Explore tweets tagged as #CommandExecution
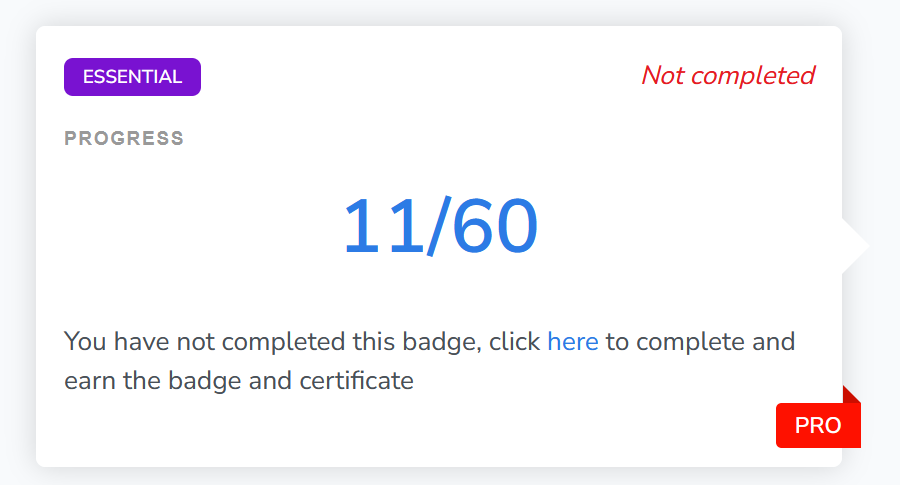
Day 3 for 90 days challenge on @PentesterLab. I just completed 11 exercises of Essential Bagde @Pentesterlab. #CodeExecution #CommandExecution #Webapplication #Pentesting #Bugbounty
0
1
7
Day 4 for 90 days challenge on @PentesterLab.completed more in the exercises of Essential Bagde @Pentesterlab but this progress maybe change at the end of today. Saturday and Sunday I have more time to learn. #CodeExecution #CommandExecution #Webapplication #Pentesting #Bugbounty
0
1
5
#Vulnyx día 14, Maquina Pl0t.#rce.#urlencode.#sudo.#ssh.#TAR_Wildcards.#CommandExecution.#learning #vulnyx #remote #hacking #habock #Bolivia
0
0
0
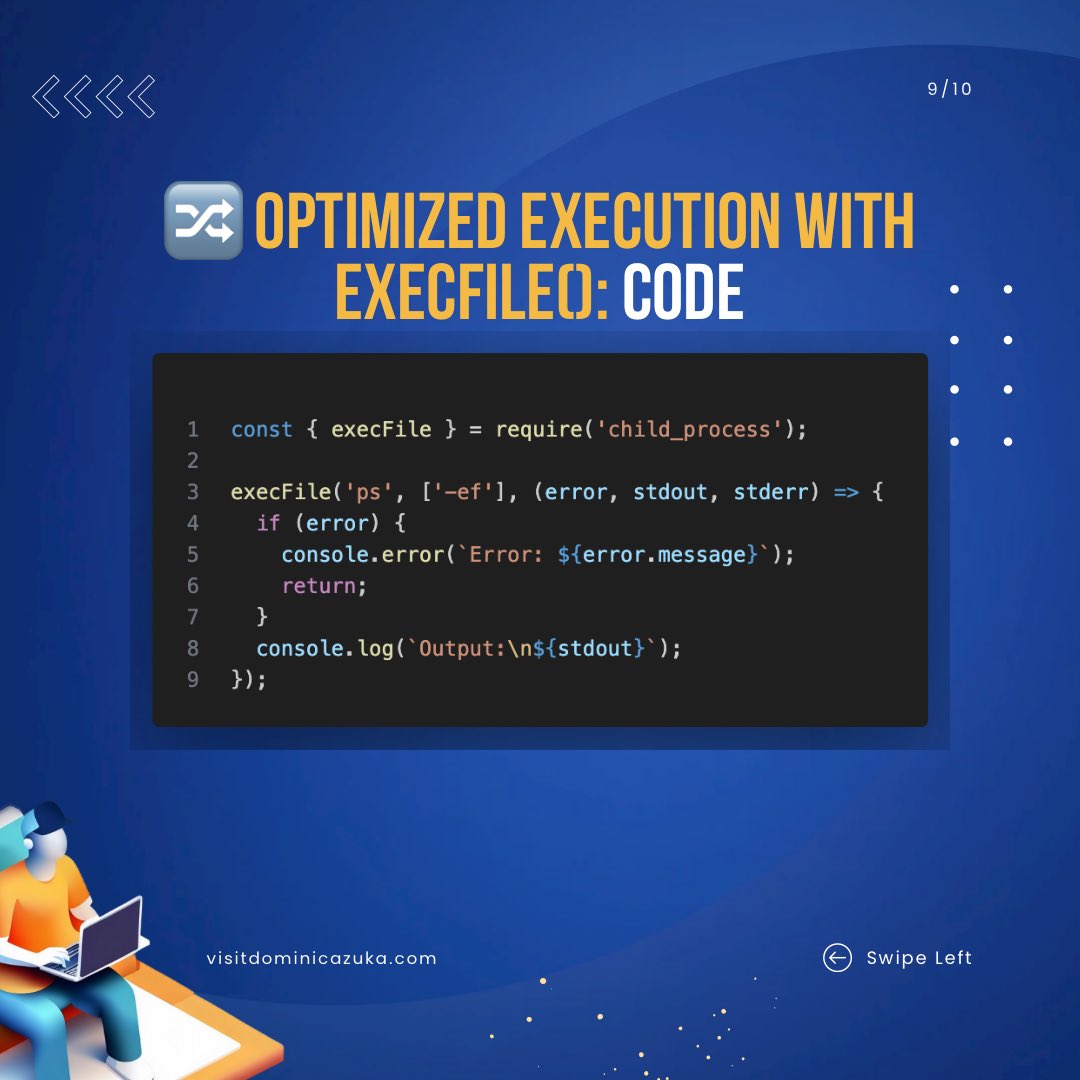
I'm confident that by the last slide of this thread, you'll be a command-line ninja! You'll be able to use the child_process module to execute commands like a pro. #NodeJS #ChildProcessModule #CommandExecution . •#programming.•#coding.•#programmer.•#developer
0
0
0
🌐 I-O DATA routers under attack! 2.1.8 & earlier are vulnerable to #CredentialTheft, #CommandExecution, #FirewallBypass: CVE-2024-45841, CVE-2024-47133, CVE-2024-52564.🛡 Stay secure with SOCRadar's #VulnerabilityIntelligence: #PatchNow #IODATA
0
0
1
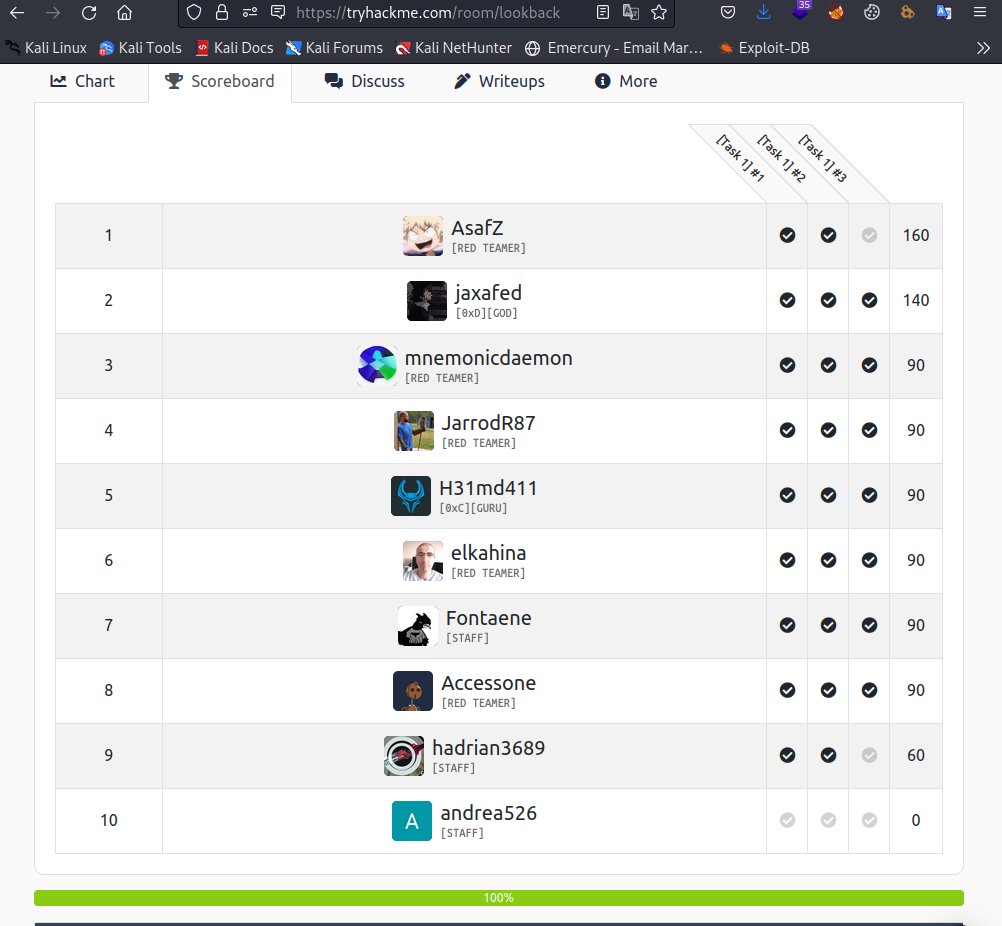
Another room finished on Tryhackme I do like when i finish the room within the first few users and get on that scoreboard!.#tryhackme #powershell #commandexecution #RCE
0
0
1
🚨 CVE-2025-46816 in goshs allows command execution. Update to version 1.0.5 or later immediately and consider access controls for temporary protection. 🔧 Read more: #goshs #CommandExecution #CyberSecurity #Vulert #PatchNow 🛡️
0
0
0
Proof-of-Concept Released for Kubernetes Vulnerabilities Exposing Windows Nodes. Read HiveForce Labs' threat advisory: #Kuberenetes #PrivilegeEscalation #commandexecution #SecurityUpdate #ThreatIntel #InfoSec #Uni5 #Risk #vulnerability #CVE
0
0
0
Android TV box on Amazon came pre-installed with malware #AndroidTV #Amazon #Malware #SmartTV #Firmware #DataModification #CommandExecution #ThreatActor #FactoryReset
0
1
0
• #CommandExecution over #NamedPipes (#SMB). • No Installation Required. • #UserFriendly Framework. • Versatile Post-Exploitation Modules. #TrustEverybodyButCutTheCards.
0
0
0
¡Intro to Whitebox Pentesting! 💪.#CodeReview #CodeInjection #CommandExecution #BlindExploitation #ExploitDevelopment #Patching #ApplicationSecurity #AppSec #HTBAcademy.
0
0
0
readLine()の処理を、EditorStateで分岐するようにしました。#MyHL. for (;;) { // 2行目以降. if (editor.state == EditorState_Initial) {. }. else if (editor.state == EditorState_InputHandling) {. }. else if (editor.state == EditorState_CommandExecution) {. }.}.
0
0
4
SnipBot: Nova RomCom varijanta #antisandboxingtechniques #archivepayloads #c2communications #commandexecution #dataexfiltration #filestealing #granularcontrol #snipbotmalware #tlsprotocol #windowsregistrymodification.
0
0
0