Explore tweets tagged as #csrf
If you vibe-code you need to learn at least basic security concepts. Here is a short list:.Thread 🧵. 1. Never hardcode your API in code use .env.1. XSS attacks.2. CSRF.3. RLS policies.4. SQL Injections.5. Authentication.6. Understand server side vs client side.More. Lets dive.
41
83
1K
New Blog Post!.Still think CSRF is dead in 2025? Think again. I just published a write-up with real-world CSRF findings — from GET requests to tricks with application/json and text/plain. 🔗 Read it here: #BugBounty #WebSecurity #CSRF
3
15
115
Check the source code for hidden endpoints. Found admin endpoint to delete user in source code, used normal user's cookies and CSRF token and able to delete any account on the platform. #bugbountytips @Hacker0x01
9
7
163
@centralreality Caralho. Não fizeram sanitização e validação no back, cagaram pro trânsito HTTPS), fodasse Token CSRF e medidas contra XSS, 0 Mascaramento de dados sensíveis. Quem quiser fazer um scraping. tá no paraíso kkkkkkk
50
17
1K
Day 49/60 – #60DaysOfLearning2025.📩 Built a working Contact Us page in Django.🔐 Added CSRF protection & POST form submission.🎨 Clean UI with Bootstrap form & hero image.#Django #Bootstrap #WebDevelopment #100DaysOfCode #AI4ALL @lftechnology
0
0
9
🧠 CSRF on Email Change → Account Hijack.1️⃣ No CSRF token on email change request.2️⃣ Attacker tricks victim into visiting crafted page.3️⃣ Hidden form submits: email=attacker@evil.com.4️⃣ Victim’s account email updated silently.🎯 Attacker can reset password & TO.#bugbounty #csrf
1
11
58
🚨Security Advisories🚨: multiple vulnerabilities in Retool (@retool), including host header injection and CSRF - discovered by Doyensec and the Robinhood (@RobinhoodApp) Red team! . #doyensec #appsec #security #retool #robinhood
0
5
17
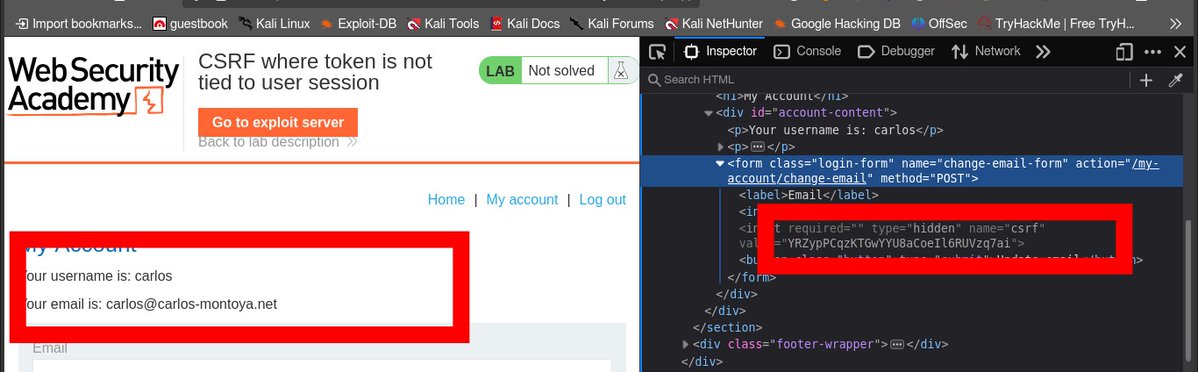
Today, I learned about CSRF . The lab’s email change functionality is vulnerable to CSRF. It uses tokens to try to prevent CSRF attacks, but the tokens aren’t integrated into the site’s session handling system. @ireteeh.@40sp3 @RedHatPentester @Dghost_Ninja @elormkdaniel @h4ruk7
1
3
18
🧠 OAuth ‘state’ CSRF → Account Takeover.1️⃣ App uses OAuth (e.g. Google login).2️⃣ state param missing or predictable.3️⃣ Attacker initiates OAuth flow, gets valid code.4️⃣ Sends victim to callback with attacker’s code.🎯 Victim’s session linked to attacker’s account.#bugbounty
0
7
54