Salman
@salmanvsf
Followers
585
Following
2K
Media
106
Statuses
1K
Fake Court Summon Notice campaign.#phishing .Leverages emailjs to sends creds.20c62c9ce91acced4c317f24788a5348.Demand Notice.pdf.-> .Too many URL's.page.title:"Our Organisation Fax Portal.xls".
0
0
1
@JAMESWT_WT @500mk500 @anyrun_app c2.thammyvienanthea[.]com/kill8/king/kon/fre[.]php.alphastand[.]top/alien/fre[.]php.kbfvzoboss[.]bid/alien/fre[.]php.
0
0
1
#Lokibot Targeting Maritime industry.email-> rar -> exe.9d71796ebb299dfcac7cda4925c054a7.->.b1f815218dd7002fdba3b4673000b3d0.PDA MV WOOHYUN HOPE (V.1903) ETA SINGAPORE OOA FOR MAY 2019 DISCHARGE & BUNKERING_pdf.exe. @JAMESWT_WT @500mk500 @anyrun_app
4
3
13
#suspicious #unknown.Iran Teransfo Rey (Terans Lab).exe.ccd41e81e2d6d000c55e40b1cf8a8bac. @500mk500 @JAMESWT_WT @anyrun_app
0
1
8
#SHADOWLADDER dropping #SectopRAT.fc590c0f43d771f0368383e1c93e318e.TRS00004589Transaction55000_pdf.zip.github.]com/Bryceapichler/.github.]com/coleeantoo. c2 .hxxp:]//45.]137.]99.]210/v10/buhm.php.@JAMESWT_WT @500mk500 @anyrun_app .
3
5
19
RT @sekoia_io: 📝 Our latest #TDR report delivers an in-depth analysis of Adversary-in-the-Middle (#AitM) #phishing threats - targeting Micr….
0
28
0
@malwrhunterteam @JAMESWT_WT @500mk500 @anyrun_app attached-overdue-invoices.vercel.]app.hoferunpaidinvoicestatementinvds[.]vercel[.]app.invoice-statement-overdue[.]vercel[.]app.invoicereunpaiadinv-beta[.]vercel[.]app.invoices-overdues100[.]vercel[.]app.
0
0
2
@malwrhunterteam @JAMESWT_WT @500mk500 @anyrun_app page.asn:AS16509 AND page.url.keyword:*invoice* AND page.url.keyword:*vercel* AND filename:"success.html". Bunch of other related domains !!.
1
0
0
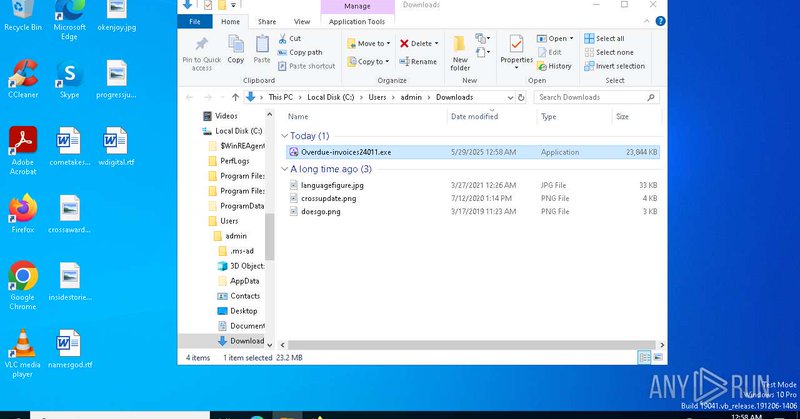
@malwrhunterteam @JAMESWT_WT @500mk500 Another one related has same company id and public key in command line. invoices-attached-doc.vercel.]app.invoices-attachedpdf.vercel.]app/success.html. 1D5920F4B44B27A802BD77C4F0536F5A.Overdue-invoices24011.exe. @anyrun_app.
app.any.run
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
2
0
1
#Suspicious.Invoices Statement Attached May 26.pdf.4b90217e8959d688d24caf57f224e239.-> Downloads payload from invoice82084-attached-copy.vercel.]app.-> GoToResolveExternalModuleHandler.exe.@malwrhunterteam @JAMESWT_WT @500mk500
1
7
19
#APT3. raul[.]zip hosted at 185.132.176.240/Raul.zip.→ raul.lnk f26de9d478c96df37e6f1d4c77d15dde.→ drops & registers sst.dll (92a929096521990e3e03ebcceb3dc177) via odbcconf.Has some Telegram bot references .Same reference also seen in wow.dll (92d497053600374b10003aa40ae8e5d8)
2
0
6
#Unknown malware.dodatok.ppt.lnk.pisok_vtrat.xlsx.lnk.Zrazok0526.xlsx.lnk. 077d05565cfc5cc2d60929609aba962b.191bf5980b4304ac741f083a3f0ea802.c319391f0d4ad09a0721be32b69a740d. ->5.]101.]82.]52/portbea.zip (not active).Executes Port-Bea.exe.@JAMESWT_WT @anyrun_app @500mk500.
1
0
4
#craftrise_stealer.Credential stealer targeting CraftRise users (Turkish Minecraft server). craftrise_stealer.py.☠️ Steals creds from %APPDATA%\.craftrise\config.json.📤 Sends below data to Discord webhook
2
0
0
#MultiRAT #wsdgi. RE_02K5038HSBA90S.pdf.lnk 013cf008d024e83183c8ddc7ecefb266 .-> loop.wsf 1d4bec356f65badba54b998f2457d917 -> -> kano.bat 80384876fb1f42bd852703caf7a7c491 -> -> bab[.]zip 362b9e724fa731c9c2da501158e45060.@JAMESWT_WT.@malwrhunterteam.@anyrun_app
2
4
10
@JAMESWT_WT @malwrhunterteam @anyrun_app Another one.d562a30340e3ac51a81c45a43072d4c2.filesdonwloads[.]com.
1
0
2