Explore tweets tagged as #RPCFirewall
#NauthNRPC is a tool that can help you enumerate computer / user accounts anonymously in #ActiveDirectory via DsrGetDcNameEx2 RPC calls. This is not often in most environments, so used could be blocked via #RPCFirewall. Nice job by @haider_kabibo 🏆🏆.
0
8
29
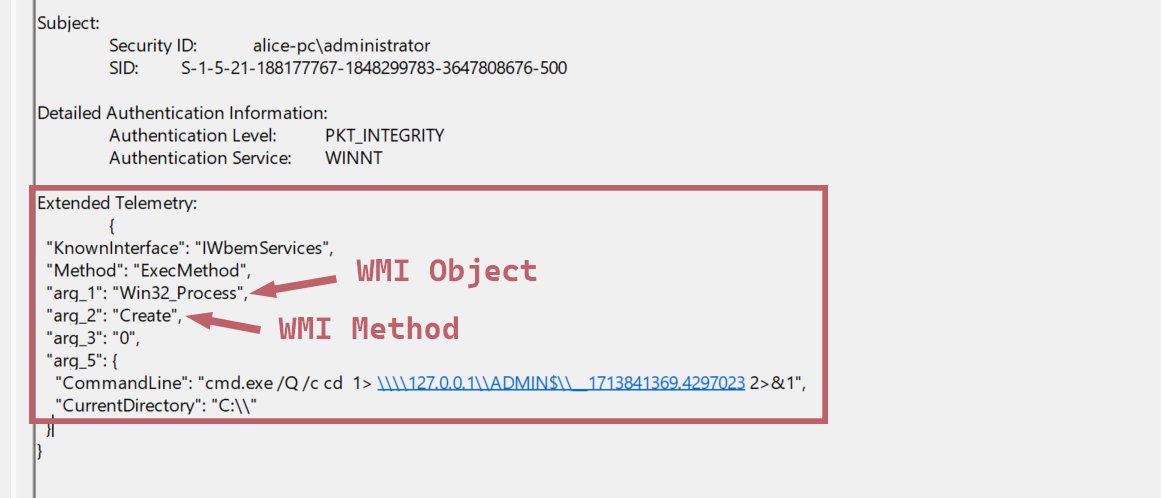
Excellent writeup by @cybergentix on #WMI #LateralMovement. Didn't mention mitigation via #RPCFirewall, which could be achieved by blocking remote #DCOM operations.
1
35
131
We've added argument decoders for CertServerRequest to the Extended Telemetry fork of RPC Firewall. This can reveal AD CS abuse in real time with:. • source user/IP.• the requested certificate template.• subject alt names. #ThreatHunting #DFIR
2
34
135
Extended telemetry for RPC Firewall decodes RPC call parameters. The context gives a single authoritative event for:. • Lateral movement.• Forced authentication.• Remote enumeration. #ThreatHunting #DFIR
4
22
67
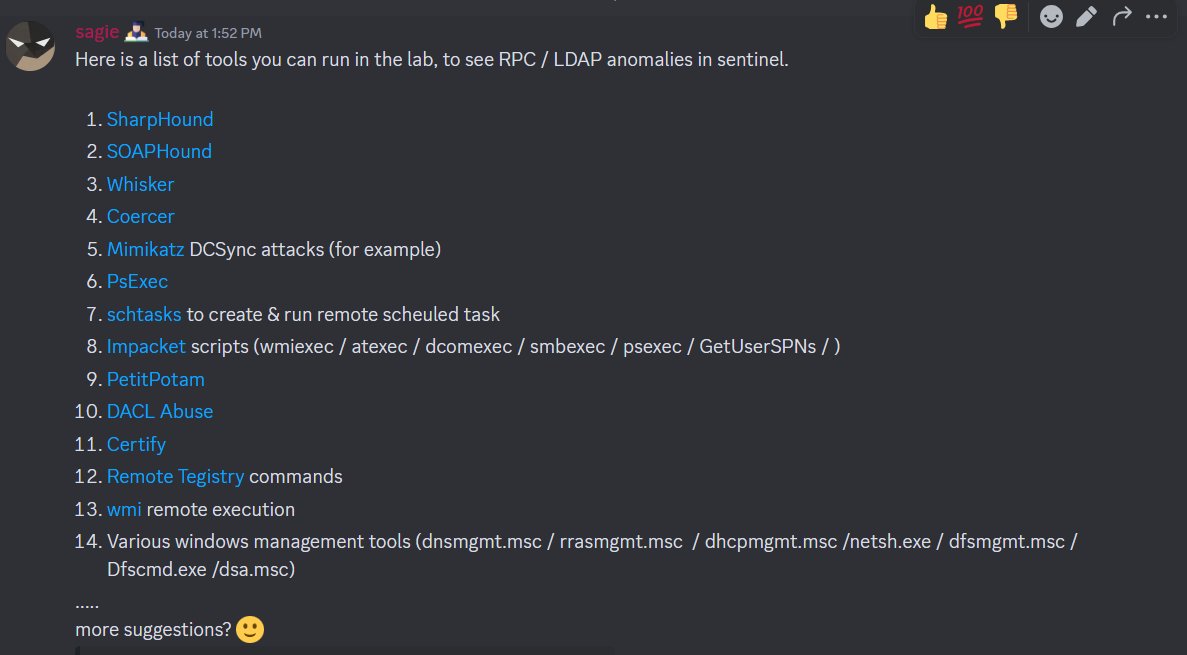
Shared a (partial) list of suggested tools to run in the @DEATHCon2024 lab to see #LDAPFirewall & #RPCFirewall in action. Anything else I need to add ? :)
1
1
10
RPCFirewall is a great tool, and one of the few available that can help you detect RPC activities, as I already mentioned in my research. However, be careful about blocking such activities before you monitor your environment, especially if you have legacy systems.
#NauthNRPC is a tool that can help you enumerate computer / user accounts anonymously in #ActiveDirectory via DsrGetDcNameEx2 RPC calls. This is not often in most environments, so used could be blocked via #RPCFirewall. Nice job by @haider_kabibo 🏆🏆.
0
7
29
@MGrafnetter directed my attention to a new RPC filter capability!. Good job by @MSFTResearch / @Microsoft for this. I Hope that #RPCFirewall contributed in showcasing the need for a more granular RPC WFP support .
1
5
18
Don't miss Zero Networks' Sagie Dulce & Dekel Paz at #DEATHCon2023 💪! Check out their session on November 4 📅: "Detection Engineering with #RPCFirewall and #LDAPFirewall," and better detect and prevent #lateralmovement and #ransomware attacks. 🔐
0
2
4
RPC Firewall. Check out our RPC Firewall blog post or our BlackHat talk to gain better understanding of RPC, RPC attacks and the solution: the RPC Firewall. #cybersecurity #infosec.
0
0
11
One week till @NorthSec_io. @dekel_paz and I are doing a workshop on how to stop (a lot!) of #ActiveDirectory attacks via #LDAPFirewall and #RPCFirewall. Make sure to BYOAD (Bring Your Own Active Directory) so you can follow along yourself.
2
3
6
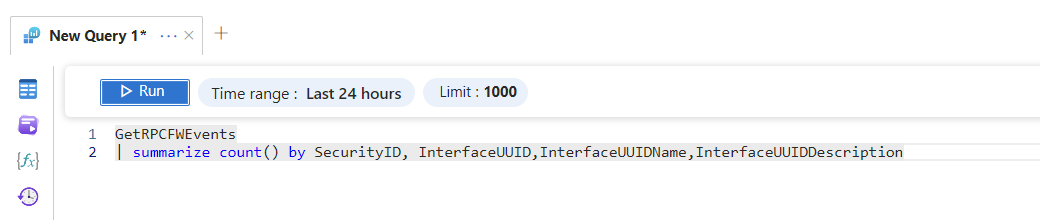
In this @DEATHCon2024 , @dekel_paz and @SagieDulce will show how #RPCFirewall & #LDAPFirewall capture potentially malicious activities on the DCs. If you configure our tools right, you're a simple Sentinel query away from detecting (and the next step is stopping) attacks!
0
3
11
🚨 𝗦𝗲́𝗰𝘂𝗿𝗶𝘁𝗲́ 𝗱𝗲 𝗹'𝗔𝗰𝘁𝗶𝘃𝗲 𝗗𝗶𝗿𝗲𝗰𝘁𝗼𝗿𝘆 : filtrez les accès RPC 𝗱𝗮𝗻𝗴𝗲𝘂𝗿𝗲𝘂𝘅 avec 𝗥𝗣𝗖𝗙𝗶𝗿𝗲𝘄𝗮𝗹𝗹 . 📖 Lisez l'article pour en savoir plus : #cybersécurité #ActiveDirectory #RPCFirewall
0
3
9
Great research @mcbroom_evan . Thank you for checking out #RPCFirewall, even though it is not adequate at mitigating local attacks (its very easy to modify the code so it monitors local RPC calls), as it is intended to stop remote RPC calls.
0
0
3
#LDAPNightmare #PoC by @safebreach uses RPC to trigger CLDAP search. Crafted response may #RCE. Once you achieve MITM (via RPC or otherwise) you could exploit on any windows OS. #RPCFirewall could mitigate the triggering part :). @guhe120.@MacmodSec .@oryair1999 .@ShahakMo.
1/ A DoS exploit demo for CVE-2024-49112 by @safebreach. RCE exploit is probably coming soon. Patch!
0
3
10
My thoughts about CVE-2025-33073, and on how to prevent #NTLM / #Kerberos relay attacks in general using #RPCFirewall & #LDAPFirewall.
0
6
11
Great content from @D1iv3, introducing 𝗿𝗲𝗺𝗼𝘁𝗲 privilege escalation via #NTLM & #Kerberos over DCOM. I would recommend also using the #RPCFirewall as mitigation on your ADCS servers :).#BHASIA
During #BHASIA Briefing "CertifiedDCOM: The Privilege Escalation Journey to Domain Admin with DCOM" we will uncover a remote attack surface of DCOM and disclose a critical vulnerability related to it. Register now >>
0
35
90