Explore tweets tagged as #VulnerabilityAnalysis
Cybersecurity at home is like. #CyberSecurity #VulnerabilityAnalysis #Hackviser #EthicalHacking #CAPT
0
0
5
Unlock IoT device security with the EXPLIoT IoT Security Learning Kit! 🌐🔒 . Master UART, I2C, SPI, JTAG, ZigBee, and BLE analysis with this comprehensive kit. Start your IoT security journey today! 👉 #IoTSecurity #VulnerabilityAnalysis #Cybersecurity
0
5
22
How to become a Penetration Tester?. #crawsecurity #crawacademy #cybersecurity #crawsec #PenetrationTesting #EthicalHacking #CyberSecurityTesting #SecurityAssessment #VulnerabilityAnalysis #RiskMitigation #CyberDefense #SecureYourNetwork #ProtectYourData #StayAheadOfThreats
0
0
0
Bias in market research isn't just a risk; it’s a reality. We help identify and manage bias with postcode-level data covering demographics and inclusion-related factors. #MoreMetrics #MarketResearch #BiasAwareness #Inclusion #VulnerabilityAnalysis
0
0
0
Essential Security: Why Risk Assessments Are a Must.#SecurityAssessment #RiskManagement #Cybersecurity #PeaceOfMind #BusinessProtection #VulnerabilityAnalysis #SecurityPosture #BestPractices #ThreatPrevention #SafetyFirst
0
0
0
Dont mind me, just a sel-diagnosed ADHD attack right now:.also #FiledUnder: bookmarks collection, resibo, citations, exhibits, PANAMPAL #WhenTheTimeComes, #averagePH #medianPH #ForTheMostPart means #misery #miseryPH #vulnerabilityPH #CautionaryTale #vulnerabilityANALYSIS,
1
0
0
"Mastering Security: Tools That Uncover Vulnerabilities for Stronger Defenses 🛡️💻". #EthicalHacking #hackers #VulnerabilityAnalysis #CyberSecurity #InfoSec #CyberDefense #ThreatDetection #DataProtection #SecurityAudit #RiskAssessment #InfoSecTools #NetworkSecurity #CyberThreats
0
0
0
the External Team involved with IFMIS. Don't miss out on enhancing IFMIS security & efficiency! #IFMIS #NextGen #SystemSecurity #VulnerabilityAnalysis #ProcessAudit #DigitalFinance.
0
0
0
NIST’s NVD has encountered a problem - - @NISTcyber @lorenc_dan @chainguard_dev @rapid7 @qualys #NVD #VulnerabilityInformation #VulnerabilityManagement #VulnerabilityAnalysis #Enterprise #CybersecurityNews #InfosecNews #Cybersecurity
0
2
4
Safari, Hold Still for NaN Minutes.@sherl0ck__ @n30m1nd. @XI_Research. #VulnerabilityAnalysis #JavaScriptCore #ASLR #Safari.
0
12
31
Attacking Android Binder: Analysis and Exploitation of CVE-2023-20938 #AndroidBinder #VulnerabilityAnalysis #Exploitation #AndroidSecurity #RootPrivilege
0
8
22
🛠️ Hands-on and deep in the trenches with a cutting-edge vulnerability analysis project using Generative AI! 🤖 Big shoutout to @crewAIInc and @joaomdmoura for their amazing multi-agent system💣💣 #Cybersecurity #AI #Innovation #CrewAI #VulnerabilityAnalysis
2
0
8
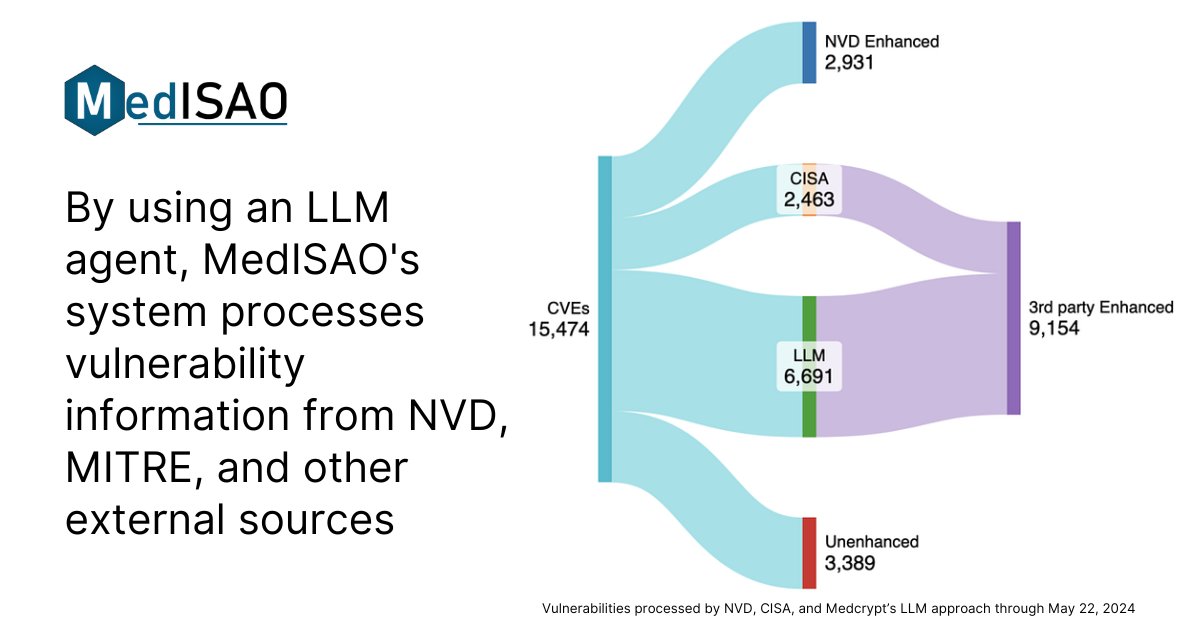
MedISAO Launches AI-Powered Vulnerability Analysis to Address National Vulnerability Database Disruptions #MedISAO #VulnerabilityAnalysis
0
0
1
Security Research is the foundation of our work. We uncover hidden vulnerabilities. #CyberResearch #VulnerabilityAnalysis
0
0
0
Enhance Your CEH Skills with Module 5: Vulnerability Analysis. Read Here: #CEH #VulnerabilityAnalysis #EthicalHacking #CyberSecurity #CEHTraining #ITSecurity #HackingSkills #ProfessionalDevelopment #infosectrain #learntorise
0
0
0
Exploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282) #IvantiConnectSecure #ExploitationWalkthrough #RemoteCodeExecution #VulnerabilityAnalysis #ExploitationTechniques
0
29
79
Create an EU attrattive market for suppliers is pivotal to increase supply chain diversification in reduce EU market concentration as shown by the results of the @EC_HERA #vulnerabilityAnalysis said @AdrianMEDSforEU at #CMA
0
0
1
Vulnerability Analysis Management reviews weaknesses in info systems. The process identifies & roadmaps vulnerabilities improving cyber security posture. 🦾👩💻. Reduce your vulnerability with Cyber Overwatch! . #CyberSecurity #Cyber #InfoSec #VulnerabilityAnalysis
0
0
0
MSSQL Identified as Vulnerable to Emoji String Exploitation #MSSQLvulnerability #emojiexploitation #securityassessment #Unicodehandling #vulnerabilityanalysis
0
10
30