I visited colab a month ago with a friend and I was really amazed by the conducive learning environment.
0
0
2
Happy birthday mama
@ireteeh
Thank you for all you do
0
0
3
@TheOyinbooke
I keep starting and stopping and that because my laptop is bad...been patching with it but it recently became so worse😥😥
0
0
2
@CoLab_kd
I will be delighted to join the present session to increase my practical knowledge on coding and learn about other interesting subjects that will be taught.
0
0
2
Sharpen your Networking skills
Which type of device provides an internet connection through the use of a phone jack
a satellite modem
b Wi-Fi AP
c DSL modem
d cable modem
@CyberPatronMC
@SecurityTrybe
@TheSecMaster1
0
0
2
I am still in my first month of learning. The need to acquire a skill that is relevant to my course of study keeps me motivated daily.
I need a group of people that are currently learning and in their beginner level along with mentorship.
Day 5
@CyberPatronMC
How long have you been in this Cybersecurity journey?
What motivates you to keep going daily?
Are you facing any challenge currently? How can we help?
128
37
107
0
0
2
@xtertainerr
It is because of statements like this
@sisinerdtweets
is empowering women in Cybersecurity.....some years from now this narrative would have changed ✔️
3
0
2
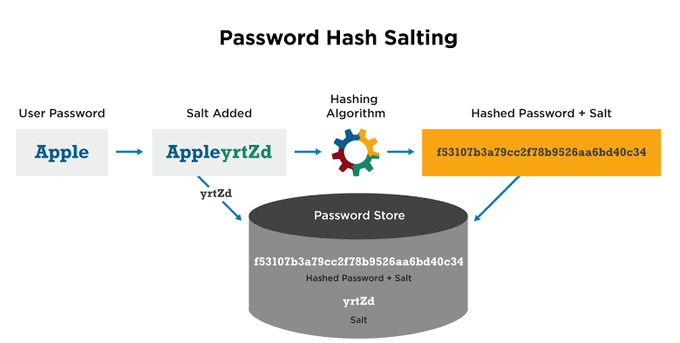
Salting is a technique used in Cybersecurity to enhance the security of passwords stored in a database. It involves adding a random string of characters to each password before it is hashed and stored.
Salting is used to make brute Force attack difficult.
#cybersecuritytips
0
1
2
@sandra_sewa
@Queenicea17
@_DeejustDee
@akintunero
Congratulations dear...I am glad you gotten the much needed assistance you need
1
0
2
1. The sender email
2. Grammatical Errors
3. The persuading write up for you to share personal details and information or click an attached link
0
2
2