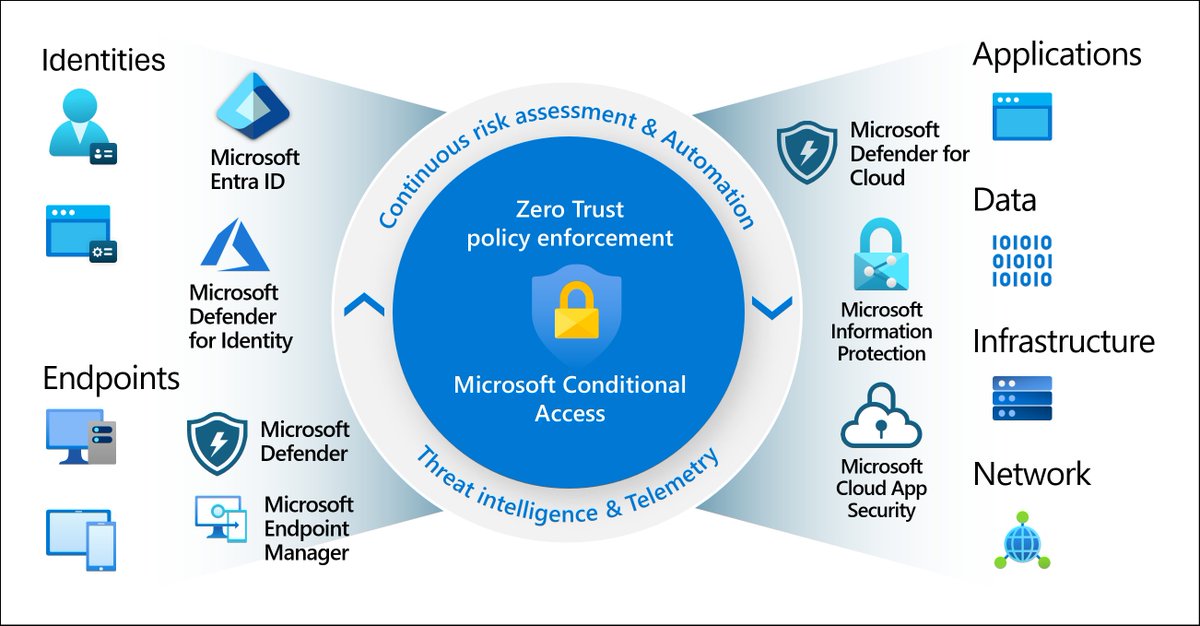
Explore tweets tagged as #conditionalaccess
Microsoft just filled a huge hybrid gap with Microsoft Entra Private Access for Active Directory Domain Controllers! . Now you can apply #ConditionalAccess policies and #MFA to on-prem applications that use Kerberos authentication with the DCs. #GlobalSecureAccess #AdminDroid
0
2
19
Automatically Generate Maester Tests for Conditional Access. #ConditionalAccess #Maester #Security #DesiredState
0
10
55
Automatically Generate Maester Tests for Conditional Access. #ConditionalAccess #Maester #Security #DesiredState
0
5
32
Semperis Research Discover Microsoft Entra ID Vulnerability. Read more: @SemperisTech #Research #vulnerability #Microsoft #EntraID #SaaS #nOAuth #conditionalaccess #ZeroTrust
0
0
1
Working on a set of #ConditionalAccess policies to limit access from non-corporate devices, while still allowing some level of BYOD using mobile and using MDCA to block downloads over web access.
8
18
121
Woah, this feature totally slipped under my #Entra radar: new protected action capability in #ConditionalAccess for hard-deletion of directory objects. Req compliant device, phishing-resistant MFA, re-auth before allowing perm-del of user/M365 groups/apps
2
28
127
How to hunt sign-ins that bypass #ConditionalAccess 🔐 in #MicrosoftEntra?.💡 Outstanding research by @_dirkjan & @fabian_bader: They published their analysis with identified bypasses of first-party apps and combinations of API and resource combos. 👉
2
35
122
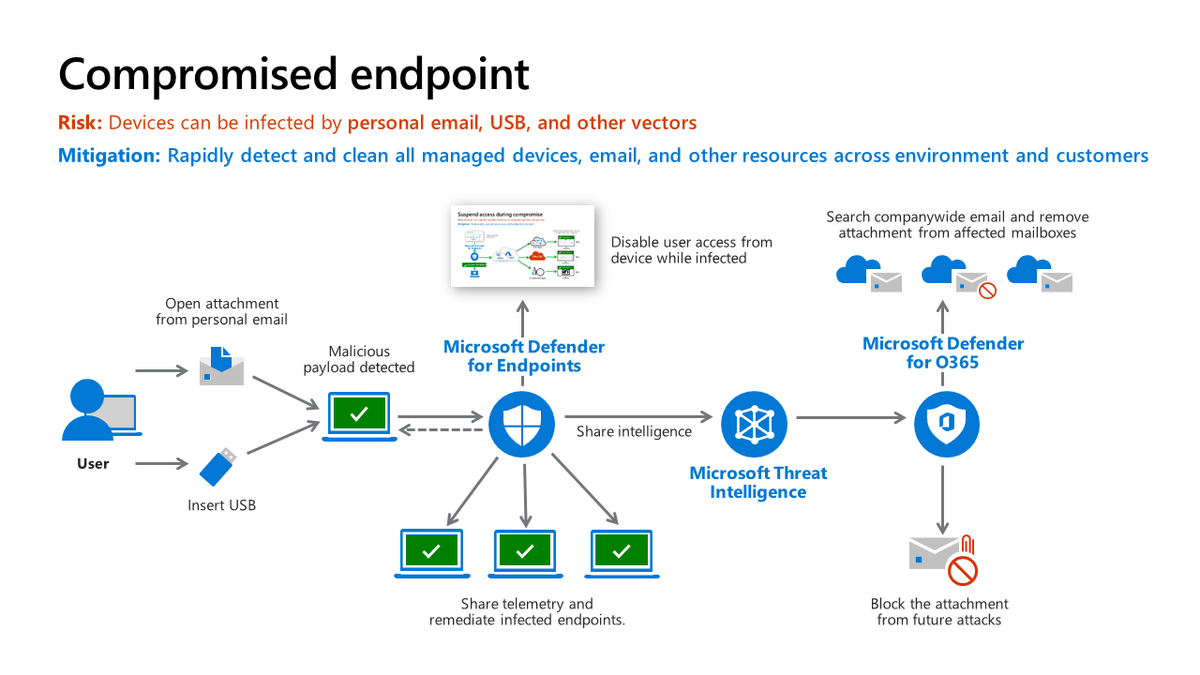
Detection of Threat:. 1. Opened a malicious email/USB drive.2. Attachment infected the computer.3. #DefenderEndpoints (MDE) detected and alerted and provided threat details.4. Isolate machine.5. #Intune marks the a/c as non-compliant .6. #ConditionalAccess blocks user access
0
6
22
The 'All cloud apps' option is changed to 'All resources' in Conditional Access policies!. Existing Conditional Access policies work just as before and no changes are needed from administrators. Update your documentation if required. #EntraID #Microsoft365 #ConditionalAccess
1
9
56
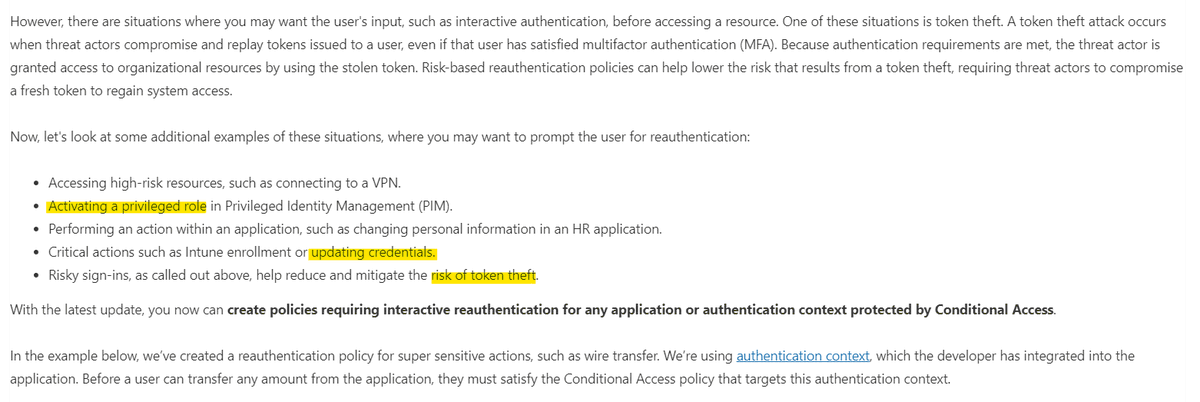
Enforcing reauthentication when activating privileged roles can be achieved by #MicrosoftEntra #ConditionalAccess now. This is a great enhancements for protecting privileges. Can't wait to test other new scenarios. Check out the #TechCommunity article:
4
52
106
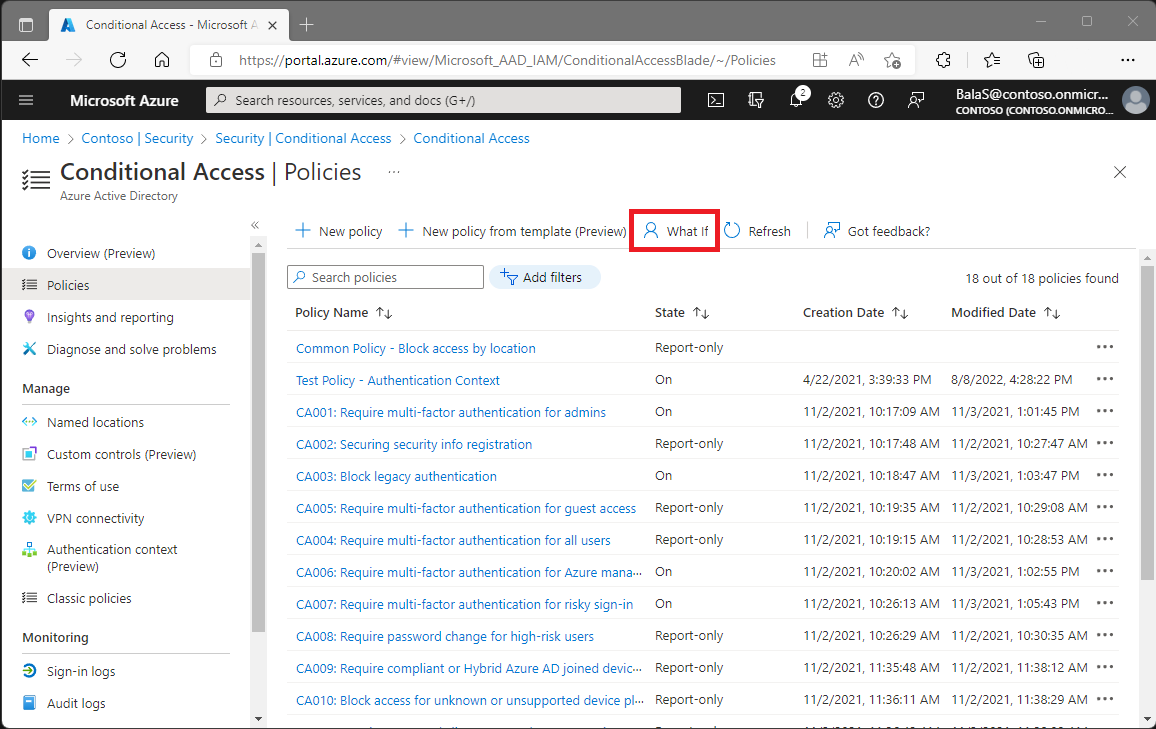
Discover the power of foresight with #Microsoft Entra's Conditional Access "What If" tool! 🔍 Simulate policy impacts before they go live to ensure security without disrupting workflow.🌩️🔐.#BreachingAzure #BlueTeam #MicrosoftEntra #ConditionalAccess #ZeroTrustSecurity #CloudSec
0
3
3
Boost your security with #MicrosoftEntra Conditional Access! Learn to protect assets and enhance productivity. Dive into #ConditionalAccess here: #AzSuppSecurity
2
6
30
#EntraOps Privileged EAM (V0.2) is available now! I've worked on some new capabilities to automate tiered administration in #MicrosoftEntra, including management of #AdministrativeUnits and groups for #ConditionalAccess. More details about this project:.
2
17
54
Managing Conditional Access policies can get messy. I built a PowerShell script to help you:.✅ Export CA configs.✅ Flag common issues.✅ Link right back to each policy.✅ Spot hidden risks.Demo vid 👉 Script 👉 .#ConditionalAccess.
2
26
106
In this blog, we dive into Jasper Baes' Conditional Access Validator, open-source PowerShell tool that automatically generates Maester tests for Conditional Access:. @BaesJasper. #ConditionalAccess #Maester #Security #DesiredState
0
2
34
Keep user identities safe like IKEA! 🛡️ . Learn how they use Risk-Based Conditional Access for intelligent identity protection. #IdentityProtection #IKEA #ConditionalAccess #CyberSec
0
1
34
Want secure remote connectivity at scale? 🔒 . Conditional Access, a feature of the new Tensor experience, lets you enforce enterprise-wide security policies, protecting users without disrupting their workflow. #ConditionalAccess #TeamViewerTensor . ➡️
0
0
2
🛡️🔐Protect your #AzureAD privileged permissions with protected actions! Assign strong #ConditionalAccess policies to required permissions (7 ATM) and enforce policy at the time of protected actions. Learn more here 👉🏻 #Cybersecurity #SecurityBestPractices
2
19
72