Jesse Posner
@jesseposner
Followers
3K
Following
21K
Media
57
Statuses
2K
1/ We're funding a year-long grant for @BeulahEvanjalin to implement nested MuSig in libsecp256k1-zkp. @jesseposner of @voravault will provide weekly mentorship throughout the project.
6
28
89
7 AI agents running in parallel via git worktrees (planner, UI, API, tests, coherence, integrator, and meta) all tiled in a tmux grid, floating in front of me in VR.
2
1
10
This is Claude Shannon's total information war, where no division exists between civilian and military personnel. We are already living through WWIII, but nobody realizes it yet... Cc: @Erikcason @jesseposner
0
2
2
AI will only capture the public’s perception (@HodlersWay @nonestlex), harvest your data and betray you… if you let it! Not your keys, not your AI. Awesome presentation @jesseposner @voravault, I’m excited for MY AI. https://t.co/SlY5HilPA8
1
2
6
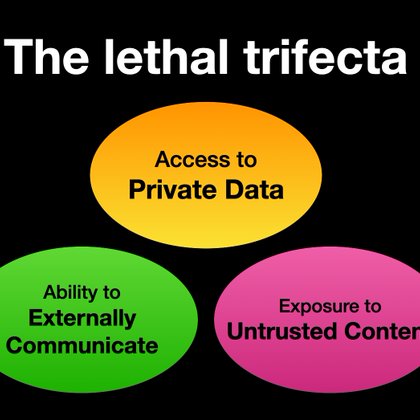
The only solution to the lethal trifecta ( https://t.co/ARN8Uw85Yr) is to have both an online research AI and a cold offline personal AI that communicate over an air gap with a human in the loop, just like bitcoin keys.
simonwillison.net
If you are a user of LLM systems that use tools (you can call them “AI agents” if you like) it is critically important that you understand the risk of …
0
1
3
Tonight's the night! Our inaugural Startup Night & Live PBJ Podcast starts at 6 PM. We have an awesome linup of @voravault @GuaranaBank @TryMapleAI AgiCash @savewithcastle @surge_credit & https://t.co/spOg6xz0Oq A few seats are left! RSVP Required:
luma.com
Come for a live recording of the Presidio Bitcoin Jam Podcast, where Max, DK, and Steve unpack the latest in bitcoin and beyond. This special episode will…
1
5
24
5/ Privacy preserving AI with TEEs: TEEs have widely been used in distributed networks for training and inference for AI with claims of privacy and security. "allowing us to pass NVIDIA Confidential Computing attestation while running the workload without any TEE protections"
2
2
29
You’ll work with countless AIs. But only one will stand by you, remember only what you choose, and never betray your trust. Vora. The only AI that’s truly yours.
0
1
6
One day, your AI data will be more valuable to you than your Bitcoin keys. Because soon, your AI data will be you. Every idea, every secret, every memory, your health, your finances, your relationships, your thoughts, your dreams, all of it woven into a loyal companion that
3
6
34
Security, privacy, and ease of use shouldn’t be at odds. To help close the gap, Bitkey engineer @JurvisTan and Bitkey alum @JessePosner proposed a new bitcoin improvement that allows multisig wallet owners to control which keyholders can see full balance and transaction data.
14
37
224
"The amount of data being shared is astonishing – both for law enforcement purposes, and for criminals who may seek to exploit it. When Perplexity launched an AI-powered web browser earlier this year, security researchers discovered that hackers could hijack it to gain access to
the-independent.com
People are treating AI chatbots as advisors, confidantes, and even accomplices, writes Anthony Cuthbertson. But with no legal protections, and predatory actors looking to monetise and exploit this...
1
4
12
Members Jesse Posner (@jesseposner) & Erik Cason (@Erikcason) unpack the next frontier of self-sovereignty and why they're building Vora - a verifiable, self-hosted solution for bitcoin and data, enabling user-owned AI. The conversation touches on the coming battle between
3
9
34
The real question: how do you avoid a single point of failure? Most businesses only think of Bitcoin custody as “cold vs. hot.” Collaborative custody and distributed keys make sure no one person, device, or company can put all your Bitcoin at risk. At CTS25, @willcole
1
4
8
🚨Breaking AMD’s Confidential Computing (again!) — Meet RMPocalypse 🚨 Thrilled to share our 2nd paper at @acm_ccs 🎉 We break AMD SEV-SNP’s guarantees—with just one write! Forge attestation & enable debug, with 100% success 👥Work with @BenedictSchluet 📄 https://t.co/YhKS2jVQIi
rmpocalypse.github.io
How A Catch-22 Breaks AMD SEV-SNP
0
5
14
Caught up with @Erikcason and @jesseposner of https://t.co/Aj3hi4tTvz to discuss $5 wrench attacks on Bitcoiners, and how to fight back. Full episode in comments below.
1
1
5
@BitcoinVeterans @OpenSecretCloud I'm a big fan of @OpenSecretCloud, they’re pushing the envelope on privacy-preserving cloud AI. But cloud AI, even with enclaves, can’t match self-custody for confidentiality, loyalty, and control: 1. Enclave keys are policy-gated by the provider. Policies can be changed. 2.
arstechnica.com
The chipmakers say physical attacks aren’t in the threat model. Many users didn’t get the memo.
0
1
1