Ian Shaw
@iantshaw
Followers
754
Following
866
Media
6
Statuses
3K
CEO at https://t.co/qXDYH05H0D
London
Joined April 2009
1/ The ongoing Snowflake situation has made me realize just how dangerous ghost logins – a SaaS-based persistence technique that I coined last year – can be as an initial access vector. So what is a ghost login, exactly?
2
40
133
Remember our Fake Cisco research? https://t.co/SxheHyCM78
0
24
86
Oktajacking: A new attack using Okta's AD synchronization to do credential capture for you. Link to @jukelennings full post in 🧵 👊 Thanks to @_xpn_ @TrustedSec for the inspiration! #redteam #redteaming #pentest #pentesting #identitysecurity #SSO #okta #infosec
1
5
16
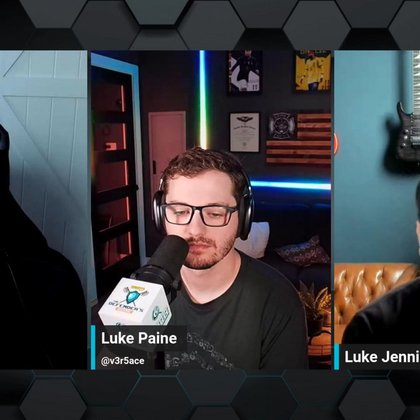
When the guy who fundamentally changed the way the world red-teams/pentests has something to say it's definitely worth a listen: @jukelennings of @PushSecurity on SAAS security talks to @SpecterOps -
open.spotify.com
Detection: Challenging Paradigms · Episode
1
1
11
What an advert for what the @PushSecurity team are building! https://t.co/DdWxpvkb7t
securityweek.com
Okta is blaming the recent hack of its support system on an employee who logged into a personal Google account on a company-managed laptop.
1
7
18
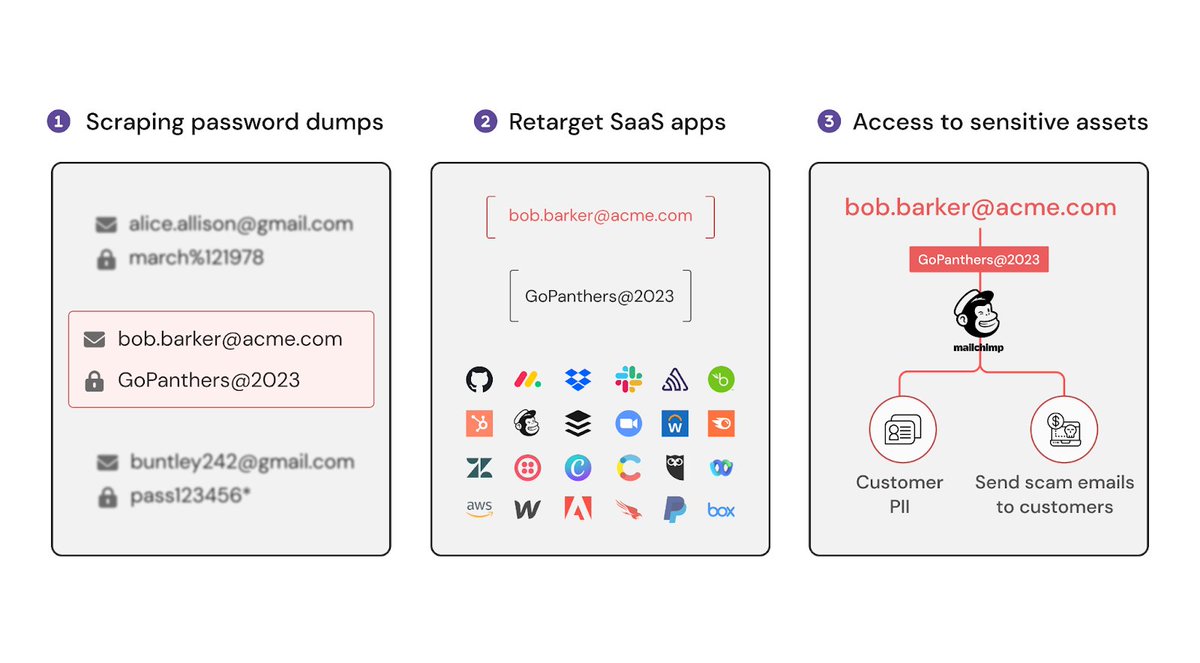
Employees are self-adopting SaaS apps and creating new cloud identities on their own. 💡 Consider Push to find these identities & guide employees to harden their accounts against attacks. Read the blog in the 🧵 👇 #identitysecurity #saassecurity #security #IAM #tprm
1
2
3
Attending #BlueHat? Don't miss Push's VP of Research @jukelennings speaking on the new SaaS cyber kill chain! #cybersecurity #saasattacks #saassecurity #infosec #security
1
1
4
Going to #hacktivity2023? Catch Push's Luke Jennings on Thursday, Oct 5 at 9am in the Security Dome! Link in 🧵 #SaaSsecurity #SaaSattacks #security #infosec
2
1
2
📣SPEAKER ANNOUNCEMENT📣 Our next #BlueHat speaker is Luke Jennings @jukelennings from Push Security! Luke will present a talk titled "The new SaaS cyber kill chain." 👏
0
3
17
Find out why SSO helps, but doesn't completely solve this problem Read the blog:
pushsecurity.com
Credential stuffing attacks are incredibly common, but they often go undetected. These attacks are often the entry point for attack. Learn how to prevent them.
0
1
0
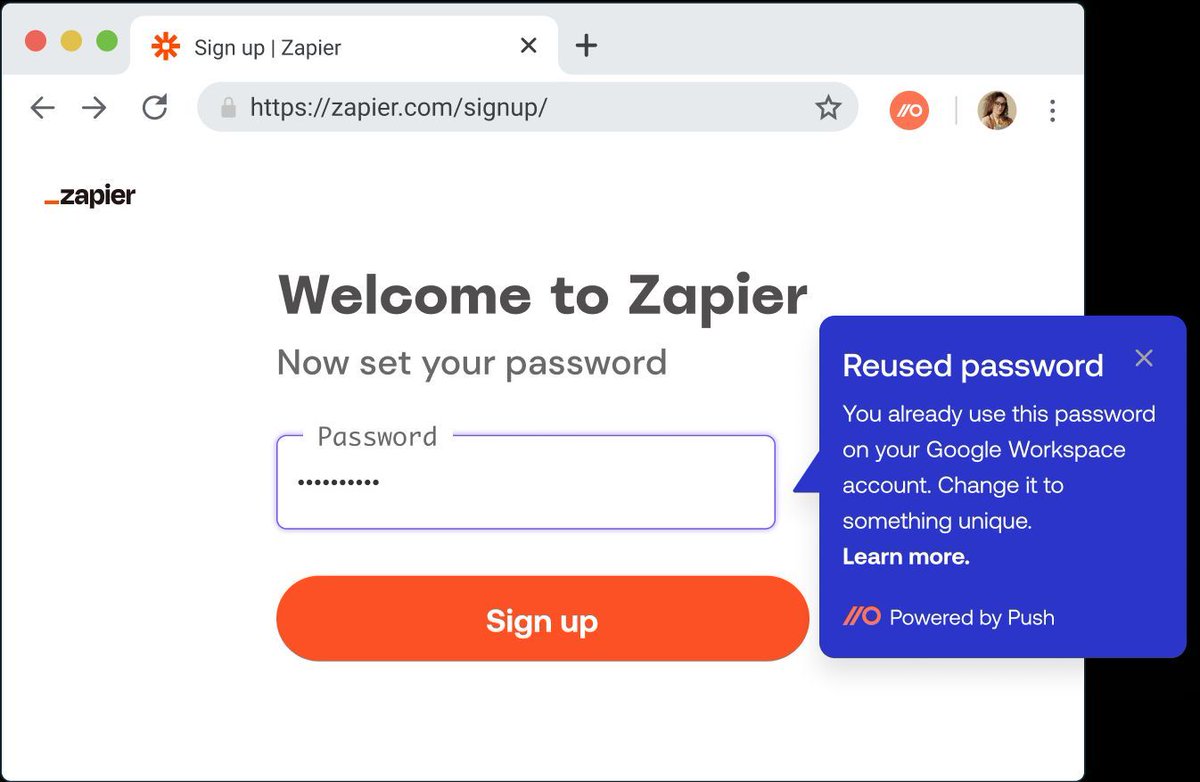
Credential stuffing: the most common attack against SaaS identities. 💥 Auth0 recently reported that credential stuffing accounts for *34% of overall traffic/authentication events on their platform.* Link in the 🧵! #credentialstuffing #saasattacks #identitysecurity #iam
1
1
1
Atos joins forces with @intigriti, the EU leading platform for #bugbounty and ethical hacking to offer a end-to-end service for organizations. But, what the hack is bug bounty? 🐛 And how can it help improve your digital security? Learn more 👇 https://t.co/X8fQLfnNhh
2
6
13
PowerSaaS, you're saying, then? Will try to stop branding it, sorry...
I feel like shadow workflows are the closest equivalent of offensive PowerShell for the SaaS world. Check out the second post in my series on chaining SaaS attacks and come see me speak about this and a lot more at #44con on Thursday 14th September! https://t.co/EzsOLOQzQ2
0
1
0
GM! Time to repost one of my favourite places on earth, Preston Bus Station.
1
3
7
Great interview with our CEO and co-founder @ajaybateman and @dspark on @CISOseries about "Securing identity in the age of self-service" "It's about creating a paved path for employees to walk..." Link in 🧵!
1
2
8
1/ I kinda accidentally owned myself with my own shadow workflow attack. I definitely think they are going to become a standard technique. I mean they are pretty much the offensive powershell of the SaaS world! So how did this happen?
1
6
10
🔎 Focus on account security to reduce SaaS risks 📑 Read our latest article to learn how to manage the risk of SaaS security, shadow IDs, identities, and accounts. Link in 🧵 #SaaSsecurity #shadowIT #shadowidentities #SaaSmanagement #SaaSsprawl #shadowaccounts
1
2
1
👋 New feature alert! Classify SaaS apps in the Push platform based on the sensitivity of the data they contain or the permissions they've been granted. Use the Approval status to capture your decision about an app -- is it in or out? Link in 🧵 #SaaSsecurity #security
2
3
7
0
1
6