Jayesh Madnani
@Jayesh25_
Followers
14K
Following
1K
Media
60
Statuses
935
CEO and Hacker in charge @ EIS | HackerOne Top 10 | https://t.co/JSX03WutFN
http://hackerone.com/jayesh25
Joined February 2016
Here’s how I discovered a critical issue on a wide-scope program using @netlas_io 👇. The target had a pretty generic login flow via a 3rd-party service with specific keywords. It was pretty much using the same codebase reused across multiple assets. I used.
4
34
212
RT @zhero___: very pleased to announce the release of my new article based on my research that led to CVE-2024-46982 titled:. Next.js, cach….
0
239
0
RT @Jayesh25_: 🔐Secrets no one will share with you - Here's a technique that might grant you access to takeover other users' accounts using….
0
274
0
Great initiative by @c3l3si4n! Don’t forget to include the tool below in your list for discovering subdomains for your bug bounty targets. It’s always great to have multiple data sources :).
In the past few months, I've been making a subdomains database containing 1.6 billion subdomains scrapped from multiple public (and private) sources. This database is now public and FREE and can be queried on the following website. Enjoy!
0
8
100
Found a pretty cool feature on @Netlas_io called the "Attack Surface Discovery Tool" to quickly map the external attack surface for large-scope targets. This helped me find some quick wins during a recent bug bounty engagement. What’s awesome? It provides a complete overview of
1
42
259
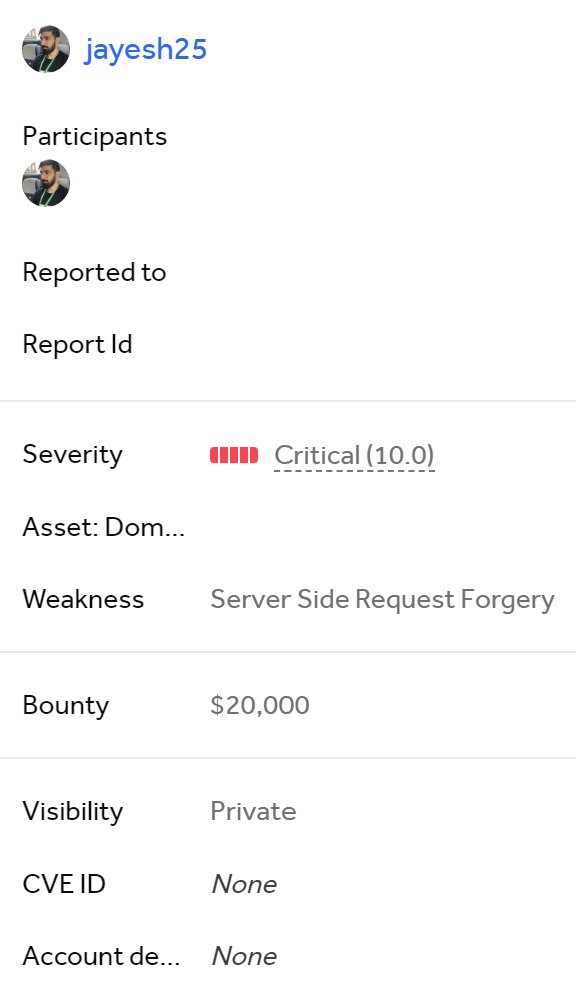
🚨 Yay, we were rewarded with $20,000 on our.@Hacker0x01 submission for a SSRF bug discovered in collaboration with @Shlibness! 💰🎉. 🥳 We uncovered a Critical SSRF vulnerability, turning it into unauthorized access to internal admin endpoints, leading to PII leaks and
58
147
1K