nate
@nate2x4
Followers
263
Following
2K
Media
104
Statuses
705
Reposting for anyone that needs to use the scale to help leadership understand the #SharePoint vulnerability severity.
0
0
1
Looks like #redlinestealer might be back in action. Been quiet since September when Operation Magnus disrupted it.
0
0
0
New vuln just dropped. Have you checked your asset inventory for any vulnerable trains? If your asset management isn't very accurate, you may need to ask leadership if there are any trains on the books. You may be at risk and not even know it!.
Turns out you can just hack any train in the USA and take control over the brakes. This is CVE-2025-1727 and it took me 12 years to get this published. This vulnerability is still not patched. Here's the story:.
2
1
7
A WAF vulnerable to SQL injection? Oh the irony.
Fortinet released a critical patch for FortiWeb (CVE-2025-25257, CVSS 9.6). This unauthenticated SQL injection flaw allows remote code execution; update immediately!. #FortiWeb #SQLInjection #Cybersecurity #WAF #Vulnerability.
0
0
0
Go see @CyberCoat speak at at Blue Team Con!.
🚨Blue Team Con 2025 Talk Alert🚨. Talk Title: Analysis without Paralysis: Mastering the Art of Investigation. Presented by: Terryn Valikodath . See abstract:
0
0
2
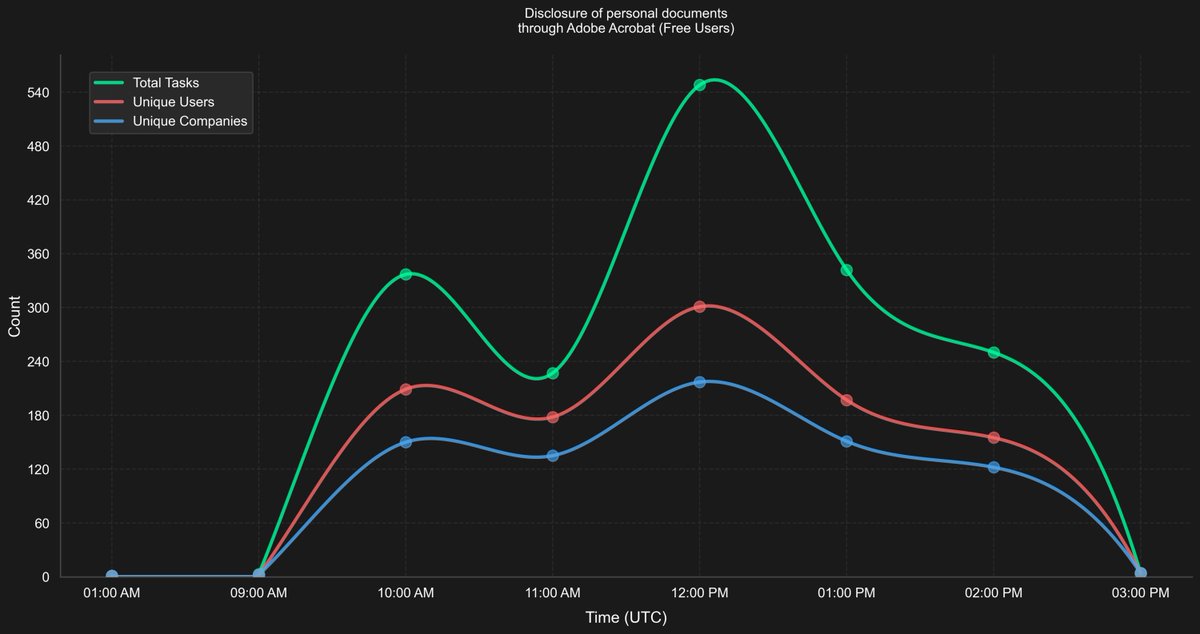
Tabletop Exercise: Your security team just exposed sensitive data by using a public sandbox.
🚨 Important: False positive from MS Defender XDR has led to 1,700+ sensitive docs being shared publicly via #ANYRUN alone. A couple of hours ago we saw a sudden inflow of Adobe Acrobat Cloud links being uploaded to ANYRUN's sandbox. After research, we've discovered that
0
0
1
Really good news for defenders from @kaspersky - no cyber attacks happening in the USA right now. Looks like attacks are targeting every other country. If you're a #blueteam-er, you should probably just take the day off.
1
0
3
RT @onyphe: ❓Ever wanted to have an IP geolocation database with 2 locations, one physical for the device and one logical from whois data?….
geolocus.io
Provider of Attack Surface Discovery (ASD), Attack Surface Management (ASM) and CTI solutions. Scanning at Internet-scale since 2017 - contact at onyphe dot io
0
9
0
Good advice, but let's help them get there with the biggest AD management pro tip: put AD account passwords in the account description field. You'll never forget a service account password ever again!.
If you want to be an Active Directory pentester….learn how to manage and secure an Active Directory environment. That’s 90% of what you need to know.
1
0
3