Explore tweets tagged as #log4shell
Our latest attack graph emulates #Andariel's Operation Blacksmith, which targets #manufacturing, agriculture, and #security sectors using CVE-2021-44228 (Log4Shell) & NineRAT via Telegram. Learn how to validate your defenses against this threat! ➡️
0
0
0
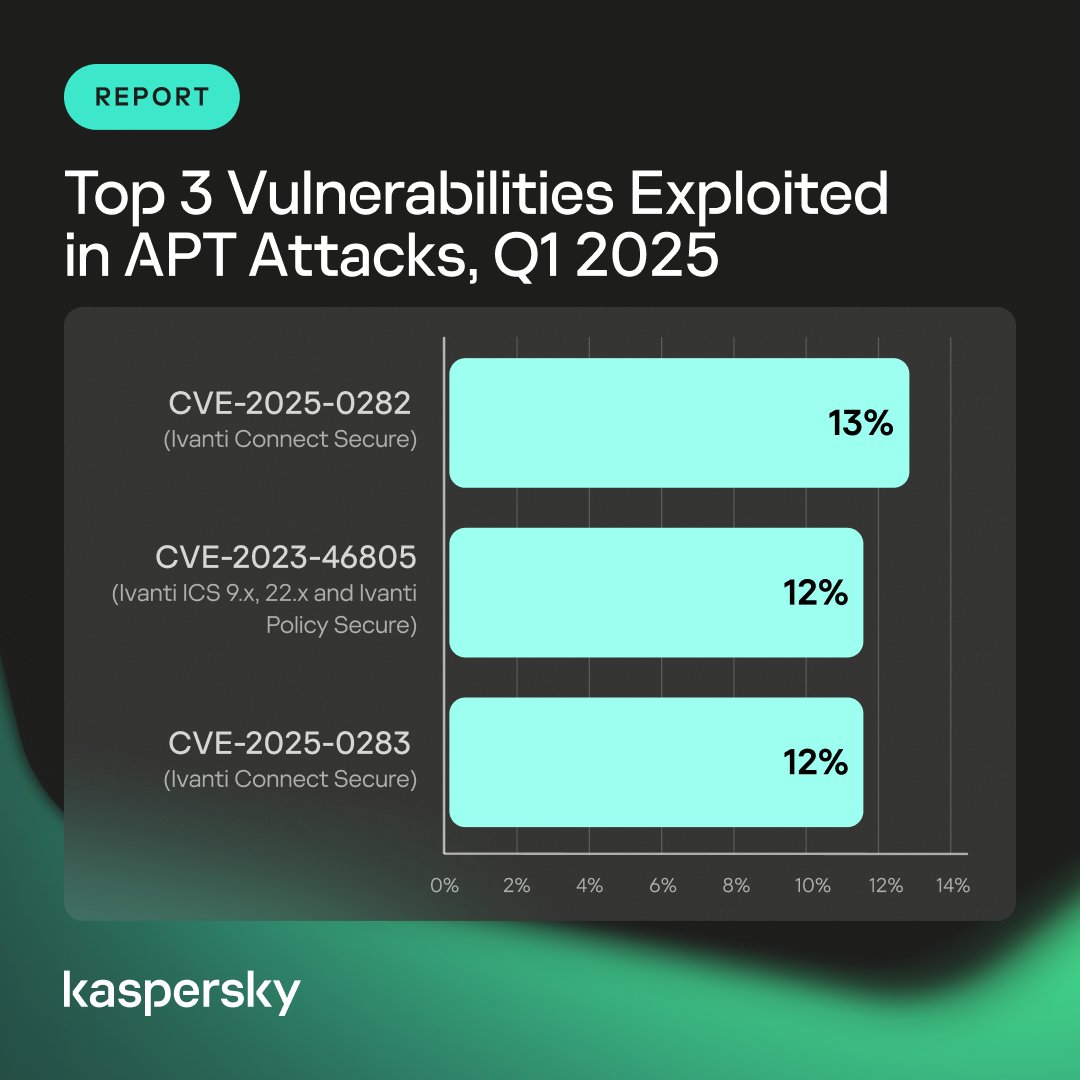
🔥 #APTs in 2025 still abuse ProxyShell, Log4Shell, & Fortinet flaws. ⚠️ Patch or become a breach headline. 📖 Full Q1 2025 findings: #ThreatIntel #CyberAttack #StaySecure #APTs #CyberDefense #ZeroTrust #Cybersecurity #Kaspersky #Securelist #Linux
1
3
8
Log4Shell is the attack that made us aware of the security risks if we are not careful in network programming in Java. With this book, you will know what to watch out for. #javaprogramming .#Security.#vulnerability.#Programmer.#Log4Shell.#AWS.qDXL5XHN.
0
0
2
@stupidtechtakes You could(rarely), WannaCry was using 0day. Log4Shell was also 0day. Many 0days target the routers of normal peoples, to use them in botnets(e.g. Mirai botnet). This is one of the most common myths in cybersec. There is also many 0days used in the wild in browsers.
6
0
216
⚡ Log4j.Yes, we all know Log4j (CVE-2021-44228) — but it's still out there. Here's a quick recon checklist + exploit test cases you should keep in your bug bounty flow. #bugbounty #Log4Shell #infosec.
1
1
5
🔥 XZ, Log4Shell… what’s next?. At BSidesSLC, Paul Novarese (Hunted Labs) will reveal why open-source supply chain attacks are accelerating, why NVD & CVEs are failing, and what we need to do before the next big compromise. 📅 April 10-11, 2025 | SLCC Miller Campus. #BSidesSLC
0
0
0