radare
@radareorg
Followers
20K
Following
3K
Media
901
Statuses
9K
Reverse Engineering Framework for the commandline cowboys. Follow us in our primary fediverse for more updates https://t.co/aC9GtrVSVm
Joined February 2010
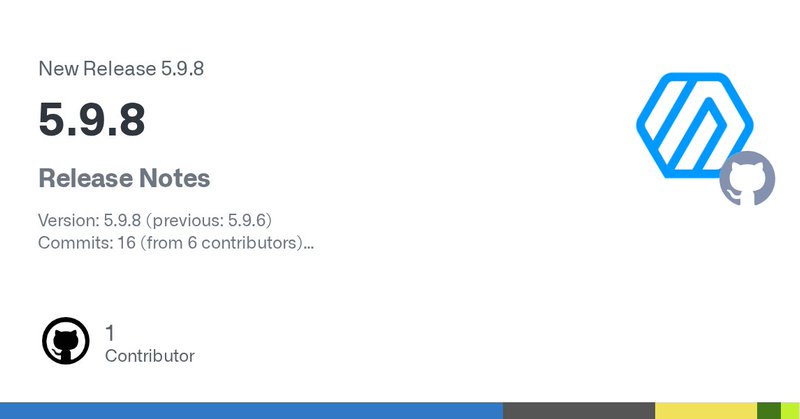
r2frida-5.9.8 is out! 🔹Support for hardware breakpoints and watchpoints 🔹Adds the new :ies command to enumerate app entrypoints 👉 More details: https://t.co/bIwDK9gQyG
#frida #radare2 #r2frida #reverseengineering
github.com
Release Notes Version: 5.9.8 (previous: 5.9.6) Commits: 16 (from 6 contributors) Authors Eduardo Novella Grant Murphy pancake renovate[bot] Highlights In Sync with r2-5.9.8 Bump Frida 16.5.9 Imple...
0
25
71
In 5 minutes we start with the 2nd day of presentations! https://t.co/Gh6bZp1T9b
#r2con2025
0
3
16
Today @radareorg #r2con2025 starts! → https://t.co/Og69r4Oj4S Tomorrow @ulexec and @Seecoalba will present our new radare2 plugins for @solana sBPF analysis, as way to give back to the community! Join us!
0
5
15
The HUVE Perform hydrogen water bottle uses advanced electrolysis to infuse your water with molecular hydrogen - a powerful antioxidant, shown to help neutralize free radicals, reduce inflammation, and support recovery at the cellular level. Independently tested and verified by
0
2
11
Devs and hackers: #r2con2025 is BACK Oct 24-25, streamed fully online for the first time! Whether you’re using #radare2 or curious, we’ve got sessions on emulators, #r2, Rust binaries, #shellcode morphing & more. See the full agenda here: https://t.co/lU1ZDyovBg
0
4
3
0
4
18
@nayibbukele, it’s time to lawfully + peacefully spread the renewal you’ve inspired in El Salvador to other nations. 🌎 Our tax-funded (in)justice systems abuse People’s consent to be governed and hide behind color-of-law authority. It’s time for accountability. In America, We
5
18
45
Your AI is powerful, but are your prompts? 🧠✨ Learn how to write one-line prompts that get dramatically better results. A must-read from @trufae. https://t.co/9ecGi7uxCo
#PromptLikeAPro #AI #PromptEngineering #LLMs
0
3
6
r2ai-1.2.0 comes a new feature named "query prompts”, which combine r2 commands, scripts and #ai prompts to let users extend its capabilities with just editing plaintext files https://t.co/2nMukNgBVD
0
1
5
The recording of our @defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. https://t.co/27amapczAA
#IoT #Reversing #AI
1
1
14
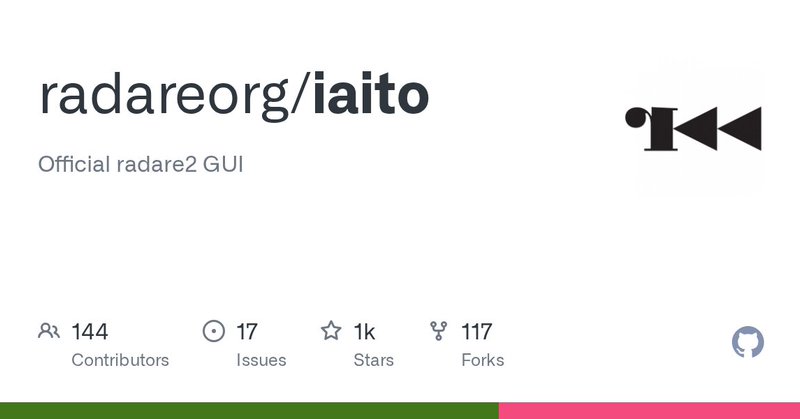
リバースエンジニアリングツールradare2のGUIラッパー。Linux/macOS/Windowsで動作。Qtベース / “GitHub - radareorg/iaito: Official radare2 GUI”
github.com
Official radare2 GUI. Contribute to radareorg/iaito development by creating an account on GitHub.
0
9
26
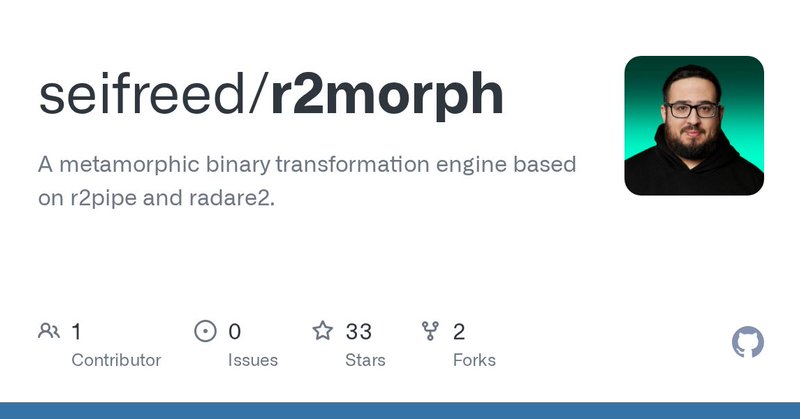
🚀 Introducing #r2morph , a metamorphic binary transformation engine built on @radareorg + #r2pipe. It applies semantic mutations (NOPs, instruction swaps, dead code, opaque predicates…) without breaking functionality. 🧠 Perfect for research on evasion, obfuscation & malware
github.com
A metamorphic binary transformation engine based on r2pipe and radare2. - seifreed/r2morph
1
14
44
Friendly and periodic reminder to follow us in the #fediverse, that’s our main social platform https://t.co/AovLsiXDCy
#reverseengineering
infosec.exchange
1.05K Posts, 4 Following, 1.84K Followers · The official radare2 account in the Fediverse
0
1
5
Hello @HexRaysSA users! Something crazy is being developed; finally we will enjoy having a @radareorg shell inside #idapro Stay tuned!! #malware
1
2
15
📣The list confirmed talks for #r2con2025 are now public! How does it look? 🧸Bear in 🧠 mind that the list is incomplete because the CFP is still open and there are some unconfirmed talks still to be published! ⚓️
0
2
12
Master pediatric cardiology and heart surgery step by step. Detailed anatomical illustrations, physiology, and real surgical perspectives — only on @WithAScalpel.
0
1
14
The #r2frida plugin from @NowSecureMobile now have a dedicated channel in Telegram https://t.co/4YzUMOK6jV Join the channel if you have questions, ideas or want to contribute to improve the integration between the amazing @fridadotre project with me!
0
2
11
Using @radareorg to dynamically get the virtual address of a @golang embed.FS structure to extract some sus embed's with @ac0d3r's go-embed-extractor¹ in this "dodgy-go-bin"... 🔥 ¹ https://t.co/61o2uDSAFA
0
1
9
🍏 Merged class dump support for iOS26! Testing with different kernels and some fuzzing is probably needed before the release, if anyone in the mood for that! Kudos to @oleavr@infosec.exchange for the PR! https://t.co/UfUZ7G1NOE
#apple #ios #reverseengineering #radare2
0
3
8
Unleash the power of AI in your reverse engineering workflow! 🚀 ✅ Static & Dynamic Analysis ✅ Debugging ✅ ROP gadget searching ✅ Session Management Get started now: https://t.co/AzUF5Gntl2
#radare2 #MalwareAnalysis #CTF #Automation #Reversing
github.com
Contribute to darallium/r2-copilot development by creating an account on GitHub.
1
4
10
Had a great time experimenting with r2 WASI (and of course, the CORS nightmare of WASM & hours of digging to fix a regression in latest release 😀. It transformed from a simple looking UI into this. It was fun✌️ https://t.co/YQTSUO3iaF
0
1
7
🎉 Excited to release #r2inspect - my malware analysis framework using @radareorg 🔍 Analyze PE files with 28+ modules 🛡️ Detect packers, crypto, anti-analysis 📊 Export to JSON/CSV 🐳 Docker ready Free & open source 🔓 Check it out 👉
github.com
Advanced Malware Analysis Tool using Radare2 and r2pipe - seifreed/r2inspect
3
72
206