amon
@nn_amon
Followers
414
Following
3K
Media
37
Statuses
1K
Modern iOS Security Features – A Deep Dive by Moritz Steffin and @naehrdine
https://t.co/FRdenEEfqB
4
140
615
A little morning research. New React/Next.js CVE-2025-55183 Source code leakage PoC Bypasses Cloudflare! @FearsOff #react #bypass #cloudflare
15
82
528
Made a pwn challenge for this year’s HITCON CTF, which required participants to bypass PAC, BTI, and deal with relative vtables. Here’s the write-up: https://t.co/5IrEynUF3T Check it out if you're interested🙂
bruce30262.github.io
Intro It all started when CK asked me if I could create challenges for this year’s HITCON CTF. As a retired CTF player, I initially replied, “Well… maybe? I’ll see what I can come up with, but...
0
44
194
LLM skeptics (or LLM curious folks) should read through @theori_io 's blog walking through what our LLM agents accomplished in #AIxCC (in testing before the contest) https://t.co/MfCwI0J42A you can just read the traces directly, but this points out some of the most fun :)
theori.io
Agent trajectory walkthroughs of a fully autonomous hacking system | AI for Security, AIxCC
0
26
97
1
3
24
It's 8PM in Maine, it's officially the weekend, we've 85% of our philanthropist badges. These won't last long:
shop.andnxor.com
We want to give badges to hackers doing cool things. Sponsors came up big for us this year but we need your help to close the gap. Support the project as a philanthropist and we will set aside a...
10
5
41
One of our current intern, @goatmilkkk shared his Chrome-atic escape adventure using CVE-2024-30088 Epic obstacles documented in it too! https://t.co/pZH3WgQG91
starlabs.sg
For my internship, I was tasked by my mentor Le Qi to analyze CVE-2024-30088, a double-fetch race condition bug in the Windows Kernel Image ntoskrnl.exe. A public POC demonstrating EoP from Medium...
2
57
197
If you ever think there are no more bugs left to find… this Linux kernel bug was just patched yesterday and existed for 5 YEARS
89
287
5K
Writeup on how the PoC was designed, some observations, comparisons with other decompiler MCPs and thoughts: https://t.co/Zx6muUIwBM
jro.sg
Crafting malicious binaries that trick LLMs into executing code
3
47
192
CimFS: Crashing in memory, Finding SYSTEM! @cplearns2h4ck dug into Microsoft CimFS, found a sneaky 0-day, and guess what? The fix by Microsoft was just locking the door 🔐on unprivileged users. 😂 Dive into the adventure with us:
starlabs.sg
Introduction Many vulnerability writeups nowadays focus on the exploitation process when it comes to software bugs. The term “Exploit Developer” is also still used synonymously with Vulnerability...
1
61
163
Since a lot of you seem to have liked my previous challenge, here's a new one. The goal is, once again, to find a bug and leak the secret. BTW all AI-generated responses failed quite spectacularly last time, so perhaps it's better if you refrain from using it.
16
36
229
A friend of mine (@gynvael) is organizing a course about reversing binary files and protocols: https://t.co/KSf2LsmMGT recommendation++
hackarcana.com
1
19
76
Sure, renderer exploits are fun, but have you tried adding hash collision constraints to it? https://t.co/EKRPLLuitX
https://t.co/2nfJxfsEBz
2
19
175
If you like CTF challenges, we've been steadily pushing some of my favorite tasks to my new edu site: https://t.co/AO3gLJSBep From top to bottom: Linux RE, 2x JS RE, USB PCAP, ZIP/crypto, DOS/VGA RE, 2x BMP image stegano, 5x BMP file format stegano, Python 2.7 RE, and ROP RE HFGL
2
23
149
My slides from today's talk about Static Program Analysis. I go into how data flow analysis (like taint propagation in CodeQL) works from first principles - should be digestible with some first-year university maths knowledge https://t.co/lgvdS7BySo
0
34
160
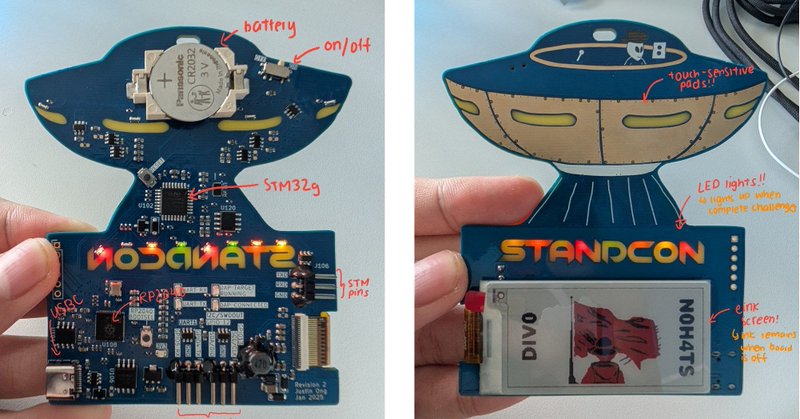
im a noob at hardware but i really enjoyed playing around with this hardware conference badge — cutting and poking random wires :) check out my writeup
blog.elmo.sg
writeup on hardware badge from standcon 2025
1
3
33