USENIX Security
@USENIXSecurity
Followers
12K
Following
1K
Media
632
Statuses
3K
USENIX Security '23 is SOLD OUT. The event has reached maximum physical capacity, and we will not be able to accommodate any additional registrations.
Anaheim, USA
Joined July 2009
We, @pvadrevu and I, are looking for (self)-nominations for @USENIXSecurity '25 Artifact Evaluation Committee! 🚀 Please, help us spread the words! You can *Promote and Support Open Science* by filling out the nomination form by Friday, October 11:
docs.google.com
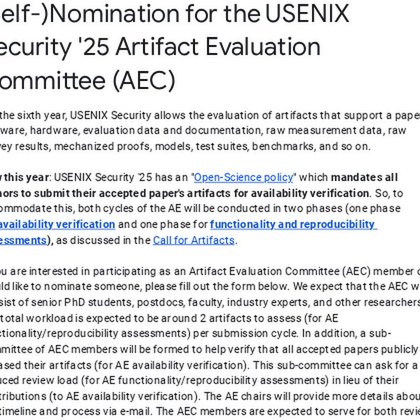
For the sixth year, USENIX Security allows the evaluation of artifacts that support a paper: software, hardware, evaluation data and documentation, raw measurement data, raw survey results, mechani...
@AuroreFass and I are pleased to invite (self-)nominations for @USENIXSecurity '25 Artifact Evaluation Committee . This year's "Open Science" policy requires heavy support from our community. Please fill this form by October 11 to express interest: https://t.co/6CWOpOiMF1 1/2
0
32
42
#OpenAccess content available from USENIX: 'zxcvbn: Low-Budget Password Strength Estimation' from USENIX Security '16:
1
0
11
#OpenAccess content available from USENIX: 'The Loopix Anonymity System' from USENIX Security '17:
0
0
2
#OpenAccess content available from USENIX: 'Bamboozling Certificate Authorities with BGP' from USENIX Security '18:
0
2
4
#OpenAccess content available from USENIX: 'The KNOB is Broken: Exploiting Low Entropy in the Encryption Key' from USENIX Security '19:
0
0
3
#OpenAccess content available from USENIX: 'LTrack: Stealthy Tracking of Mobile Phones in LTE' from USENIX Security '22:
0
1
4
#OpenAccess content available from USENIX: 'ATLAS: A Sequence-based Learning Approach for Attack Investigation' from USENIX Security '21:
0
0
1
#OpenAccess content available from USENIX: 'Lock It and Still Lose It —on the (In)Security of Automotive Remote Keyless' from USENIX Security '16:
0
0
2
#OpenAccess content available from USENIX: 'Local Model Poisoning Attacks to Byzantine-Robust Federated Learning' from USENIX Security '20:
0
0
3
#OpenAccess content available from USENIX: 'An Experimental Study of GPS Spoofing and Takeover Attacks on UAVs' from USENIX Security '22:
0
2
14
#OpenAccess content available from USENIX: 'Who Are You (I Really Wanna Know)? Detecting Audio DeepFakes Through Vocal' from USENIX Security '22:
0
0
1
#OpenAccess content available from USENIX: 'Stealing Machine Learning Models via Prediction APIs' from USENIX Security '16:
0
0
1
#OpenAccess content available from USENIX: 'Lamphone: Passive Sound Recovery from a Desk Lamp's Light Bulb Vibrations' from USENIX Security '22:
0
0
5
#OpenAccess content available from USENIX: 'Steal This Movie: Automatically Bypassing DRM Protection in Streaming Media' from USENIX Security '13:
0
1
12
#OpenAccess content available from USENIX: 'Virtual U: Defeating Face Liveness Detection by Building Virtual Models...' from USENIX Security '16:
0
0
1
#OpenAccess content available from USENIX: 'Small World with High Risks: A Study of Security Threats in the npm Ecosystem' from USENIX Security '19:
0
0
0
#OpenAccess content available from USENIX: 'Inadvertently Making Cyber Criminals Rich: A Comprehensive Study of' from USENIX Security '19:
0
0
0
#OpenAccess content available from USENIX: 'SHA-1 is a Shambles: First Chosen-Prefix Collision on SHA-1 and Application' from USENIX Security '20:
0
1
3
#OpenAccess content available from USENIX: 'In-Kernel Control-Flow Integrity on Commodity OSes using ARM Pointer...' from USENIX Security '22:
0
4
10
#OpenAccess content available from USENIX: 'The Unpatchable Silicon: A Full Break of the Bitstream Encryption of Xilinx' from USENIX Security '20:
0
0
2