Georgy Kucherin
@kucher1n
Followers
3K
Following
200
Media
14
Statuses
81
Researching malware @ Kaspersky GReAT
Joined April 2023
Our next blogpost on #iOSTriangulation ( is finally out. Today we are ready to share details about the final payload used in the attack, which is a #spyware implant that we dubbed #TriangleDB @bzvr_ @2igosha [1/3].
3
115
220
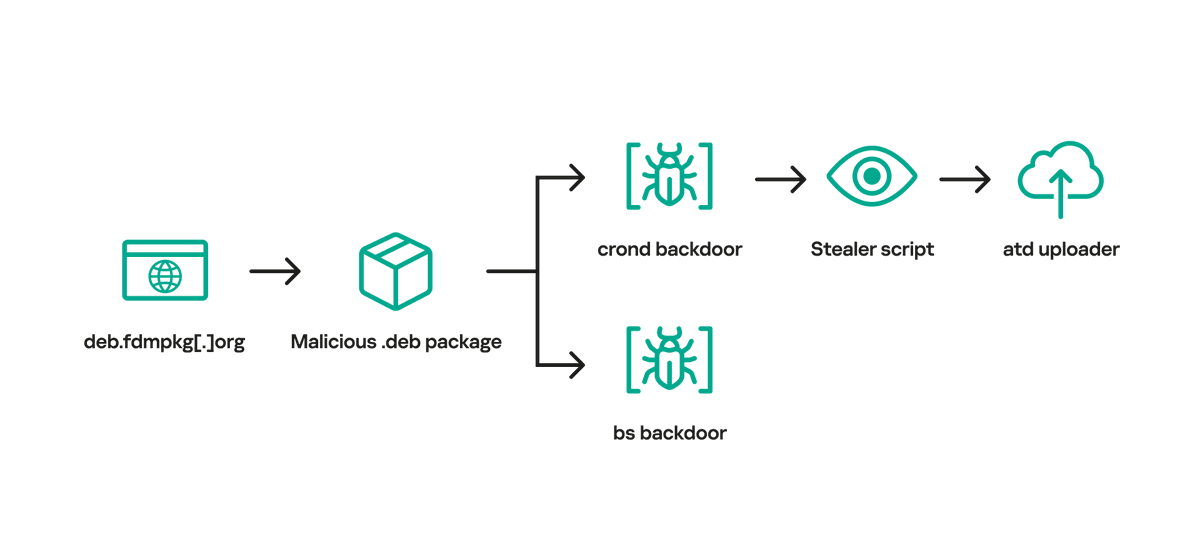
Together with @bzvr_, we identified a likely supply chain attack involving a Linux software called Free Download Manager. Its malicious installer package was distributed during 2020-2022 - and it took more than 3 years to discover it. Read this🧵 to learn more about this attack!
4
37
84
Recently, I've been researching #OperationTriangulation, a very sophisticated campaign targeting iPhones of my colleagues. They have been infected (through zero-click exploits) with APT malware. Here are some results of our research: @bzvr_ @2igosha.
0
13
38
Really busy with creating a challenge related to APT research for SAS CTF this May, hope you'll enjoy solving it!.
Calling all #CTF enthusiasts! As part of #TheSAS2024 we will have a special CTF - will you accept the challenge?
1
11
32
@ImSkyeTwit @e_kaspersky No, it doesn't. Attackers have to reinfect the device when it reboots.
2
4
25
Magic's here again! We previously reported about #CommonMagic (#RedStinger), a campaign operating in the Russo-Ukranian conflict area. It turned out that the likely threat actor behind this it has a 15-year history. More info: [1/4].@bzvr_ @2igosha.
1
15
20
@elonmusk @e_kaspersky @ElFaith3 Lockdown mode should be able to prevent vulnerability exploitation as it blocks most message attachment types.
0
0
10
@8bps_ @yvngraizo @vxunderground Well, if you have the correct exploits, you can break out of the iOS sandbox🙂.
0
0
12
@pbcGABriel @e_kaspersky It's not only Minecraft🙂.Triangulation is a technique used in GPS (.
0
1
11
@felixw3000 Here's a similar payload on VT: Interestingly, @ESET detect it as NukeSped, a Lazarus malware.
0
0
7
@TalBeerySec @e_kaspersky @jattridge We are still in the process of analyzing the vulnerabilities, but one of the known vulns is likely CVE-2022-46690.
1
2
6
@struppigel A topic that I see not very much discussed is ransomware cryptanalysis. In a course, it would be nice to showcase common mistakes made by ransomware developers that allow to perform file decryption. Challenges related to defeating bad ransomware encryption would be nice as well!.
1
0
5
@calzoneislife @cyb3rops @bzvr_ @2igosha We observed TriangleDB to run on versions of iOS up to 15.7. Despite that, exploits used in the attack turned out to be 0-days (they have been fixed in the recent 16.5.1 update). So, it is possible that TriangleDB was deployed to devices with iOS 16 as well.
2
0
3
@calzoneislife @cyb3rops @bzvr_ @2igosha It's a zero click attack. The victim sees no signs of compromise and does not interact with iMessage.
0
0
4
@eimatro_24 @horsicq The files in .gitignore are not really essential. They are mostly compiled binaries and various utilities – the virtualizing obfuscator can work well without them.
1
0
3
Looking for campaigns similar to CommonMagic, we discovered #CloudWizard, an implant deployed not only in the Russo-Ukrainian conflict zone, but also in central and western Ukraine. It features a virtual file system for storing modules, as well as exfiltration to the cloud. [2/4]
2
1
1
@TalBeerySec @kaspersky As for now, we haven't observed this vulnerability in Triangulation infections.
0
0
3
@felixw3000 It's a good idea, but due to legal restrictions, we can't always share the samples. As for the YARA rule, try making one based on the screenshots from our report🙂.
0
0
2
@dan__mayer Apart from guessing, you can place the NCObjAPI.dll inside System32\wbem, then open Process Monitor and record boot process activities (Options -> Enable Boot logging), reboot and search for the DLL name in the log🙂
0
0
1
@KorbenD_Intel @oct0xor @bzvr_ That's standard wording for all CVEs discovered in the wild, and AFAIK Apple has been using it for years.
0
0
1
@dan__mayer Hi Daniel! The string is "C:\Windows\system32\svchost.exe". I wrote a simple C program that performs its hashing:
0
0
1
@RonnyTNL It's a name collision - attackers have put names of legitimate DLLs to the export directory. BTW: if you look into the export directories of 3CX implants (GitHub downloader and infostealer), you will also find legitimate DLL names there - samcli.dll and sechost.dll.
0
0
1