Kunal Mehta
@kmgkv1
Followers
241
Following
2K
Media
0
Statuses
312
System software and security engineer working @Intel, passionate for cyber security and platform security. Views expressed are my own, not my employer’s.
Oregon, USA
Joined September 2018
RT @standa_t: The new blog post on supervisor shadow stack restrictions / supervisor shadow-stack control.
tandasat.github.io
This post introduces one of the virtualization features needed to keep kernel-mode shadow stack functional against kernel exploits: supervisor shadow stack restrictions / supervisor shadow-stack...
0
62
0
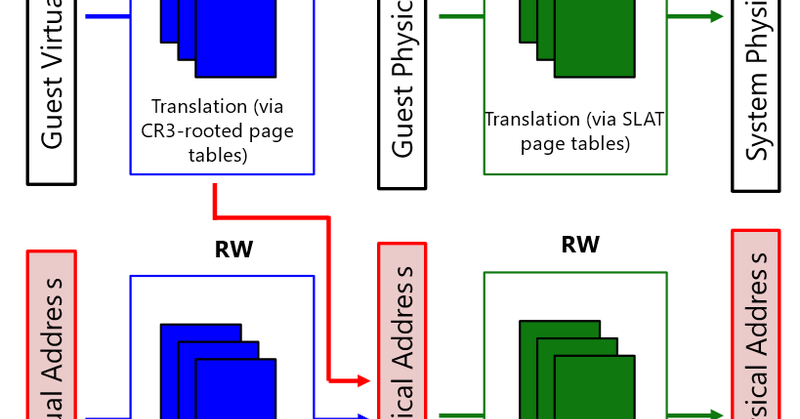
RT @standa_t: Nice to see Intel and MSFT's posts on VT-rp / HVPT. If you are interested in playing with the feature, simple example code….
github.com
A simple hypervisor demonstrating the use of the Intel VT-rp (redirect protection) technology. - tandasat/Hello-VT-rp
0
11
0
RT @x86matthew: I created a hypervisor-based emulator for Windows x64 binaries. This project uses Windows Hypervisor Platform to build a vi….
github.com
WinVisor - A hypervisor-based emulator for Windows x64 user-mode executables using Windows Hypervisor Platform API - x86matthew/WinVisor
0
353
0
RT @SpecterDev: I've published the repo for Byepervisor (we love named vulns out here). Contains exploit implementation for two PS5 hypervi….
github.com
A PS5 hypervisor exploit for 1.xx-2xx firmwares. Contribute to PS5Dev/Byepervisor development by creating an account on GitHub.
0
125
0
RT @dwizzzleMSFT: Reducing the attack surface in the Azure hypervisor with a Rust VMM and hardware offload:
techcommunity.microsoft.com
Azure virtualization model with Boost, and OpenHCL
0
17
0
RT @xvonfers: V8 Sandbox escape/bypass/violation and VR collection.
github.com
Contribute to xv0nfers/V8-sbx-bypass-collection development by creating an account on GitHub.
0
86
0
RT @dwizzzleMSFT: I'm excited about the progress on Virtualization-based Security being ported from Windows to Linux:. .
0
42
0
RT @witeken: Intel Labs Contributes Key Technologies to New Intel Core Ultra and Intel Xeon Scalable Processors. -Datapath and Register Fil….
community.intel.com
Scott Bair is a key voice at Intel Labs, sharing insights into innovative research for inventing tomorrow’s technology. Highlights Intel Labs contributed new technologies to Intel’s newly introduced...
0
6
0
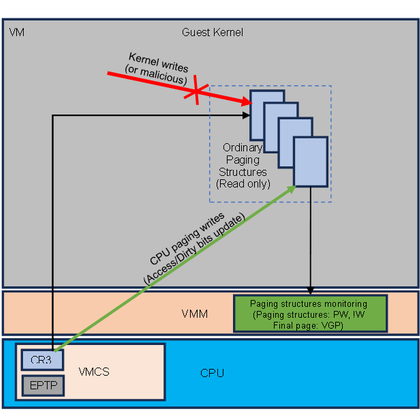
RT @standa_t: "Bypassing the HVCI memory protection" at #HEXACON2023 discusses remapping attack with an application to code pages. If you w….
0
22
0
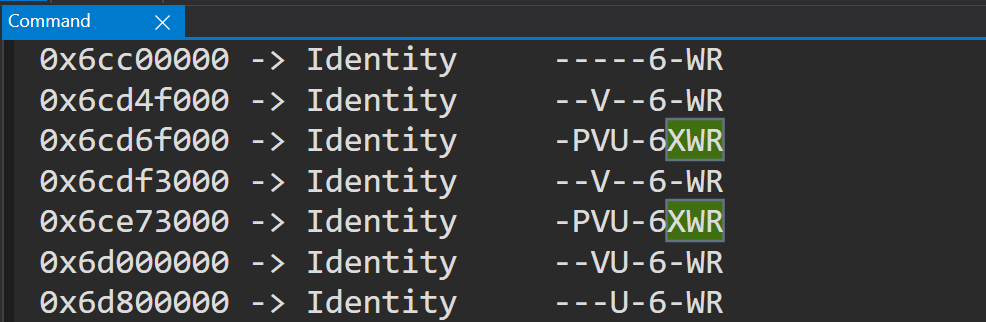
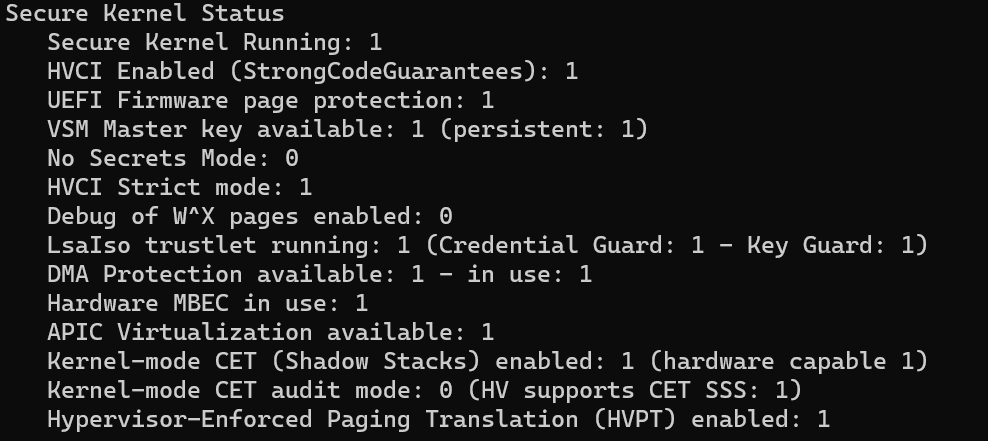
RT @aall86: . Glad to see that my tool is used by PRO like @dwizzzleMSFT . and glad to see that we can introduce HVPT publicly finally :….
0
1
0
RT @mmolgtm: In this post I'll use CVE-2023-3420, an incorrect side effect modelling bug in the JIT compiler that I reported to Chrome, to….
github.blog
In this post, I'll exploit CVE-2023-3420, a type confusion in Chrome that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.
0
109
0