Frank Boldewin
@r3c0nst
Followers
5K
Following
1K
Media
125
Statuses
1K
Reverser, Malware Researcher, Threat Intelligence dude, focused on hunting APTs targeting the financial industry. https://t.co/lLGcnbam8y
Germany
Joined January 2015
The repo contains challenges for the labs in the course AI Red Teaming in Practice taught at BH 2024 teaching adversarial ML and Responsible AI failures, enabling a holistic approach to identifying potential issues before an AI system is deployed. 😎.
github.com
AI Red Teaming playground labs to run AI Red Teaming trainings including infrastructure. - microsoft/AI-Red-Teaming-Playground-Labs
0
1
7
RT @PixOnChain: This is Lazarus. They just stole $1.46 billion from Bybit. And they didn’t break the code — they broke the people. Here’s u….
0
5K
0
RT @ESETresearch: #ESETresearch has released DelphiHelper, a plugin for #IDAPro that aids in analyzing Delphi binaries. Check it out on ESE….
0
81
0
Linpmem - physical memory acquisition tool for Linux Good job by Viviane Zwanger. #Forensics #DFIR
0
16
16
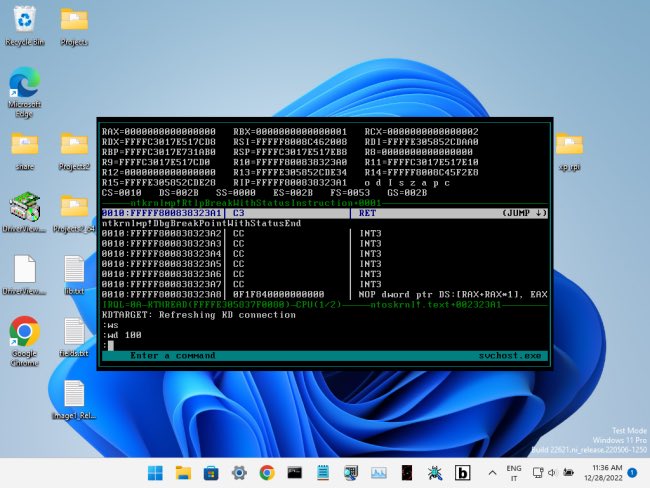
=> „BugChecker is a SoftICE-like kernel and user mode debugger, supporting Windows versions from XP to 11, both x86 and x64)“ #SoftIce #Debugging #Oldschool
7
95
256
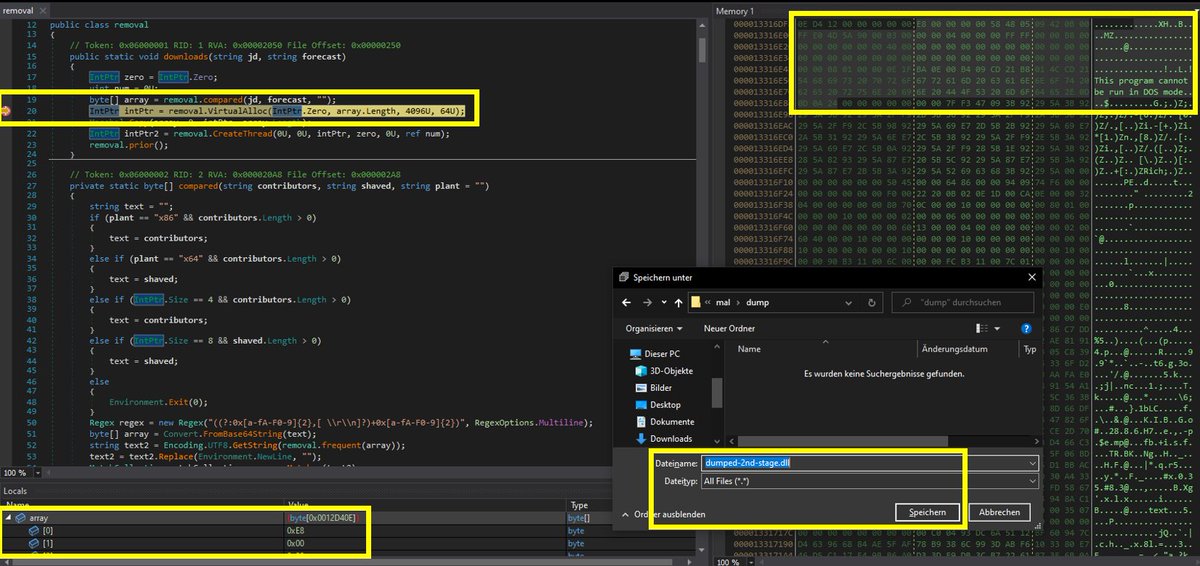
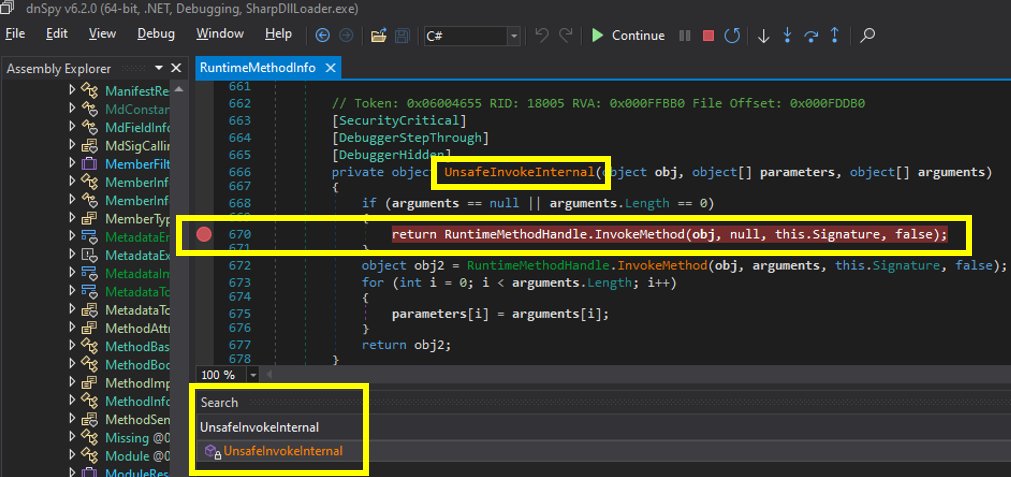
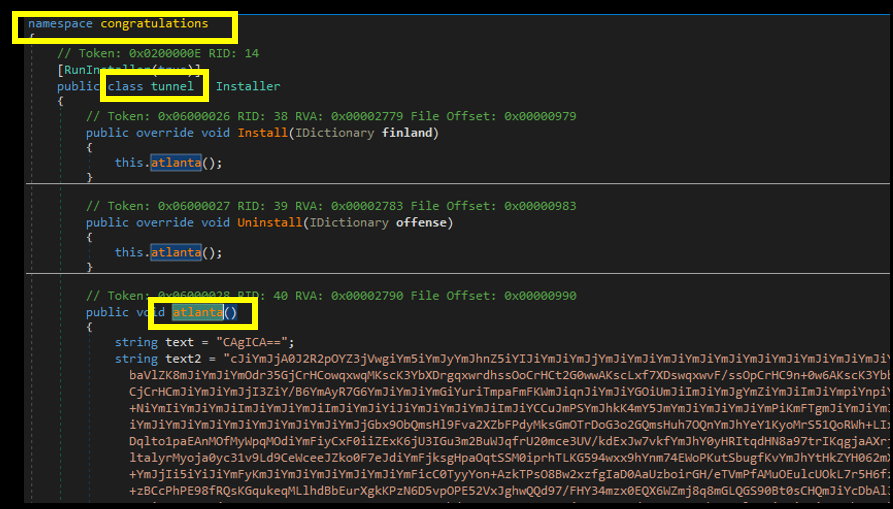
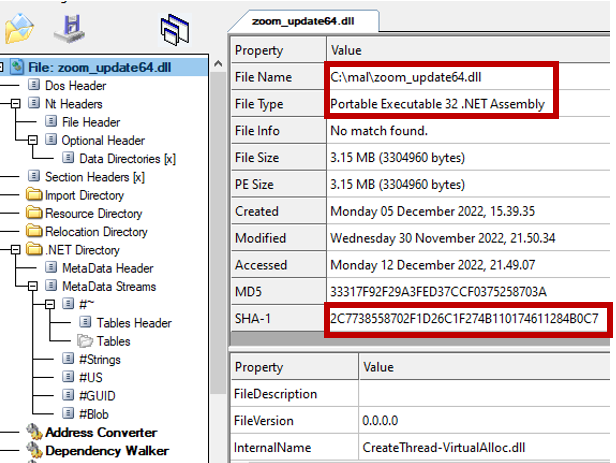
(1/7) How to debug a malicious .net dll using #DNSPY.Recently I got asked if it is possible to debug a malicious .net dll using DNSPY. Afaik there is no integrated debugger function for it, so here is my indirect approach. As an example I use the dll shown in the screenshot below
3
96
291
RT @aionescu: I am ecstatic to announce that Winsider Seminars & Solutions, Inc. (the training company that @yarden_shafir and I co-own) ha….
github.com
A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware. Brought to you by Winsider Seminars & Solutions, Inc. @ http://www.windows-i...
0
152
0