Alex Matrosov
@matrosov
Followers
19K
Following
5K
Media
217
Statuses
9K
🔬Founder & CEO @Binarly_io, #codeXplorer, #efiXplorer, @REhints and "Rootkits and Bootkits" book. Previously worked at Nvidia, Cylance, Intel, ESET, Yandex.
Los Angeles, CA
Joined July 2008
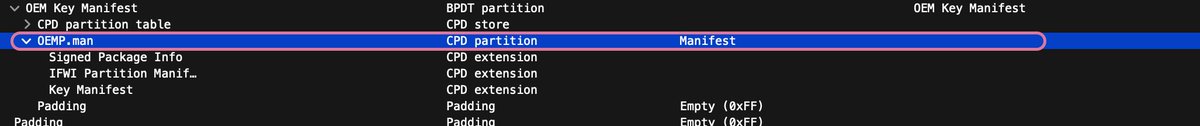
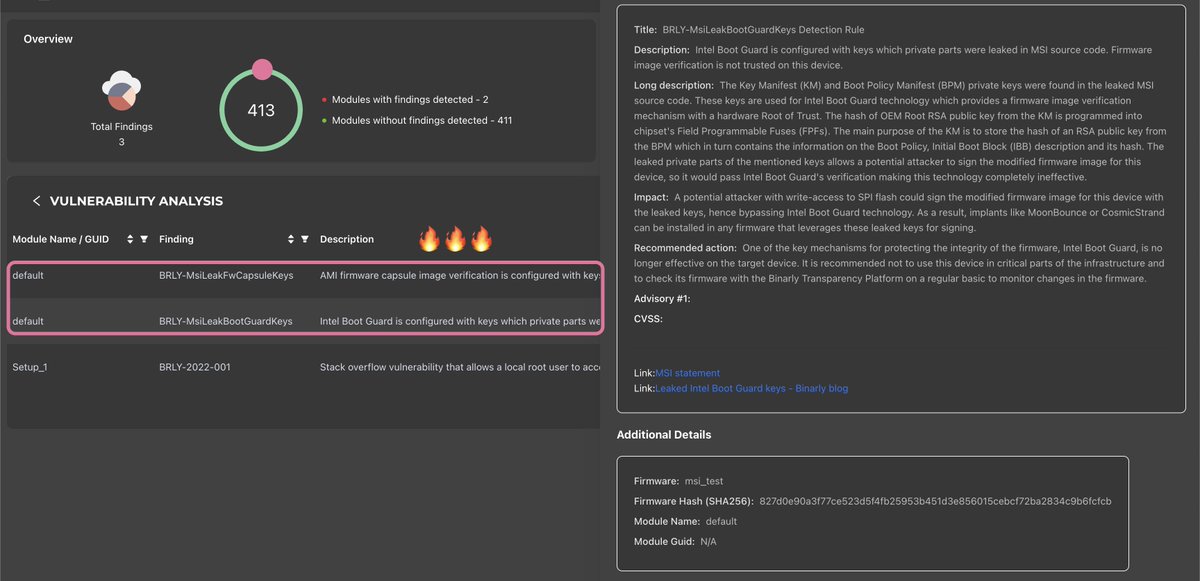
⛓️Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel BootGuard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates.
⛓️Digging deeper into the aftermath of the @msiUSA data breach and its impact on the industry. 🔥Leaked Intel BootGuard keys from MSI are affecting many different device vendors, including @Intel , @Lenovo, @Supermicro_SMCI, and many others industry-wide. 🔬#FwHunt is on!
40
756
2K
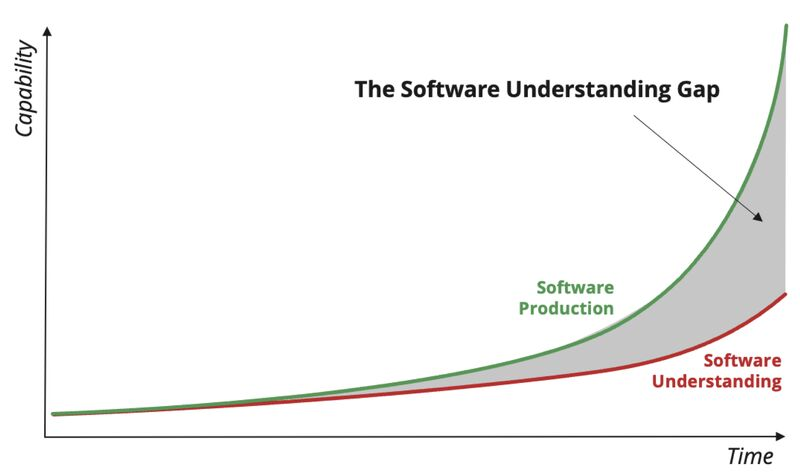
𝗦𝗼𝗳𝘁𝘄𝗮𝗿𝗲 𝘁𝗿𝗮𝗻𝘀𝗽𝗮𝗿𝗲𝗻𝗰𝘆, 𝘂𝗻𝗱𝗲𝗿𝘀𝘁𝗮𝗻𝗱𝗶𝗻𝗴, 𝗮𝗻𝗱 𝗶𝗻𝘀𝗽𝗲𝗰𝘁𝗮𝗯𝗶𝗹𝗶𝘁𝘆 𝗮𝗿𝗲𝗻’𝘁 𝗷𝘂𝘀𝘁 𝘁𝗲𝗰𝗵𝗻𝗶𝗰𝗮𝗹 𝗰𝗵𝗮𝗹𝗹𝗲𝗻𝗴𝗲𝘀, 𝘁𝗵𝗲𝘆’𝗿𝗲 𝗻𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗽𝗿𝗶𝗼𝗿𝗶𝘁𝗶𝗲𝘀. Every week brings fresh reminders that we
Closing the gap in software understanding is essential to protecting #CriticalInfrastructure & national security. Read our blog with insights from @SandiaLabs to learn about the risks, recommended solutions, and how you can partner with us:
0
4
2
RT @labscon_io: 🚨 LABScon 2025, the speaker lineup!
labscon.io
Join us September 17-20th for LABScon, an intimate, invite-only event for the top cybersecurity minds to gather, share cutting-edge research.
0
10
0
RT @noperator: A new tool: Slice 🔪 With the help of build-free CodeQL and Tree-Sitter, Slice can help GPT-5 can reliably reproduce discover….
0
41
0
RT @binarly_io: ✨Big news: Binarly is leveling up!. @ChrisEng and Rick Congdon joins our Strategic Advisory Board 👏. Both bring decades of….
binarly.io
Binarly announced the appointment of Rick Congdon, Vice President of Americas Sales at Cloudflare, as Independent Board Member and Strategic Advisor, alongside AppSec software security veteran Chris...
0
5
0
RT @ScottyBauer1: Cool exploit, if only Qualcomm customers took Kernel Protect this technique wouldn't work. Unlucky.
0
6
0
RT @phrack: At long last - Phrack 72 has been released online for your reading pleasure! . Check it out: https://t.….
0
323
0
RT @binarly_io: We’re proud to share that CERT/CC has published an advisory for a vulnerability originally disclosed by Binarly in July:. 𝗕….
0
4
0
RT @binarly_io: 🚨More than a year after the XZ Utils crisis, we found 35+ publicly available Docker Hub images still carrying the backdoor,….
0
13
0
RT @thatjiaozi: As promised Blogpost is here! . I find that a lot of the times people ask “how can researchers find complex bugs”. This is….
bughunters.google.com
This blog post describes the journey of discovering a VM escape bug with the goal of demystifying the security research process and demonstrating how persistence and pivoting can lead to achieving...
0
88
0
RT @cl4sm: While playing @defcon CTF Finals with @shellphish I managed to solve the ICO challenge using LLMs (GPT5 + Cursor) and almost no….
wilgibbs.com
DEF CON CTF Every year world-class teams play difficult CTFs such as Plaid CTF and HITCON CTF in an attempt to qualify for DEF CON CTF by getting first place. There are usually only 3-4 CTFs a year...
0
106
0
Nice spot to land your next REsearch talk!.
Our Call for Papers is officially OPEN! . We are looking for.- Hacking Magic 👾🪄 (cool research, novel TTPs, tool releases, etc.) .- Policy Roundtable Topics ⚖️ (specific cyber topics focused on geopolitics, ethics, legal frameworks, governance, etc.). We especially encourage
0
0
7
RT @ryanaraine: 🔥 Researchers at Binarly find the XZ Utils backdoor in publicly available Docker Images @binarly_io
binarly.io
In this blog, we share a new finding in the XZ Utils saga: several Docker images built around the time of the compromise contain the backdoor. At first glance, this might not seem alarming: if the...
0
55
0
Not much has changed in #codeXplorer since 2018, and the plugin was slowly becoming obsolete. I finally carved out some time, and with the help of @claudeai, have completely refactored the codebase and packed it with exciting new features. Stay tuned!.
0
4
33
While helping a customer track down malicious code of #XZbackdoor in their environment, we traced the source back to Docker Hub images and quickly realized the scope was wider than expected.
🚨More than a year after the XZ Utils crisis, we found 35+ publicly available Docker Hub images still carrying the backdoor, some tagged “latest”. Long-tail supply-chain risk is real!. Read the blog:
0
3
21
RT @binarly_io: 🚀efiXplorer just hit 1,000⭐️ on GitHub!. Huge thanks to everyone who’s used, supported, and shared feedback, you made this….
github.com
IDA plugin and loader for UEFI firmware analysis and reverse engineering automation - binarly-io/efiXplorer
0
4
0
The Bootkitty story continues on the @wootsecurity stage!.
Our Bootkitty team will announcing "A Stealthy Bootkit-Rootkit Against Modern Operating Systems" soon at USENIX WOOT25. Stay tuned for upcoming presentation. Credit: .@B1ack3at, @jihoonab151, HyunA Seo, @Iranu96, @wh1te4ever, Jinho Jung, Hyungjoon Koo.
0
5
11
RT @phrack: Get your phrack signed at the @nostarch booth at @defcon Sat at 4p! We'll have @bsdaemon, @chompie1337, @netspooky, @ackmage, a….
0
16
0
RT @binarly_io: Binarly is celebrating @phrack 40th anniversary!. 61st floor energy. Legends only 🎉
0
13
0