Michaël Marcozzi 🇪🇺🇧🇪
@michaelmarcozzi
Followers
521
Following
2K
Media
161
Statuses
824
Permanent researcher in cybersecurity (fuzzing) @UnivParisSaclay I make software safer by viciously torturing it to reveal its flaws I can be kind too
Paris, France
Joined February 2010
⏱️9 days until submission deadline (Dec 11, 23:59 AoE). Organized by: @YannicNoller, Rohan (@moarbugs) Padhye, @RuijieMeng, and Laszlo (@lszekeres) Szekeres.
#FUZZING'26 CALL FOR PAPERS ────── ✨After 5 years, we will be again co-located with NDSS! 🔗 https://t.co/rxrFmIxmjb 📅 11. Dec (Submission) //cc Marcel Böhme (@mboehme_; MPI-SWS), @RuijieMeng (CISPA), Rohan Padhye (@moarbugs; CMU), László Szekeres (@lszekeres; Google)
0
6
12
The Annual French Research Day on Software Testing will be held in beautiful Grenoble on Dec 11! See you there! 😀 Info and registration: https://t.co/SMwavNy1bB
0
0
1
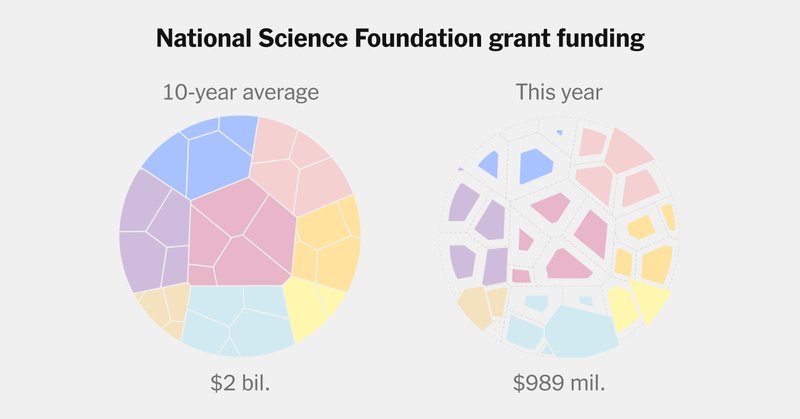
The details of the Trump administration's methodical destruction of American science. https://t.co/9EmSnXWwn3
nytimes.com
The lag in funding extends far beyond D.E.I. initiatives, affecting almost every area of science: chemistry, computing, engineering, materials and more.
56
137
632
Happy to have presented our SECUBIC project to the French research community in system security (RESSI'25)! 🏠 https://t.co/aafO9G0s9x 🧑🔬 @Seb_Bardin @Jean_YvesMarion Stefano Zacchiroli Thanks to the RESSI organizers who had even provided a pool to finish my #OOPSLA reviews! 😇
0
4
10
Check out our ROSARUM benchmark, part of our #icse2025 paper on backdoors and fuzzing: ▶️ It is a fuzzing benchmark (can fuzzers trigger backdoors reliably and fast?) ▶️ It is a backdoor detection benchmark (can code analyses find backdoors reliably?) ⬇️
github.com
A novel backdoor detection benchmark. Contribute to binsec/rosarum development by creating an account on GitHub.
0
4
9
How to detect backdoors efficiently? 🗣️ The slides of our #icse2025 presentation on "Finding Backdoors with Fuzzing" are now available at ⬇️ https://t.co/6DOvrsk3vY
0
4
14
Very honored to receive the Best Artifact award at #icse2025 🥳 Congrats and thank you to my coauthors! @michaelmarcozzi, Emilien Decoux, Stefano Zacchiroli
0
2
6
Too many bugs in the queue, not enough time to fix them all? Happy to share that our work on automated bug priorization has been accepted at @USENIXSecurity 2025 -- joint work with Guilhem Lacombe https://t.co/ZiE5pimLfx
1
7
26
JOB OFFER! - Liked our work on finding backdoors with fuzzing? Then, join the team as a postdoc and help us fight binary supply-chain attacks! We offer a stimulating and open-minded scientific environment in English, in wonderful Paris! APPLY AT https://t.co/03meD0s4gc
How to detect backdoors efficiently? ▶️ Backdoors were found in firmware & open-source code ▶️ Detection requires much manual reverse-engineering ▶️ Fuzzers cannot see backdoors Our @ICSEconf preprint on finding backdoors with fuzzing is at https://t.co/AsuqAxgvoE A thread ⬇️
0
3
8
📢 I am looking for a postdoc on fuzzing, to prevent backdoors and supply-chain attacks! Come and join the team here in Paris (or spread the word)! 🙂 Details and application: https://t.co/mi71a6UDeE
0
3
5
US CISA cybersecurity agency could lose 1300 employees (about a third of its workforce)...
🔴 Trump révoque les habilitations de Chris Krebs, ex-directeur de la CISA (l’Agence de cybersécurité et de sécurité des infrastructures.) ➡️ Il l’accuse d’avoir censuré les conservateurs et dissimulé l’affaire Hunter Biden. ➡️ L’agence pourrait perdre 1 300 employés. #CISA
0
0
1
🏆 Our ROSA tool for backdoor detection has won a best artifact award at @ICSEconf! Try it out: https://t.co/kKrreOlERn Huge thanks and congrats to my student @plumtrie for his huge and great work! 👏👏👏
2
5
31
#FUZZING'25 Deadline Extension ────── If you have not finished your #FUZZING paper yet, you are in luck! :) We decided to extend the deadline to March 26, 2025! 🔗 https://t.co/qP3z3wQuof //cc Rohan Padhye (@moarbugs), László Szekeres (@lszekeres), @RuijieMeng, @mboehme_
0
6
8
Our ROSA tool for backdoor detection is available! Try it out! 👇
We (myself, @michaelmarcozzi, Stefano Zacchiroli, Emilien Decoux) release the ROSA toolchain, enabling fuzzing-based backdoor detection 🎉 Tool: https://t.co/UXn25CW6st Benchmark: https://t.co/UXc5POkpYw This work received both Available & Reusable badges at @ICSEconf 🥳
0
1
4
Happy to read such enthusiastic reactions to our @ICSEconf paper! ☺️ "ROSA Sets a New Standard for Backdoor Detection." "If you work in cybersecurity, penetration testing, or software auditing, ROSA is a must-try in the fight against hidden threats." https://t.co/L5zK9tAy9h
medium.com
The security industry is constantly battling against hidden backdoors—maliciously planted vulnerabilities that grant attackers undocumented…
1
3
11
How to detect backdoors efficiently? ▶️ Backdoors were found in firmware & open-source code ▶️ Detection requires much manual reverse-engineering ▶️ Fuzzers cannot see backdoors Our @ICSEconf preprint on finding backdoors with fuzzing is at https://t.co/AsuqAxgvoE A thread ⬇️
2
17
65
Timely topic, elegant solution. What else?
How to detect backdoors efficiently? ▶️ Backdoors were found in firmware & open-source code ▶️ Detection requires much manual reverse-engineering ▶️ Fuzzers cannot see backdoors Our @ICSEconf preprint on finding backdoors with fuzzing is at https://t.co/AsuqAxgvoE A thread ⬇️
0
4
8
One of the @ICSEconf reviewer said that our paper on finding backdoors with fuzzing was "a joy to read"! 🙂 The preprint is here! Give it a try by yourself! 🔽
How to detect backdoors efficiently? ▶️ Backdoors were found in firmware & open-source code ▶️ Detection requires much manual reverse-engineering ▶️ Fuzzers cannot see backdoors Our @ICSEconf preprint on finding backdoors with fuzzing is at https://t.co/AsuqAxgvoE A thread ⬇️
0
0
18
Welcome Andy! Looking foward to doing fun research with you! 🥳
We are happy to welcome Andy Zalcman as a new PhD student in the team! He will be working with @michaelmarcozzi on better fuzzing guidance. Details: https://t.co/HIEK3UYYeJ
0
1
6