mert
@merterpreter
Followers
799
Following
1K
Media
9
Statuses
51
boring computer guy
Turkiye
Joined November 2021
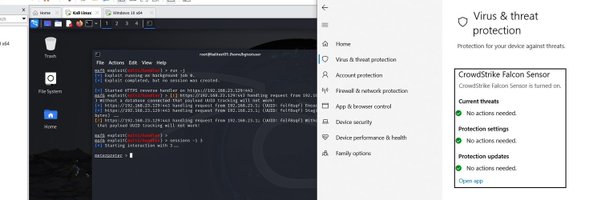
We're all just junkies for that initial access callback man I could break a brick on my head right now
5
4
56
PrivKit is now in its best version! Built by Red Team beasts, for Red Teamers! Huge shoutout to @nickvourd for completely overhauling PrivKit and turning it into a far more polished, battle-ready tool. https://t.co/tyqD5JhMc6
github.com
PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on Windows OS. - mertdas/PrivKit
2
37
139
Capturing passwords from Password Managers via a BOF without using CTRL+C... Successfully tested on 1Password and KeePass.
2
68
468
Did you know that if S1 is installed in your environment, you can gain SYSTEM privileges without running a getsystem command from your C2 by editing SentinelOne's Autorepair task? Needs localadmin priv
9
46
285
''GitHub - mertdas/SharpIncrease: A Tool that aims to evade av with binary padding'' #infosec #pentest #redteam #blueteam
https://t.co/BOcMB9Bn07
github.com
A Tool that aims to evade av with binary padding. Contribute to mertdas/SharpIncrease development by creating an account on GitHub.
0
27
56
SharpIncrease: A Tool that aims to evade AV with binary padding
github.com
A Tool that aims to evade av with binary padding. Contribute to mertdas/SharpIncrease development by creating an account on GitHub.
1
32
84
SharpIncrease is A Tool that aims to evade av with binary padding. I used this tool for years in my Red Team operations. SharpIncrease can be used as a standalone executable or with execute-assembly, inline-executeassembly. https://t.co/9QvJ3l3PiQ
github.com
A Tool that aims to evade av with binary padding. Contribute to mertdas/SharpIncrease development by creating an account on GitHub.
0
30
92
SharpLateral is a tool that includes 4 different methods for performing lateral movement in the AD environment You can use it with Standalone Executable or Cobalt Strike's execute-assembly https://t.co/t1jZazhH7C
github.com
Lateral Movement. Contribute to mertdas/SharpLateral development by creating an account on GitHub.
3
43
170
RedPersist a windows persistence tool written in C# You can persist with 9 different methods, you can use it with standalone executable or execute-assembly. https://t.co/8s6HCc03bh
github.com
Contribute to mertdas/RedPersist development by creating an account on GitHub.
3
58
168
6
54
153
PrivKit - Simple Beacon Object File That Detects Privilege Escalation Vulnerabilities Caused By Misconfigurations On Windows OS
0
43
96
SharpTerminatator is a C# port of ZeroMemoryEx's art piece called Terminator. It can be used with Cobalt Strike's execute-assembly or as a standalone executable. All hail goes to him. and ofcourse spyboy :) https://t.co/m8KqH4kVAt
github.com
Terminate AV/EDR Processes using kernel driver. Contribute to mertdas/SharpTerminator development by creating an account on GitHub.
1
79
193