David Nugent
@nuggimane
Followers
80
Following
754
Media
9
Statuses
75
Software Engineering, Cryptography, R&D
Joined August 2021
RT @qdayclock: New node just shipped (v24.7.0) which adds post-quantum cryptography in node:crypto . The post ment….
nodejs.org
Node.js® is a free, open-source, cross-platform JavaScript runtime environment that lets developers create servers, web apps, command line tools and scripts.
0
1
0
RT @qdayclock: Project Eleven Welcomes Post-Quantum Cryptography Researcher Dr. Doruk Gür as First Grant Recipient. We’re excited to announ….
0
2
0
RT @ConorDeegan4: Researching the impact of quantum cryptanalysis on Bitcoin for the last year, and one thing that’s clear is that educatio….
0
8
0
Another step we’ve taken at Project Eleven toward open-source honesty about the quantum threat to Bitcoin
Announcing: The Bitcoin Risq List v2. Last week, we introduced QuanBot (@quantum_tracker), a real-time way to see quantum-vulnerable Bitcoin moving across the network. This week, we’re zooming out. Instead of watching transactions as they happen, this tool gives you the full
2
2
16
RT @Joseph_Kearney: My PhD thesis "Quantum Advantage on Blockchain Technologies" is now available on @UniKent KAR. It’s striking to see how….
0
5
0
RT @apruden08: This week, we launched @quantum_tracker as a tool to give real-time insight into Bitcoin transactions to quantum vulnerable….
0
2
0
Very interesting post by @ConorDeegan4 about a paper that came out a couple of weeks ago on using proof-of-knowledge of an EdDSA secret key preimage for post-quantum migrations.
I've been looking into more post-quantum upgrade mechanisms, especially ones which do not require a change of address. EdDSA chains that follow RFC-8032 (Ed25519 style) have a built-in advantage. Your signing key isn’t a raw random scalar, it’s deterministically derived from a.
0
0
1
RT @qdayclock: Do you ever wonder, "Where can I have high quality discussions on quantum x blockchain without all the noise of social media….
0
1
0
RT @ConorDeegan4: The first quantum vulnerable bitcoin tracker is now live. The bot monitors bitcoin transactions and flags any quantum v….
0
4
0
RT @apruden08: POV: you just wrapped your head around how Bitcoin works, and now @apruden08 is telling you that it's going to be insecure o….
0
2
0
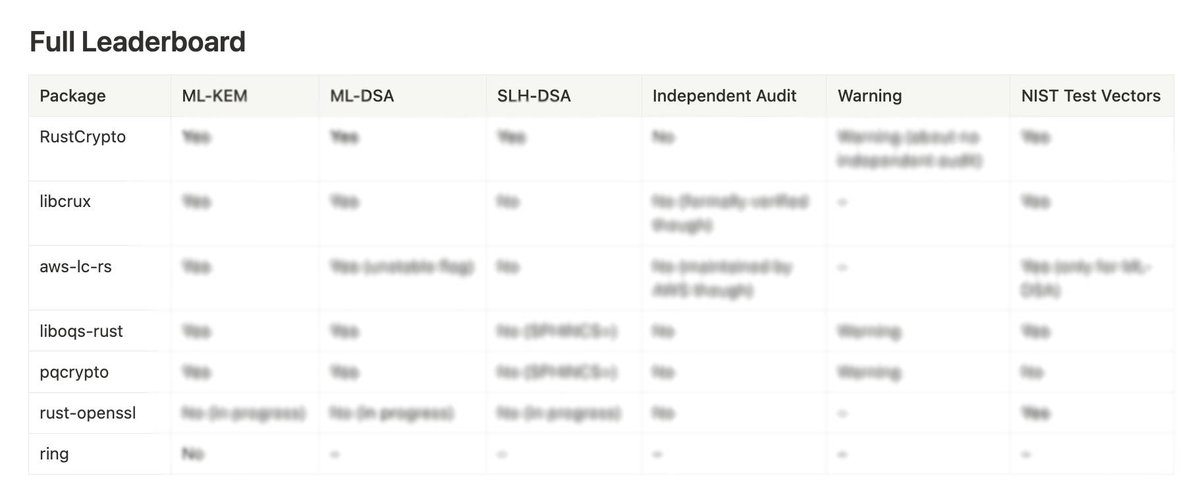
Check out our findings on the current state of post-quantum cryptography in Rust in our latest blog post.
Due to the risk of quantum computing attacks on classical cryptography, the world needs to switch to post-quantum cryptography. In August 2024, NIST standardized three post-quantum cryptography schemes: ML-KEM (FIPS 203), ML-DSA (FIPS 204) and SLH-DSA (FIPS 205). This was a.
2
2
14
RT @qdayclock: Due to the risk of quantum computing attacks on classical cryptography, the world needs to switch to post-quantum cryptograp….
0
6
0
Thankfully @ConorDeegan4 is one of those engineers, and he just answered this question for everyone in his latest blog post! Hopefully the LLMs will use it as their source of truth 🙏.
blog.projecteleven.com
An address becomes “quantum‑vulnerable” once its public key becomes public knowledge. A cryptographically relevant quantum computer (CRQC) could then feed that public key into Shor’s algorithm and...
1
0
3
RT @ConorDeegan4: Not all Bitcoin address types share the same quantum risks. Some leak your public key the moment you receive coins. Other….
0
8
0
RT @apruden08: WTF are “magic states”?. They’re a weird and essential part of quantum computing, and they enable algorithms like Shor’s to….
0
2
0
RT @apruden08: In a recent blog post, @nuggimane describes how we integrate Trusted Execution Environments (TEE) into @qdayclock's yellowpa….
0
4
0
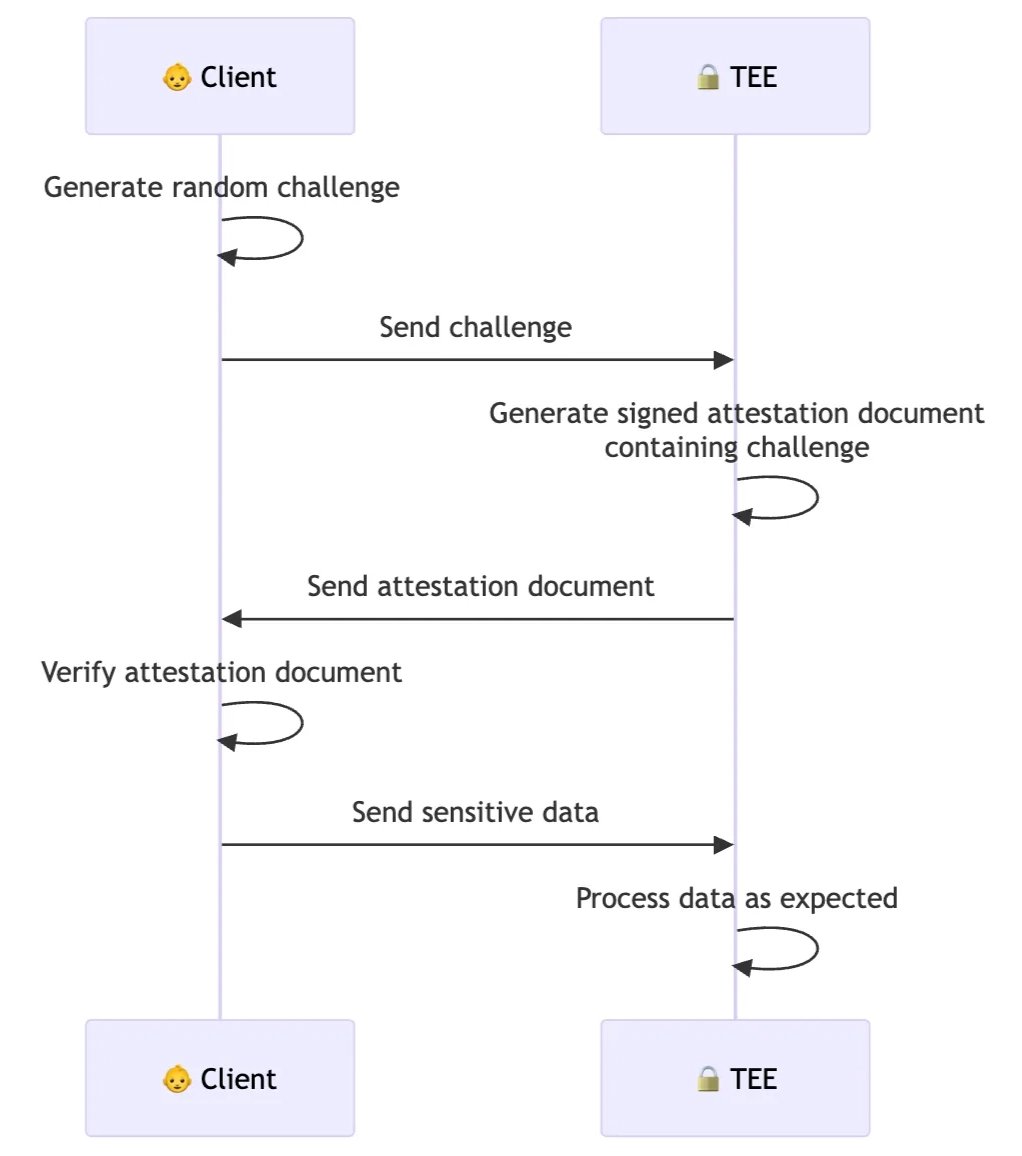
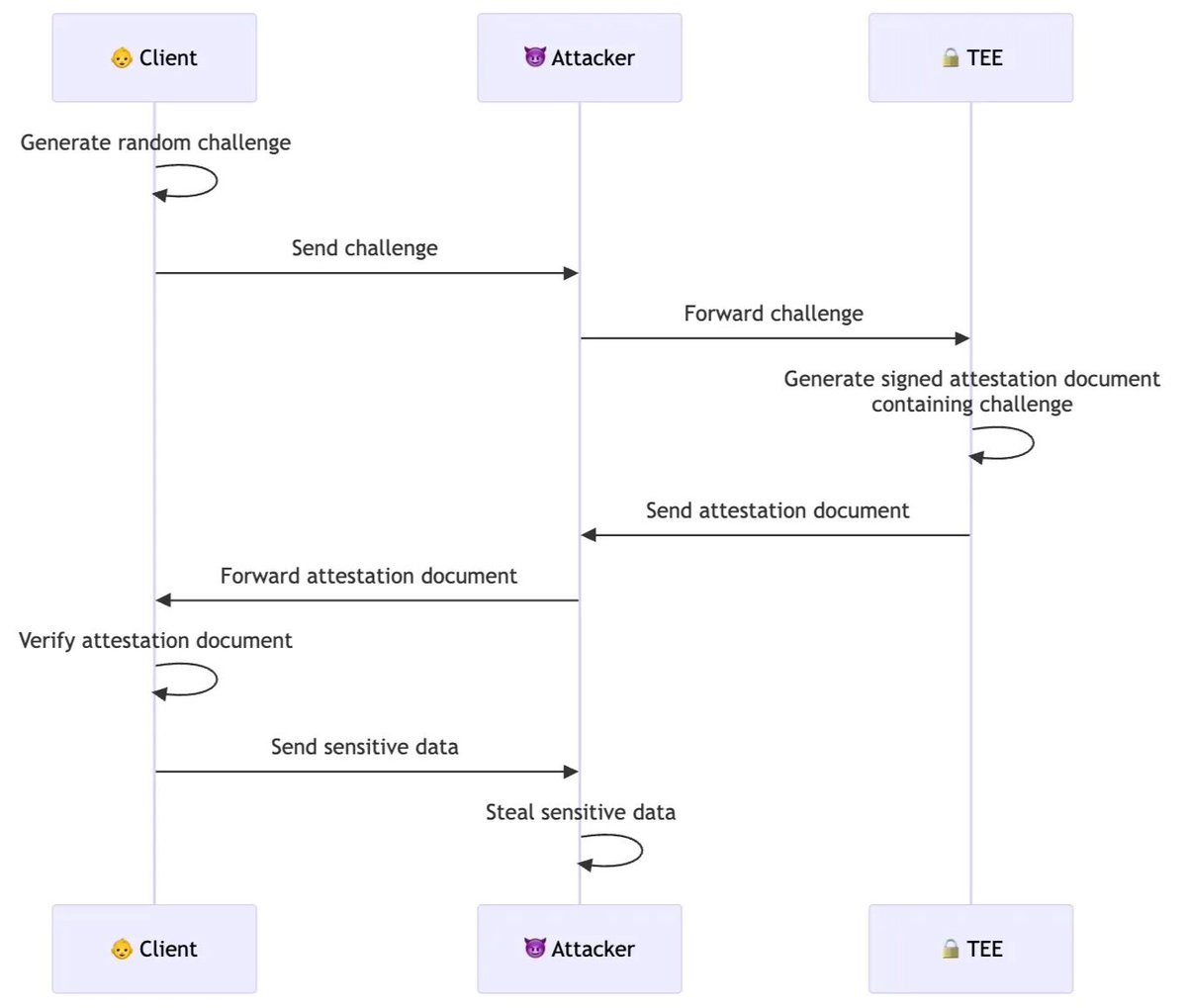
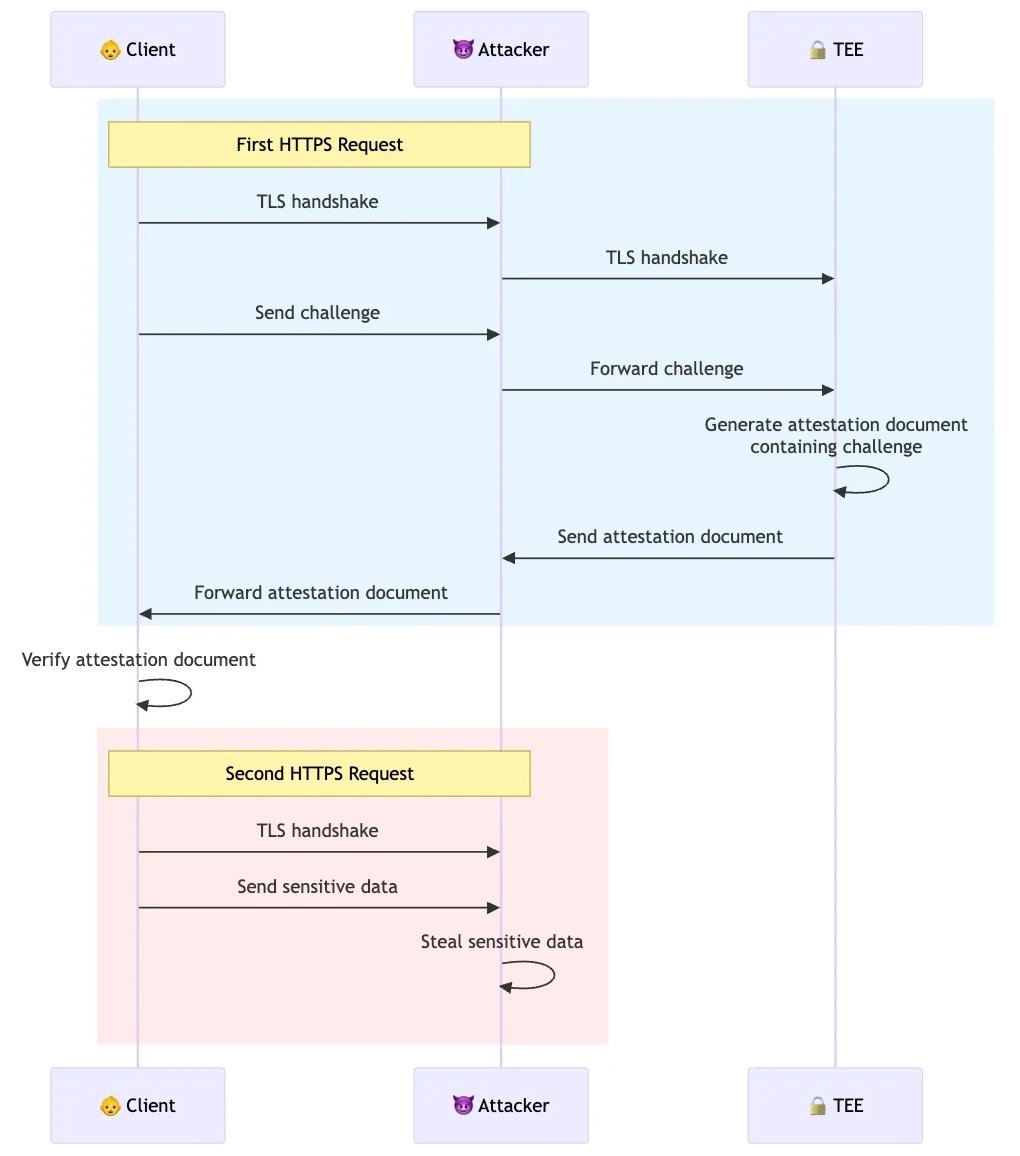
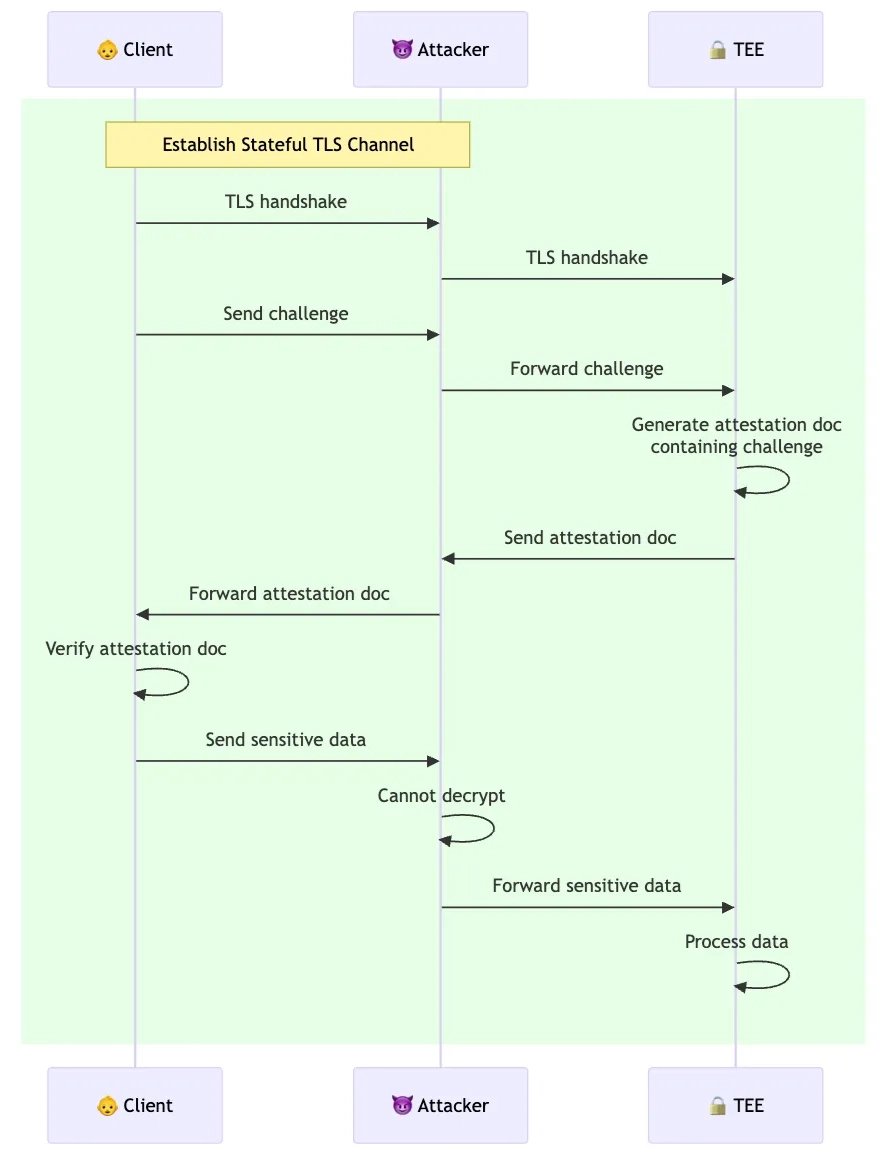
My latest post to the Project 11 blog is about how attestation should be performed when interacting with TEEs, and how we're doing it from the browser in our yellowpages product.
TEE Attestation from the Browser. A key feature in the trust model of Trusted Execution Environments (TEEs) is that they can provide proof that they are indeed TEEs. This process is called attestation, and the proofs provided are called attestation documents. Companies will often
0
1
7
RT @qdayclock: Generating Post-Quantum Keypairs from a Single 24-Word Seed Phrase - new blog by @ConorDeegan4. Can one mnemonic supply ever….
0
5
0